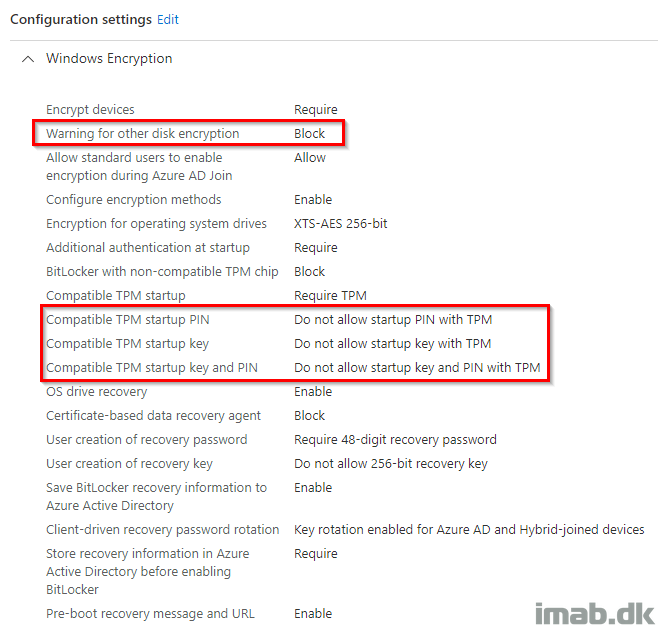
Endpoint Security Bitlocker . View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Use a device with tpm for maximum. Best practices for configuring bitlocker for intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Enabling bitlocker and allowing user interaction on a device with or without tpm. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune.
from laptrinhx.com
Here are best practices and recommended processes for using bitlocker with intune. Best practices for configuring bitlocker for intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Enabling bitlocker and allowing user interaction on a device with or without tpm. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Use a device with tpm for maximum. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices.
Silently enable BitLocker on nonModern Standby capable devices using
Endpoint Security Bitlocker Best practices for configuring bitlocker for intune. Best practices for configuring bitlocker for intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Here are best practices and recommended processes for using bitlocker with intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Use a device with tpm for maximum. Enabling bitlocker and allowing user interaction on a device with or without tpm.
From techlabs.blog
Silently enable BitLocker using a Disk Encryption Policy with Microsoft Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template. Endpoint Security Bitlocker.
From petri.com
Best Practices for Deploying BitLocker with Intune Petri IT Knowledgebase Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Enabling bitlocker and allowing user interaction on a device with or without tpm. Best practices for configuring bitlocker for intune. Use. Endpoint Security Bitlocker.
From www.tpsearchtool.com
Configure Endpoint Protection Bitlocker With Intune On Windows 10 Images Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. Use a device with tpm for maximum. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Endpoint security profiles are the newer type of intune profile, with the intent being you can. Endpoint Security Bitlocker.
From thewindowsupdate.com
Configuring BitLocker encryption with Endpoint security Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. You can use either the bitlocker profile from. Endpoint Security Bitlocker.
From www.manageengine.com
BitLocker Prerequisites ManageEngine Endpoint Central Endpoint Security Bitlocker View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Best practices for configuring bitlocker for intune. Here are best practices and recommended processes for using bitlocker with intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. Use a device. Endpoint Security Bitlocker.
From www.reddit.com
BitLocker Silent Encryption Endpoint security r/Intune Endpoint Security Bitlocker Use a device with tpm for maximum. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Learn how microsoft endpoint manager can help you. Endpoint Security Bitlocker.
From khogenmaibamblog.wordpress.com
EndPoint Protection Bitlocker integration with SCCM Microsoft Endpoint Security Bitlocker Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Best practices for configuring bitlocker for intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Use a device with tpm for maximum. You can use either the. Endpoint Security Bitlocker.
From www.reddit.com
Endpoint Security BitLocker profile changed format? r/Intune Endpoint Security Bitlocker Use a device with tpm for maximum. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Enabling bitlocker and allowing user interaction on a device with or without tpm. Here are best practices and recommended processes for using bitlocker with intune. Learn how microsoft endpoint manager can help you. Endpoint Security Bitlocker.
From petri.com
Best Practices for Deploying BitLocker with Intune Petri IT Knowledgebase Endpoint Security Bitlocker Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Best practices for configuring bitlocker for intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Here are best practices and recommended processes for using bitlocker with intune. View the settings you can configure in. Endpoint Security Bitlocker.
From laptrinhx.com
Silently enable BitLocker on nonModern Standby capable devices using Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Enabling bitlocker and allowing user interaction on a device with or without tpm. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from.. Endpoint Security Bitlocker.
From vigilantemichele.wordpress.com
BitLocker Silent Configuration via Microsoft Endpoint Manager Michele Endpoint Security Bitlocker Best practices for configuring bitlocker for intune. Use a device with tpm for maximum. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Managing BitLocker in the enterprise using Microsoft Endpoint Manager Endpoint Security Bitlocker Use a device with tpm for maximum. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can configure in profiles for disk encryption policy. Endpoint Security Bitlocker.
From www.reddit.com
New Interface for Bitlocker Endpoint Security Disk Encryption Profile Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune. Best practices for configuring bitlocker for intune.. Endpoint Security Bitlocker.
From www.tpsearchtool.com
Configure Endpoint Protection Bitlocker With Intune On Windows 10 Images Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. You can use either the bitlocker profile from. Endpoint Security Bitlocker.
From www.anoopcnair.com
New BitLocker Disk Encryption Policy For Intune Endpoint Security HTMD Blog Endpoint Security Bitlocker Use a device with tpm for maximum. Here are best practices and recommended processes for using bitlocker with intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Best practices for configuring bitlocker for intune. Endpoint security profiles are the newer type. Endpoint Security Bitlocker.
From khogenmaibamblog.wordpress.com
EndPoint Protection Bitlocker integration with SCCM Microsoft Endpoint Security Bitlocker Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune. Best practices for configuring bitlocker for intune. Use a device with tpm for maximum. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security. Endpoint Security Bitlocker.
From www.drware.com
Managing BitLocker with Microsoft Endpoint Manager Dr. Ware Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Best practices for configuring bitlocker for intune. Learn how microsoft. Endpoint Security Bitlocker.
From khogenmaibamblog.wordpress.com
EndPoint Protection Bitlocker integration with SCCM Microsoft Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. You can use either the bitlocker profile from an. Endpoint Security Bitlocker.
From www.manageengine.com
BitLocker Prerequisites ManageEngine Endpoint Central Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Use a device with tpm for maximum. Best practices for configuring bitlocker for intune. Learn how microsoft endpoint manager can help you manage. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Managing BitLocker in the enterprise using Microsoft Endpoint Manager Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Best practices for configuring bitlocker for intune. Use a device with tpm for maximum.. Endpoint Security Bitlocker.
From www.manageengine.com
Bitlocker Policy Creation ManageEngine Endpoint Central Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Best practices for configuring bitlocker for intune. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Managing BitLocker with Microsoft Endpoint Manager Microsoft Tech Endpoint Security Bitlocker View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Configuring BitLocker encryption with Endpoint security Microsoft Endpoint Security Bitlocker Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part. Endpoint Security Bitlocker.
From khogenmaibamblog.wordpress.com
EndPoint Protection Bitlocker integration with SCCM Microsoft Endpoint Security Bitlocker View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Use a device with tpm for maximum. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune. You can. Endpoint Security Bitlocker.
From petri.com
Best Practices for Deploying BitLocker with Intune Petri IT Knowledgebase Endpoint Security Bitlocker Enabling bitlocker and allowing user interaction on a device with or without tpm. Use a device with tpm for maximum. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here. Endpoint Security Bitlocker.
From www.azure365pro.com
Disk Encryption BitLocker Policy in Intune Endpoint Security Endpoint Security Bitlocker Use a device with tpm for maximum. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can configure. Endpoint Security Bitlocker.
From techlabs.blog
Silently enable BitLocker using a Disk Encryption Policy with Microsoft Endpoint Security Bitlocker Best practices for configuring bitlocker for intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. You. Endpoint Security Bitlocker.
From www.manageengine.com
BitLocker Prerequisites ManageEngine Endpoint Central Endpoint Security Bitlocker Enabling bitlocker and allowing user interaction on a device with or without tpm. Use a device with tpm for maximum. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Best practices for configuring bitlocker for intune. View the settings you can configure. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Configuring BitLocker encryption with Endpoint security Microsoft Endpoint Security Bitlocker Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Learn how microsoft endpoint manager can help you manage bitlocker on your windows. Endpoint Security Bitlocker.
From www.anoopcnair.com
Learn How To Deploy BitLocker Using Intune HTMD Blog Endpoint Security Bitlocker Best practices for configuring bitlocker for intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Use a device with tpm for. Endpoint Security Bitlocker.
From www.42gears.com
The Benefits of BitLocker that Windows 11 to enhance data security Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. You can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from. Best practices for configuring bitlocker for intune. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Enabling bitlocker and allowing user interaction on. Endpoint Security Bitlocker.
From techlabs.blog
Silently enable BitLocker using a Disk Encryption Policy with Microsoft Endpoint Security Bitlocker Use a device with tpm for maximum. Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Here are best practices and recommended processes for using bitlocker with intune. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Endpoint security. Endpoint Security Bitlocker.
From petri.com
Best Practices for Deploying BitLocker with Intune Petri IT Knowledgebase Endpoint Security Bitlocker Learn how microsoft endpoint manager can help you manage bitlocker on your windows devices. Best practices for configuring bitlocker for intune. Use a device with tpm for maximum. Here are best practices and recommended processes for using bitlocker with intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. You can use either the bitlocker profile. Endpoint Security Bitlocker.
From narodnatribuna.info
Windows 11 Bitlocker How To Setup Bitlocker Windows 11 Endpoint Security Bitlocker Here are best practices and recommended processes for using bitlocker with intune. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules in a dedicated part of mem. Best practices for configuring bitlocker for intune. Enabling bitlocker and allowing user interaction on a device with or without tpm. Learn. Endpoint Security Bitlocker.
From techcommunity.microsoft.com
Managing BitLocker with Microsoft Endpoint Manager Microsoft Endpoint Security Bitlocker Use a device with tpm for maximum. Best practices for configuring bitlocker for intune. View the settings you can configure in profiles for disk encryption policy in the endpoint security node of intune as part of an endpoint security. Endpoint security profiles are the newer type of intune profile, with the intent being you can manage all your security rules. Endpoint Security Bitlocker.