Hunting Process Meaning . threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. in this chapter, i will discuss the process of hunting. threat hunting is the process of detecting and responding to cyber intrusions that network and endpoint security controls. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game and game birds,. headhunting is a direct sourcing methodology which stems from an approach widely used within executive search. Cyber threat hunting digs deep to find. threat indicators are virtual fingerprints left by malware or an attacker, a strange ip address, phishing emails or other unusual. — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. The initial trigger phase, the investigation phase, and. — threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. — job hunting is the process of looking for an occupation. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. — there are 10 critical sales hunting skills every successful hunter possesses. — process of threat hunting. When you are hiring a.
from threatcop.com
threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. — there are 10 critical sales hunting skills every successful hunter possesses. — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. A proactive threat hunting process consists of three stages: — cyber threat hunting is a proactive search for malicious activity in your system. — using a recruiter gives job hunters access to many exclusive opportunities. Cyber threat hunting digs deep to find. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. When you are hiring a.
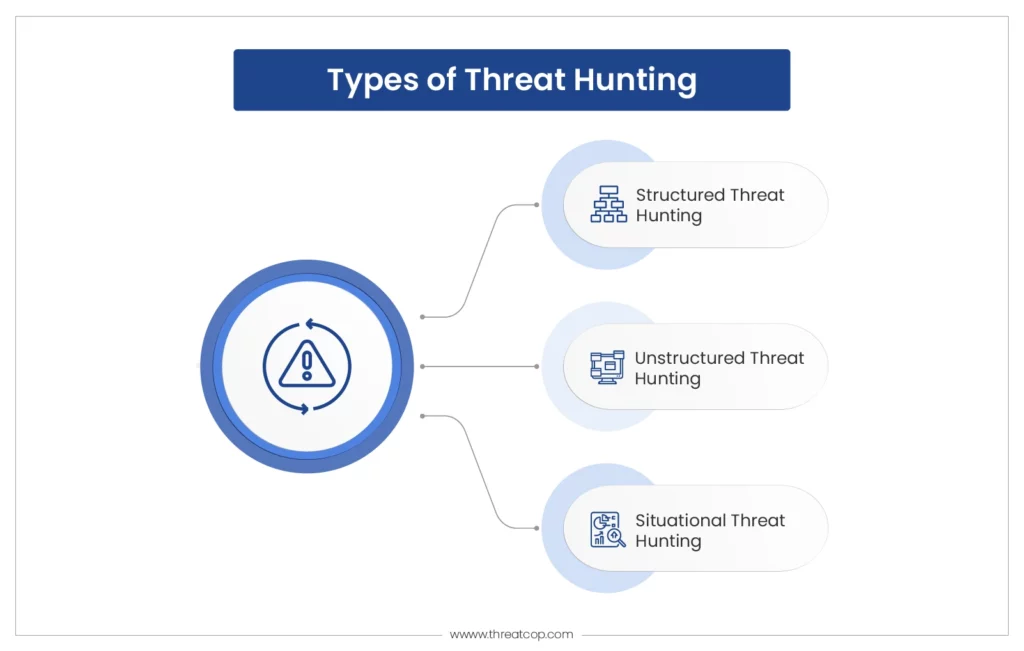
Different Types of Threat Hunting Threatcop
Hunting Process Meaning headhunting is a direct sourcing methodology which stems from an approach widely used within executive search. threat hunting is the process of detecting and responding to cyber intrusions that network and endpoint security controls. threat hunting is an active it security exercise with the intent of finding and rooting out cyber attacks that have penetrated your environment without raising any. a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. People may switch careers, leave toxic workplaces, or learn. — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. — headhunting is a process of recruitment of a prospective employee, who is working elsewhere and who has a relevant. headhunting, which is often referred to as an executive search, is the process of sourcing the best possible candidate for a position. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. — there are 10 critical sales hunting skills every successful hunter possesses. This is an iterative process, similar to engineering or scientific research but. — cyber threat hunting is a proactive search for malicious activity in your system. When you are hiring a. headhunting is a direct sourcing methodology which stems from an approach widely used within executive search. — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about the. — using a recruiter gives job hunters access to many exclusive opportunities.
From www.blusapphire.com
The Complete Guide To Threat Hunting Hunting Process Meaning headhunting, which is often referred to as an executive search, is the process of sourcing the best possible candidate for a position. The initial trigger phase, the investigation phase, and. This is an iterative process, similar to engineering or scientific research but. — job hunting is the process of looking for an occupation. — process of threat. Hunting Process Meaning.
From www.talentlyft.com
Headhunting vs Recruitment What is the Difference? Hunting Process Meaning Threat hunting is a must. This is an iterative process, similar to engineering or scientific research but. — there are 10 critical sales hunting skills every successful hunter possesses. People may switch careers, leave toxic workplaces, or learn. hunting strategy or hunting method is any specific techniques or tactics that are used to target, pursue, and hunt an. Hunting Process Meaning.
From heimdalsecurity.com
Managed Threat Hunting The Next Step from Traditional Cybersecurity Hunting Process Meaning — cyber threat hunting is a proactive search for malicious activity in your system. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. in this chapter, i will discuss the process of hunting. — job hunting is the process of looking for an occupation. threat hunting. Hunting Process Meaning.
From giofpwhgc.blob.core.windows.net
Upland Hunting Meaning at Barbara Weeks blog Hunting Process Meaning This is an iterative process, similar to engineering or scientific research but. — there are 10 critical sales hunting skills every successful hunter possesses. — threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified. Hunting Process Meaning.
From ripjar.com
The Art Of Threat Hunting How To Identify Hidden Threats In Your Hunting Process Meaning threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. threat hunting is the process of detecting and responding to cyber intrusions that network and endpoint security controls. — a technical definition. Hunting Process Meaning.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Hunting Process Meaning — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. headhunting, which is often referred to as an executive search, is the process of sourcing the best possible candidate for a position. — process of threat hunting. People may switch careers, leave toxic workplaces, or learn. a threat. Hunting Process Meaning.
From www.youtube.com
How To Hunt Process and Cook Wild Turkey YouTube Hunting Process Meaning a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. Threat hunting is a must. Cyber threat hunting digs deep to find. — cyber threat hunting is a proactive search for malicious activity. Hunting Process Meaning.
From www.talentlyft.com
Headhunting vs Recruitment What is the Difference? Hunting Process Meaning People may switch careers, leave toxic workplaces, or learn. — cyber threat hunting is a proactive search for malicious activity in your system. — there are 10 critical sales hunting skills every successful hunter possesses. Threat hunting is a must. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game. Hunting Process Meaning.
From skyhawk.security
InfoSec's Top 10 ThreatHunting Tools for 2023 Skyhawk Hunting Process Meaning — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. — using a recruiter gives job hunters access to many exclusive opportunities. People may switch careers, leave toxic workplaces,. Hunting Process Meaning.
From www.zippyops.com
5Step Cyber Threat Hunting Process Hunting Process Meaning threat hunting is a proactive cybersecurity approach that combines digital forensics and incident response tactics to identify unknown and ongoing cyber threats. The initial trigger phase, the investigation phase, and. threat indicators are virtual fingerprints left by malware or an attacker, a strange ip address, phishing emails or other unusual. — hunting in sales is a crucial. Hunting Process Meaning.
From www.bigstockphoto.com
Process Hunting During Image & Photo (Free Trial) Bigstock Hunting Process Meaning — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. hunting strategy or hunting method is any specific techniques or tactics that are used to target, pursue, and hunt an animal. — process of threat hunting. — hunting in sales is a crucial strategy for businesses to expand. Hunting Process Meaning.
From www.linkedin.com
Job Hunting While Working Hunting Process Meaning A proactive threat hunting process consists of three stages: — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about the. This is an iterative process, similar to engineering or scientific research but. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game. Hunting Process Meaning.
From www.atatus.com
Threat Hunting Definition, Process, Methodologies, and More Hunting Process Meaning headhunting is a direct sourcing methodology which stems from an approach widely used within executive search. A proactive threat hunting process consists of three stages: — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and. Hunting Process Meaning.
From dictionary.langeek.co
Definition & Meaning of "Hunt" LanGeek Hunting Process Meaning — job hunting is the process of looking for an occupation. — using a recruiter gives job hunters access to many exclusive opportunities. A proactive threat hunting process consists of three stages: a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. — there are 10 critical sales hunting skills. Hunting Process Meaning.
From www.alamy.com
Head Hunting data infographics visualization. Process chart. Diagram Hunting Process Meaning — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. Threat hunting is a must. People may switch careers, leave toxic workplaces, or learn. A proactive threat hunting process consists of three. Hunting Process Meaning.
From dictionary.langeek.co
Definition & Meaning of "Hunt" LanGeek Hunting Process Meaning A proactive threat hunting process consists of three stages: — using a recruiter gives job hunters access to many exclusive opportunities. — process of threat hunting. — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about the. — threat hunting is the proactive process of identifying and. Hunting Process Meaning.
From sysdig.com
What is Threat Hunting? Sysdig Hunting Process Meaning hunting strategy or hunting method is any specific techniques or tactics that are used to target, pursue, and hunt an animal. threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. The initial trigger phase, the investigation phase, and. — hunting, sport that involves the seeking, pursuing, and killing. Hunting Process Meaning.
From se-scholar.com
Funny Flow Charts — SE Scholar Hunting Process Meaning — job hunting is the process of looking for an occupation. When you are hiring a. A proactive threat hunting process consists of three stages: — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game and game birds,. This is an iterative process, similar to engineering or scientific research but. Cyber. Hunting Process Meaning.
From www.cyberproof.com
What is threat hunting? CyberProof Hunting Process Meaning — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. — process of threat hunting. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and. Hunting Process Meaning.
From www.researchgate.net
Threat Hunting Process from Scratch Download Scientific Diagram Hunting Process Meaning a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. — cyber threat hunting is a proactive search for malicious activity in your system. threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. This is an iterative process, similar to engineering or. Hunting Process Meaning.
From sariyflorenza.pages.dev
Hunt The Wicked 2024 Micki Susanna Hunting Process Meaning threat hunting is the process of detecting and responding to cyber intrusions that network and endpoint security controls. — job hunting is the process of looking for an occupation. — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. headhunting, which is often referred to as. Hunting Process Meaning.
From threatcop.com
Different Types of Threat Hunting Threatcop Hunting Process Meaning hunting strategy or hunting method is any specific techniques or tactics that are used to target, pursue, and hunt an animal. — job hunting is the process of looking for an occupation. threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. — a technical definition of hunting,. Hunting Process Meaning.
From doc.xuehai.net
the job hunting process_文档下载 Hunting Process Meaning — cyber threat hunting is a proactive search for malicious activity in your system. threat hunting is an active it security exercise with the intent of finding and rooting out cyber attacks that have penetrated your environment without raising any. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game. Hunting Process Meaning.
From www.slideteam.net
Five Step Process Of Cyber Threat Hunting Hunting Process Meaning A proactive threat hunting process consists of three stages: — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. threat hunting is a proactive cybersecurity approach that combines digital forensics and incident response tactics to identify unknown and ongoing cyber threats. People may switch careers, leave toxic workplaces, or learn.. Hunting Process Meaning.
From www.researchgate.net
Hunting process, image taken from [41] Download Scientific Diagram Hunting Process Meaning threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. A proactive threat hunting process consists of three stages: — job hunting is the process of looking for an occupation. — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about. Hunting Process Meaning.
From blog.careerangels.eu
How (in)efficient is your job hunting process? Hunting Process Meaning This is an iterative process, similar to engineering or scientific research but. threat indicators are virtual fingerprints left by malware or an attacker, a strange ip address, phishing emails or other unusual. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. threat hunting is a proactive cybersecurity approach. Hunting Process Meaning.
From www.chaossearch.io
Threat Hunting Frameworks and Methodologies An Introductory Guide Hunting Process Meaning — cyber threat hunting is a proactive search for malicious activity in your system. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about the. Cyber threat hunting digs deep. Hunting Process Meaning.
From www.redkettle.co
The efficient hunting toolbox RedKettle Hunting Process Meaning — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. — there are 10 critical sales hunting skills every successful hunter possesses. — using a recruiter gives job hunters access to many exclusive opportunities. — job hunting is the process of looking for an occupation. . Hunting Process Meaning.
From hxescfczs.blob.core.windows.net
Truffle Hunting Alberta at Jacob Pittman blog Hunting Process Meaning — there are 10 critical sales hunting skills every successful hunter possesses. This is an iterative process, similar to engineering or scientific research but. — hunting, sport that involves the seeking, pursuing, and killing of wild animals and birds, called game and game birds,. threat hunting is a proactive cybersecurity approach that combines digital forensics and incident. Hunting Process Meaning.
From www.youtube.com
Hunting Meaning YouTube Hunting Process Meaning Threat hunting is a must. headhunting is a direct sourcing methodology which stems from an approach widely used within executive search. — there are 10 critical sales hunting skills every successful hunter possesses. — process of threat hunting. a threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically. —. Hunting Process Meaning.
From www.dreamstime.com
Handwriting Text Head Hunting. Concept Meaning Process of Recruitment Hunting Process Meaning in this chapter, i will discuss the process of hunting. — job hunting is the process of looking for an occupation. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. — headhunting is a process of recruitment of a prospective employee, who is working elsewhere and who. Hunting Process Meaning.
From www.process.st
Hunting Checklist Process Street Hunting Process Meaning Cyber threat hunting digs deep to find. — a technical definition of hunting, in the context of motion control, is periodic oscillation of the axis about the. — headhunting, which is also referred to as an executive search, is a hiring process that aims to pinpoint candidates. — hunting, sport that involves the seeking, pursuing, and killing. Hunting Process Meaning.
From giofpwhgc.blob.core.windows.net
Upland Hunting Meaning at Barbara Weeks blog Hunting Process Meaning in this chapter, i will discuss the process of hunting. headhunting, which is often referred to as an executive search, is the process of sourcing the best possible candidate for a position. — hunting in sales is a crucial strategy for businesses to expand their reach, build relationships and stay. threat hunting is the practice of. Hunting Process Meaning.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Hunting Process Meaning — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. in this chapter, i will discuss the process of hunting. — cyber threat hunting is a proactive search for malicious activity in your system. threat hunting is an active it security exercise with the intent of finding and. Hunting Process Meaning.
From jeopardylabs.com
The Age of Exploration Jeopardy Template Hunting Process Meaning When you are hiring a. threat hunting is an active it security exercise with the intent of finding and rooting out cyber attacks that have penetrated your environment without raising any. — simply put, headhunting in recruiting refers to the process of seeking and hiring highly qualified candidates for. — process of threat hunting. This is an. Hunting Process Meaning.