Access Control Definition Nist . Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. This document provides federal agencies with a definition of attribute based access control (abac). Identity and access management is a fundamental and critical cybersecurity capability. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Abac is a logical access control methodology where authorization to perform a set. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among.
from idn.lombapad.com
Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Identity and access management is a fundamental and critical cybersecurity capability. This document provides federal agencies with a definition of attribute based access control (abac). Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Abac is a logical access control methodology where authorization to perform a set. Simply put, with its focus on foundational and applied research and standards, nist seeks to.
Cybersecurity resources control framework nist engineers system
Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Identity and access management is a fundamental and critical cybersecurity capability. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. This document provides federal agencies with a definition of attribute based access control (abac). An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Abac is a logical access control methodology where authorization to perform a set.
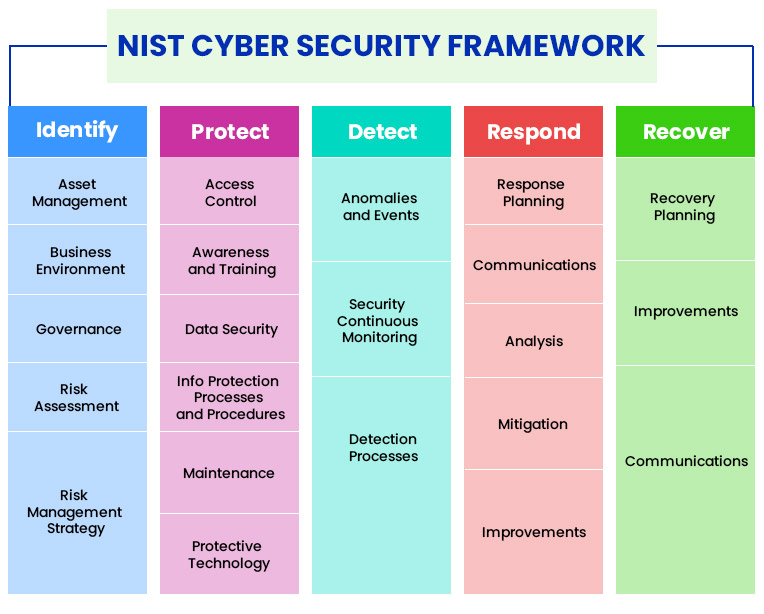
From www.securityscientist.net
20 NIST Control Families Access Control Definition Nist Abac is a logical access control methodology where authorization to perform a set. Simply put, with its focus on foundational and applied research and standards, nist seeks to. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. Access Control Definition Nist.
From campusguard.com
NIST SP 800171 Framework Series Access Control CampusGuard Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. This document provides federal agencies with a definition of attribute. Access Control Definition Nist.
From fortsafe.com
Understanding and Implementing the NIST Framework Access Control Definition Nist This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac is a logical access control methodology where authorization to perform a set. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a.. Access Control Definition Nist.
From www.govinfosecurity.com
NIST Guide Aims to Ease Access Control GovInfoSecurity Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set. Nearly all applications that deal with financial,. Access Control Definition Nist.
From www.g2.com
Access Control Technology Glossary Definitions G2 Access Control Definition Nist An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Identity and access management is a fundamental and critical cybersecurity capability. This document. Access Control Definition Nist.
From dokumen.tips
(PDF) Guide to Attribute Based Access Control (ABAC) Definition and Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Abac is a logical access control methodology where authorization to perform a set. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Nearly all applications that deal with financial, privacy, safety, or. Access Control Definition Nist.
From coggle.it
NIST Assessment of Access Control Systems Coggle Diagram Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac is a logical access control methodology where authorization to perform a set. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. This document provides federal agencies with a definition of attribute based access control (abac). The process of granting. Access Control Definition Nist.
From www.enzoic.com
NIST Password Guidelines Best Practices Revealed Enzoic Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Identity and access management is a fundamental and critical cybersecurity capability. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization). Access Control Definition Nist.
From 3columns.io
NIST Framework Guide for SaaS Security Compliance 3Columns Access Control Definition Nist This document provides federal agencies with a definition of attribute based access control (abac). An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Simply put, with its focus on foundational and applied research and standards, nist. Access Control Definition Nist.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac is a logical access control methodology where authorization to perform a set. Identity and access management is a fundamental and critical cybersecurity capability. The process of. Access Control Definition Nist.
From www.desertcart.com.au
Buy Guide to Attribute Based Access Control (ABAC) Definition and Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. Access Control Definition Nist.
From www.quickintel.com
What is the NIST Cybersecurity Framework (CSF)? Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to. Access Control Definition Nist.
From 34.218.175.242
What is Network Access Control? IT Services CRT Utah Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles,. Access Control Definition Nist.
From www.vrogue.co
Everything You Should Know About The Nist Cybersecuri vrogue.co Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Simply put, with its focus. Access Control Definition Nist.
From www.archtis.com
NIST SP 800162 Attribute Based Access Control (ABAC) Guide archTIS Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied. Access Control Definition Nist.
From www.youtube.com
NIST SP 80053, Revision 5 Security Controls for Information Systems Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set. Simply put, with its focus on foundational and applied research and standards, nist seeks to. This document provides. Access Control Definition Nist.
From www.csi-tools.com
The NIST framework for SAP Access Security, with CSI tools' help. Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Identity and access management is a fundamental and critical. Access Control Definition Nist.
From kanini.com
5 functions of NIST Cybersecurity (CSF) Framework KANINI Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to perform a set. Simply put, with its focus on foundational and applied research and standards, nist seeks to.. Access Control Definition Nist.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Abac is a logical access. Access Control Definition Nist.
From youattest.com
NIST SP 80053 PR.AC1, User Access Reviews and Identity Security Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to perform a set.. Access Control Definition Nist.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Identity and access management is a fundamental and critical cybersecurity capability. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Access controls limit the rights of authorized users, systems, applications, or processes. Access Control Definition Nist.
From www.sunnyvalley.io
What is NIST Cybersecurity Framework? sunnyvalley.io Access Control Definition Nist An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac is a logical access control methodology where authorization to perform a set. This document provides federal agencies with a definition of attribute based access control (abac). Nearly all applications that. Access Control Definition Nist.
From www.nist.gov
Next Generation Access Control System and Process for Controlling Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set.. Access Control Definition Nist.
From www.varonis.com
NIST 80053 Definition and Tips for Compliance Access Control Definition Nist This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Access. Access Control Definition Nist.
From www.computertechreviews.com
What is an Access Control? Definition, Uses and More Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. This document provides federal agencies with a definition of attribute based access control (abac). Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set. The process of granting. Access Control Definition Nist.
From www.youtube.com
NIST CSF PR AC Lesson 7 Access Control YouTube Access Control Definition Nist Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set. This document provides federal agencies with a definition of attribute based access control (abac). An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Access controls limit the rights of authorized users,. Access Control Definition Nist.
From neqterlabs.com
NIST SP 800171 Requirement 3.1 Access Control NeQter Labs Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. The process of granting or denying specific requests to 1) obtain and use. Access Control Definition Nist.
From www.linkedin.com
User Access Control ISO or NIST Standard? Access Control Definition Nist Identity and access management is a fundamental and critical cybersecurity capability. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac. Access Control Definition Nist.
From www.lakeridge.us
Control and Manage Physical Access Devices NIST SP 800171 & CMMC 2.0 Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Nearly all applications that deal with financial, privacy, safety, or defense include some. Access Control Definition Nist.
From cyberhoot.com
Access Control Mechanism CyberHoot Access Control Definition Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Identity and access management is a fundamental and critical cybersecurity capability. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. The process. Access Control Definition Nist.
From viettuans.vn
Network Access Control là gì? Ứng dụng thực tiễn của Network Access Co Access Control Definition Nist An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to perform a set. Identity and access management is a fundamental and critical cybersecurity capability. This document provides federal agencies with a definition of attribute based access control (abac). Access controls limit the rights of authorized users,. Access Control Definition Nist.
From www.youtube.com
Access Control Family What is NIST Access Control (part1) YouTube Access Control Definition Nist This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied research and standards, nist seeks to. Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination. Access Control Definition Nist.
From slidetodoc.com
Chapter 4 Access Control Access Control Definition RFC Access Control Definition Nist Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. Abac is a logical access control methodology where authorization to perform a set. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Nearly all applications that deal with financial, privacy, safety, or defense include some form of. Access Control Definition Nist.
From idn.lombapad.com
Cybersecurity resources control framework nist engineers system Access Control Definition Nist An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to perform a set. The process of granting or denying specific requests to 1) obtain and use information and related information processing services. This document provides federal agencies with a definition of attribute based access control (abac).. Access Control Definition Nist.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard Access Control Definition Nist Nearly all applications that deal with financial, privacy, safety, or defense include some form of access (authorization) control. Access controls limit the rights of authorized users, systems, applications, or processes and prevent unauthorized use of a. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to. Access Control Definition Nist.