Access Control List Group Policy . In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. An access control list (acl) is a tool used to enforce it security policies. However, the wrong acl configuration can severely impact your organization. Learn more about acls and how they are. An access control list (acl) is a list of access control entries (ace). Access control lists are essential elements of an effective network security strategy. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each ace in an acl identifies a trustee and specifies the.
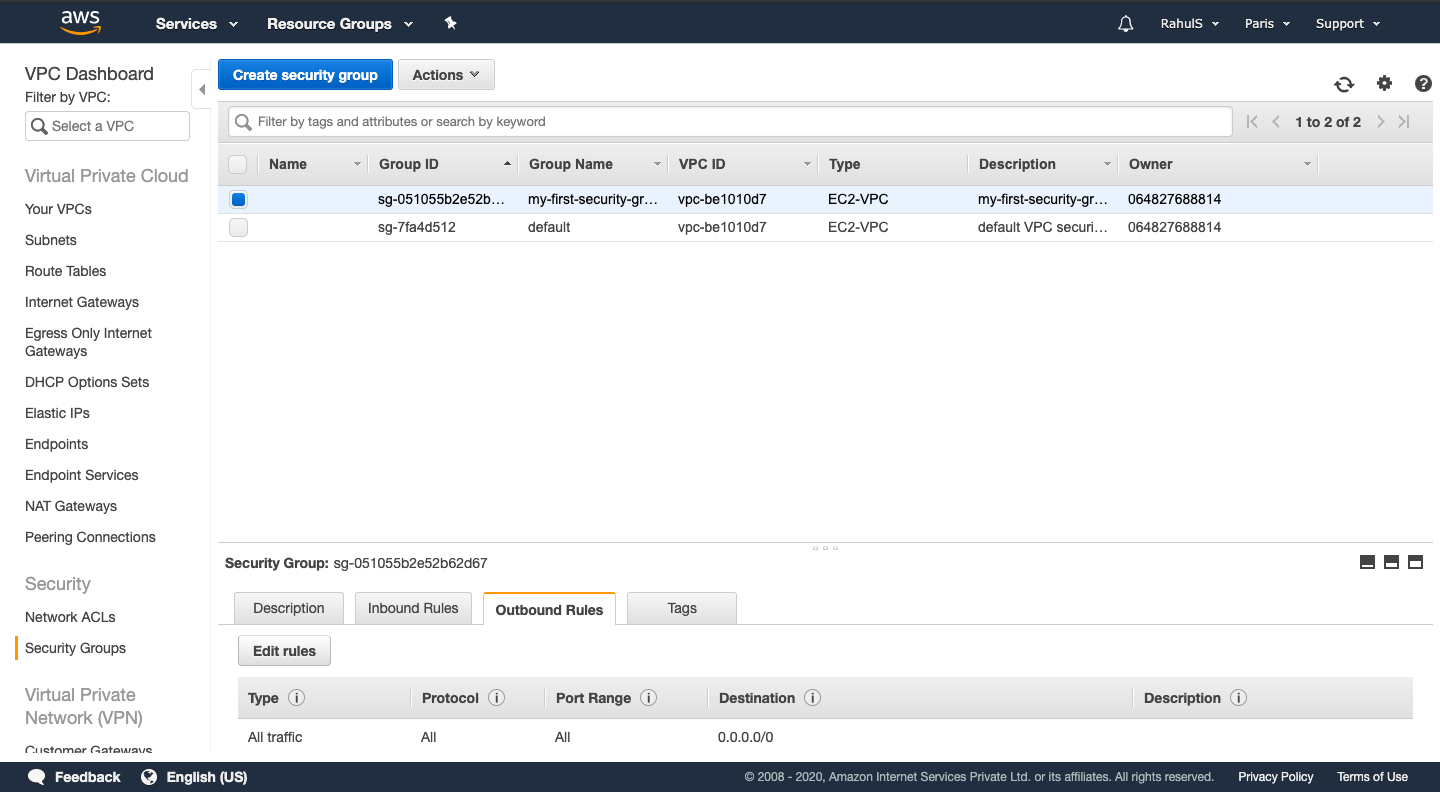
from www.howtoforge.com
In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. However, the wrong acl configuration can severely impact your organization. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. An access control list (acl) is a tool used to enforce it security policies. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Learn more about acls and how they are. Access control lists are essential elements of an effective network security strategy. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each ace in an acl identifies a trustee and specifies the. An access control list (acl) is a list of access control entries (ace).
How to create a Security Group (SG) and Network Access Control List
Access Control List Group Policy Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Learn more about acls and how they are. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Access control lists are essential elements of an effective network security strategy. An access control list (acl) is a tool used to enforce it security policies. An access control list (acl) is a list of access control entries (ace). Each ace in an acl identifies a trustee and specifies the. However, the wrong acl configuration can severely impact your organization. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Access Control List Group Policy Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Each ace in an acl identifies a. Access Control List Group Policy.
From docs.accops.com
Access Control List Accops HySecure 5.4 Knowledge Center Access Control List Group Policy In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. An access control list (acl) is a list of access control entries (ace). An access control list (acl) is a tool used to enforce it security policies. Each permission rule in an acl is known as an access. Access Control List Group Policy.
From www.youtube.com
Microsoft Access How to Group Controls YouTube Access Control List Group Policy Learn more about acls and how they are. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. An access control list, or acl, is a set of rules that determines the level of access a user or system. Access Control List Group Policy.
From www.youtube.com
Learn Access Control List Rules in ServiceNow ServiceNow CSA Tutorial Access Control List Group Policy It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Learn more about acls and how they are. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. An access control list,. Access Control List Group Policy.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Access Control List Group Policy Each ace in an acl identifies a trustee and specifies the. An access control list (acl) is a list of access control entries (ace). An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. In active directory, access control lists are tables,. Access Control List Group Policy.
From www.webservertalk.com
How to Make an Access Control List (ACL) Access Control List Group Policy An access control list (acl) is a list of access control entries (ace). Learn more about acls and how they are. An access control list (acl) is a tool used to enforce it security policies. Access control lists are essential elements of an effective network security strategy. Each permission rule in an acl is known as an access control entry. Access Control List Group Policy.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft Access Control List Group Policy An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Learn more about acls and how they are. An access. Access Control List Group Policy.
From www.lepide.com
Group Policy Examples and Settings for Effective Administration Access Control List Group Policy In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. An access control list (acl) is a tool used to enforce it security policies. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee,. Access Control List Group Policy.
From www.youtube.com
Types of access control lists explained Standard, Extended, Numbered Access Control List Group Policy It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. However, the wrong acl configuration can severely impact your organization. Each permission rule in an acl is known as an access. Access Control List Group Policy.
From budibase.com
RoleBased Access Control Ultimate Guide Access Control List Group Policy An access control list (acl) is a list of access control entries (ace). An access control list (acl) is a tool used to enforce it security policies. Each ace in an acl identifies a trustee and specifies the. Learn more about acls and how they are. It specifies which users or system processes (subjects) are granted access to resources (objects),. Access Control List Group Policy.
From identitymanagementinstitute.org
Access Control Matrix and Capability List Identity Management Institute® Access Control List Group Policy Each ace in an acl identifies a trustee and specifies the. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. An access control list, or acl, is a set of rules that determines the level of access a. Access Control List Group Policy.
From www.isunshare.com
5 Ways to Access Local Group Policy Editor on Windows 10 Access Control List Group Policy Learn more about acls and how they are. An access control list (acl) is a tool used to enforce it security policies. However, the wrong acl configuration can severely impact your organization. Each ace in an acl identifies a trustee and specifies the. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as.. Access Control List Group Policy.
From www.slideteam.net
Logical Access Control Policy Network Measures PPT Sample Access Control List Group Policy Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. In. Access Control List Group Policy.
From www.twingate.com
Access Control Lists (ACLs) How They Work & Best Practices Twingate Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. However, the wrong acl configuration can severely impact your organization. An access control list (acl) is a list of access control entries (ace). It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each permission rule in an acl is known. Access Control List Group Policy.
From www.wallarm.com
What is ACL? Examples and Types of Access Control List Access Control List Group Policy An access control list (acl) is a tool used to enforce it security policies. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. However, the wrong acl configuration can severely impact your organization. Access control lists are essential elements of an effective network security strategy. An access. Access Control List Group Policy.
From dirteam.com
New features in Active Directory Domain Services in Windows Server 2012 Access Control List Group Policy However, the wrong acl configuration can severely impact your organization. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. An access control list (acl). Access Control List Group Policy.
From www.youtube.com
AWS Network Access Control List AWS NACL NACL YouTube Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as.. Access Control List Group Policy.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Access Control List Group Policy An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. An access control list (acl) is a tool used to enforce it security policies. Learn more about acls and how they are. An access control list (acl) is a list of access. Access Control List Group Policy.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Access Control List Group Policy Each ace in an acl identifies a trustee and specifies the. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Access control lists are essential elements of an effective network. Access Control List Group Policy.
From learn.microsoft.com
Deploy and manage Removable Storage Access Control using group policy Access Control List Group Policy In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Each ace in an acl identifies a trustee and specifies the. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or. Access Control List Group Policy.
From frontegg.com
What is RoleBased Access Control RBAC vs ABAC Access Control List Group Policy An access control list (acl) is a list of access control entries (ace). Access control lists are essential elements of an effective network security strategy. Learn more about acls and how they are. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or. Access Control List Group Policy.
From www.freecodecamp.org
What is An ACL? Access Control Lists Explained Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Each ace in an acl identifies a trustee and specifies the. Learn more about acls and how they are. An access control list, or acl, is. Access Control List Group Policy.
From www.rootusers.com
Create and Configure Central Access Rules and Policies RootUsers Access Control List Group Policy An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. However, the wrong acl configuration can severely impact your organization. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. In active directory, access control. Access Control List Group Policy.
From learn.microsoft.com
Create and manage group policy in Microsoft Entra Domain Services Access Control List Group Policy In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. Each ace in an acl identifies a trustee and specifies the. Learn more about acls and how they are. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each permission. Access Control List Group Policy.
From www.youtube.com
Configuration of Access Control Lists on Cisco ASA using ASDM YouTube Access Control List Group Policy Learn more about acls and how they are. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. In active directory, access. Access Control List Group Policy.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. An access control list (acl) is a list of access control entries (ace). Learn more about acls and how they are. An access control list (acl) is a tool used to enforce it security policies. In active directory, access control lists are tables, or simple lists, that define. Access Control List Group Policy.
From medium.com
Difference between Security Groups and Network Access Control List by Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. However, the wrong acl configuration can severely impact your organization. Each ace in an acl identifies a trustee and specifies. Access Control List Group Policy.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft Access Control List Group Policy Access control lists are essential elements of an effective network security strategy. An access control list (acl) is a tool used to enforce it security policies. An access control list (acl) is a list of access control entries (ace). Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by. Access Control List Group Policy.
From learn.microsoft.com
Customize Windows 10 Start and taskbar with group policy Configure Access Control List Group Policy However, the wrong acl configuration can severely impact your organization. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. Access control lists are essential elements of an effective network security strategy. In active directory, access control lists are tables, or simple. Access Control List Group Policy.
From www.howtoforge.com
How to create a Security Group (SG) and Network Access Control List Access Control List Group Policy Learn more about acls and how they are. An access control list (acl) is a tool used to enforce it security policies. However, the wrong acl configuration can severely impact your organization. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. In active directory, access control lists are tables, or simple lists,. Access Control List Group Policy.
From techhay.vn
Amazon S3 Access Control IAM Policies, Bucket Policies and ACLs Access Control List Group Policy An access control list (acl) is a list of access control entries (ace). It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Learn more about acls and how they are. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in.. Access Control List Group Policy.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft Access Control List Group Policy Each ace in an acl identifies a trustee and specifies the. However, the wrong acl configuration can severely impact your organization. Access control lists are essential elements of an effective network security strategy. Learn more about acls and how they are. It specifies which users or system processes (subjects) are granted access to resources (objects), as well as. Each permission. Access Control List Group Policy.
From www.formsbirds.com
Access Control Policy Template 2 Free Templates in PDF, Word, Excel Access Control List Group Policy Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Access control lists are essential elements of an effective network security strategy. In active directory, access control lists are tables, or simple lists, that define the trustees who have. Access Control List Group Policy.
From www.resmo.com
9 Access Control Best Practices Resmo Access Control List Group Policy However, the wrong acl configuration can severely impact your organization. An access control list, or acl, is a set of rules that determines the level of access a user or system has to a particular network or resource. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in.. Access Control List Group Policy.
From www.isunshare.com
5 Ways to Access Local Group Policy Editor on Windows 10 Access Control List Group Policy Each ace in an acl identifies a trustee and specifies the. In active directory, access control lists are tables, or simple lists, that define the trustees who have access to the object in. However, the wrong acl configuration can severely impact your organization. Each permission rule in an acl is known as an access control entry (ace), which controls access. Access Control List Group Policy.