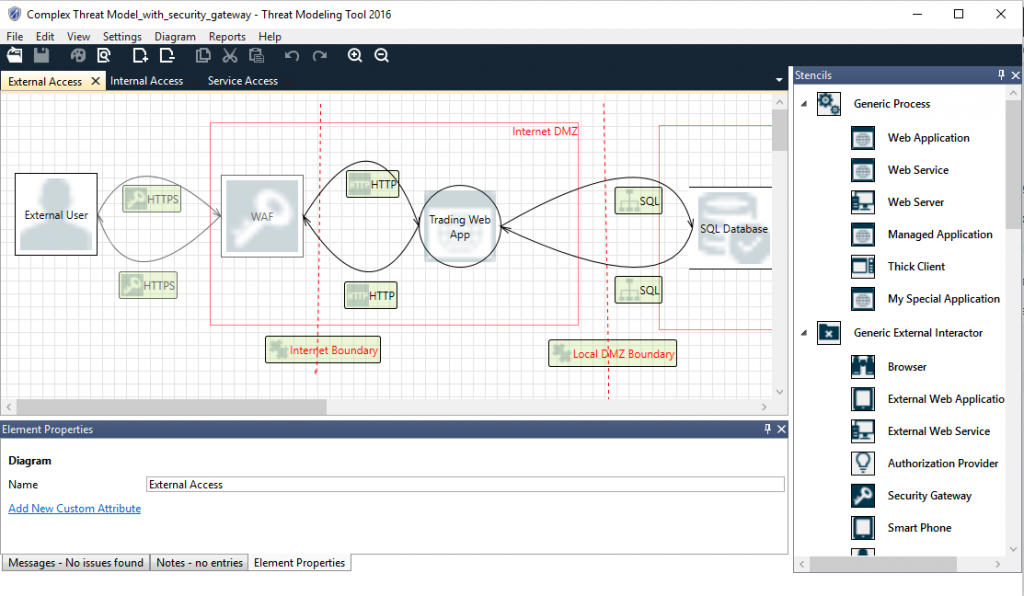
Threat Modeling Tools . It supports various threat modeling methods and provides. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Create a diagram, identify threats, mitigate threats, and validate each. The tool is part of the. It then identifies all points of attack. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Explore different frameworks, methodologies, and tools to. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn how to get started using the threat modeling tool. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to identify and mitigate cybersecurity threats with threat modeling.
from blog.secodis.com
It supports various threat modeling methods and provides. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to identify and mitigate cybersecurity threats with threat modeling. It then identifies all points of attack. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Create a diagram, identify threats, mitigate threats, and validate each. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. The tool is part of the. Learn how to get started using the threat modeling tool.
Microsofts New Threat Modeling Tool Sustainable Application
Threat Modeling Tools It then identifies all points of attack. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to identify and mitigate cybersecurity threats with threat modeling. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. The tool is part of the. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Learn how to get started using the threat modeling tool. It then identifies all points of attack. Explore different frameworks, methodologies, and tools to. It supports various threat modeling methods and provides. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design.
From online.visual-paradigm.com
Free Threat Modeling Tool Threat Modeling Tools Explore different frameworks, methodologies, and tools to. It then identifies all points of attack. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn how to use the microsoft threat modeling tool to. Threat Modeling Tools.
From dzone.com
Threat Modeling Tools Analysis 101 OWASP THREAT DRAGON DZone Threat Modeling Tools Threat modeling examines the design of system operations and how data flows across subsystem boundaries. It supports various threat modeling methods and provides. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. The tool is part of the. Learn how to get started using the threat modeling tool. It then. Threat Modeling Tools.
From www.formacionprofesional.info
Guía rápida Microsoft Threat Modeling Tool Buscar Tutorial Threat Modeling Tools Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to identify and mitigate cybersecurity threats with threat modeling. Explore different frameworks, methodologies, and tools to. It supports various threat modeling methods and provides.. Threat Modeling Tools.
From blogs.microsoft.com
Introducing Microsoft Threat Modeling Tool 2014 Microsoft Secure Blog Threat Modeling Tools Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. It supports various threat modeling methods and provides. Create a diagram, identify threats, mitigate threats, and validate each. The tool is part of the.. Threat Modeling Tools.
From securityxp.com
The Microsoft Threat Modeling Tool (TMT) SecurityXP Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to identify and mitigate cybersecurity threats with threat modeling. The tool is part of the. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn. Threat Modeling Tools.
From rafeeqrehman.com
A Threat Modeling Process to Improve Resiliency of Cybersecurity Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Explore different frameworks, methodologies, and tools to. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Owasp threat dragon is a web or desktop application. Threat Modeling Tools.
From www.geeksforgeeks.org
Microsoft Threat modelling tool 2016 Set 2 Threat Modeling Tools It supports various threat modeling methods and provides. It then identifies all points of attack. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn how to identify and mitigate cybersecurity threats with. Threat Modeling Tools.
From embracethered.com
Threat modeling a machine learning system · Embrace The Red Threat Modeling Tools It then identifies all points of attack. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. The tool. Threat Modeling Tools.
From holisticinfosec.blogspot.com
HolisticInfoSec™ toolsmith Microsoft Threat Modeling Tool 2014 Threat Modeling Tools It supports various threat modeling methods and provides. The tool is part of the. It then identifies all points of attack. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Create a diagram, identify threats,. Threat Modeling Tools.
From www.sunnyvalley.io
Top 10 Threat Modeling Tools sunnyvalley.io Threat Modeling Tools It then identifies all points of attack. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. It supports various threat modeling methods and provides. Learn how to identify and mitigate cybersecurity threats with threat modeling. Create a diagram, identify threats, mitigate threats, and validate each. Threat modeling examines the design. Threat Modeling Tools.
From blog.johner-institute.com
Threat modeling An introduction Threat Modeling Tools Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. It supports various threat modeling methods and provides. Learn. Threat Modeling Tools.
From www.geeksforgeeks.org
Microsoft Threat modelling tool 2016 Set 2 Threat Modeling Tools Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Explore different frameworks, methodologies, and tools to. Learn how to identify and mitigate cybersecurity threats with threat modeling. Learn how to get started using the threat modeling tool. It then identifies all points of attack. It supports various threat modeling methods and provides.. Threat Modeling Tools.
From learn.microsoft.com
概要 Microsoft Threat Modeling Tool Azure Microsoft Learn Threat Modeling Tools It then identifies all points of attack. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to identify and mitigate cybersecurity threats with threat modeling. The tool is part of the. Create a diagram, identify threats, mitigate threats, and validate each. Automated threat modeling tools simplify the process. Threat Modeling Tools.
From info.threatmodeler.com
Threat Modeling Tools Threat Modeling Tools Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. The tool is part of the. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Create a diagram, identify threats, mitigate threats, and validate each. Explore different frameworks, methodologies, and tools. Threat Modeling Tools.
From www.youtube.com
TM04. Microsoft Threat Modeling Tool YouTube Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Explore different frameworks, methodologies, and tools to. Learn how to get started using the threat modeling tool. Learn how to use the microsoft threat modeling tool to identify and mitigate security. Threat Modeling Tools.
From www.microsoft.com
What's New with Microsoft Threat Modeling Tool 2016 Microsoft Threat Modeling Tools Explore different frameworks, methodologies, and tools to. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. It supports various threat modeling methods and provides. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. It then identifies all points of attack. The tool. Threat Modeling Tools.
From www.spiceworks.com
Top 10 Threat Modeling Tools in 2021 Spiceworks Threat Modeling Tools Learn how to identify and mitigate cybersecurity threats with threat modeling. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. It supports various threat modeling methods and provides. The tool is part of the. Explore different frameworks, methodologies, and tools to. Learn how to use the microsoft threat modeling tool. Threat Modeling Tools.
From ashish-shri2015.medium.com
Threat modeling for OAuth 2.0 via Security by Design approach using the Threat Modeling Tools It supports various threat modeling methods and provides. Learn how to get started using the threat modeling tool. Explore different frameworks, methodologies, and tools to. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure. Threat Modeling Tools.
From blog.secodis.com
Microsofts New Threat Modeling Tool Sustainable Application Threat Modeling Tools Explore different frameworks, methodologies, and tools to. It then identifies all points of attack. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to get started using the threat modeling tool. The tool. Threat Modeling Tools.
From www.visual-paradigm.com
Threat Modeling Tool Threat Modeling Tools Learn how to identify and mitigate cybersecurity threats with threat modeling. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. The tool is part of the. It supports various threat modeling methods and provides. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn. Threat Modeling Tools.
From templates.rjuuc.edu.np
Threat Model Template Threat Modeling Tools It supports various threat modeling methods and provides. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to identify and mitigate cybersecurity threats with threat modeling. Automated threat modeling tools simplify the process of identifying threats aimed at. Threat Modeling Tools.
From www.dts-solution.com
Threat Modelling Network and Cyber Security Solutions and Services Threat Modeling Tools It then identifies all points of attack. Learn how to get started using the threat modeling tool. It supports various threat modeling methods and provides. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to use the microsoft threat modeling. Threat Modeling Tools.
From online.visual-paradigm.com
Free Threat Modeling Tool Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Learn how to get started using the threat modeling tool. Explore different frameworks, methodologies, and tools to. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure. Threat Modeling Tools.
From learn.microsoft.com
Microsoft Threat Modeling Tool 功能概述 Azure Microsoft Learn Threat Modeling Tools It then identifies all points of attack. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to get started using the threat modeling tool. It supports various threat modeling methods and provides. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to use the microsoft threat modeling tool to. Threat Modeling Tools.
From threat-modeling.com
Threat Modeling Tool Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Learn how to identify and mitigate cybersecurity threats with threat modeling. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Threat modeling examines. Threat Modeling Tools.
From www.acte.in
What is Threat Modeling? All you need to know [OverView] Threat Modeling Tools Learn how to identify and mitigate cybersecurity threats with threat modeling. Create a diagram, identify threats, mitigate threats, and validate each. It supports various threat modeling methods and provides. The tool is part of the. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Threat modeling examines the design of system operations. Threat Modeling Tools.
From mouseprice.weebly.com
Sdl threat modeling tool v3 mouseprice Threat Modeling Tools Learn how to get started using the threat modeling tool. It then identifies all points of attack. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to identify and mitigate cybersecurity threats with threat modeling. Automated threat modeling. Threat Modeling Tools.
From dzone.com
Threat Modeling Tools Analysis 101 OWASP THREAT DRAGON DZone Threat Modeling Tools The tool is part of the. Explore different frameworks, methodologies, and tools to. Learn how to identify and mitigate cybersecurity threats with threat modeling. It then identifies all points of attack. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to get started using the threat modeling tool.. Threat Modeling Tools.
From dzone.com
Threat Modelling Tools Analysis 101 DZone Threat Modeling Tools Learn how to identify and mitigate cybersecurity threats with threat modeling. It then identifies all points of attack. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Create a diagram, identify threats, mitigate threats, and validate each. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for. Threat Modeling Tools.
From threat-modeling.com
Threat Modeling Tool Threat Modeling Tools The tool is part of the. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Learn how to. Threat Modeling Tools.
From www.formacionprofesional.info
Guía rápida Microsoft Threat Modeling Tool Buscar Tutorial Threat Modeling Tools Explore different frameworks, methodologies, and tools to. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. It then identifies all points of attack. The tool is part of the. Learn how to use. Threat Modeling Tools.
From learn.microsoft.com
概要 Microsoft Threat Modeling Tool Azure Microsoft Learn Threat Modeling Tools Create a diagram, identify threats, mitigate threats, and validate each. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. Learn how to get started using the threat modeling tool. It then identifies all points of. Threat Modeling Tools.
From learn.microsoft.com
概要 Microsoft Threat Modeling Tool Azure Microsoft Learn Threat Modeling Tools Owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Learn how to identify and mitigate cybersecurity threats with threat modeling. Learn how to use the microsoft threat modeling tool to identify and mitigate security threats. Threat Modeling Tools.
From bartwullems.blogspot.com
Microsoft Threat Modeling Tool Threat Modeling Tools Learn how to use the microsoft threat modeling tool to identify and mitigate security threats in your application design. It then identifies all points of attack. Explore different frameworks, methodologies, and tools to. Automated threat modeling tools simplify the process of identifying threats aimed at organizations and information systems, as. Create a diagram, identify threats, mitigate threats, and validate each.. Threat Modeling Tools.
From holisticinfosec.blogspot.com
HolisticInfoSec™ toolsmith Microsoft Threat Modeling Tool 2014 Threat Modeling Tools Explore different frameworks, methodologies, and tools to. The tool is part of the. Learn how to identify and mitigate cybersecurity threats with threat modeling. Threat modeling examines the design of system operations and how data flows across subsystem boundaries. Create a diagram, identify threats, mitigate threats, and validate each. It then identifies all points of attack. Learn how to get. Threat Modeling Tools.