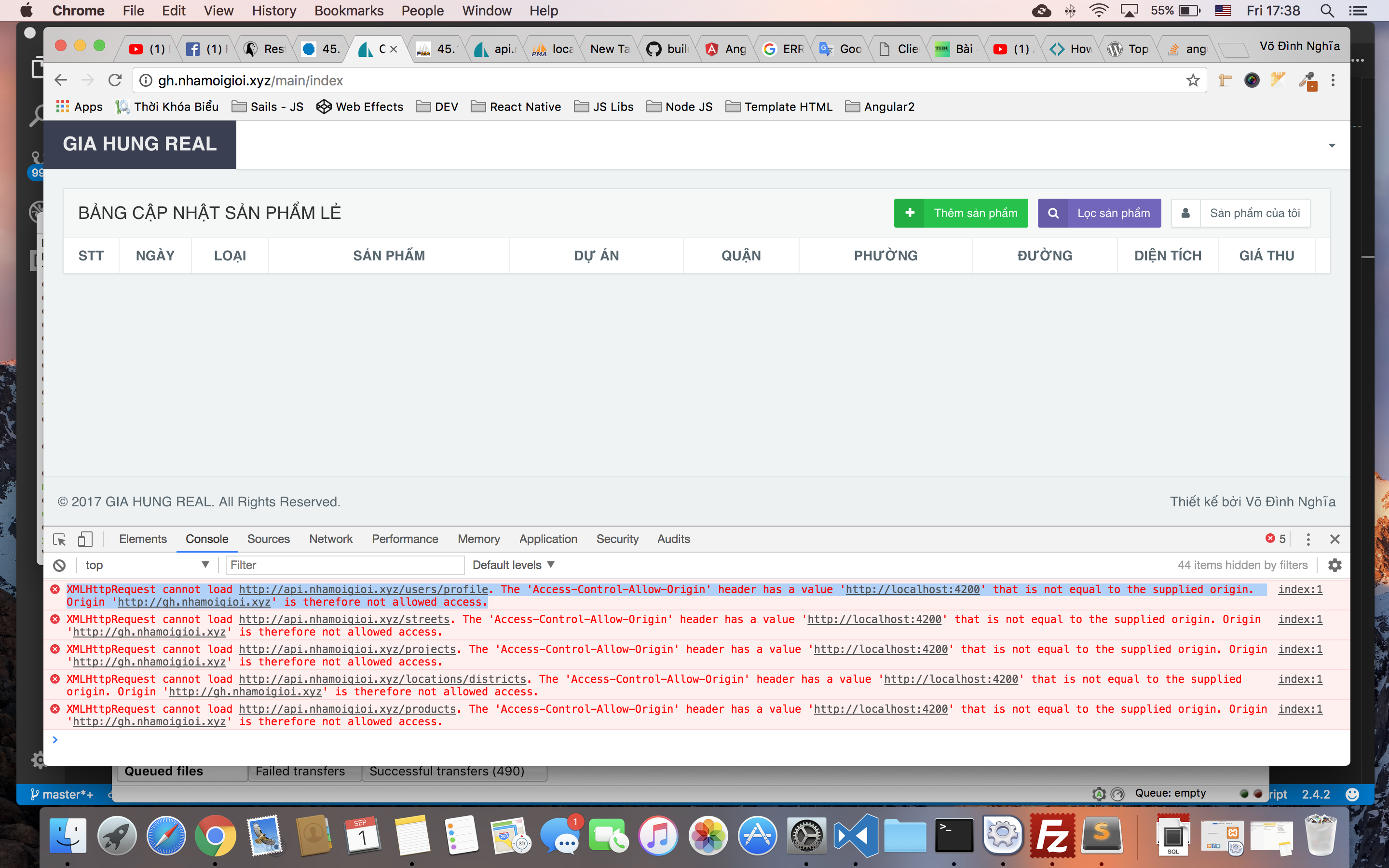
From www.youtube.com
How To Fix CORS Access Control Allow Origin Cross Domain js jQuery Use Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From hxeglyxjz.blob.core.windows.net
Javascript AccessControlAllowOrigin Example at Joseph Smart blog Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From www.youtube.com
access controll allow origin on IIS YouTube Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From keycloak.discourse.group
AccessControlAllowOrigin header missing Securing applications Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From www.youtube.com
Solving "AccessControlAllowOrigin" in localhost NodeJS + Express Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From blog.csdn.net
Java Demo示例:Springboot解决AccessControlAllowOrigin跨域问题、浏览器同源策略详解 Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From www.vrogue.co
The Access Control Allow Origin Header Explained With vrogue.co Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From www.tenable.com
Understanding CrossOrigin Resource Sharing Vulnerabilities Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From crunchify.com
How to fix AccessControlAllowOrigin (CORS origin) Issue for your Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From www.youtube.com
How to Enable CORS and Fix AccessControlAllowOrigin in Core Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From www.holisticseo.digital
AccessControlAllowOrigin HTTP Header Syntax, Directive, Examples Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From 9to5answer.com
[Solved] AccessControlAllowOrigin header contains the 9to5Answer Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From stackoverflow.com
CORS Missing 'AccessControlAllowOrigin' Stack Overflow Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From blog.csdn.net
Allow CORS AccessControlAllowOrigin插件使用CSDN博客 Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From 9to5answer.com
[Solved] AccessControlAllowOrigin syntax 9to5Answer Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From blog.csdn.net
解决The ‘AccessControlAllowOrigin‘ header contains multiple values的问题 Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From www.youtube.com
AccessControlAllowOrigin Response Header Explained (CORS) HTTP/ Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From copyprogramming.com
AccessControlAllowOrigin Issue in SOAP Request A Javascript Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From giooibsaq.blob.core.windows.net
AccessControlAllowOrigin In Angular at Emily Corn blog Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From fyohtkwbk.blob.core.windows.net
AccessControlAllowOrigin Que Es at Vanessa Henry blog Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From www.vrogue.co
How To Fix Access Control Allow Origin Cors Origin Is vrogue.co Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From kakechimaru.com
画像のみにAccessControlAllowOriginを設定する方法 Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From stackoverflow.com
apache Allow AccessControlAllowOrigin Stack Overflow Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From blog.opencagedata.com
New feature setting the accesscontrolalloworigin HTTP header Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From fyohtkwbk.blob.core.windows.net
AccessControlAllowOrigin Que Es at Vanessa Henry blog Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From hilodo.weebly.com
Access control allow origin' header hilodo Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From 9to5answer.com
[Solved] How to implement "AccessControlAllowOrigin" 9to5Answer Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From www.youtube.com
The 'AccessControlAllowOrigin' header contains multiple values Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From 9to5answer.com
[Solved] How to set accesscontrolalloworigin in 9to5Answer Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From fyohtkwbk.blob.core.windows.net
AccessControlAllowOrigin Que Es at Vanessa Henry blog Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From manage.accuwebhosting.com
How to setup AccessControlAllowOrigin for IIS 8 in web config Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Access-Control-Allow-Origin * Vulnerability.
From www.vrogue.co
How To Fix Access Control Allow Origin Cors Origin Is vrogue.co Access-Control-Allow-Origin * Vulnerability Verify that the origin validation is. Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Access-Control-Allow-Origin * Vulnerability.
From www.w3docs.com
How Does the AccessControlAllowOrigin Header Work Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From www.programmingcube.com
How Does the AccessControlAllowOrigin Header Work in JavaScript Access-Control-Allow-Origin * Vulnerability * is totally safe to add to any resource, unless that resource contains private data. Vulnerabilities arising from cors configuration issues. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.
From giouolylk.blob.core.windows.net
AccessControlAllowOrigin Fix at Steven Leet blog Access-Control-Allow-Origin * Vulnerability Vulnerabilities arising from cors configuration issues. * is totally safe to add to any resource, unless that resource contains private data. Verify that the origin validation is. Access-Control-Allow-Origin * Vulnerability.