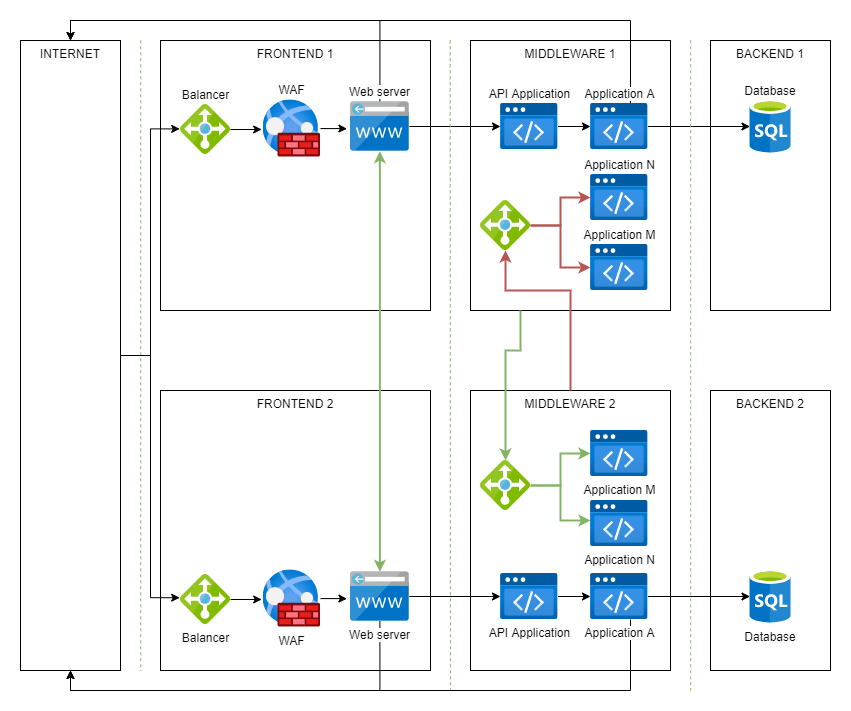
Acl Network Segmentation . This enables administrators to ensure that, unless the proper. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Network segmentation is dividing a computer network into smaller subnetworks or segments. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Each segment can act as its own small network, which. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. In this article, we will explore and compare vrf and acl to. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Learn what a network access control list (acl) is, its benefits, and the different types. One of the most common is network segmentation, where acls are.
from cheatsheetseries.owasp.org
Network segmentation is dividing a computer network into smaller subnetworks or segments. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. In this article, we will explore and compare vrf and acl to. Learn what a network access control list (acl) is, its benefits, and the different types. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Each segment can act as its own small network, which. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). One of the most common is network segmentation, where acls are. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality.
Network Segmentation OWASP Cheat Sheet Series
Acl Network Segmentation Network segmentation is dividing a computer network into smaller subnetworks or segments. One of the most common is network segmentation, where acls are. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Learn what a network access control list (acl) is, its benefits, and the different types. This enables administrators to ensure that, unless the proper. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Each segment can act as its own small network, which. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. In this article, we will explore and compare vrf and acl to. Network segmentation is dividing a computer network into smaller subnetworks or segments. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface.
From www.bkns.vn
Segment là gì? Những kiến thức bạn cần biết về Segment BKNS Acl Network Segmentation One of the most common is network segmentation, where acls are. This enables administrators to ensure that, unless the proper. Network segmentation is dividing a computer network into smaller subnetworks or segments. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Network segmentation can be based on physical separation,. Acl Network Segmentation.
From cheatsheetseries.owasp.org
Network Segmentation OWASP Cheat Sheet Series Acl Network Segmentation Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. In this article, we will explore and compare vrf and acl to. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Network segmentation can be based on physical separation, logical separation. Acl Network Segmentation.
From www.einnews.com
Network Segmentation in 2024 6 Benefits & 8 Best Practices EIN Presswire Acl Network Segmentation There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). This enables administrators to ensure that, unless the proper. Each segment can act as its own small network, which. Learn what a network. Acl Network Segmentation.
From www.cyres-consulting.com
Access control, secure communication, network segmentation and isolation Acl Network Segmentation This enables administrators to ensure that, unless the proper. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. One of the most common is network segmentation, where acls are. Network segmentation is dividing a computer network. Acl Network Segmentation.
From networkustad.com
How to Configure Extended ACLs Exclusive Explanation » NetworkUstad Acl Network Segmentation One of the most common is network segmentation, where acls are. Learn what a network access control list (acl) is, its benefits, and the different types. In this article, we will explore and compare vrf and acl to. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). There are several practical. Acl Network Segmentation.
From www.alibabacloud.com
Overview of network ACLs Virtual Private Cloud Alibaba Cloud Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. In this article, we will explore and compare vrf and acl to. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation. Acl Network Segmentation.
From www.pinterest.co.kr
Cisco Drives IntentBased Networking Forward with MultiLevel Acl Network Segmentation Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Network segmentation is dividing a computer network into smaller subnetworks or segments. Each segment can act as its own small network, which. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). There are several practical use cases. Acl Network Segmentation.
From www.enterprisenetworkingplanet.com
9 Network Segmentation Best Practices to Improve Security Acl Network Segmentation Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Network segmentation can be based on physical separation,. Acl Network Segmentation.
From www.annexustech.com
What Is Network Segmentation, and Why Should You Care? annexustech Acl Network Segmentation One of the most common is network segmentation, where acls are. This enables administrators to ensure that, unless the proper. Learn what a network access control list (acl) is, its benefits, and the different types. Each segment can act as its own small network, which. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access. Acl Network Segmentation.
From netcraftsmen.com
Managing SDAccess Segmentation NetCraftsmen, a BlueAlly Company Acl Network Segmentation Each segment can act as its own small network, which. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. One of the most common is network segmentation, where acls are. This enables administrators to ensure that, unless the proper. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control. Acl Network Segmentation.
From ransomware.org
Ransomware and Active Directory How to protect your network Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. Each segment can act as its own small network, which. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Network segmentation is dividing a computer network into smaller subnetworks or segments. This enables administrators to ensure. Acl Network Segmentation.
From www.youtube.com
TCP Established ACL Advanced ACLs Part 2 YouTube Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. Network segmentation is dividing a computer network into smaller subnetworks or segments. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks.. Acl Network Segmentation.
From www.deepsonline.com
Network micro segmentation Acl Network Segmentation Network segmentation is dividing a computer network into smaller subnetworks or segments. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). This enables administrators to ensure that, unless the proper. Learn what a network. Acl Network Segmentation.
From www.networkingsignal.com
What Are Extended ACLs And How To Configure It? Acl Network Segmentation Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Network segmentation is dividing a computer network into smaller subnetworks or segments. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Firewalls, access control lists (acls) and virtual lans (vlans). Acl Network Segmentation.
From medium.com
Does NAC Strengthen your Security Posture for Network Segmentation Acl Network Segmentation Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. In this article, we will explore and compare vrf and acl to. Learn what a network access control list (acl) is, its benefits, and the different types. Network. Acl Network Segmentation.
From www.tditechnologies.com
Network Segmentation Best Practices TDi Acl Network Segmentation Each segment can act as its own small network, which. Learn what a network access control list (acl) is, its benefits, and the different types. This enables administrators to ensure that, unless the proper. Network segmentation is dividing a computer network into smaller subnetworks or segments. There are several practical use cases where a network access control list (acl) proves. Acl Network Segmentation.
From aclanthology.org
A Joint Model for Document Segmentation and Segment Labeling ACL Acl Network Segmentation This enables administrators to ensure that, unless the proper. Learn what a network access control list (acl) is, its benefits, and the different types. Each segment can act as its own small network, which. One of the most common is network segmentation, where acls are. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. In. Acl Network Segmentation.
From www.zenarmor.com
What Is Network Segmentation? Introduction to Network Segmentation Acl Network Segmentation There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). One of the most common is. Acl Network Segmentation.
From edge-cloud.github.io
Securing your AWS networks Edge Cloud Acl Network Segmentation Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. This enables administrators to ensure that, unless the proper. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Network segmentation can be based on physical separation, logical separation or both, depending. Acl Network Segmentation.
From blog.matrixpost.net
Virtual Local Area Networks (VLANs) Basics about Network Segmentation Acl Network Segmentation This enables administrators to ensure that, unless the proper. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance.. Acl Network Segmentation.
From blog.matrixpost.net
Virtual Local Area Networks (VLANs) Basics about Network Segmentation Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. This enables administrators to ensure that, unless the proper. In this article, we will explore and compare vrf and acl to. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Network segmentation is dividing. Acl Network Segmentation.
From www.varonis.com
What Is Network Segmentation? Acl Network Segmentation This enables administrators to ensure that, unless the proper. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. In this article, we will explore and compare vrf and acl to. One of the most common is. Acl Network Segmentation.
From blogs.cisco.com
Cisco Drives IntentBased Networking Forward with MultiLevel Acl Network Segmentation Network segmentation is dividing a computer network into smaller subnetworks or segments. One of the most common is network segmentation, where acls are. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl).. Acl Network Segmentation.
From zeronetworks.com
Network segmentation All you need to know about its benefits Acl Network Segmentation There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). One of the most common is. Acl Network Segmentation.
From study-ccna.com
Configuring Extended ACLs (Access Lists) Study CCNA Acl Network Segmentation Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Acls can be used to segment networks, isolating critical systems. Acl Network Segmentation.
From aclanthology.org
A Unified Neural Architecture for Joint Dialog Act Segmentation and Acl Network Segmentation Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Each segment can act as its own small network, which. In this article, we will explore and compare vrf and acl to. Firewalls,. Acl Network Segmentation.
From www.theasciiconstruct.com
Cisco SDA and Security Part II microsegmentation in SDA The ASCII Acl Network Segmentation Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. One of the most common is network segmentation, where acls are. Each segment can act as its own small network, which. In this article, we will explore and compare vrf and acl to. Network segmentation is dividing a computer network into smaller subnetworks or segments. Acls. Acl Network Segmentation.
From www.securityandit.com
Best practices for network segmentation Network Security Protocols Acl Network Segmentation Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. One of the most common is network segmentation, where acls are. Network segmentation is dividing a computer network into smaller subnetworks or segments. Learn what a network access. Acl Network Segmentation.
From research.aimultiple.com
Network Segmentation in 2024 6 Benefits & 8 Best Practices Acl Network Segmentation One of the most common is network segmentation, where acls are. Each segment can act as its own small network, which. In this article, we will explore and compare vrf and acl to. This enables administrators to ensure that, unless the proper. Network segmentation is dividing a computer network into smaller subnetworks or segments. Firewalls, access control lists (acls) and. Acl Network Segmentation.
From slideplayer.com
CEBAF Control System Access ppt download Acl Network Segmentation Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access control lists (acl). There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Network segmentation is dividing a computer network into smaller. Acl Network Segmentation.
From xytoki.github.io
ACLs Headscale Acl Network Segmentation Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. Network segmentation is dividing a computer network into smaller subnetworks or segments. Each segment can act as its own small network, which. Acls can be used to segment networks, isolating critical systems or data from less trusted segments, reducing the attack surface. Learn. Acl Network Segmentation.
From medium.com
Multicast vs. Broadcast Unveiling the Differences in Networking by Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. Network segmentation is dividing a computer network into smaller subnetworks or segments. In this article, we will explore and compare vrf and acl to. There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. Network segmentation. Acl Network Segmentation.
From aclanthology.org
A Pointer Network Architecture for Joint Morphological Segmentation and Acl Network Segmentation Learn what a network access control list (acl) is, its benefits, and the different types. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. This enables administrators to ensure that, unless the proper. Network segmentation is dividing a computer network into smaller subnetworks or segments. In this article, we will explore and. Acl Network Segmentation.
From aclanthology.org
SegmentLevel and CategoryOriented Network for KnowledgeBased Acl Network Segmentation In this article, we will explore and compare vrf and acl to. One of the most common is network segmentation, where acls are. Network segmentation can be based on physical separation, logical separation or both, depending on the specific instance. This enables administrators to ensure that, unless the proper. Acls can be used to segment networks, isolating critical systems or. Acl Network Segmentation.
From barisyuksel.com.tr
Extended ACL list for enterprise network system. Download Baris Kaan Acl Network Segmentation There are several practical use cases where a network access control list (acl) proves essential for securing enterprise networks. In this article, we will explore and compare vrf and acl to. Firewalls, access control lists (acls) and virtual lans (vlans) provide the basic segmentation functionality. Two common methods used for network segmentation are virtual routing and forwarding (vrf) and access. Acl Network Segmentation.