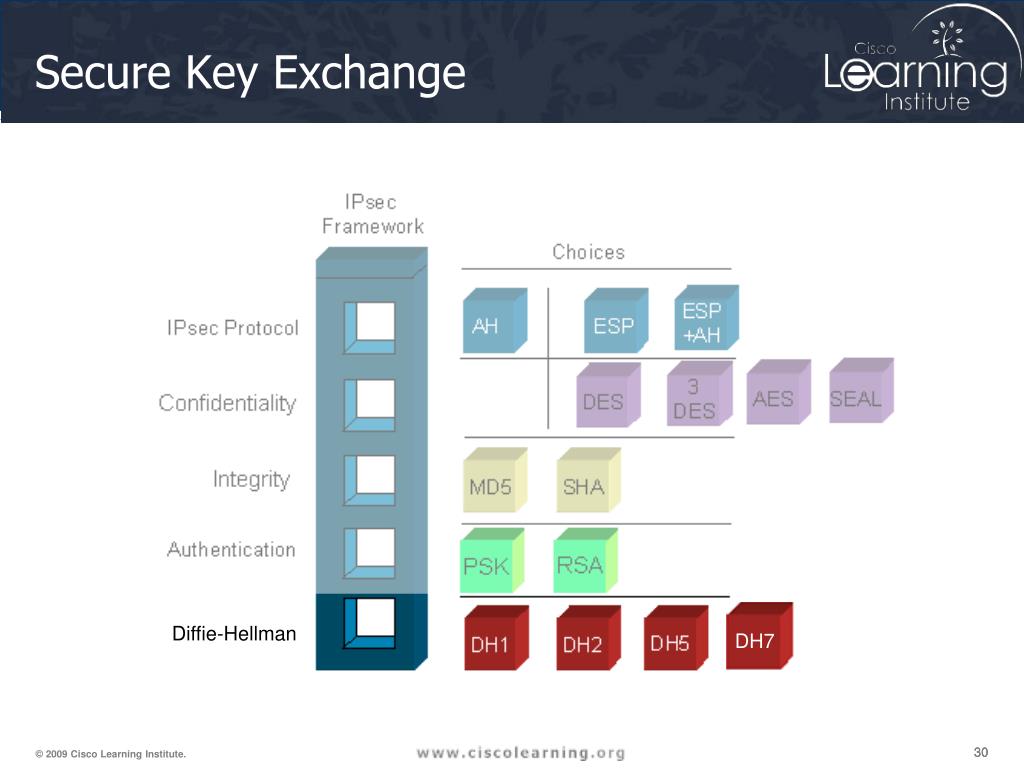
Secure Key Exchange . How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages.
from www.slideserve.com
Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption.
PPT CCNA Security PowerPoint Presentation, free download ID6816913
Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time?
From smartcardsecurity.org
Secure Key Exchange Process In Cryptographic Key Management Secure Key Exchange Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From slideplayer.com
Recent developments in group key exchange ppt download Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.slideserve.com
PPT CCNA Security PowerPoint Presentation, free download ID6816913 Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From www.cleo.com
File Sharing Security Risks Tips for Secure File Exchange Cleo Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From guardiandigital.com
What Is S/MIME and How Can It Secure Email?. Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From 2www.handytrac.com
5 Essential Characteristics of a Secure Key Management System HandyTrac Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric. Secure Key Exchange.
From www.researchgate.net
STFTP's Secure Key Exchange and Data Encryption Protocol. Download Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric. Secure Key Exchange.
From www.slideserve.com
PPT Public Key Encryption PowerPoint Presentation, free download ID Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From lockedinlust.com
Secure Key Exchange Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.slideserve.com
PPT Implementing Virtual Private Networks PowerPoint Presentation Secure Key Exchange Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From www.researchgate.net
Secure key exchange technique Download Scientific Diagram Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.slideteam.net
Secure Key Exchange In Powerpoint And Google Slides Cpb Presentation Secure Key Exchange Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric. Secure Key Exchange.
From www.certauri.com
Understanding Secure Key Exchange Protocols An Expert Guide Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From www.researchgate.net
Secure Key Exchange Protocol Download Scientific Diagram Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric. Secure Key Exchange.
From www.freepik.com
Premium AI Image Quantum cryptography's secure key exchange Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From github.com
GitHub pubnub/securekeyexchange Babel Encrypted Self Destructing Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From www.linkedin.com
Secure Key Exchange EndtoEnd Encryption Secure Key Exchange Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric. Secure Key Exchange.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From www.slideserve.com
PPT Mutual Authentication and Key Exchange Protocol (MAKEP Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From cheapsslsecurity.com
What is SSL/TLS Handshake? How Does TLS Work? Quick Guide Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric. Secure Key Exchange.
From www.slideserve.com
PPT Protocol Verification & Secure Key Exchange PowerPoint Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From www.researchgate.net
STFTP's Secure Key Exchange and Data Encryption Protocol. Download Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From eureka.patsnap.com
Method and system for performing perfectly secure key exchange and Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.preveil.com
What’s the best way to send and receive encrypted email? PreVeil Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric. Secure Key Exchange.
From www.keyfactor.com
Demystifying the TLS Handshake What it is and how it works Keyfactor Secure Key Exchange Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric. Secure Key Exchange.
From www.slideserve.com
PPT Proving Security Protocols Correct— Correctly PowerPoint Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From gamma.app
Secure Key Exchange with DiffieHellman Algorithm Secure Key Exchange Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. How can you securely exchange information with someone if you haven’t had the opportunity. Secure Key Exchange.
From www.youtube.com
Secure Text Transfer using DiffieHellman Key Exchange based on Cloud Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric cryptography to encrypt and decrypt their messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From medium.com
An Efficient and Secure Key Exchange Method X25519 and Blake2b by Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From www.101howto.com
Understanding Key Exchange Your Guide to Digital Secrecy Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.researchgate.net
Secure key exchange technique Download Scientific Diagram Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. The two parties use symmetric. Secure Key Exchange.
From www.simplilearn.com.cach3.com
Guide to the DiffieHellman Key Exchange Algorithm & its Working Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique. Secure Key Exchange.
From www.freepik.com
Premium AI Image Quantum cryptography's secure key exchange Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From www.electronicsforu.com
Quantum Key Distribution The Future Of Secure Communication Secure Key Exchange The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique symmetric key for encrypting and decrypting messages. How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication. Secure Key Exchange.
From studylib.net
Protocol Verification & Secure Key Exchange Secure Key Exchange How can you securely exchange information with someone if you haven’t had the opportunity to share the key ahead of time? Secure key exchange is essential for establishing a secure communication channel in systems relying on symmetric encryption. The two parties use symmetric cryptography to encrypt and decrypt their messages. Communicating parties use the shared secret to create a unique. Secure Key Exchange.