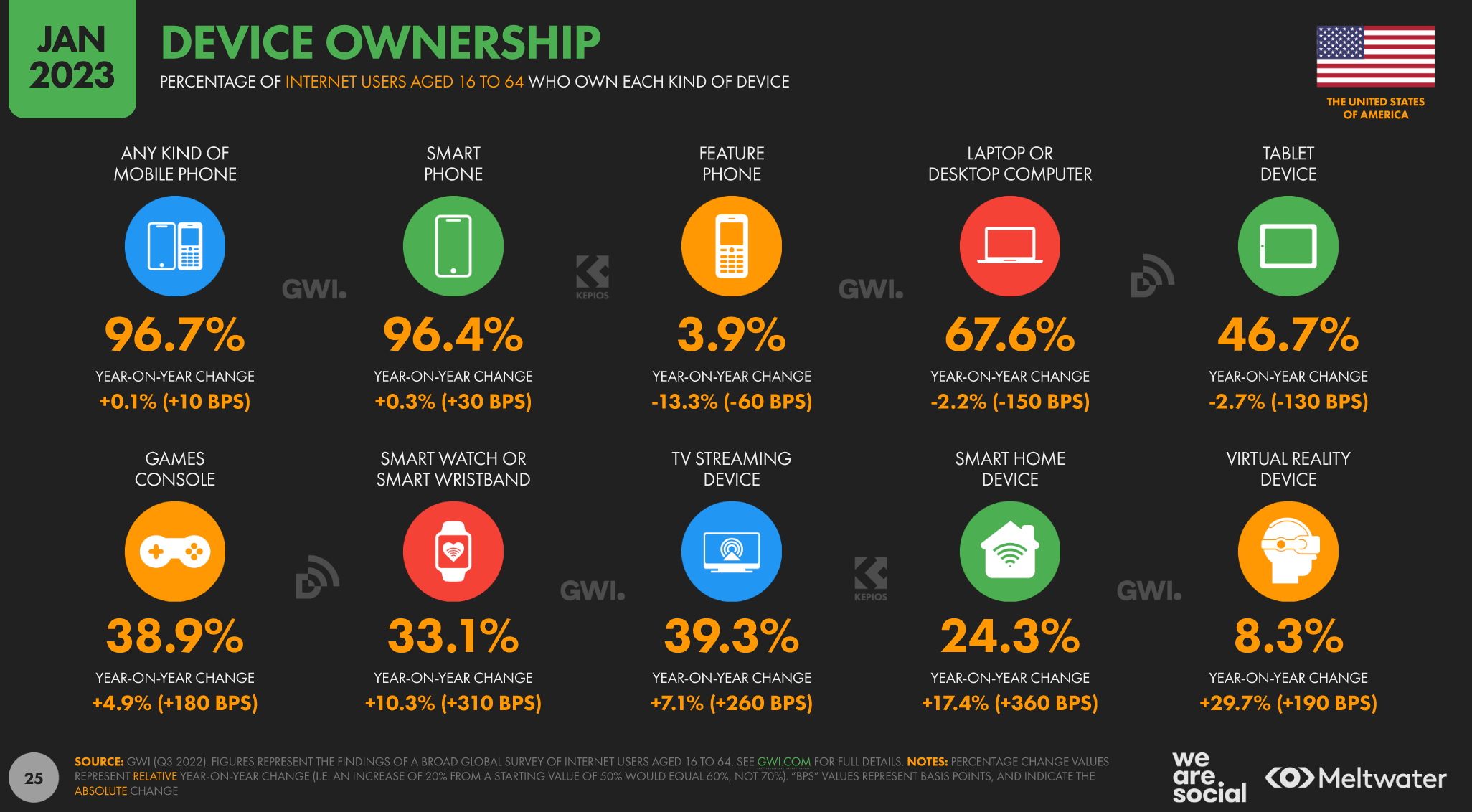
Device Ownership Requirements . Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. To enroll their devices in mdm, users either use their managed apple id or manually. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. There are two types of device enrollment restrictions you can configure in microsoft intune: Once they're enrolled, they receive the policies and profiles you create. Add corporate identifiers in admin center. If a device hasn’t enrolled using one of our true corporate methods, we do.
from www.smartinsights.com
To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods, we do. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. There are two types of device enrollment restrictions you can configure in microsoft intune: Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Add corporate identifiers in admin center. Once they're enrolled, they receive the policies and profiles you create.
Digital marketing statistics sources to inform your marketing strategy
Device Ownership Requirements Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Once they're enrolled, they receive the policies and profiles you create. To enroll their devices in mdm, users either use their managed apple id or manually. There are two types of device enrollment restrictions you can configure in microsoft intune: If a device hasn’t enrolled using one of our true corporate methods, we do. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Add corporate identifiers in admin center.
From iabaustralia.com.au
Device Ownership and Trends Sept. 2016 Nickable Charts Content Device Ownership Requirements There are two types of device enrollment restrictions you can configure in microsoft intune: Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Once they're enrolled, they receive the policies and profiles you create. Add corporate identifiers in admin center. To enroll their devices in. Device Ownership Requirements.
From www.hexnode.com
How to change the ownership of a device? Hexnode Help Center Device Ownership Requirements Once they're enrolled, they receive the policies and profiles you create. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. To enroll their devices in mdm, users either use. Device Ownership Requirements.
From www.researchgate.net
Different forms of device ownership Download Scientific Diagram Device Ownership Requirements Once they're enrolled, they receive the policies and profiles you create. There are two types of device enrollment restrictions you can configure in microsoft intune: Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Add corporate identifiers in admin center. To enroll their devices in. Device Ownership Requirements.
From www.researchgate.net
State of Device Ownership. Download Scientific Diagram Device Ownership Requirements There are two types of device enrollment restrictions you can configure in microsoft intune: To enroll their devices in mdm, users either use their managed apple id or manually. Add corporate identifiers in admin center. Once they're enrolled, they receive the policies and profiles you create. If a device hasn’t enrolled using one of our true corporate methods, we do.. Device Ownership Requirements.
From www.modea.com
10 Digital Front Door Stats We Think You Should Know Modea Device Ownership Requirements There are two types of device enrollment restrictions you can configure in microsoft intune: Add corporate identifiers in admin center. To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods, we do. Today, intune has a variety of methods to identify a device. Device Ownership Requirements.
From www.researchgate.net
Student device ownership rates at Lethbridge College. Download Device Ownership Requirements Today, intune has a variety of methods to identify a device as “corporate” for windows platform. If a device hasn’t enrolled using one of our true corporate methods, we do. To enroll their devices in mdm, users either use their managed apple id or manually. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum. Device Ownership Requirements.
From www.slideshare.net
Regional Fixed and Mobile Device Ownership and Connections Influence Device Ownership Requirements If a device hasn’t enrolled using one of our true corporate methods, we do. To enroll their devices in mdm, users either use their managed apple id or manually. Once they're enrolled, they receive the policies and profiles you create. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices. Device Ownership Requirements.
From gocodes.com
6 Benefits Of Construction Management Software That You Need To Know Device Ownership Requirements Once they're enrolled, they receive the policies and profiles you create. To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods, we do. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices. Device Ownership Requirements.
From blog.tcea.org
Six Ways to Promote Digital Citizenship and Device Ownership Device Ownership Requirements Once they're enrolled, they receive the policies and profiles you create. If a device hasn’t enrolled using one of our true corporate methods, we do. To enroll their devices in mdm, users either use their managed apple id or manually. Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for. Device Ownership Requirements.
From help.ivanti.com
If Change Device Ownership role is enabled Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Add corporate identifiers in admin center. If a device hasn’t enrolled using one of our true corporate methods, we do. Once they're enrolled, they receive the policies and profiles you create. To enroll their devices in. Device Ownership Requirements.
From creatingresults.com
Baby Boomers, Seniors and Technology Device Ownership Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Once they're enrolled, they receive the policies and profiles you create. If a device hasn’t enrolled using one of our true corporate methods, we do. There are two types of device enrollment restrictions you can configure. Device Ownership Requirements.
From www.smartinsights.com
Digital marketing statistics sources to inform your marketing strategy Device Ownership Requirements To enroll their devices in mdm, users either use their managed apple id or manually. There are two types of device enrollment restrictions you can configure in microsoft intune: Today, intune has a variety of methods to identify a device as “corporate” for windows platform. If a device hasn’t enrolled using one of our true corporate methods, we do. Once. Device Ownership Requirements.
From www.statista.com
Chart The evolution of digital device ownership in the UK Statista Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. If a device hasn’t enrolled using one of our true corporate methods, we do. Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for windows platform.. Device Ownership Requirements.
From www.vrogue.co
Change Device Ownership In Microsoft Intune Standalone Using Microsoft Device Ownership Requirements Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. To enroll their devices in mdm, users either use their managed apple id or manually. There are two types of device enrollment restrictions you can configure in microsoft intune: Device trust helps you enforce your enterprise's compliance or. Device Ownership Requirements.
From www.flickriver.com
Figure 1 Device Ownership, 20062013 a photo on Flickriver Device Ownership Requirements To enroll their devices in mdm, users either use their managed apple id or manually. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. If a device hasn’t enrolled using one of our true corporate methods, we do. There are two types of device enrollment restrictions you can configure in microsoft intune: Once. Device Ownership Requirements.
From www.barb.co.uk
Device Ownership Barb Device Ownership Requirements Today, intune has a variety of methods to identify a device as “corporate” for windows platform. To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods, we do. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum. Device Ownership Requirements.
From scottduf.medium.com
About Intune device ownership Corporate vs Personal by Scott Duffey Device Ownership Requirements If a device hasn’t enrolled using one of our true corporate methods, we do. There are two types of device enrollment restrictions you can configure in microsoft intune: Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Once they're enrolled, they receive the policies and profiles you create. Device trust helps you enforce. Device Ownership Requirements.
From help.comodo.com
Change The Ownership Status Of A Device, Endpoint Manager Comodo Device Ownership Requirements To enroll their devices in mdm, users either use their managed apple id or manually. There are two types of device enrollment restrictions you can configure in microsoft intune: Once they're enrolled, they receive the policies and profiles you create. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices. Device Ownership Requirements.
From help.ivanti.com
If Change Device Ownership role is enabled Device Ownership Requirements If a device hasn’t enrolled using one of our true corporate methods, we do. Once they're enrolled, they receive the policies and profiles you create. To enroll their devices in mdm, users either use their managed apple id or manually. Add corporate identifiers in admin center. There are two types of device enrollment restrictions you can configure in microsoft intune:. Device Ownership Requirements.
From www.vectorstock.com
User requirements specifications document paper Vector Image Device Ownership Requirements Add corporate identifiers in admin center. There are two types of device enrollment restrictions you can configure in microsoft intune: If a device hasn’t enrolled using one of our true corporate methods, we do. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Once they're enrolled, they receive the policies and profiles you. Device Ownership Requirements.
From www.ypulse.com
Topline Tech/Device Use & Ownership YPulse Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. To enroll their devices in mdm, users either use their managed apple id or manually. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Add corporate identifiers in admin. Device Ownership Requirements.
From www.youtube.com
Device Ownership campaign YouTube Device Ownership Requirements If a device hasn’t enrolled using one of our true corporate methods, we do. Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. There are two types of device enrollment restrictions you can configure in microsoft intune: Once they're enrolled, they receive the policies and profiles you. Device Ownership Requirements.
From www.techeconomy2030.it
svoddeviceownership Tech Economy 2030 Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Once they're enrolled, they receive the policies and profiles you create. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. If a device hasn’t enrolled using one of our. Device Ownership Requirements.
From digitalopportunity.network
The Importance of Large Device Ownership Digital Opportunity Network Device Ownership Requirements If a device hasn’t enrolled using one of our true corporate methods, we do. There are two types of device enrollment restrictions you can configure in microsoft intune: Add corporate identifiers in admin center. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Device trust helps you enforce your enterprise's compliance or security. Device Ownership Requirements.
From iabaustralia.com.au
Device Ownership and Trends May 2017 Nickable Charts Content Device Ownership Requirements Add corporate identifiers in admin center. To enroll their devices in mdm, users either use their managed apple id or manually. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access. Device Ownership Requirements.
From www.npd.com
5 Fast Facts Speed and Tech Device Ownership The NPD Group Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. There are two types of device enrollment restrictions you can configure in microsoft intune: To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one. Device Ownership Requirements.
From www.researchgate.net
Device ownership history and 2015 projections Download Scientific Diagram Device Ownership Requirements To enroll their devices in mdm, users either use their managed apple id or manually. Once they're enrolled, they receive the policies and profiles you create. There are two types of device enrollment restrictions you can configure in microsoft intune: If a device hasn’t enrolled using one of our true corporate methods, we do. Add corporate identifiers in admin center.. Device Ownership Requirements.
From rizwanranjha.com
Device Ownership in Microsoft Intune? Rizwan Ranjha Device Ownership Requirements Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Add corporate identifiers in admin center. To enroll their devices in mdm, users either use their managed apple id or manually. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access. Device Ownership Requirements.
From iabaustralia.com.au
Device Ownership & Trends January 2018 IAB Australia Device Ownership Requirements To enroll their devices in mdm, users either use their managed apple id or manually. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. Add corporate identifiers in admin center. There are two types of device enrollment restrictions you can configure in microsoft intune: Today,. Device Ownership Requirements.
From digitunity.org
Device Ownership Matters Digitunity Device Ownership Requirements Today, intune has a variety of methods to identify a device as “corporate” for windows platform. Add corporate identifiers in admin center. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. To enroll their devices in mdm, users either use their managed apple id or. Device Ownership Requirements.
From voicebot.ai
Global AI Device Ownership by Country PwC Voicebot.ai Device Ownership Requirements There are two types of device enrollment restrictions you can configure in microsoft intune: To enroll their devices in mdm, users either use their managed apple id or manually. Add corporate identifiers in admin center. If a device hasn’t enrolled using one of our true corporate methods, we do. Today, intune has a variety of methods to identify a device. Device Ownership Requirements.
From iabaustralia.com.au
Connected TV Device Ownership & Usage April 2018 IAB Australia Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods, we do. Add corporate identifiers in admin center. Once. Device Ownership Requirements.
From www.digitalmarketingcommunity.com
Device Ownership And Preferences & Smartphones Importance By Country Device Ownership Requirements Today, intune has a variety of methods to identify a device as “corporate” for windows platform. If a device hasn’t enrolled using one of our true corporate methods, we do. Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. To enroll their devices in mdm,. Device Ownership Requirements.
From www.pymnts.com
shareofconsumersbydeviceownership Device Ownership Requirements Add corporate identifiers in admin center. Once they're enrolled, they receive the policies and profiles you create. Today, intune has a variety of methods to identify a device as “corporate” for windows platform. To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one of our true corporate methods,. Device Ownership Requirements.
From www.access.fda.gov
Register a New Medical Device Facility StepbyStep Instructions Device Ownership Requirements Device trust helps you enforce your enterprise's compliance or security policies by defining a minimum set of requirements for devices used to access box. There are two types of device enrollment restrictions you can configure in microsoft intune: To enroll their devices in mdm, users either use their managed apple id or manually. If a device hasn’t enrolled using one. Device Ownership Requirements.