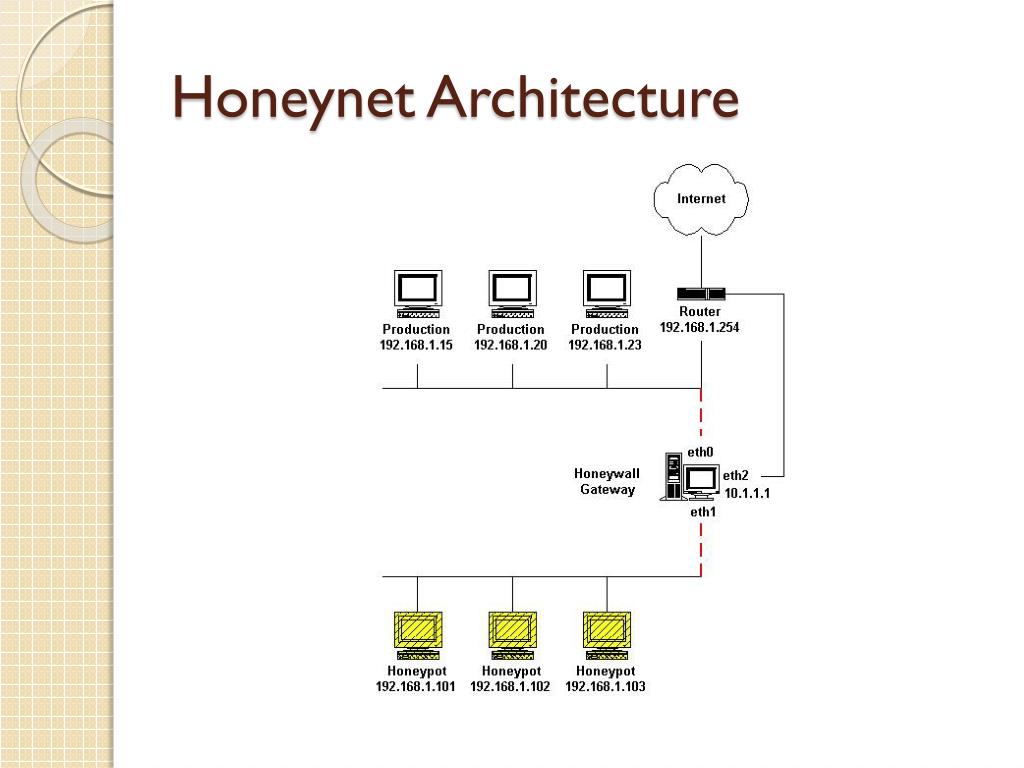
Honeynet Cyber Security . a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. A honeypot is a security mechanism that creates a virtual trap to lure attackers. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. honeypots in cybersecurity have two primary uses, research and production. Most often, honeypots will balance rooting out and collecting. Cyber honeypots are baited, virtual traps for threat actors. By luring adversaries to interact with the decoy. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots.
from www.slideserve.com
By luring adversaries to interact with the decoy. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. Most often, honeypots will balance rooting out and collecting. Cyber honeypots are baited, virtual traps for threat actors. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. honeypots in cybersecurity have two primary uses, research and production. A honeypot is a security mechanism that creates a virtual trap to lure attackers. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies.
PPT Honeypots and PowerPoint Presentation, free download
Honeynet Cyber Security a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. A honeypot is a security mechanism that creates a virtual trap to lure attackers. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. By luring adversaries to interact with the decoy. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. honeypots in cybersecurity have two primary uses, research and production. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. Most often, honeypots will balance rooting out and collecting. Cyber honeypots are baited, virtual traps for threat actors. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers.
From www.youtube.com
Network Security Fastflux (Basic part 4/9) YouTube Honeynet Cyber Security By luring adversaries to interact with the decoy. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. Most often, honeypots will balance rooting out and collecting. A honeypot is a security mechanism that creates a. Honeynet Cyber Security.
From www.youtube.com
Cybersecurity 101 What Is A Honeypot YouTube Honeynet Cyber Security Cyber honeypots are baited, virtual traps for threat actors. Most often, honeypots will balance rooting out and collecting. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. honeypots in cybersecurity have two primary uses, research and production. They’re decoys designed to mimic targets for attackers and can be. Honeynet Cyber Security.
From exemplarysecurity.com
Microsoft Azure SOC and Exemplary Security Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them. Honeynet Cyber Security.
From www.youtube.com
& Sandbox Explained by Cyber security Professional Honeynet Cyber Security honeypots in cybersecurity have two primary uses, research and production. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. A honeypot is a security mechanism that creates a virtual trap to lure attackers. a honeynet is a network set up to. Honeynet Cyber Security.
From www.huffingtonpost.com
Map Of Global Cyberattacks, Created By Project, Shows Where Honeynet Cyber Security An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. Most often, honeypots will balance rooting out and collecting. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. in cybersecurity, cyber honeypots often work fundamentally in the same way. Honeynet Cyber Security.
From www.researchgate.net
(PDF) Implementation in Cyber Security Attack Prevention with Honeynet Cyber Security honeypots in cybersecurity have two primary uses, research and production. By luring adversaries to interact with the decoy. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. Most often, honeypots will balance rooting out and collecting. Cyber honeypots are baited, virtual traps. Honeynet Cyber Security.
From www.researchgate.net
(PDF) Adaptive and Flexible Virtual Honeynet Cyber Security in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. Most often, honeypots will balance rooting out and collecting. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. a honeynet is a network set up to catch a hacker's attention and study how they. Honeynet Cyber Security.
From medium.com
General Concept of Cyber Security Honeypot, Honeytoken Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. Most often, honeypots will balance rooting out and collecting. a honeynet is. Honeynet Cyber Security.
From www.youtube.com
What is a Honeypot Cyber Security Tutorial YouTube Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. A honeypot is a security mechanism that creates a virtual trap to lure attackers. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. a honeynet is a. Honeynet Cyber Security.
From www.slideserve.com
PPT Honeypots and PowerPoint Presentation, free download Honeynet Cyber Security By luring adversaries to interact with the decoy. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. A honeypot is a security. Honeynet Cyber Security.
From www.dewaweb.com
Honeypot Server Untuk Mengelabui Serangan Hacker Honeynet Cyber Security in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. Most often, honeypots will balance rooting out and collecting. honeypots in cybersecurity have two primary uses, research and production. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. An intentionally compromised computer system allows. Honeynet Cyber Security.
From chuvakin.org
Status Data Honeynet Cyber Security a honeynet is a network set up to catch a hacker's attention and study how they move through your system. Most often, honeypots will balance rooting out and collecting. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. A honeypot is a security mechanism that creates a virtual trap to lure attackers. An. Honeynet Cyber Security.
From www.youtube.com
Trap Hackers Honeypot Deception Technology Cyber Honeynet Cyber Security An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of. Honeynet Cyber Security.
From cyvatar.ai
What is a honeypot? How does it secure your SMB? CYVATAR.AI Honeynet Cyber Security honeypots in cybersecurity have two primary uses, research and production. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. By luring adversaries to interact with the decoy. Most often, honeypots will balance rooting out and collecting. in cybersecurity, cyber honeypots often work fundamentally in the same way as. Honeynet Cyber Security.
From www.youtube.com
Teknix 53 Based Threat Intelligence (Cyber Security Series Honeynet Cyber Security a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. By luring adversaries to interact with the decoy. a honeynet is a network set up to catch a hacker's attention. Honeynet Cyber Security.
From medium.com
and DMZ. The is protected by several… by Geeky much Honeynet Cyber Security a honeynet is a network set up to catch a hacker's attention and study how they move through your system. honeypots in cybersecurity have two primary uses, research and production. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. By luring adversaries to interact with the decoy. They’re. Honeynet Cyber Security.
From www.honeynet.or.id
inar & Cyber Security Nasional 2022 Bali_ Instiki IHP Honeynet Cyber Security By luring adversaries to interact with the decoy. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. Cyber honeypots are baited, virtual traps for threat actors. Most often, honeypots will balance rooting out and collecting. An intentionally compromised computer system allows attackers to. Honeynet Cyber Security.
From www.youtube.com
Project Cyber Forensics B Tech JNTUH A K A S H Honeynet Cyber Security Most often, honeypots will balance rooting out and collecting. By luring adversaries to interact with the decoy. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. A honeypot is a security mechanism that creates a virtual trap to lure attackers. Cyber honeypots are baited, virtual traps for threat actors. An intentionally compromised computer system. Honeynet Cyber Security.
From www.researchgate.net
(PDF) A Firewall Scheme with Initiative Security Strategies Honeynet Cyber Security A honeypot is a security mechanism that creates a virtual trap to lure attackers. honeypots in cybersecurity have two primary uses, research and production. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. in cybersecurity, cyber honeypots often work fundamentally in. Honeynet Cyber Security.
From www.studocu.com
security systems for shielding intrusions in networks Ijertv Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. A honeypot is a security mechanism that creates a virtual trap to lure attackers. By luring adversaries to interact with the decoy. a honeynet is a network set up with intentional vulnerabilities hosted. Honeynet Cyber Security.
From www.slideserve.com
PPT Wireless Network Security PowerPoint Presentation, free download Honeynet Cyber Security An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. honeypots in cybersecurity have two primary uses, research and production. Most often, honeypots will balance rooting out and collecting. They’re. Honeynet Cyber Security.
From sectigostore.com
What Is a Honeypot in Network Security? Definition, Types & Uses Honeynet Cyber Security A honeypot is a security mechanism that creates a virtual trap to lure attackers. By luring adversaries to interact with the decoy. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an. Honeynet Cyber Security.
From studylib.net
and Honeypots Companion Technology for Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. honeypots in cybersecurity have two primary uses, research and production. Most often, honeypots will balance rooting out and collecting. By luring adversaries to interact with the decoy. a honeynet is a network. Honeynet Cyber Security.
From www.orangsiber.com
Based Cyber Threat Intelligence Orang Siber Honeynet Cyber Security in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. Most often, honeypots will balance rooting out and collecting. A honeypot is a security mechanism that creates a virtual trap to lure attackers. Cyber honeypots are. Honeynet Cyber Security.
From www.researchgate.net
(PDF) Using data and a time series to predict the number of Honeynet Cyber Security a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. honeypots in cybersecurity have two primary uses, research and production. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. Most often, honeypots will balance rooting out and collecting. Cyber honeypots. Honeynet Cyber Security.
From www.securityartwork.es
UML Security Art Work Honeynet Cyber Security a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s. Honeynet Cyber Security.
From www.slideshare.net
2019 0910 seminar cyber security acad csirt universitas Honeynet Cyber Security They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. Cyber honeypots are baited, virtual traps for threat actors. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. a honeynet is. Honeynet Cyber Security.
From www.researchgate.net
(PDF) Cybersecurity and Network Forensics Analysis of Malicious Honeynet Cyber Security a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. By luring adversaries to interact with the decoy. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. in cybersecurity, cyber honeypots often work. Honeynet Cyber Security.
From medium.com
Building a SOC + in Azure (Live Traffic) by Jose's Cyber Honeynet Cyber Security a honeynet is a network set up to catch a hacker's attention and study how they move through your system. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. a honeynet is a. Honeynet Cyber Security.
From sectigostore.com
What Is a Honeypot in Network Security? Definition, Types & Uses Honeynet Cyber Security Cyber honeypots are baited, virtual traps for threat actors. a honeynet is a network set up to catch a hacker's attention and study how they move through your system. By luring adversaries to interact with the decoy. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. An intentionally compromised. Honeynet Cyber Security.
From www.slideserve.com
PPT Evaluating the Feasibility of a Pakistan Node PowerPoint Honeynet Cyber Security honeypots in cybersecurity have two primary uses, research and production. Most often, honeypots will balance rooting out and collecting. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s. Honeynet Cyber Security.
From medium.com
General Concept of Cyber Security Honeypot, Honeytoken Honeynet Cyber Security By luring adversaries to interact with the decoy. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. A honeypot is a security mechanism. Honeynet Cyber Security.
From www.ijcnis.org
Retracted Paper Implementation in Cyber Security Attack Honeynet Cyber Security Most often, honeypots will balance rooting out and collecting. They’re decoys designed to mimic targets for attackers and can be used as a reconnaissance tool to assess an attacker’s techniques, capabilities, and levels of sophistication. A honeypot is a security mechanism that creates a virtual trap to lure attackers. By luring adversaries to interact with the decoy. a honeynet. Honeynet Cyber Security.
From cioinfluence.com
Cybersecurity Experts from GoSecure Will Reveal Unprecedented Insights Honeynet Cyber Security Cyber honeypots are baited, virtual traps for threat actors. a honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. a honeynet is a network of decoy systems designed to mimic a real network and attract potential attackers. Most often, honeypots will balance rooting out and collecting. a honeynet is. Honeynet Cyber Security.
From www.lupovis.io
vs Honeypots Lupovis Honeynet Cyber Security By luring adversaries to interact with the decoy. Cyber honeypots are baited, virtual traps for threat actors. in cybersecurity, cyber honeypots often work fundamentally in the same way as traditional honeypots. Most often, honeypots will balance rooting out and collecting. A honeypot is a security mechanism that creates a virtual trap to lure attackers. honeypots in cybersecurity have. Honeynet Cyber Security.