Keycloak Kubernetes Authentication . A lot of concerns are left to the user to configure and implement: From exposing the keycloak api. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. Strictly running keycloak in kubernetes won’t make your platform secure. Use keycloak to authenticate and authorize users.
from www.dirigible.io
In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. Strictly running keycloak in kubernetes won’t make your platform secure. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Use keycloak to authenticate and authorize users. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. A lot of concerns are left to the user to configure and implement: In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. From exposing the keycloak api.
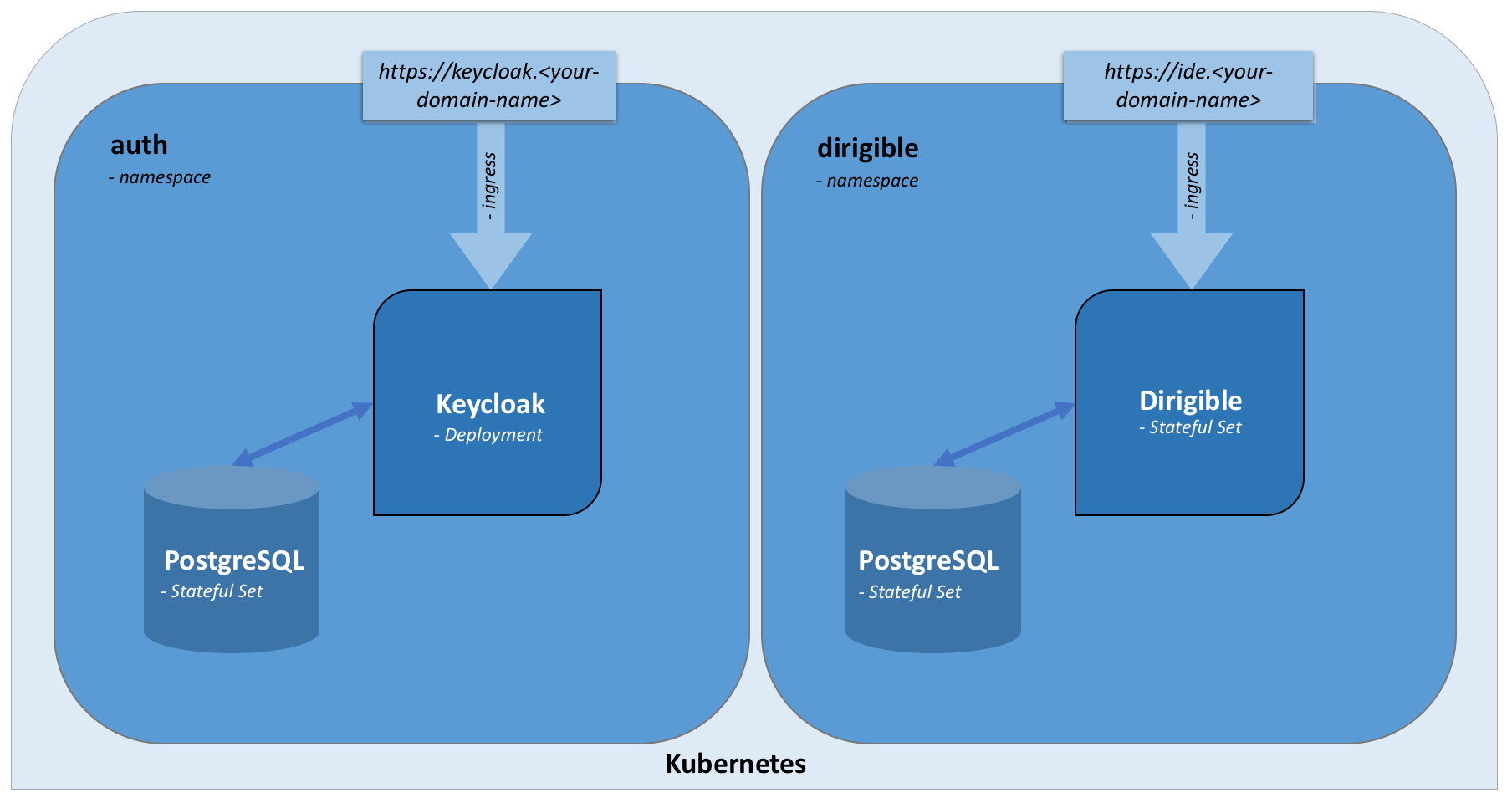
Keycloak, PostgreSQL & Dirigible Eclipse Dirigible Blog
Keycloak Kubernetes Authentication From exposing the keycloak api. Use keycloak to authenticate and authorize users. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. A lot of concerns are left to the user to configure and implement: In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Strictly running keycloak in kubernetes won’t make your platform secure. From exposing the keycloak api. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different.
From medium.com
Authentication with Keycloak OpenID Connect Part 1 by Zufar Dhiyaulhaq Medium Keycloak Kubernetes Authentication A lot of concerns are left to the user to configure and implement: In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant. Keycloak Kubernetes Authentication.
From www.redhat.com
Adding authentication to your applications with Keycloak Keycloak Kubernetes Authentication In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. From exposing the keycloak api. A lot of concerns are left to the user to configure and implement: Use keycloak to authenticate and authorize users. Strictly running keycloak in kubernetes won’t make your platform secure. In this post. Keycloak Kubernetes Authentication.
From openunison.github.io
Keycloak Authentication and SSO OpenUnison Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In this article, i will walk you. Keycloak Kubernetes Authentication.
From www.vrogue.co
Authentication With Keycloak Openid Connec vrogue.co Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. Use keycloak to authenticate and authorize users. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Strictly running keycloak in kubernetes won’t. Keycloak Kubernetes Authentication.
From medium.com
authentication with keycloak oidc by Amir Ad Medium Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. We can use keycloak to pass group. Keycloak Kubernetes Authentication.
From medium.com
— Authenticating to your cluster using Keycloak by Aaron Pejakovic ELMO Software Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. Kubernetes oidc authentication with keycloak is a. Keycloak Kubernetes Authentication.
From developers.redhat.com
Authentication and authorization using the Keycloak REST API Red Hat Developer Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: In this article, i will walk you through the deployment of keycloak, a. Keycloak Kubernetes Authentication.
From blog.knoldus.com
How to deploy Keycloak with Postgres on GKE Knoldus Blogs Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. Strictly running keycloak in kubernetes won’t make your platform secure. From exposing the keycloak api. In this post i will show how to use the authorization code flow (also known as. Keycloak Kubernetes Authentication.
From ibrahimhkoyuncu.medium.com
— Ingress External Authentication with OAuth2 Proxy and Keycloak by Ibrahim Halil Keycloak Kubernetes Authentication Use keycloak to authenticate and authorize users. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. From exposing the keycloak api. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to. Keycloak Kubernetes Authentication.
From www.linkedin.com
Simplify User Access with Keycloak Single SignOn (SSO) Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. Use keycloak to authenticate and authorize users. Strictly running keycloak in kubernetes won’t make your platform secure. A lot of concerns are left to the user to configure and implement: In this post we'll integrate kubernetes. Keycloak Kubernetes Authentication.
From www.olivercoding.com
at home Part 6 Keycloak authentication and Azure Active Directory Oliver Coding Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. From exposing the keycloak api. Use keycloak. Keycloak Kubernetes Authentication.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Kubernetes oidc authentication with keycloak is a neat. Keycloak Kubernetes Authentication.
From keycloak.discourse.group
X509 authentication with via ingress Getting advice Keycloak Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. Use keycloak to authenticate and authorize users. A lot of concerns are left to the user to configure and implement: In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or. Keycloak Kubernetes Authentication.
From github.com
GitHub OIDC Keycloak Kubernetes Authentication In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. Use keycloak to authenticate and authorize users. Kubernetes oidc authentication with keycloak is a neat and modern. Keycloak Kubernetes Authentication.
From middlewaretechnologies.in
How to authenticate user with Keycloak OIDC Provider in MiddlewareTechnologies Keycloak Kubernetes Authentication In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. In this article, i will walk you through the deployment of keycloak, a user. Keycloak Kubernetes Authentication.
From awesomeopensource.com
Keycloak On Aws Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes. Keycloak Kubernetes Authentication.
From medium.com
Keycloak for Identity and Access Management & High Availability Deployment with by Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Use keycloak to authenticate and authorize users. Strictly. Keycloak Kubernetes Authentication.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Apache APISIX Keycloak Kubernetes Authentication A lot of concerns are left to the user to configure and implement: In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: From exposing the keycloak api. Use keycloak to authenticate and authorize users. In this post i will show how to use the authorization code. Keycloak Kubernetes Authentication.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with IBM Cloud Identity Keycloak Kubernetes Authentication We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the. Keycloak Kubernetes Authentication.
From blog.getambassador.io
StepbyStep Centralized Authentication for with Keycloak and the Ambassador Edge Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. Strictly running keycloak in kubernetes won’t make your platform secure. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes. Keycloak Kubernetes Authentication.
From www.vrogue.co
Step By Step Guide Using Keycloak vrogue.co Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. A lot of concerns are left to the user to configure and implement: In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. In. Keycloak Kubernetes Authentication.
From www.redhat.com
Adding authentication to your applications with Keycloak Keycloak Kubernetes Authentication In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Strictly running keycloak in kubernetes won’t make your platform secure. In this article, i will. Keycloak Kubernetes Authentication.
From github.com
GitHub Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: Use keycloak to authenticate and authorize users. In. Keycloak Kubernetes Authentication.
From www.olivercoding.com
at home Part 5 Keycloak for authentication Oliver Coding Keycloak Kubernetes Authentication In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. We can use keycloak to pass group claims onto kubernetes and therefore use. Keycloak Kubernetes Authentication.
From knowledgebase.eo-lab.org
Deploy Keycloak on with a sample app on EOLab — EOLab 0.0.1 documentation Keycloak Kubernetes Authentication In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. Kubernetes oidc authentication with keycloak is a neat and modern for devops. Keycloak Kubernetes Authentication.
From www.olivercoding.com
at home Part 5 Keycloak for authentication Oliver Coding Keycloak Kubernetes Authentication Use keycloak to authenticate and authorize users. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. Strictly running keycloak in kubernetes won’t make. Keycloak Kubernetes Authentication.
From www.redhat.com
Adding authentication to your applications with Keycloak Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user. Keycloak Kubernetes Authentication.
From github.com
GitHub OIDC Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. From exposing the keycloak api. A lot of concerns are left to the user to configure and implement: We can use keycloak to pass group claims onto kubernetes. Keycloak Kubernetes Authentication.
From github.com
GitHub OIDC Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. From exposing the keycloak api. In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to. Keycloak Kubernetes Authentication.
From www.vrogue.co
Authentication With Keycloak Openid Connect Part 1 By Vrogue Keycloak Kubernetes Authentication Kubernetes oidc authentication with keycloak is a neat and modern for devops engineers and system administrators to grant various classified access to different team. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. A lot of concerns are left to the user to configure and. Keycloak Kubernetes Authentication.
From blog.doxray.com
Secure Your Application Using Gatekeeper And Keycloak Keycloak Kubernetes Authentication In the following article i’ll configure openid connect (oidc) strategy so as delegate the authentication to one of the most popular identity management: In this article, i will walk you through the deployment of keycloak, a user authentication and authorization tool and how to integrate this to any kubernetes web application without. A lot of concerns are left to the. Keycloak Kubernetes Authentication.
From www.dirigible.io
Keycloak, PostgreSQL & Dirigible Eclipse Dirigible Blog Keycloak Kubernetes Authentication A lot of concerns are left to the user to configure and implement: From exposing the keycloak api. Use keycloak to authenticate and authorize users. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or. Keycloak Kubernetes Authentication.
From www.tremolosecurity.com
Authentication Comparing Solutions Keycloak Kubernetes Authentication From exposing the keycloak api. We can use keycloak to pass group claims onto kubernetes and therefore use different rbac rules to determine different. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. In the following article i’ll configure openid connect (oidc) strategy so as. Keycloak Kubernetes Authentication.
From www.redhat.com
Adding authentication to your applications with Keycloak Keycloak Kubernetes Authentication From exposing the keycloak api. In this post we'll integrate kubernetes with keycloak so that when we execute a kubectl or helm command, if the user is not already. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. In this article, i will walk you through the. Keycloak Kubernetes Authentication.
From alphabsolutions.com
Securing with Keycloak Single SignOn (SSO) and Identity Management Alpha Business Keycloak Kubernetes Authentication Strictly running keycloak in kubernetes won’t make your platform secure. From exposing the keycloak api. Use keycloak to authenticate and authorize users. In this post i will show how to use the authorization code flow (also known as the standard flow) to authenticate users. A lot of concerns are left to the user to configure and implement: In this article,. Keycloak Kubernetes Authentication.