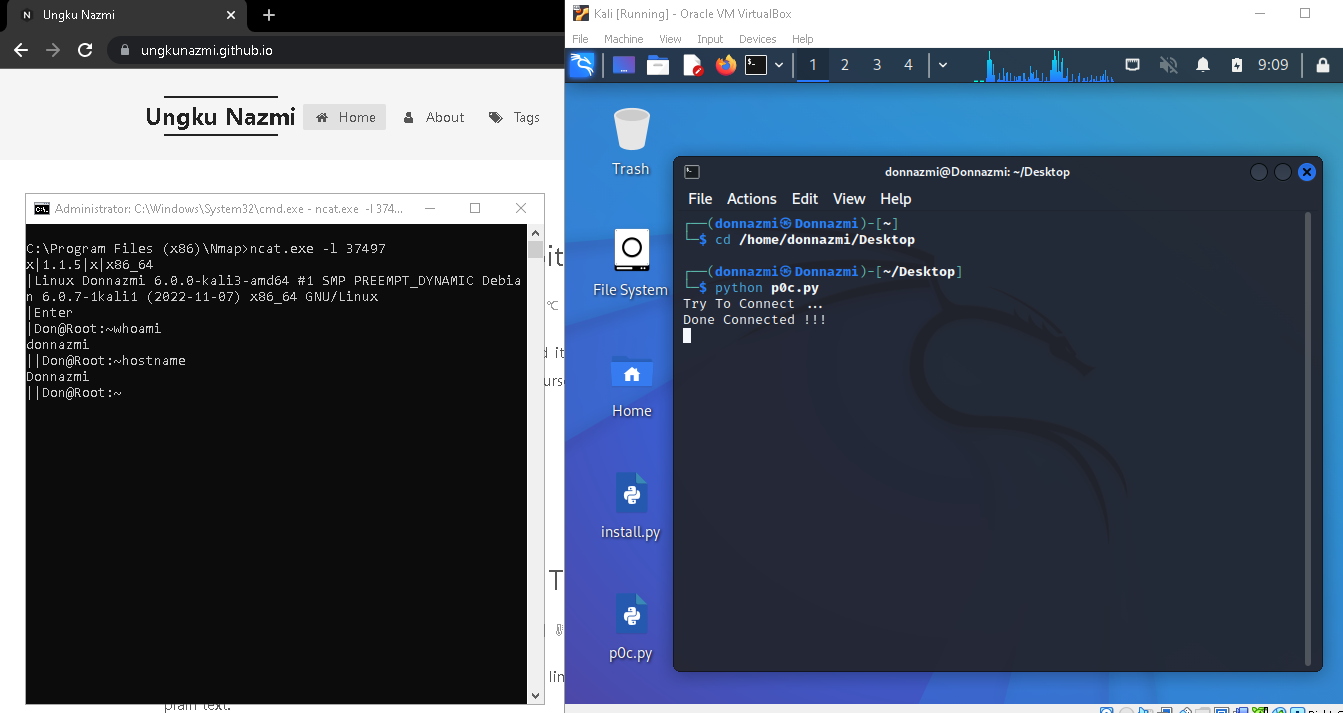
How To Stop Reverse Shell . Meet any email demanding urgent action with scrutiny—including. How to prevent reverse shell attacks. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Audit and test software regularly. Learn how attackers use server initiated connections and other clever. How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. Best practices for preventing reverse shell attacks. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks:
from ungkunazmi.github.io
Meet any email demanding urgent action with scrutiny—including. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Best practices for preventing reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. How to prevent reverse shell attacks. Learn how attackers use server initiated connections and other clever. Audit and test software regularly. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital.
What Are Reverse Shells? Ungku Nazmi
How To Stop Reverse Shell Organizations should do the following to prevent attackers from setting up reverse shells:. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Audit and test software regularly. Learn how attackers use server initiated connections and other clever. How to prevent reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. Best practices for preventing reverse shell attacks. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. How to prevent reverse shell attacks. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Organizations should do the following to prevent attackers from setting up reverse shells:.
From www.invicti.com
What Are Reverse Shells? Invicti How To Stop Reverse Shell Audit and test software regularly. Learn how attackers use server initiated connections and other clever. Organizations should do the following to prevent attackers from setting up reverse shells:. Best practices for preventing reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking. How To Stop Reverse Shell.
From www.scaler.com
What are Shells? (Reverse vs Bind) Scaler Topic How To Stop Reverse Shell Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. Audit and test software regularly. If we can prevent an attacker from executing code. How To Stop Reverse Shell.
From tcm-sec.com
Things to Try When your Reverse Shell Fails TCM Security How To Stop Reverse Shell How to prevent reverse shell attacks. Learn how attackers use server initiated connections and other clever. Organizations should do the following to prevent attackers from setting up reverse shells:. Meet any email demanding urgent action with scrutiny—including. How to prevent reverse shell attacks. Best practices for preventing reverse shell attacks. Audit and test software regularly. If we can prevent an. How To Stop Reverse Shell.
From www.youtube.com
Bind Shell Vs Reverse Shell In Hindi Hacking Course Zero to Hero How To Stop Reverse Shell Meet any email demanding urgent action with scrutiny—including. Best practices for preventing reverse shell attacks. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your. How To Stop Reverse Shell.
From www.hackingarticles.in
Easy way to Generate Reverse Shell Hacking Articles How To Stop Reverse Shell Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. How to prevent reverse shell attacks. Best practices for preventing reverse shell attacks. Audit and test software regularly. Organizations should do the following to prevent attackers from setting up reverse shells:. If we can prevent an attacker from executing code on your machine,. How To Stop Reverse Shell.
From blog.finxter.com
Python One Line Reverse Shell Be on the Right Side of Change How To Stop Reverse Shell Meet any email demanding urgent action with scrutiny—including. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: How to prevent reverse shell attacks. How to prevent reverse shell attacks. Audit and. How To Stop Reverse Shell.
From teracourses.com
فيديو 19 Bind Shell & Reverse Shell How To Stop Reverse Shell Best practices for preventing reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. How to prevent reverse shell attacks. Learn how attackers use server initiated connections and other clever. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Audit and test software regularly. As reverse shells. How To Stop Reverse Shell.
From in.pinterest.com
REVERSE SHELL CHEAT SHEET Cheat sheets, Cheating, Coder How To Stop Reverse Shell Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Organizations should do the following to prevent attackers from setting up reverse shells:. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: If we can prevent an attacker from executing code. How To Stop Reverse Shell.
From www.techslang.com
What is a Reverse Shell? — Definition by Techslang How To Stop Reverse Shell Organizations should do the following to prevent attackers from setting up reverse shells:. How to prevent reverse shell attacks. Audit and test software regularly. How to prevent reverse shell attacks. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Best practices for preventing reverse shell attacks. If we. How To Stop Reverse Shell.
From www.techtarget.com
What reverse shell attacks are and how to prevent them TechTarget How To Stop Reverse Shell Best practices for preventing reverse shell attacks. Audit and test software regularly. Learn how attackers use server initiated connections and other clever. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. Teach your team to take a few of the following steps to keep your entire. How To Stop Reverse Shell.
From slideplayer.com
Reverse Shell. ppt download How To Stop Reverse Shell Best practices for preventing reverse shell attacks. Learn how attackers use server initiated connections and other clever. How to prevent reverse shell attacks. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse. How To Stop Reverse Shell.
From www.yeahhub.com
Linux reverse shell tutorial Yeah Hub How To Stop Reverse Shell How to prevent reverse shell attacks. How to prevent reverse shell attacks. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. If we can prevent. How To Stop Reverse Shell.
From www.manageengine.com
Decoding reverse shell attacks Attack detection How To Stop Reverse Shell Best practices for preventing reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: How to prevent reverse shell attacks. Attackers compromise target. How To Stop Reverse Shell.
From keepcoding.io
Reverse shell vía inyección de comandos How To Stop Reverse Shell How to prevent reverse shell attacks. Audit and test software regularly. Best practices for preventing reverse shell attacks. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. As reverse shells pose a significant. How To Stop Reverse Shell.
From morioh.com
How to make Reverse Shell using Python [2021] How To Stop Reverse Shell Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Learn how attackers use server initiated connections and other clever. How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. Attackers compromise target systems by remote code execution that exploits. How To Stop Reverse Shell.
From www.youtube.com
reverse shell with bash on any unfiltered port YouTube How To Stop Reverse Shell Audit and test software regularly. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. How to prevent reverse shell attacks. Best practices for preventing reverse shell attacks. As reverse shells pose. How To Stop Reverse Shell.
From motasem-notes.net
Reverse and Bind Shells Basics TryHackMe What the Shell? How To Stop Reverse Shell How to prevent reverse shell attacks. Best practices for preventing reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Learn how attackers use server initiated connections and other clever. How to prevent. How To Stop Reverse Shell.
From www.youtube.com
From IP to Reverse Shell. What is a reverse shell? YouTube How To Stop Reverse Shell Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Learn how attackers use server initiated connections and other clever. How to prevent reverse shell attacks. How to prevent reverse shell attacks.. How To Stop Reverse Shell.
From kirelos.com
How to create reverse shells with netcat in linux? Kirelos Blog How To Stop Reverse Shell How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. How to prevent reverse shell attacks. Audit and test software regularly. Learn how attackers use server initiated connections and other clever. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse. How To Stop Reverse Shell.
From gridinsoft.com
Reverse Shell vs. Backdoor What is the Differences? How To Stop Reverse Shell How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. How to prevent reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports.. How To Stop Reverse Shell.
From www.youtube.com
The best reverse shell?! (Easy!) YouTube How To Stop Reverse Shell Audit and test software regularly. How to prevent reverse shell attacks. How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Teach your team to take a few of the following steps to keep. How To Stop Reverse Shell.
From www.youtube.com
How Does A Reverse Shell Works? remote access to target using netcat How To Stop Reverse Shell If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Organizations should do the following to prevent attackers from setting up reverse shells:. Meet any email demanding urgent action with scrutiny—including. Best practices for preventing reverse shell attacks. As reverse shells pose a significant threat to network security, taking. How To Stop Reverse Shell.
From github.com
GitHub punyaslokdutta/ReverseShellscripts A reverse shell is a How To Stop Reverse Shell How to prevent reverse shell attacks. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. How to prevent reverse shell attacks. Learn how attackers use server initiated. How To Stop Reverse Shell.
From www.wallarm.com
What is Reverse Shell? Meaning and Example How To Stop Reverse Shell Learn how attackers use server initiated connections and other clever. Audit and test software regularly. Organizations should do the following to prevent attackers from setting up reverse shells:. How to prevent reverse shell attacks. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Attackers compromise target systems by. How To Stop Reverse Shell.
From www.youtube.com
🟡 Cómo Hacer una REVERSE SHELL en LINUX Pentesting con Reverse Shell How To Stop Reverse Shell Learn how attackers use server initiated connections and other clever. Best practices for preventing reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. How to prevent reverse shell attacks. Organizations should do the following to prevent attackers from setting up reverse shells:. Teach your team to take a few of the following steps to keep your entire organization. How To Stop Reverse Shell.
From www.stationx.net
Reverse Shell Cheat Sheet 2024 A Hacking Guide How To Stop Reverse Shell Best practices for preventing reverse shell attacks. How to prevent reverse shell attacks. Meet any email demanding urgent action with scrutiny—including. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Learn how attackers use server initiated connections and other clever. As reverse shells pose a significant threat to network security, taking proactive. How To Stop Reverse Shell.
From www.geeksforgeeks.org
How to use a Reverse Shell in Metasploit in Kali Linux How To Stop Reverse Shell If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Best practices for preventing reverse shell attacks. Audit and test software regularly. Learn how attackers use server initiated connections and other clever.. How To Stop Reverse Shell.
From www.stationx.net
Reverse Shell Cheat Sheet 2023 A Quick Hack Reference Guide How To Stop Reverse Shell Organizations should do the following to prevent attackers from setting up reverse shells:. How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of. How To Stop Reverse Shell.
From www.vrogue.co
A Reverse Shell With Python Axju vrogue.co How To Stop Reverse Shell Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: Best practices for preventing reverse shell attacks. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. If we can prevent an attacker from executing code on your machine, we eliminate almost. How To Stop Reverse Shell.
From cocomelonc.github.io
Reverse shells How To Stop Reverse Shell Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Audit and test software regularly. Meet any email demanding urgent action with scrutiny—including. As reverse shells pose a. How To Stop Reverse Shell.
From github.com
GitHub evanstella/TTYReverseShellPHP A reverse shell How To Stop Reverse Shell Audit and test software regularly. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Meet any email demanding urgent action with scrutiny—including. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: How to prevent reverse shell. How To Stop Reverse Shell.
From cocomelonc.github.io
Simple C++ reverse shell for windows How To Stop Reverse Shell Organizations should do the following to prevent attackers from setting up reverse shells:. Best practices for preventing reverse shell attacks. How to prevent reverse shell attacks. As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. Teach your team to take a few of the following steps. How To Stop Reverse Shell.
From andreafortuna.org
Some thoughts about reverse shells Andrea Fortuna How To Stop Reverse Shell Meet any email demanding urgent action with scrutiny—including. Best practices for preventing reverse shell attacks. How to prevent reverse shell attacks. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Audit and test software regularly. Learn how attackers use server initiated connections and other clever. Attackers compromise target. How To Stop Reverse Shell.
From ungkunazmi.github.io
What Are Reverse Shells? Ungku Nazmi How To Stop Reverse Shell As reverse shells pose a significant threat to network security, taking proactive measures to prevent their execution is essential for safeguarding your digital. If we can prevent an attacker from executing code on your machine, we eliminate almost all possibilities of a reverse shell. Learn how attackers use server initiated connections and other clever. Best practices for preventing reverse shell. How To Stop Reverse Shell.
From www.geeksforgeeks.org
How to use a Reverse Shell in Metasploit in Kali Linux How To Stop Reverse Shell Best practices for preventing reverse shell attacks. Audit and test software regularly. Attackers compromise target systems by remote code execution that exploits system vulnerabilities—e.g., port forwarding and open ports. Teach your team to take a few of the following steps to keep your entire organization safe from reverse shell attacks: If we can prevent an attacker from executing code on. How To Stop Reverse Shell.