Network Architecture Best Practices Security . It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. It will assist administrators in. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Focus on visibility and control where it makes sense, and everything should work out just fine. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Introduction to networking on azure. Comprehensive network security design means understanding what you have, where it's located, and. This report presents best practices for overall network security and protection of individual network devices. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. Network environments are dynamic and.
from www.cisco.com
Introduction to networking on azure. Network environments are dynamic and. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. This report presents best practices for overall network security and protection of individual network devices. Comprehensive network security design means understanding what you have, where it's located, and. Focus on visibility and control where it makes sense, and everything should work out just fine. It will assist administrators in. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers:
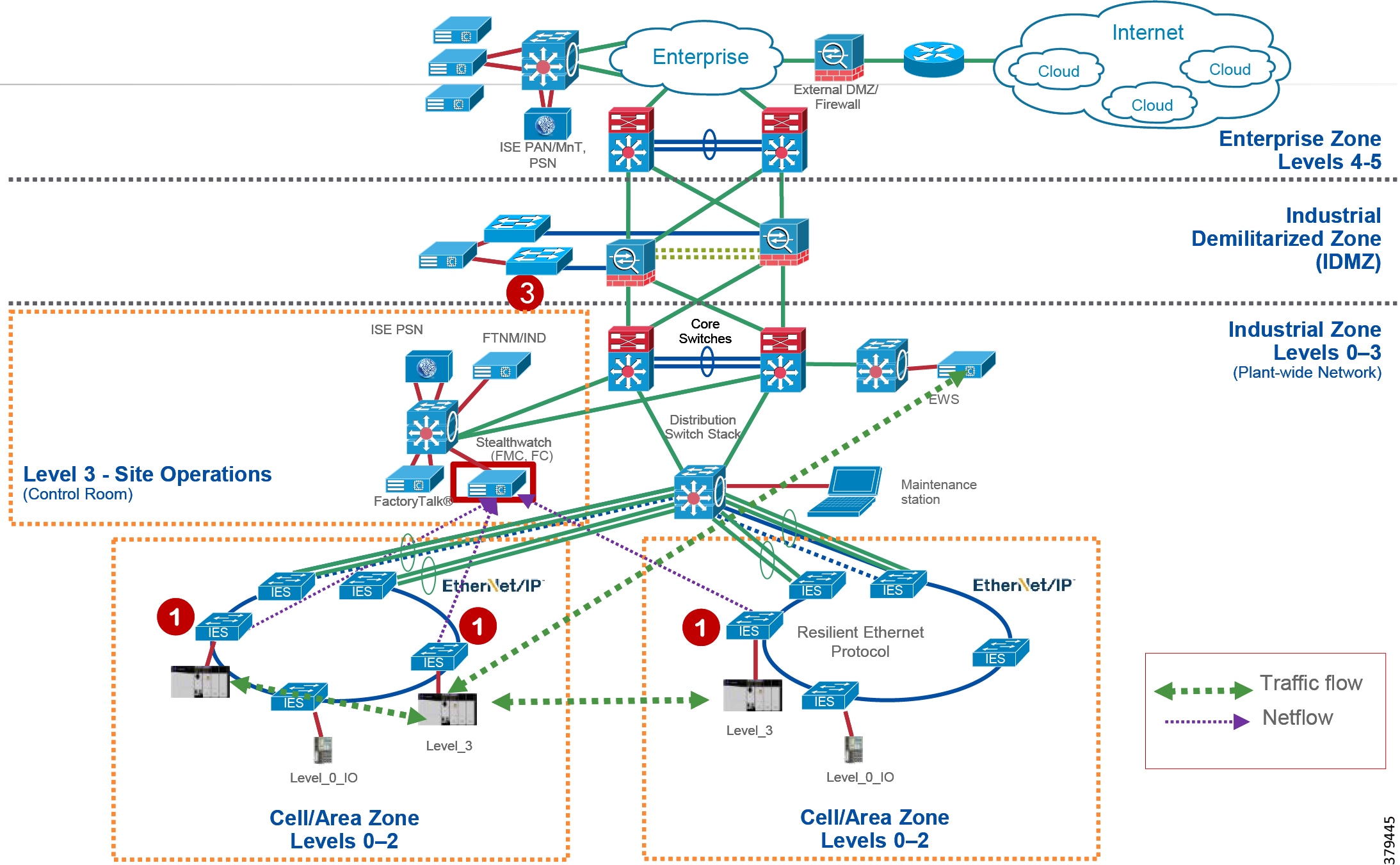
Network Security within a Converged Plantwide Architecture
Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. Comprehensive network security design means understanding what you have, where it's located, and. Focus on visibility and control where it makes sense, and everything should work out just fine. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Introduction to networking on azure. Network environments are dynamic and. This report presents best practices for overall network security and protection of individual network devices. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. It will assist administrators in.
From iebmedia.com
Designing industrial networks from a security point of view Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. Comprehensive network security design means understanding what you have, where it's located, and. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. The report captures best practices based on. Network Architecture Best Practices Security.
From zivaro.com
Enterprise Network Security Architecture Transformation Zivaro Network Architecture Best Practices Security It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. Network environments are dynamic and. This report presents best practices for overall network security and protection of individual network devices. Introduction to networking on azure. The report captures best practices based on the depth and breadth of experience in. Network Architecture Best Practices Security.
From www.conceptdraw.com
Network Security Diagrams Network Security Architecture Diagram Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. It will assist administrators in. Introduction to networking on azure. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as. Network Architecture Best Practices Security.
From www.securityandit.com
Best practices for network segmentation Network Security Protocols Network Architecture Best Practices Security Introduction to networking on azure. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Focus on visibility and control where it makes sense, and everything. Network Architecture Best Practices Security.
From www.educba.com
Security Architecture Components of Security Architecture Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. This report presents best practices for overall network security and protection of individual network devices. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It examines the security limitations of current network access solutions (e.g.,. Network Architecture Best Practices Security.
From exymlmlyf.blob.core.windows.net
Network Design Best Practices Cisco at Charles Radford blog Network Architecture Best Practices Security The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Focus on visibility and control where it makes sense, and everything should work out just fine. Network environments are dynamic and. It will assist administrators in. The report captures best practices based on the depth and breadth of experience in supporting customers. Network Architecture Best Practices Security.
From medium.com
Design for a Secure Network Architecture by Naka Medium Network Architecture Best Practices Security Network environments are dynamic and. Introduction to networking on azure. Focus on visibility and control where it makes sense, and everything should work out just fine. Comprehensive network security design means understanding what you have, where it's located, and. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: The report captures. Network Architecture Best Practices Security.
From www.iansresearch.com
OT Security Best Practices Checklist IANS Research Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. Comprehensive network security design means understanding what you have, where it's located, and. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. This report presents best practices for overall network security and protection. Network Architecture Best Practices Security.
From learn.microsoft.com
Best practices to set up networking for workloads migrated to Azure Network Architecture Best Practices Security Network environments are dynamic and. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as. Network Architecture Best Practices Security.
From aws.amazon.com
Securing SAP with AWS Network Firewall Part 1 Architecture design Network Architecture Best Practices Security It will assist administrators in. Introduction to networking on azure. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Network environments are dynamic and. This report presents best practices for overall network security and protection of individual network devices. This article explores network security architecture components, goals, best practices,. Network Architecture Best Practices Security.
From pdfprof.com
cisco network security design best practices Network Architecture Best Practices Security The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. Network environments are dynamic and. Comprehensive network security design means understanding what you have, where it's located, and.. Network Architecture Best Practices Security.
From www.gartner.com
A Primer on Network Security Architecture Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It will assist administrators in.. Network Architecture Best Practices Security.
From techzmac.blogspot.com
Securing Wireless Networks Best Practices With MikroTik Routers techzmac Network Architecture Best Practices Security It will assist administrators in. Comprehensive network security design means understanding what you have, where it's located, and. Focus on visibility and control where it makes sense, and everything should work out just fine. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. This article explores network security architecture. Network Architecture Best Practices Security.
From ipcisco.com
Network Topology Architectures ⋆ IpCisco Network Architecture Best Practices Security Introduction to networking on azure. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It will assist administrators in. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. Comprehensive network security design means understanding what you have, where it's. Network Architecture Best Practices Security.
From www.conceptdraw.com
Network Security Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. Network environments are dynamic and. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It will assist administrators in. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as. Network Architecture Best Practices Security.
From www.semanticscholar.org
[PDF] Design and Implementation of a Network Security Model for Network Architecture Best Practices Security Network environments are dynamic and. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: This report presents best practices for overall network security and protection of individual network devices. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. It will. Network Architecture Best Practices Security.
From docs.fortinet.com
Network topology best practices FortiDeceptor 4.0.0 Network Architecture Best Practices Security The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. It will assist administrators in. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Focus on visibility and control where it makes sense, and everything should work out just fine. Network. Network Architecture Best Practices Security.
From learn.microsoft.com
Security considerations for highly sensitive IaaS apps in Azure Azure Network Architecture Best Practices Security This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. This report presents best practices for overall network security and protection of individual network devices. Focus on visibility and control where it makes sense, and everything should work out just fine. The report captures best practices. Network Architecture Best Practices Security.
From learn.microsoft.com
Best practices to set up networking for workloads migrated to Azure Network Architecture Best Practices Security Network environments are dynamic and. This report presents best practices for overall network security and protection of individual network devices. Introduction to networking on azure. It will assist administrators in. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Focus on visibility and control where it makes sense, and. Network Architecture Best Practices Security.
From learn.microsoft.com
Best practices to set up networking for workloads migrated to Azure Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. Network environments are dynamic and. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Introduction to networking on azure. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as. Network Architecture Best Practices Security.
From www.mdpi.com
Applied Sciences Free FullText Firewall Best Practices for Network Architecture Best Practices Security It will assist administrators in. Introduction to networking on azure. Network environments are dynamic and. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. Focus on visibility and control where it makes sense, and everything should work out just fine. Comprehensive network security design means understanding what you. Network Architecture Best Practices Security.
From www.techtarget.com
Network security design best practices and principles Keep it simple Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. Network environments are dynamic and. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise. Network Architecture Best Practices Security.
From www.conceptdraw.com
Cisco Network Design Quickly Create HighQuality Cisco Network Diagram Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. Focus on visibility and control where it makes sense, and everything should work out just fine. Comprehensive network security design means understanding what you have, where it's located, and. It will assist administrators in. This article explores network security architecture components, goals, best practices, frameworks,. Network Architecture Best Practices Security.
From secureops.com
Four Strategic Principles of Network Security Design SecureOps Network Architecture Best Practices Security The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: Network environments are dynamic and. Introduction to networking on azure. This report presents best practices for overall network security and protection of individual network devices. It will assist administrators in. It examines the security limitations of current network access solutions (e.g., vpns). Network Architecture Best Practices Security.
From www.cisco.com
Wireless and Network Security Integration Solution Design Guide Network Architecture Best Practices Security Introduction to networking on azure. Comprehensive network security design means understanding what you have, where it's located, and. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. The. Network Architecture Best Practices Security.
From opscompass.com
5 Best Practices for Securing Microsoft Azure Network Architecture Best Practices Security This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. It will assist administrators in. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. The enterprise network landscape has undergone tremendous changes in the last. Network Architecture Best Practices Security.
From exymlmlyf.blob.core.windows.net
Network Design Best Practices Cisco at Charles Radford blog Network Architecture Best Practices Security Introduction to networking on azure. Focus on visibility and control where it makes sense, and everything should work out just fine. This report presents best practices for overall network security and protection of individual network devices. It will assist administrators in. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you. Network Architecture Best Practices Security.
From blogs.cisco.com
Cisco Secure Cloud Architecture for Azure Cisco Blogs Network Architecture Best Practices Security The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. Comprehensive network security design means understanding what you have, where it's located, and. It will assist administrators in. Introduction to networking on azure. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as. Network Architecture Best Practices Security.
From www.slideteam.net
Best Practices For Implementing Network Architecture Network Architecture Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. This report presents. Network Architecture Best Practices Security.
From www.cisco.com
Network Security within a Converged Plantwide Architecture Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. It will assist. Network Architecture Best Practices Security.
From www.arctitan.com
Network Segmentation Best Practices to Improve Security ArcTitan Network Architecture Best Practices Security Focus on visibility and control where it makes sense, and everything should work out just fine. It will assist administrators in. Introduction to networking on azure. The enterprise network landscape has undergone tremendous changes in the last decade due to the following three drivers: It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network. Network Architecture Best Practices Security.
From rajanieshkaushikk.com
Azure Architecture Best Practice for securing Azure Virtual Networks Network Architecture Best Practices Security It will assist administrators in. This report presents best practices for overall network security and protection of individual network devices. Focus on visibility and control where it makes sense, and everything should work out just fine. Network environments are dynamic and. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you. Network Architecture Best Practices Security.
From www.reddit.com
Network physical segregation with secure router/firewall r/PLC Network Architecture Best Practices Security This report presents best practices for overall network security and protection of individual network devices. It examines the security limitations of current network access solutions (e.g., vpns) to the enterprise network as well as point security. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network.. Network Architecture Best Practices Security.
From www.sdmmag.com
5 Top Network Design Considerations for Security Integrators 201901 Network Architecture Best Practices Security It will assist administrators in. Focus on visibility and control where it makes sense, and everything should work out just fine. Network environments are dynamic and. The report captures best practices based on the depth and breadth of experience in supporting customers and responding to threats. This report presents best practices for overall network security and protection of individual network. Network Architecture Best Practices Security.
From www.clickittech.com
DevOps Security Best Practices Video Network Architecture Best Practices Security It will assist administrators in. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network. This report presents best practices for overall network security and protection of individual network devices. Focus on visibility and control where it makes sense, and everything should work out just fine.. Network Architecture Best Practices Security.