Socks Proxy Kali . The target server as described below is running vulnerable servers. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. This package contains a swiss army knife proxy for rapid deployments. It supports multiple operations such as request/response dump,. We’ll walk through configuring it and how to use it. Using “proxychains” is the best method to surf internet anonymously. Redsocks supports tunneling tcp connections and udp packets. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. Proxychains is a tool that redirects the tcp (transmission.
from practonet.com
Using “proxychains” is the best method to surf internet anonymously. It supports multiple operations such as request/response dump,. Proxychains is a tool that redirects the tcp (transmission. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. The target server as described below is running vulnerable servers. This package contains a swiss army knife proxy for rapid deployments. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. We’ll walk through configuring it and how to use it. Redsocks supports tunneling tcp connections and udp packets.
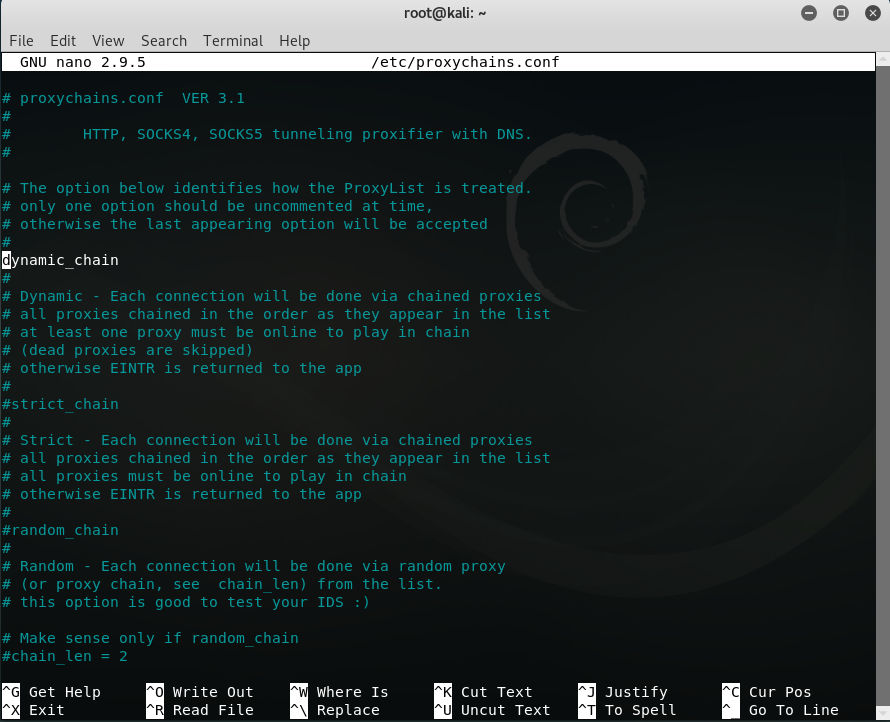
Proxy Chain Setup in Kali Cyber Security, Networking, Technology
Socks Proxy Kali We’ll walk through configuring it and how to use it. Redsocks supports tunneling tcp connections and udp packets. This package contains a swiss army knife proxy for rapid deployments. The target server as described below is running vulnerable servers. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. Using “proxychains” is the best method to surf internet anonymously. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. It supports multiple operations such as request/response dump,. Proxychains is a tool that redirects the tcp (transmission. We’ll walk through configuring it and how to use it.
From www.firewall.cx
Complete Guide to SOCKS Proxy How to Securely Bypass Blocks, Safe Socks Proxy Kali One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. This package contains a swiss army knife proxy for rapid deployments. Proxychains is a tool that redirects the tcp (transmission. Using “proxychains” is the best method to surf internet anonymously. We’ll walk through configuring it and how to. Socks Proxy Kali.
From incogniton.com
SOCKS vs HTTP Proxy Detailed Comparison Incogniton Socks Proxy Kali It supports multiple operations such as request/response dump,. This package contains a swiss army knife proxy for rapid deployments. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. Proxychains is a tool that redirects the tcp (transmission. The target server as described below is running vulnerable servers.. Socks Proxy Kali.
From www.youtube.com
How to set proxy on Kali Linux 2019 YouTube Socks Proxy Kali Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. It supports multiple operations such as request/response dump,. This package contains a swiss army knife proxy for rapid deployments. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through. Socks Proxy Kali.
From proxiesforrent.com
How to install Sock Proxy Socks Proxy Server Buy Private Proxy Socks Socks Proxy Kali One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. Redsocks supports tunneling tcp connections and udp packets. We’ll walk through configuring it. Socks Proxy Kali.
From netnut.io
What are socks Proxy? Complete Guide to Socks Proxy NetNut Socks Proxy Kali Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Redsocks supports tunneling tcp connections and udp packets. Using “proxychains” is the best method to surf. Socks Proxy Kali.
From cybervie.com
How to use Proxychains CYBERVIE Socks Proxy Kali Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. In this article, we’ll explain proxychains, its use cases, how to install it on kali and. Socks Proxy Kali.
From superuser.com
How can I set socks proxy on windows? Super User Socks Proxy Kali Using “proxychains” is the best method to surf internet anonymously. Redsocks supports tunneling tcp connections and udp packets. The target server as described below is running vulnerable servers. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. In this article, we’ll explain proxychains, its use cases, how. Socks Proxy Kali.
From github.com
Unable to connect to target using a SOCKS5 proxy on Kali (WSL 2 Socks Proxy Kali We’ll walk through configuring it and how to use it. Redsocks supports tunneling tcp connections and udp packets. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using. Socks Proxy Kali.
From www.youtube.com
SOCKS Proxy Setup, Installation & Bypass Ubuntu Testing Socks Proxy Kali Redsocks supports tunneling tcp connections and udp packets. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. It supports multiple operations such as request/response dump,. The target server as described below is running vulnerable servers. Learn how to setup the socks5 proxy server on debian, ubuntu, linux. Socks Proxy Kali.
From technopathy.club
Installation and Configuration of SOCKS Proxy Danted on Redhat/CentOS Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. Proxychains is a tool that redirects the tcp (transmission. We’ll walk through configuring it and how to use it. It supports multiple operations such as request/response dump,. The target server as described below is running vulnerable servers. In this article, we’ll explain proxychains, its use cases, how to install. Socks Proxy Kali.
From netnut.io
What’s a SOCKS5 Proxy? Definition and Function Netnut Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. Using “proxychains” is the best method to surf internet anonymously. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. We’ll walk through configuring it and how to use it. Learn how to setup. Socks Proxy Kali.
From netnut.io
What are socks Proxy? Complete Guide to Socks Proxy NetNut Socks Proxy Kali Redsocks supports tunneling tcp connections and udp packets. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. We’ll walk through configuring it. Socks Proxy Kali.
From fastestvpn.com
Here’s How SOCKS Proxy Differs from a VPN Socks Proxy Kali Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. Using “proxychains” is the best method to surf internet anonymously. Redsocks supports tunneling. Socks Proxy Kali.
From www.stupidproxy.com
Best SOCKS5 proxies for 2024 (Datacenter & Residential) Stupid Proxy Socks Proxy Kali We’ll walk through configuring it and how to use it. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. This package contains a swiss army. Socks Proxy Kali.
From removefile.com
How To Set Up A SOCKS Proxy On Windows Socks Proxy Kali It supports multiple operations such as request/response dump,. This package contains a swiss army knife proxy for rapid deployments. Redsocks supports tunneling tcp connections and udp packets. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. Proxychains is a tool that redirects the tcp. Socks Proxy Kali.
From www.learnlinux.in
Socks Proxy V5 Configuration learnlinux.in Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. It supports multiple operations such as request/response dump,. The target server as described below is running vulnerable servers. Redsocks supports tunneling tcp connections and udp packets. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Learn. Socks Proxy Kali.
From github.com
KALI linux Tools Using Proxychains to send network related functions Socks Proxy Kali Proxychains is a tool that redirects the tcp (transmission. Using “proxychains” is the best method to surf internet anonymously. It supports multiple operations such as request/response dump,. The target server as described below is running vulnerable servers. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it. Socks Proxy Kali.
From www.socksproxychecker.com
Socks Proxy Checker check and download socks proxy easily Socks Proxy Kali One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Proxychains is a tool that redirects the tcp (transmission. We’ll walk through configuring it and how to use it. Using “proxychains” is the best method to surf internet anonymously. It supports multiple operations such as request/response dump,. The. Socks Proxy Kali.
From hide-ip-proxy.com
What is a SOCKS proxy and where to find good SOCKS proxies Socks Proxy Kali Using “proxychains” is the best method to surf internet anonymously. This package contains a swiss army knife proxy for rapid deployments. Proxychains is a tool that redirects the tcp (transmission. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. One powerful tool at our. Socks Proxy Kali.
From nooblinux.com
What is a SOCKS5 Proxy Understanding SOCKS Proxies Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. Redsocks supports tunneling tcp connections and udp packets. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether. Socks Proxy Kali.
From proxidize.com
The Basic Guide to SOCKS Proxy Proxidize Socks Proxy Kali Proxychains is a tool that redirects the tcp (transmission. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. It supports multiple operations such as request/response dump,. We’ll walk through configuring it and how to use it. In this article, we’ll explain proxychains, its use cases, how to. Socks Proxy Kali.
From practonet.com
Proxy Chain Setup in Kali Cyber Security, Networking, Technology Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. The target server as described below is running vulnerable servers. Proxychains is a tool that redirects the tcp (transmission. Redsocks supports tunneling tcp connections and udp packets.. Socks Proxy Kali.
From medium.com
Socks proxy in Cloud. Definition by Arun Kumar Cloud Techies Medium Socks Proxy Kali We’ll walk through configuring it and how to use it. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. It supports multiple operations such as request/response dump,. Redsocks supports tunneling tcp connections and udp packets. The target server as described below is running vulnerable servers. Proxychains is. Socks Proxy Kali.
From www.youtube.com
Socks5 proxy and how to use it NordVPN YouTube Socks Proxy Kali The target server as described below is running vulnerable servers. Redsocks supports tunneling tcp connections and udp packets. This package contains a swiss army knife proxy for rapid deployments. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. It supports multiple operations such as request/response dump,. Using. Socks Proxy Kali.
From proxybros.com
The Ultimate Guide to Faceless Socks How to Use Socks Proxies Socks Proxy Kali One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Using “proxychains” is the best method to surf internet anonymously. It supports multiple operations such as request/response dump,. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using. Socks Proxy Kali.
From brightdata.com
SOCKS vs. HTTP proxies InDepth Comparison Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. Redsocks supports tunneling tcp connections and udp packets. The target server as described below is running vulnerable servers. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Proxychains is a tool that redirects the tcp (transmission.. Socks Proxy Kali.
From research.aimultiple.com
The Best SOCKS5 Proxy Providers of 2024 Socks Proxy Kali It supports multiple operations such as request/response dump,. Redsocks supports tunneling tcp connections and udp packets. We’ll walk through configuring it and how to use it. Using “proxychains” is the best method to surf internet anonymously. The target server as described below is running vulnerable servers. One powerful tool at our disposal is the socks proxy, which allows us to. Socks Proxy Kali.
From netnut.io
What are socks Proxy? Complete Guide to Socks Proxy NetNut Socks Proxy Kali Using “proxychains” is the best method to surf internet anonymously. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Redsocks supports tunneling tcp connections and udp packets. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you. Socks Proxy Kali.
From www.youtube.com
Configure Socks proxy for apt manager in kali linux YouTube Socks Proxy Kali Using “proxychains” is the best method to surf internet anonymously. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. This package contains a swiss army knife proxy for rapid deployments. Redsocks supports tunneling tcp connections and udp packets. Proxychains is a tool that redirects the tcp (transmission.. Socks Proxy Kali.
From crawlbase.com
What is a SOCKS5 Proxy, and What is it Best for? Crawlbase Socks Proxy Kali This package contains a swiss army knife proxy for rapid deployments. Using “proxychains” is the best method to surf internet anonymously. In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red. Socks Proxy Kali.
From itechhacks.com
Understanding Sock Proxies Advantages and Disadvantages Explored Socks Proxy Kali One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. Using “proxychains” is the best method to surf internet anonymously. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. It supports multiple operations such as. Socks Proxy Kali.
From research.aimultiple.com
The Best SOCKS5 Proxy Providers of 2023 Socks Proxy Kali The target server as described below is running vulnerable servers. This package contains a swiss army knife proxy for rapid deployments. We’ll walk through configuring it and how to use it. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. In this article, we’ll explain proxychains, its. Socks Proxy Kali.
From hide-ip-proxy.com
What is a SOCKS proxy and where to find good SOCKS proxies Socks Proxy Kali It supports multiple operations such as request/response dump,. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora, and rocky linux using the microsocks. Redsocks supports tunneling tcp connections and udp packets. The target server as described below is running vulnerable servers. One powerful tool at our disposal is the socks proxy, which allows. Socks Proxy Kali.
From pt-br.proxyscrape.com
Como configurar o SSH SOCKS Proxy 5 etapas simples Socks Proxy Kali Using “proxychains” is the best method to surf internet anonymously. One powerful tool at our disposal is the socks proxy, which allows us to tunnel our network traffic through a proxy server. We’ll walk through configuring it and how to use it. It supports multiple operations such as request/response dump,. Redsocks supports tunneling tcp connections and udp packets. The target. Socks Proxy Kali.
From blog.soax.com
What is SOCKS and SOCKS5 Proxy and How to Use It? SOAX Blog Socks Proxy Kali In this article, we’ll explain proxychains, its use cases, how to install it on kali and ubuntu, and whether you can use it on windows. This package contains a swiss army knife proxy for rapid deployments. It supports multiple operations such as request/response dump,. Learn how to setup the socks5 proxy server on debian, ubuntu, linux mint, red hat, fedora,. Socks Proxy Kali.