Keycloak.config.resolver . Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. It is then possible to integrate keycloak using the spring security feature. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Learn how to configure a keycloak server and use it with a spring boot application. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. By default, keycloak reads configuration from the conf/keycloak.properties file.
from refactorfirst.com
It is then possible to integrate keycloak using the spring security feature. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak server and use it with a spring boot application. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. By default, keycloak reads configuration from the conf/keycloak.properties file. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request.
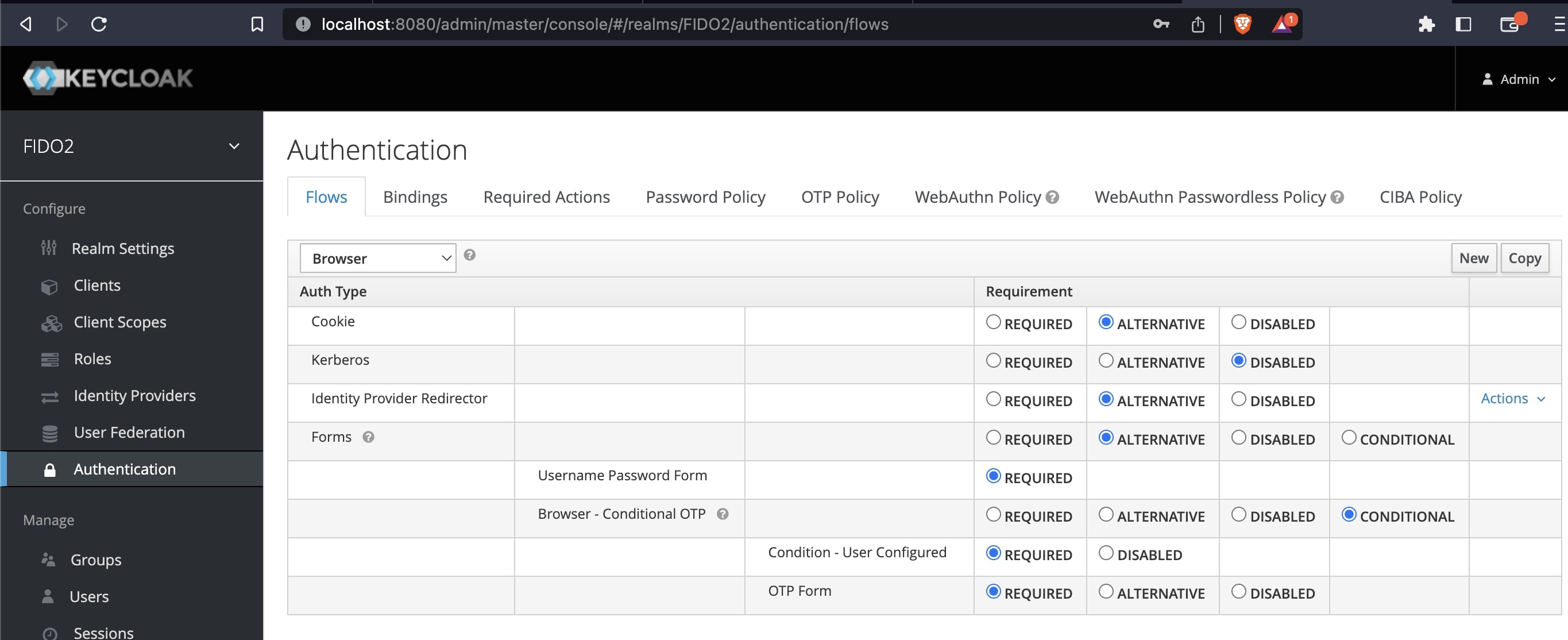
FIDO2 Passwordless Authentication With Keycloak Part 2 RefactorFirst
Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. It is then possible to integrate keycloak using the spring security feature. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. By default, keycloak reads configuration from the conf/keycloak.properties file. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Learn how to configure a keycloak server and use it with a spring boot application. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak.config.resolver Learn how to configure a keycloak server and use it with a spring boot application. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. It is then possible to integrate keycloak using the spring security feature. By default, keycloak reads configuration from the conf/keycloak.properties file. Keycloak makes it possible. Keycloak.config.resolver.
From docs.datawiza.com
Keycloak Datawiza Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. Learn how to configure a keycloak server and use it with a spring boot application. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. This. Keycloak.config.resolver.
From opensource.hcltechsw.com
Configuring KeyCloak as an OIDC provider for Connections HCL Connections 8.0 CR1 Help Center Keycloak.config.resolver We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Learn how to configure a keycloak server and use it with a spring boot application. It is then possible to integrate keycloak using the spring security feature. Keycloak makes it possible to have a custom config resolver so you can. Keycloak.config.resolver.
From doc.psono.com
Keycloak as SAML IDP for SSO Psono Documentation Keycloak.config.resolver This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. It is then possible to integrate keycloak using the spring security feature. By default, keycloak. Keycloak.config.resolver.
From github.com
GitHub adorsys/keycloakconfigcli Import YAML/JSONformatted configuration files into Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. By default, keycloak reads configuration from the conf/keycloak.properties file. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Learn how to configure a keycloak server and use it with. Keycloak.config.resolver.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. By default, keycloak reads configuration from the conf/keycloak.properties file. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Keycloak makes. Keycloak.config.resolver.
From gauthier-cassany.com
Set up Keycloak in Spring Boot using the Keycloak Admin API Keycloak.config.resolver By default, keycloak reads configuration from the conf/keycloak.properties file. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak. Keycloak.config.resolver.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak.config.resolver This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak server and use it with a spring boot application. By default, keycloak reads configuration from. Keycloak.config.resolver.
From www.reddit.com
Good practices for sharing Keycloak secrets with clients? KeyCloak Keycloak.config.resolver Learn how to configure a keycloak server and use it with a spring boot application. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. This guide explains. Keycloak.config.resolver.
From keycloak.discourse.group
Keycloak.X Wired behaivor while running keycloakconfigcli test suite Keycloak Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. By default, keycloak reads configuration from the conf/keycloak.properties file. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Learn how to configure a keycloak server and use. Keycloak.config.resolver.
From plugins.miniorange.com
OAuth/OpenID Single Sign On (SSO) into Jira using Keycloak Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak server and use it with a spring boot application. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. By default, keycloak reads configuration from. Keycloak.config.resolver.
From brampat.github.io
Keycloak tutorial Bram’s Blog Keycloak.config.resolver Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak server and use it with a spring boot application. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before. Keycloak.config.resolver.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak.config.resolver Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Learn how to configure a keycloak server and use it with a spring boot application. It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. We recommend optimizing red hat. Keycloak.config.resolver.
From stackoverflow.com
How to optimize config Keycloak Stack Overflow Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. By default, keycloak reads configuration from the conf/keycloak.properties file. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. We. Keycloak.config.resolver.
From www.azguards.com
Single Sign on Setup Okta+ Keycloak using SMAIL and OIDC Keycloak.config.resolver Learn how to configure a keycloak server and use it with a spring boot application. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. It is then possible to integrate keycloak. Keycloak.config.resolver.
From plugins.miniorange.com
WordPress Remote User Sync for Keycloak Sync WP Users to Keycloak Keycloak.config.resolver We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Learn how to configure a keycloak server and use it with a spring boot application. This guide explains the configuration methods for. Keycloak.config.resolver.
From refactorfirst.com
FIDO2 Passwordless Authentication With Keycloak Part 2 RefactorFirst Keycloak.config.resolver Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Learn how to configure a keycloak server and use it with a spring boot application. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration.. Keycloak.config.resolver.
From blog.brakmic.com
Keycloak Extensions Coding Keycloak.config.resolver Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. It is then possible to integrate keycloak using the spring. Keycloak.config.resolver.
From stackoverflow.com
Secure Java application using Keycloak saml Stack Overflow Keycloak.config.resolver Learn how to configure a keycloak server and use it with a spring boot application. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Keycloak makes it possible to have a custom. Keycloak.config.resolver.
From www.janua.fr
Keycloak config checker JANUA Keycloak.config.resolver By default, keycloak reads configuration from the conf/keycloak.properties file. Learn how to configure a keycloak server and use it with a spring boot application. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. We recommend optimizing red hat build of keycloak to. Keycloak.config.resolver.
From help.boldreports.com
Integrating Bold Reports with Keycloak via OpenID Connect. Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom.. Keycloak.config.resolver.
From www.solveforum.com
[Solved] Keycloak HTTP request with Client Credentials always returns 'login' page SolveForum Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Learn how to configure a keycloak server and use it with a spring boot application. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. This guide explains. Keycloak.config.resolver.
From docs.datawiza.com
Keycloak Datawiza Keycloak.config.resolver Learn how to configure a keycloak server and use it with a spring boot application. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom.. Keycloak.config.resolver.
From www.azguards.com
Single Sign on Setup Okta+ Keycloak using SMAIL and OIDC Keycloak.config.resolver Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Learn how to configure a keycloak server and use it with a spring boot application. It is then possible to integrate keycloak using the spring. Keycloak.config.resolver.
From www.azguards.com
Single Sign on Setup Okta+ Keycloak using SMAIL and OIDC Keycloak.config.resolver Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. Learn how to configure a keycloak server and use it with a spring boot application. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. We recommend optimizing red hat build of keycloak to provide faster startup and. Keycloak.config.resolver.
From github.com
Resources are not correctly loaded with proxy config · Issue 17586 · keycloak/keycloak · GitHub Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. By default, keycloak reads configuration from the conf/keycloak.properties file. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Learn how to configure a keycloak server and use. Keycloak.config.resolver.
From docs.mattermost.com
Configure SAML with Keycloak Mattermost documentation Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. By default, keycloak reads configuration from the conf/keycloak.properties file. It is then possible to integrate keycloak using the spring security feature. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before. Keycloak.config.resolver.
From docs.datawiza.com
Keycloak Datawiza Keycloak.config.resolver This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. By default, keycloak reads configuration from the conf/keycloak.properties file. It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter. Keycloak.config.resolver.
From bejondshao.github.io
Category Keycloak Bejond IO Keycloak.config.resolver It is then possible to integrate keycloak using the spring security feature. Learn how to configure a keycloak server and use it with a spring boot application. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Keycloak makes it possible to have a custom config resolver so you can. Keycloak.config.resolver.
From gauthier-cassany.com
Set up Keycloak in Spring Boot using the Keycloak Admin API Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption. Keycloak.config.resolver.
From handbook.digital-blueprint.org
Keycloak Integration digital blueprint handbook Keycloak.config.resolver This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. By default, keycloak reads configuration from the conf/keycloak.properties file. Learn how to configure a keycloak server and use it with a spring boot application. We. Keycloak.config.resolver.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. By default, keycloak reads configuration from the conf/keycloak.properties file. It is then possible to integrate keycloak using the spring security feature. Learn how to configure a keycloak server. Keycloak.config.resolver.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak.config.resolver Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. Learn how to configure a keycloak server and use it with a spring boot application. It is then possible to integrate keycloak using the spring security feature. Keycloak provides a keycloakwebsecurityconfigureradapter as a convenient base class for. This. Keycloak.config.resolver.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak.config.resolver We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Keycloak makes it possible to have a custom config resolver so you can choose what adapter config is used for each request. This guide explains the configuration methods for keycloak and how to start and apply the preferred configuration. By. Keycloak.config.resolver.
From www.redhat.com
How to use Keycloak to configure SSO for commandline applications Enable Sysadmin Keycloak.config.resolver We recommend optimizing red hat build of keycloak to provide faster startup and better memory consumption before deploying red hat. Instead of defining the keycloak config in spring application.yaml, keep multiple keycloak.json config files, and use a custom. Learn how to configure a keycloak server and use it with a spring boot application. This guide explains the configuration methods for. Keycloak.config.resolver.