Networking Zones . Each zone consists of a single interface or a group of. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. a security zone is a portion of a network that has specific security requirements set. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. by default, developed information systems should consist of at least three components (security zones): each zone inside the network has different security requirement depending on the systems hosted within. Zones also protect the network by. zones protect your network by segmenting it into smaller, more easily managed areas. As per the sans, below listed are common security zones which should be implemented. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure.
from learn.microsoft.com
Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. by default, developed information systems should consist of at least three components (security zones): each zone inside the network has different security requirement depending on the systems hosted within. As per the sans, below listed are common security zones which should be implemented. a security zone is a portion of a network that has specific security requirements set. Zones also protect the network by. zones protect your network by segmenting it into smaller, more easily managed areas. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Each zone consists of a single interface or a group of.
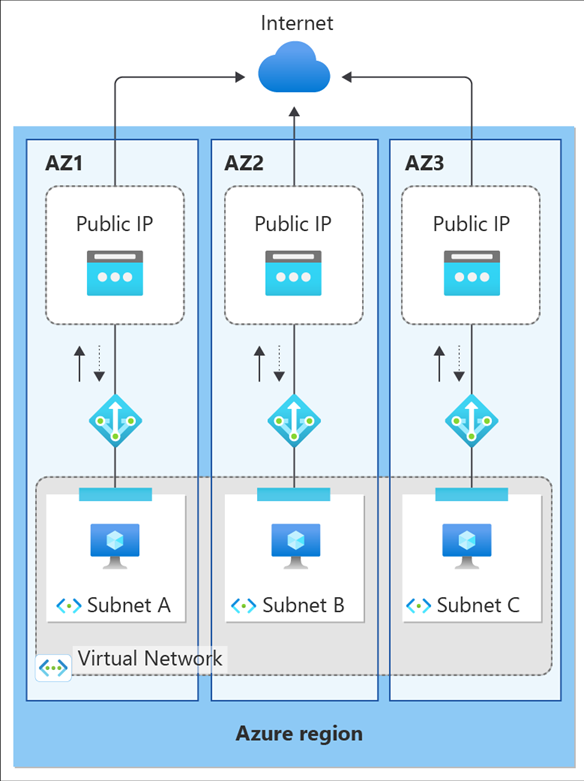
NAT gateway and availability zones Azure Virtual Network NAT
Networking Zones a security zone is a portion of a network that has specific security requirements set. zones protect your network by segmenting it into smaller, more easily managed areas. a security zone is a portion of a network that has specific security requirements set. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. Each zone consists of a single interface or a group of. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. by default, developed information systems should consist of at least three components (security zones): in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. each zone inside the network has different security requirement depending on the systems hosted within. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. As per the sans, below listed are common security zones which should be implemented. Zones also protect the network by.
From amplify.nabshow.com
Zones Facilitate Networking, Discovery and Education NAB Amplify Networking Zones a security zone is a portion of a network that has specific security requirements set. Zones also protect the network by. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. zones protect your network by segmenting it into smaller, more easily managed areas. . Networking Zones.
From www.networkmanagementsoftware.com
Google Cloud Platform (GCP) Networking Fundamentals Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. zones protect your network by segmenting it into smaller, more easily managed areas. As per the sans, below listed are. Networking Zones.
From www.researchgate.net
Concept of factory network with separated secured DMZ zones Download Networking Zones Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. each zone inside the network has different security requirement depending on the systems hosted within. Each zone consists of a single interface or a group of. by default, developed information systems should consist of at. Networking Zones.
From cloudconstruct.co.uk
AWS What is an Availability Zone? Cloud Construct Networking Zones Zones also protect the network by. Each zone consists of a single interface or a group of. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks,. Networking Zones.
From help.sap.com
Network Security Networking Zones As per the sans, below listed are common security zones which should be implemented. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Each zone consists of a single interface or a group of. by default, developed information systems should consist of at least three components (security zones): . Networking Zones.
From www.dynatrace.com
Network zones Dynatrace Docs Networking Zones As per the sans, below listed are common security zones which should be implemented. each zone inside the network has different security requirement depending on the systems hosted within. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. a security zone is a portion. Networking Zones.
From bogotobogo.com
AWS Networking 2021 Networking Zones in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. each zone inside the network has different security requirement depending on the systems hosted within.. Networking Zones.
From help.sap.com
Using Multiple Network Zones Networking Zones in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. a security zone is a portion of a network that has specific security requirements set.. Networking Zones.
From www.cisco.com
Network Security within a Converged Plantwide Architecture Networking Zones by default, developed information systems should consist of at least three components (security zones): Each zone consists of a single interface or a group of. a security zone is a portion of a network that has specific security requirements set. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks,. Networking Zones.
From 1reddrop.com
AWS Global Infrastructure Regions and Availability Zones Explained Networking Zones Each zone consists of a single interface or a group of. each zone inside the network has different security requirement depending on the systems hosted within. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. As per the sans, below listed are common. Networking Zones.
From www.techtarget.com
What is a DMZ in Networking? Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. a network zone is a configurable boundary that you can use to grant or restrict access to computers. Networking Zones.
From blogs.vmware.com
Segmentation of the Network into Security Zones Network and Security Networking Zones Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. each zone inside the network has different security requirement depending on the systems hosted within. Zones also protect the network by. As per the sans, below listed are common security zones which should be implemented. . Networking Zones.
From jayendrapatil.com
AWS Regions, Availability Zones and Edge Locations Certification Networking Zones network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. As per the sans, below listed are common security zones which should be implemented. Each zone consists of a single interface or a group of. zones protect your network by segmenting it into smaller, more easily managed areas. in. Networking Zones.
From hevodata.com
A QuickStart Guide to AWS High Availability and Its 3 Dimensions Networking Zones a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. each zone inside the network has different security requirement depending on the systems hosted within. Zones also. Networking Zones.
From www.pinterest.ph
Division of diffident zones in a local network. You can edit this Networking Zones in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Each zone consists of a single interface or a group of. zones protect your network by segmenting it into smaller, more easily managed areas. a network zone is a configurable boundary that you. Networking Zones.
From learn.microsoft.com
Azure regions and availability zones Microsoft Learn Networking Zones As per the sans, below listed are common security zones which should be implemented. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Each zone consists of. Networking Zones.
From www.cisco.com
Products ISA/IEC6244333 What is it and how to comply? Cisco Networking Zones by default, developed information systems should consist of at least three components (security zones): Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. zones protect your network by segmenting it into smaller, more easily managed areas. each zone inside the network has different. Networking Zones.
From www.cisco.com
Industrial Security Design Guide Industrial Security Design Guide Networking Zones Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. by default, developed information systems should consist of at least three. Networking Zones.
From aws.amazon.com
VPC Zoning Patterns for SAP on AWS, Part 2 Network Zoning AWS Networking Zones As per the sans, below listed are common security zones which should be implemented. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. a network zone. Networking Zones.
From learn.microsoft.com
NAT gateway and availability zones Azure Virtual Network NAT Networking Zones in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. by default, developed information systems should consist of at least three components (security zones): network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. As. Networking Zones.
From 1reddrop.com
AWS Global Infrastructure Regions and Availability Zones Explained Networking Zones zones protect your network by segmenting it into smaller, more easily managed areas. As per the sans, below listed are common security zones which should be implemented. by default, developed information systems should consist of at least three components (security zones): Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the. Networking Zones.
From intellipaat.com
What is an AWS landing zone? Overview, Architecture, Benefits & Setup Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. by default, developed information systems should consist of at least three components (security zones): in cybersecurity, the concepts of. Networking Zones.
From www.youtube.com
Module 5 Demilitarized Zone (DMZ) YouTube Networking Zones Zones also protect the network by. As per the sans, below listed are common security zones which should be implemented. each zone inside the network has different security requirement depending on the systems hosted within. zones protect your network by segmenting it into smaller, more easily managed areas. by default, developed information systems should consist of at. Networking Zones.
From medium.com
Security Zoning in Network Architecture by Aman Bansal Jun, 2020 Networking Zones a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. by default, developed information systems should consist of at least three components (security zones): network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. a security. Networking Zones.
From gca.isa.org
How to Define Zones and Conduits Networking Zones network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Zones also protect the network by. zones protect your network by segmenting it into smaller, more easily managed areas. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices. Networking Zones.
From www.networkmanagementsoftware.com
Google Cloud Platform (GCP) Networking Fundamentals Networking Zones zones protect your network by segmenting it into smaller, more easily managed areas. Each zone consists of a single interface or a group of. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. in cybersecurity, the concepts of zones and conduits are used to. Networking Zones.
From www.youtube.com
Firewall Security Zones Zone based Policy Firewall ZPF YouTube Networking Zones As per the sans, below listed are common security zones which should be implemented. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Each zone consists of a single interface or a group of. zones protect your network by segmenting it into smaller, more easily managed areas. in. Networking Zones.
From www.spamtitan.com
Network Segmentation Best Practices to Improve Security Filtering Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Each zone consists of a single interface or a group of. As per the sans, below listed are common. Networking Zones.
From dzone.com
AWS VPC NAT Instance Failover and High Availability DZone Networking Zones by default, developed information systems should consist of at least three components (security zones): Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. a security zone is a portion of a network that has specific security requirements set. a network zone is a. Networking Zones.
From www.glocomp.com
Securing industrial networks What is ISA/IEC 62443? Systems Networking Zones As per the sans, below listed are common security zones which should be implemented. a network zone is a configurable boundary that you can use to grant or restrict access to computers and devices in your. by default, developed information systems should consist of at least three components (security zones): network segmentation in computer networking is the. Networking Zones.
From www.pinterest.com
Everything You Need to Know about Network Diagrams from Network Networking Zones zones protect your network by segmenting it into smaller, more easily managed areas. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. a network zone. Networking Zones.
From www.redhat.com
OpenShift on OpenStack Introduction to availability zones Networking Zones in cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. each zone inside the network has different security requirement depending on. Networking Zones.
From kingofnetworking.weebly.com
Different Types of Computer Networks King Of Networking Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. by default, developed information systems should consist of at least three components (security zones): Zones also protect the network by. Each zone consists of a single interface or a group of. As per the sans, below listed are common security zones which should. Networking Zones.
From www.vrogue.co
Aws Regions Availability Zones And Edge Locations Exp vrogue.co Networking Zones Each zone consists of a single interface or a group of. As per the sans, below listed are common security zones which should be implemented. zones protect your network by segmenting it into smaller, more easily managed areas. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. Zones also. Networking Zones.
From aws.amazon.com
VPC Zoning Patterns for SAP on AWS, Part 2 Network Zoning AWS Networking Zones each zone inside the network has different security requirement depending on the systems hosted within. network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each. As per the sans, below listed are common security zones which should be implemented. zones protect your network by segmenting it into smaller, more. Networking Zones.