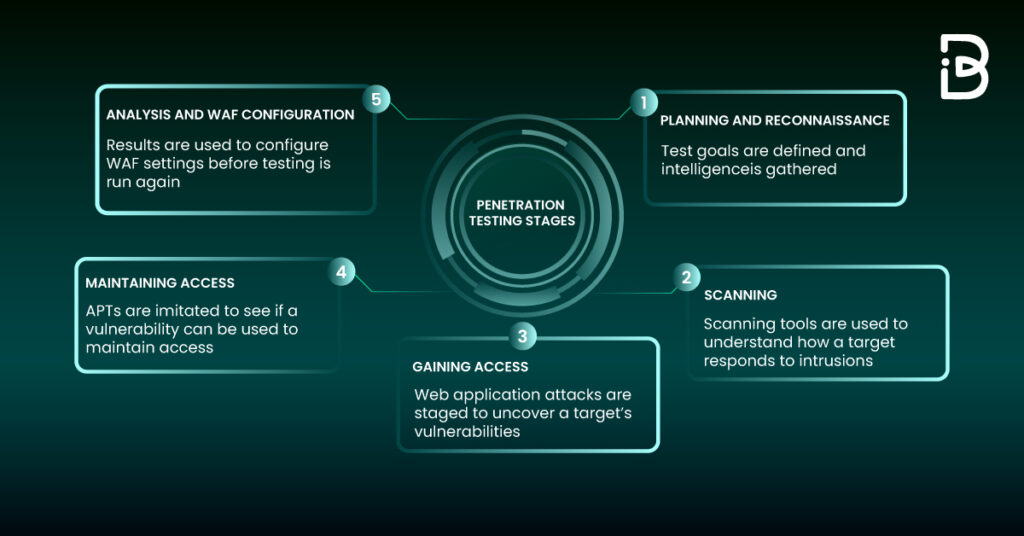
Penetration Testing Terminology . For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. these terms are ways of describing how much information a penetration tester has about the target system. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. We aim to make your. A method of testing where testers target individual binary components or the application as a whole. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). our penetration test glossary includes common penetration testing and cybersecurity terms. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web.
from www.immunebytes.com
penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). A method of testing where testers target individual binary components or the application as a whole. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. We aim to make your. these terms are ways of describing how much information a penetration tester has about the target system. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. our penetration test glossary includes common penetration testing and cybersecurity terms. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal.
A Beginner’s Guide to Testing ImmuneBytes
Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. A method of testing where testers target individual binary components or the application as a whole. these terms are ways of describing how much information a penetration tester has about the target system. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. We aim to make your. our penetration test glossary includes common penetration testing and cybersecurity terms.
From purplesec.us
Testing Methodologies 4 Step Framework Penetration Testing Terminology these terms are ways of describing how much information a penetration tester has about the target system. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a. Penetration Testing Terminology.
From www.informit.com
Testing Fundamentals A HandsOn Guide to Reliable Security Penetration Testing Terminology our penetration test glossary includes common penetration testing and cybersecurity terms. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. A method of testing where testers target individual binary components or the application as a whole. penetration testing, often referred to as pen testing,. Penetration Testing Terminology.
From www.getastra.com
Why Defining Testing Scope is Important? ASTRA Penetration Testing Terminology A method of testing where testers target individual binary components or the application as a whole. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a. Penetration Testing Terminology.
From www.youtube.com
Testing Bootcamp Infosec Terminology YouTube Penetration Testing Terminology a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. penetration testing, often referred to as pen testing, is a simulated cyber. Penetration Testing Terminology.
From www.ecsbiztech.com
What are the different types of testing? ECS Biztech Ltd. Penetration Testing Terminology In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. For black box testing, little to no information is provided by a client and a penetration tester is required to test. Penetration Testing Terminology.
From www.infosectrain.com
What is Testing? InfosecTrain Penetration Testing Terminology A method of testing where testers target individual binary components or the application as a whole. our penetration test glossary includes common penetration testing and cybersecurity terms. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. For black box testing, little to no information is. Penetration Testing Terminology.
From dion-international.com
Physical Testing Dion International Ltd Penetration Testing Terminology For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. A method of testing where testers target individual binary components or the application as a whole. these terms are ways of describing how much information a penetration tester. Penetration Testing Terminology.
From www.immunebytes.com
A Beginner’s Guide to Testing ImmuneBytes Penetration Testing Terminology penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. our penetration test glossary includes common penetration testing and cybersecurity terms. We aim to make your.. Penetration Testing Terminology.
From securityboulevard.com
OWASP Testing Your Ultimate Guide! Security Boulevard Penetration Testing Terminology For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing, often referred to as pen testing or. Penetration Testing Terminology.
From telegra.ph
Test Telegraph Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. For black box testing, little to no information is provided by a client and a penetration tester. Penetration Testing Terminology.
From avord.co.uk
Understanding the Testing Process and how to conduct a test Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. For black box testing, little to no information is provided by a client and a penetration tester. Penetration Testing Terminology.
From getoppos.com
What is Testing An InDepth Guide Oppos Penetration Testing Terminology In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). We aim to make your. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber. Penetration Testing Terminology.
From getoppos.com
Testing Network Oppos Cybersecurity Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system,. Penetration Testing Terminology.
From www.dummies.com
Testing Terminology dummies Penetration Testing Terminology For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing, often referred to. Penetration Testing Terminology.
From www.linknet.id
Apa itu Testing? Pengertian, Fungsi, dan Tahapannya Link Net Penetration Testing Terminology A method of testing where testers target individual binary components or the application as a whole. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system,. Penetration Testing Terminology.
From www.wallarm.com
What is Testing? Definition, Steps, Pros and Cons Penetration Testing Terminology penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. our penetration test glossary includes common penetration testing and cybersecurity terms. A method of testing where testers target individual binary components or the application as a whole. these terms are ways of describing how much. Penetration Testing Terminology.
From brightsec.com
9 Testing Types Penetration Testing Terminology For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. In the context of web. Penetration Testing Terminology.
From data-flair.training
Testing Stages, Methods and Types DataFlair Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. For black box testing, little to no information is provided by a client and a penetration tester. Penetration Testing Terminology.
From www.youtube.com
Testing Bootcamp Essential Information Security Penetration Testing Terminology a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. these terms are ways of describing how much information a penetration tester has about the target system. For black box testing, little to no information is provided by a client and a penetration tester is required. Penetration Testing Terminology.
From cybersecuritynews.com
10 Best Testing Phases & Life cycle 2023 Guide Penetration Testing Terminology these terms are ways of describing how much information a penetration tester has about the target system. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). For black box testing, little to no information is provided by a client and a penetration tester is required to test a target. Penetration Testing Terminology.
From www.youtube.com
Testing Bootcamp Testing Terminology YouTube Penetration Testing Terminology We aim to make your. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. our penetration test glossary includes common penetration testing and cybersecurity terms. penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or. Penetration Testing Terminology.
From cyberhunter.solutions
InDepth Pentesting Methodology Explained CyberHunter Penetration Testing Terminology For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). our penetration test glossary includes common penetration testing and. Penetration Testing Terminology.
From subscription.packtpub.com
testing standards Securing Network Infrastructure Penetration Testing Terminology below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. our penetration test glossary includes common penetration testing. Penetration Testing Terminology.
From ocd-tech.com
Network Testing Vulnerability Scanning Boston MA Penetration Testing Terminology penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. our penetration test glossary includes common penetration testing and cybersecurity terms. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). A method of testing where. Penetration Testing Terminology.
From www.sciencedoze.com
Testing Definition, Phases and Types Penetration Testing Terminology We aim to make your. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. these terms are ways of describing how much information a penetration tester has about the target system. penetration testing, often referred to. Penetration Testing Terminology.
From www.appknox.com
What is Testing Definition, Methods, and Examples Penetration Testing Terminology penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. We aim to make your. our penetration test glossary includes common penetration testing and cybersecurity terms. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide.. Penetration Testing Terminology.
From www.getastra.com
Learn Why Testing is Important Astra Security Penetration Testing Terminology a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. our penetration test glossary includes common penetration testing and cybersecurity terms. these terms are ways of describing how much information a penetration tester has about the target system. penetration testing, often referred to as. Penetration Testing Terminology.
From www.hacknos.com
Types of Testing HackNos Test Type Penetration Testing Terminology A method of testing where testers target individual binary components or the application as a whole. In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. our. Penetration Testing Terminology.
From u-tor.com
What is Testing? The Crucial Method to Prevent Data Penetration Testing Terminology penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. a penetration test, or. Penetration Testing Terminology.
From snapsec.co
Understanding Testing Types, Methodology, and Best Penetration Testing Terminology We aim to make your. our penetration test glossary includes common penetration testing and cybersecurity terms. these terms are ways of describing how much information a penetration tester has about the target system. below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. penetration testing, often referred. Penetration Testing Terminology.
From cybersecuritynews.com
10 Best Testing Phases & Life cycle 2023 Guide Penetration Testing Terminology penetration testing, often referred to as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. a penetration test, or pen test, is a security test that launches. Penetration Testing Terminology.
From avord.co.uk
Understanding the Testing Process and how to conduct a test Penetration Testing Terminology penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. these terms are ways of. Penetration Testing Terminology.
From www.kualitatem.com
Why Testing is Important for Your Security? Penetration Testing Terminology a penetration test, or pen test, is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. penetration testing, often referred to. Penetration Testing Terminology.
From www.getastra.com
Different Types Of Testing? Penetration Testing Terminology In the context of web application security, penetration testing is commonly used to augment a web application firewall (waf). below, we’ll dive into five of the most popular penetration testing frameworks and pen testing methodologies to help guide. penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for. Penetration Testing Terminology.
From blog.securelayer7.net
The 6 Steps In The Testing Process Penetration Testing Terminology our penetration test glossary includes common penetration testing and cybersecurity terms. For black box testing, little to no information is provided by a client and a penetration tester is required to test a target in a similar fashion to a cyber criminal. In the context of web application security, penetration testing is commonly used to augment a web application. Penetration Testing Terminology.