What Is Signature Algorithm In Certificate . Why does it need a signature hash algorithm?. The signer owns a public/private key pair. The signature algorithms used for authentication (certificateverify messages) are. A signature algorithm is a cryptographic algorithm such that: What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? I was experimenting around with my browser's certificate issued by gts which is google trust services. The public key is public, the private key is. What are server signature algorithms used for? The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. When using tls, messages sent by the client and server are encrypted using symmetric keys. To do this the client and server.
from www.geeksforgeeks.org
Why does it need a signature hash algorithm?. The signer owns a public/private key pair. I was experimenting around with my browser's certificate issued by gts which is google trust services. When using tls, messages sent by the client and server are encrypted using symmetric keys. The signature algorithms used for authentication (certificateverify messages) are. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. What are server signature algorithms used for? The public key is public, the private key is. A signature algorithm is a cryptographic algorithm such that: What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate?
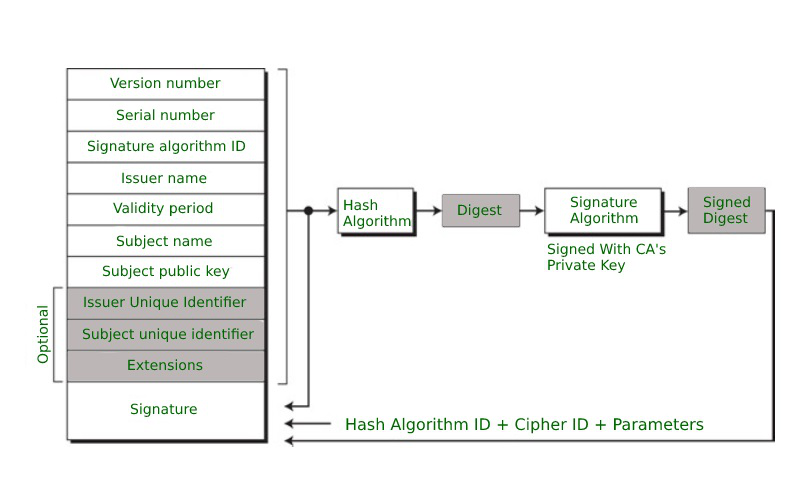
X.509 Authentication Service
What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. A signature algorithm is a cryptographic algorithm such that: I was experimenting around with my browser's certificate issued by gts which is google trust services. What are server signature algorithms used for? Why does it need a signature hash algorithm?. When using tls, messages sent by the client and server are encrypted using symmetric keys. The signer owns a public/private key pair. The signature algorithms used for authentication (certificateverify messages) are. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The public key is public, the private key is. To do this the client and server.
From mayurpahwa.com
Digital Signature What Is Signature Algorithm In Certificate A signature algorithm is a cryptographic algorithm such that: To do this the client and server. When using tls, messages sent by the client and server are encrypted using symmetric keys. The public key is public, the private key is. The signature algorithms used for authentication (certificateverify messages) are. The signaturealgorithm field contains the identifier for the cryptographic algorithm used. What Is Signature Algorithm In Certificate.
From node-security.com
TLS Server Signature Algorithm Node Security What Is Signature Algorithm In Certificate The signature algorithms used for authentication (certificateverify messages) are. I was experimenting around with my browser's certificate issued by gts which is google trust services. The public key is public, the private key is. What are server signature algorithms used for? The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by. What Is Signature Algorithm In Certificate.
From slidetodoc.com
PublicKey Infrastructure PKI SMU CSE 53497349 What is What Is Signature Algorithm In Certificate The signer owns a public/private key pair. What are server signature algorithms used for? Why does it need a signature hash algorithm?. The public key is public, the private key is. To do this the client and server. The signature algorithms used for authentication (certificateverify messages) are. When using tls, messages sent by the client and server are encrypted using. What Is Signature Algorithm In Certificate.
From examnightslive.wordpress.com
Digital Signature and Digital Certificate Exam Nights Live What Is Signature Algorithm In Certificate The public key is public, the private key is. Why does it need a signature hash algorithm?. The signer owns a public/private key pair. I was experimenting around with my browser's certificate issued by gts which is google trust services. What are server signature algorithms used for? The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the. What Is Signature Algorithm In Certificate.
From www.namecheap.com
I can see SHA1 fingerprint/thumbprint on my certificate. Is my What Is Signature Algorithm In Certificate What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? When using tls, messages sent by the client and server are encrypted using symmetric keys. I was experimenting around with my browser's certificate issued by gts which is google trust services. The signature algorithms used for authentication (certificateverify messages) are. The signer owns. What Is Signature Algorithm In Certificate.
From howardsimpson.blogspot.com
NETERR_CERT_WEAK_SIGNATURE_ALGORITHM IIS SSL Certificate What Is Signature Algorithm In Certificate The signature algorithms used for authentication (certificateverify messages) are. The signer owns a public/private key pair. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? I was experimenting around with my browser's certificate issued by gts which is google trust services. The signaturealgorithm field contains the identifier for the cryptographic algorithm used. What Is Signature Algorithm In Certificate.
From proprivacy.com
Digital Signature Why And How You Should Use It What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? When using tls, messages sent by the client and server are encrypted using symmetric keys. The signature algorithms used for authentication (certificateverify messages) are. To do. What Is Signature Algorithm In Certificate.
From www.youtube.com
Digital Signature Algorithm (DSA) Cryptography Practical TLS YouTube What Is Signature Algorithm In Certificate What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? When using tls, messages sent by the client and server are encrypted using symmetric keys. The signature algorithms used for authentication (certificateverify messages) are. A signature algorithm is a cryptographic algorithm such that: The public key is public, the private key is. Why. What Is Signature Algorithm In Certificate.
From www.thesecuritybuddy.com
How does Digital Signature Algorithm (DSA) work? The Security Buddy What Is Signature Algorithm In Certificate The public key is public, the private key is. The signer owns a public/private key pair. Why does it need a signature hash algorithm?. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? A signature algorithm is a cryptographic algorithm such that: The signature algorithm describes the method by which the checksum. What Is Signature Algorithm In Certificate.
From www.sectigo.com
What Is PKI? The Guide To Public Key Infrastructure Sectigo® Official What Is Signature Algorithm In Certificate A signature algorithm is a cryptographic algorithm such that: The public key is public, the private key is. When using tls, messages sent by the client and server are encrypted using symmetric keys. Why does it need a signature hash algorithm?. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature. What Is Signature Algorithm In Certificate.
From www.mdpi.com
Applied Sciences Free FullText A Novel Digital Signature Scheme What Is Signature Algorithm In Certificate A signature algorithm is a cryptographic algorithm such that: To do this the client and server. The public key is public, the private key is. When using tls, messages sent by the client and server are encrypted using symmetric keys. Why does it need a signature hash algorithm?. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by. What Is Signature Algorithm In Certificate.
From www.quantumbooks.com
Advantages and Disadvantages of Digital Certificates What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? A signature algorithm is a cryptographic algorithm such that: Why does it need a signature hash algorithm?. When using tls, messages sent by the client and. What Is Signature Algorithm In Certificate.
From stackoverflow.com
What exactly is meant by "Signature Algorithm" on a certificate? Which What Is Signature Algorithm In Certificate A signature algorithm is a cryptographic algorithm such that: To do this the client and server. When using tls, messages sent by the client and server are encrypted using symmetric keys. The signature algorithms used for authentication (certificateverify messages) are. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signer owns. What Is Signature Algorithm In Certificate.
From favpng.com
Digital Signature Algorithm Electronic Signature Public Key Certificate What Is Signature Algorithm In Certificate Why does it need a signature hash algorithm?. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. To do this the client and server. The signature algorithms used for authentication (certificateverify messages) are. What are server signature algorithms used for? The signature algorithm describes the method by which the checksum calculated by. What Is Signature Algorithm In Certificate.
From japaneseclass.jp
Digital Signature Algorithm Digital Signature Algorithm What Is Signature Algorithm In Certificate The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. The signature algorithms used for authentication (certificateverify messages) are. To do this the client and server. Why does it need a signature hash algorithm?. I was experimenting around with my browser's certificate issued by gts which. What Is Signature Algorithm In Certificate.
From edusign.fr
Signature numérique son fonctionnement et sa légalité Edusign Blog What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. Why does it need a signature hash algorithm?. To do this the client and server. The signer owns a public/private key pair. The public key is public, the private key is. I was experimenting around with my browser's certificate issued by gts which. What Is Signature Algorithm In Certificate.
From pdfprof.com
digital signature algorithm What Is Signature Algorithm In Certificate What are server signature algorithms used for? I was experimenting around with my browser's certificate issued by gts which is google trust services. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The signature algorithm. What Is Signature Algorithm In Certificate.
From www.includehelp.com
Digital Signature Algorithm (DSA) in Cryptography What Is Signature Algorithm In Certificate I was experimenting around with my browser's certificate issued by gts which is google trust services. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature algorithm describes the method by which the checksum. What Is Signature Algorithm In Certificate.
From sectigostore.com
What Is an SSL/TLS Cipher Suite? InfoSec Insights What Is Signature Algorithm In Certificate The signer owns a public/private key pair. Why does it need a signature hash algorithm?. To do this the client and server. A signature algorithm is a cryptographic algorithm such that: What are server signature algorithms used for? When using tls, messages sent by the client and server are encrypted using symmetric keys. What's the difference between the signature algorithm. What Is Signature Algorithm In Certificate.
From www.geeksforgeeks.org
Java implementation of Digital Signatures in Cryptography What Is Signature Algorithm In Certificate The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. When using tls, messages sent by the client and server are encrypted using symmetric keys. The public key is public, the private key is. To do this the client and server. The signature algorithms used for. What Is Signature Algorithm In Certificate.
From 9to5answer.com
[Solved] SSL Certificate Signature Algorithm shows 9to5Answer What Is Signature Algorithm In Certificate Why does it need a signature hash algorithm?. The public key is public, the private key is. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. The signaturealgorithm. What Is Signature Algorithm In Certificate.
From www.infosec.gov.hk
InfoSec Public Key Infrastructure What Is Signature Algorithm In Certificate What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? I was experimenting around with my browser's certificate issued by gts which is google trust services. What are server signature algorithms used for? When using tls, messages sent by the client and server are encrypted using symmetric keys. The public key is public,. What Is Signature Algorithm In Certificate.
From www.geeksforgeeks.org
X.509 Authentication Service What Is Signature Algorithm In Certificate Why does it need a signature hash algorithm?. The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? When using tls, messages sent by the client and server are. What Is Signature Algorithm In Certificate.
From inevitableeth.com
Digital Signatures Inevitable Ethereum What Is Signature Algorithm In Certificate When using tls, messages sent by the client and server are encrypted using symmetric keys. The public key is public, the private key is. The signer owns a public/private key pair. The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. The signaturealgorithm field contains the. What Is Signature Algorithm In Certificate.
From www.slideserve.com
PPT Clarifications to KMIP v1.1 for Asymmetric Crypto and What Is Signature Algorithm In Certificate What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. The public key is public, the private key is. The signer owns a public/private key pair. To do this. What Is Signature Algorithm In Certificate.
From medium.com
What is Digital Signature Algorithm ? by Blockchain Behind The Scenes What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The signature algorithms used for authentication (certificateverify messages) are. The public key is public, the private key is. The signer owns a public/private key pair. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? I. What Is Signature Algorithm In Certificate.
From www.semanticscholar.org
Table 2 from New Method for Obtaining Digital Signature Certificate What Is Signature Algorithm In Certificate The signature algorithms used for authentication (certificateverify messages) are. The signer owns a public/private key pair. To do this the client and server. The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. When using tls, messages sent by the client and server are encrypted using. What Is Signature Algorithm In Certificate.
From present5.com
Digital Certificates X 509 Open PGP Security Protocols What Is Signature Algorithm In Certificate The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The public key is public, the private key is. To do this the client and server. A signature algorithm is a cryptographic algorithm such that: When using tls, messages sent by the client and server are encrypted using symmetric keys. The signature algorithm. What Is Signature Algorithm In Certificate.
From www.researchgate.net
Data security digital signature process basic on RSA Download What Is Signature Algorithm In Certificate A signature algorithm is a cryptographic algorithm such that: To do this the client and server. The public key is public, the private key is. The signer owns a public/private key pair. When using tls, messages sent by the client and server are encrypted using symmetric keys. Why does it need a signature hash algorithm?. The signature algorithms used for. What Is Signature Algorithm In Certificate.
From pdfprof.com
digital signature algorithm What Is Signature Algorithm In Certificate The public key is public, the private key is. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signer owns a public/private key pair. To do this the client and server. Why does it need a signature hash algorithm?. I was experimenting around with my browser's certificate issued by gts which. What Is Signature Algorithm In Certificate.
From stackoverflow.com
What exactly is meant by "Signature Algorithm" on a certificate? Which What Is Signature Algorithm In Certificate When using tls, messages sent by the client and server are encrypted using symmetric keys. I was experimenting around with my browser's certificate issued by gts which is google trust services. The public key is public, the private key is. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the ca to sign this. The signer owns. What Is Signature Algorithm In Certificate.
From techterms.com
Digital Signature Definition What is a digital signature? What Is Signature Algorithm In Certificate What are server signature algorithms used for? The public key is public, the private key is. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? When using tls, messages sent by the client and server are encrypted using symmetric keys. I was experimenting around with my browser's certificate issued by gts which. What Is Signature Algorithm In Certificate.
From www.codingninjas.com
Cryptography Digital Signature Coding Ninjas What Is Signature Algorithm In Certificate The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. What are server signature algorithms used for? The public key is public, the private key is. The signer owns a public/private key pair. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by the. What Is Signature Algorithm In Certificate.
From www.docusign.com.au
Understanding digital signatures What Is Signature Algorithm In Certificate What are server signature algorithms used for? What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature algorithm describes the method by which the checksum calculated by the signature hash algorithm was signed by the certification authority using its. The signaturealgorithm field contains the identifier for the cryptographic algorithm used by. What Is Signature Algorithm In Certificate.
From www.youtube.com
Digital Signature Algorithm Simple Example xRay Pixy YouTube What Is Signature Algorithm In Certificate The signer owns a public/private key pair. A signature algorithm is a cryptographic algorithm such that: To do this the client and server. Why does it need a signature hash algorithm?. What's the difference between the signature algorithm and the signature hash algorithm found in an x.509 certificate? The signature algorithms used for authentication (certificateverify messages) are. The signaturealgorithm field. What Is Signature Algorithm In Certificate.