Hardware Key Aws . Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws cloudhsm gives you full control of the algorithms and keys you use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can generate, store, import, export, manage, and use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring.
from paladincloud.io
Aws kms provides you with. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws cloudhsm gives you full control of the algorithms and keys you use. You can generate, store, import, export, manage, and use. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication.
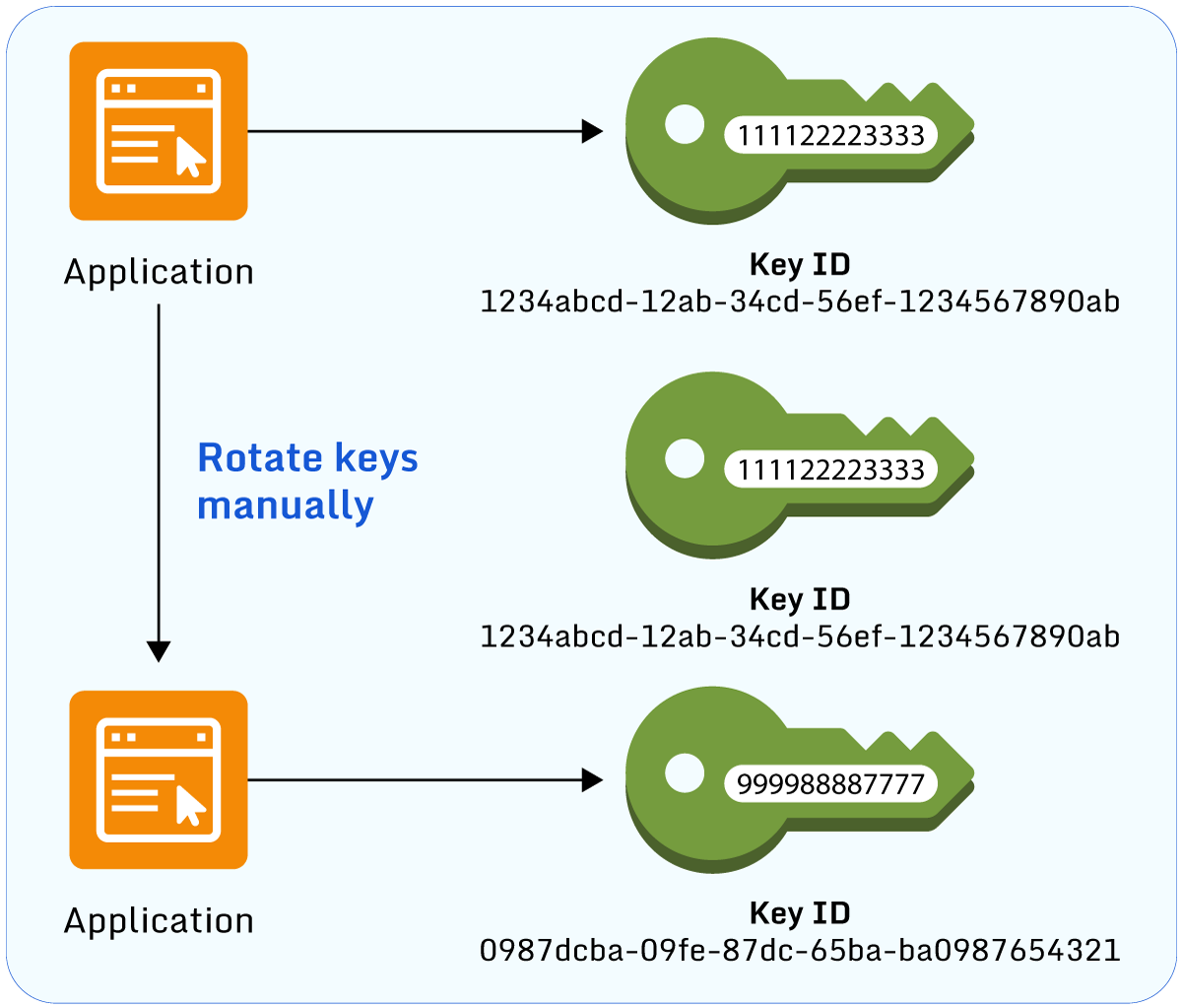
How to rotate keys with AWS KMS Paladin Cloud
Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can generate, store, import, export, manage, and use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws cloudhsm gives you full control of the algorithms and keys you use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication.
From docs.aws.amazon.com
External key stores AWS Key Management Service Hardware Key Aws You can generate, store, import, export, manage, and use. Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads,. Hardware Key Aws.
From blog.awsfundamentals.com
AWS MFA Secure Your Account with MultiFactor Authentication Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can generate, store, import, export, manage, and use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. You. Hardware Key Aws.
From morioh.com
AWS Key Management Service (KMS) Data Encryption AWS Tutorial Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws kms provides you with. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can generate, store,. Hardware Key Aws.
From aws.amazon.com
AWS CloudHSM Update Cost Effective Hardware Key Management at Cloud Hardware Key Aws Aws kms provides you with. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. You can generate, store, import, export, manage, and use. Discover how. Hardware Key Aws.
From k21academy.com
How To Create Access Keys And Secret Keys In AWS Hardware Key Aws Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Use aws kms to encrypt. Hardware Key Aws.
From aws.amazon.com
CloudHSM best practices to maximize performance and avoid common Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Use aws kms to encrypt data across your aws workloads,. Hardware Key Aws.
From www.youtube.com
How to Create AWS Access Key ID and Secret Access Key AWS Access Keys Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can generate, store, import, export, manage, and use. Aws cloudhsm gives you full control of the algorithms and keys you use. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the. Hardware Key Aws.
From www.businesswire.com
Yubico Announces YubiHSM 2 Integration With AWS IoT Greengrass Hardware Key Aws You can generate, store, import, export, manage, and use. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using. Hardware Key Aws.
From www.youtube.com
How to get AWS access key and secret key id YouTube Hardware Key Aws Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication.. Hardware Key Aws.
From support.kochava.com
AWS Access and Secret Keys Hardware Key Aws Aws kms provides you with. You can generate, store, import, export, manage, and use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws cloudhsm gives you full control of the algorithms and keys you use. You can enable a hardware totp. Hardware Key Aws.
From velog.io
[AWS SAA] S3 Encryption Hardware Key Aws You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. You can generate, store, import, export, manage, and use. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Discover how hardware security modules (hsms) fortify cloud security by. Hardware Key Aws.
From lifesciences-resources.awscloud.com
Reducing AWS Key Management Service costs by up to 99 with S3 Bucket Keys Hardware Key Aws Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with. You can generate, store, import, export, manage, and use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using. Hardware Key Aws.
From www.decodingdevops.com
How To Create AWS Access Key and Secret Key DecodingDevops Hardware Key Aws You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can generate, store, import, export, manage, and use. Use aws kms to encrypt data across your aws workloads, digitally sign data,. Hardware Key Aws.
From nerdyelectronics.com
Create AWS Access key ID and secret access key NerdyElectronics Hardware Key Aws Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with.. Hardware Key Aws.
From teachmyselfcloud.com
Teach Myself Cloud AWS VPC Hardware Key Aws You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. You can generate, store, import, export, manage, and use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Discover how hardware security modules (hsms) fortify cloud security by safeguarding. Hardware Key Aws.
From digitalcloud.training
AWS KMS AWS Cheat Sheet Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can generate, store, import, export, manage, and use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Use. Hardware Key Aws.
From www.youtube.com
How to Setup MFA on AWS Account (Root User) YouTube Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can generate, store, import, export, manage, and use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws. Hardware Key Aws.
From www.youtube.com
Thetis Security Key Setup For AWS (Amazon Services) YouTube Hardware Key Aws Aws kms provides you with. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within. Hardware Key Aws.
From letmetechyou.com
Create an aws key pair using terraform Let Me Tech You Hardware Key Aws Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use.. Hardware Key Aws.
From browndragon105.weebly.com
Generate Access Key And Secret Key Aws browndragon Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. You can generate, store, import, export, manage, and use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws key management service (kms) gives you control over the cryptographic. Hardware Key Aws.
From www.scaler.com
AWS Access Key Scaler Topics Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws kms provides you with. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws cloudhsm gives you full control of the algorithms and keys you use. You can generate, store, import, export, manage, and use. You. Hardware Key Aws.
From k21academy.com
How to Configure & Install AWS CLI Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Use aws. Hardware Key Aws.
From www.tpsearchtool.com
What Is Aws Architecture Components Explained With Diagram Images Hardware Key Aws You can generate, store, import, export, manage, and use. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws kms provides you with. Use aws kms to encrypt data. Hardware Key Aws.
From automateinfra.com
AWS Keys DevOps Automateinfra Learning Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Discover how hardware security modules (hsms) fortify. Hardware Key Aws.
From awsteele.com
AWS Access Key ID formats Aidan Steele’s blog (usually about AWS) Hardware Key Aws You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption. Hardware Key Aws.
From aws.amazon.com
Introducing Amazon ECR serverside encryption using AWS Key Management Hardware Key Aws You can generate, store, import, export, manage, and use. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can enable a hardware totp token for an iam user from the aws management console, the command. Hardware Key Aws.
From fivetran.com
AWS CustomerManaged Keys Setup Guide Hardware Key Aws You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws cloudhsm gives you full control of the algorithms and. Hardware Key Aws.
From paladincloud.io
How to rotate keys with AWS KMS Paladin Cloud Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management. Hardware Key Aws.
From www.youtube.com
Configure AWS CLI with Access & Secret Keys YouTube Hardware Key Aws Aws cloudhsm gives you full control of the algorithms and keys you use. Aws kms provides you with. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws. Hardware Key Aws.
From www.youtube.com
What is AWS Key Management Service? Amazon Services YouTube Hardware Key Aws Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Aws key management service (kms) gives you control over the cryptographic keys used to protect. Hardware Key Aws.
From jayendrapatil.com
AWS S3 Encryption Hardware Key Aws Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws kms provides you with. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You can generate, store, import, export, manage, and use. You can enable a hardware totp token for an iam user from the aws. Hardware Key Aws.
From data-flair.training
What is AWS KMS Features of Key Management Services DataFlair Hardware Key Aws You can generate, store, import, export, manage, and use. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Use aws kms to encrypt data across your aws workloads, digitally sign data, encrypt within your applications using aws encryption sdk, and generate and verify message authentication. Discover how hardware security modules (hsms). Hardware Key Aws.
From www.youtube.com
Secure Your AWS API Gateway with API Keys AWS Tutorial YouTube Hardware Key Aws Aws kms provides you with. You can generate, store, import, export, manage, and use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. Aws cloudhsm gives you full control of the algorithms and keys you use. You. Hardware Key Aws.
From www.youtube.com
How to get AWS access key and secret key id for s3 YouTube Hardware Key Aws You can generate, store, import, export, manage, and use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws kms provides you with. Aws cloudhsm gives you full control. Hardware Key Aws.
From mindmajix.com
What Is AWS KMS Functions Of AWS Key Management Service Hardware Key Aws You can generate, store, import, export, manage, and use. Aws key management service (kms) gives you control over the cryptographic keys used to protect your data. Aws kms provides you with. Aws cloudhsm gives you full control of the algorithms and keys you use. Discover how hardware security modules (hsms) fortify cloud security by safeguarding cryptographic keys & ensuring. You. Hardware Key Aws.