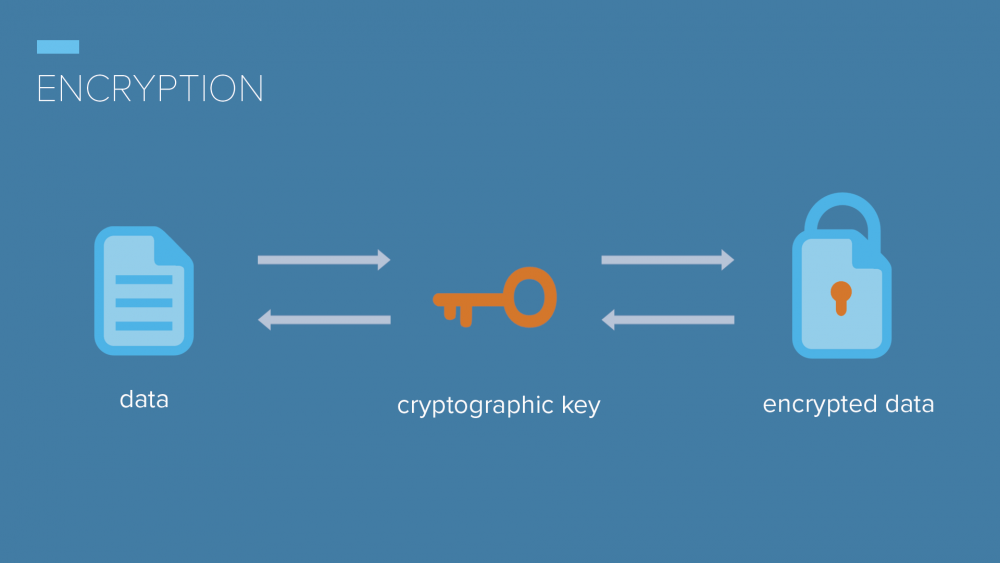
How Are Encryption Keys Stored . Keys must be protected on both volatile and persistent memory, ideally processed. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Cryptographic keys are lumped into two general categories: Symmetric keys = a single. Effective key management is crucial for successful data encryption and the protection of sensitive. There are four basic types of encryption keys: Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as.
from medium.com
Symmetric keys = a single. Effective key management is crucial for successful data encryption and the protection of sensitive. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Keys must be protected on both volatile and persistent memory, ideally processed. Symmetric, asymmetric, public and private. Cryptographic keys are lumped into two general categories: Understand what memory devices the keys are stored on. There are four basic types of encryption keys: Data encrypted by an application that’s running in the customer’s datacenter or by a service application.
What is Encryption & How Does It Work? Search Encrypt Medium
How Are Encryption Keys Stored To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Keys must be protected on both volatile and persistent memory, ideally processed. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. Symmetric keys = a single. There are four basic types of encryption keys: Symmetric, asymmetric, public and private. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Understand what memory devices the keys are stored on. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as.
From docs.microsoft.com
Configure encryption with customermanaged keys stored in Azure Key How Are Encryption Keys Stored When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Cryptographic keys are lumped into two general categories: Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. There are four basic types of encryption keys: Symmetric keys = a single. Keys must be protected on both volatile and. How Are Encryption Keys Stored.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Effective key management is crucial for successful data encryption and the protection of sensitive. Symmetric keys = a single. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive,. How Are Encryption Keys Stored.
From us.norton.com
What is encryption? How it works + types of encryption Norton How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Symmetric keys = a single. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Effective key management is crucial for successful data encryption and the protection of sensitive. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and. How Are Encryption Keys Stored.
From www.encryptionconsulting.com
What is Key Management? How does Key Management work? Encryption How Are Encryption Keys Stored Keys must be protected on both volatile and persistent memory, ideally processed. Effective key management is crucial for successful data encryption and the protection of sensitive. Symmetric, asymmetric, public and private. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Understand what memory devices the keys are stored on. Cryptographic keys are. How Are Encryption Keys Stored.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P How Are Encryption Keys Stored Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Symmetric keys =. How Are Encryption Keys Stored.
From ico.org.uk
Types of encryption ICO How Are Encryption Keys Stored Effective key management is crucial for successful data encryption and the protection of sensitive. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Understand what memory devices the keys are stored on. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Data. How Are Encryption Keys Stored.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed How Are Encryption Keys Stored To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. Data encrypted. How Are Encryption Keys Stored.
From aim4truth.org
All about those encryption keys American Intelligence Media How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Symmetric keys = a single. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Symmetric, asymmetric, public and private. Cryptographic keys are lumped into two general categories: There are four basic types of encryption keys: Keys must be protected on both. How Are Encryption Keys Stored.
From mailtrap.io
Email Encryption AllinOne Guide Mailtrap Blog How Are Encryption Keys Stored Understand what memory devices the keys are stored on. There are four basic types of encryption keys: Cryptographic keys are lumped into two general categories: When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Effective key management is crucial for successful data encryption and the protection of sensitive. Symmetric, asymmetric, public and. How Are Encryption Keys Stored.
From medium.com
What are encryption keys and how do they work? 🔐 CodeClan Medium How Are Encryption Keys Stored When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Symmetric keys = a single. Understand what memory devices the keys are stored on. Effective key management is crucial for successful data encryption and the protection of sensitive. Keys must be protected on both volatile and persistent memory, ideally processed. To manage encryption. How Are Encryption Keys Stored.
From www.clickssl.net
What is Public Key Encryption and How Does It Works? How Are Encryption Keys Stored There are four basic types of encryption keys: Symmetric keys = a single. Understand what memory devices the keys are stored on. Keys must be protected on both volatile and persistent memory, ideally processed. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. When managing encryption keys, choosing the right storage solution is. How Are Encryption Keys Stored.
From www.proofpoint.com
What Is Encryption? Definition, Types & More Proofpoint US How Are Encryption Keys Stored There are four basic types of encryption keys: Keys must be protected on both volatile and persistent memory, ideally processed. Symmetric keys = a single. Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Effective key. How Are Encryption Keys Stored.
From www.klennet.com
Encryption keys in storage encryption How Are Encryption Keys Stored Symmetric, asymmetric, public and private. Cryptographic keys are lumped into two general categories: When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Symmetric keys = a single. Effective key management is crucial for successful data encryption. How Are Encryption Keys Stored.
From www.babypips.com
What is Encryption? How Are Encryption Keys Stored Understand what memory devices the keys are stored on. There are four basic types of encryption keys: Cryptographic keys are lumped into two general categories: Symmetric keys = a single. Effective key management is crucial for successful data encryption and the protection of sensitive. Keys must be protected on both volatile and persistent memory, ideally processed. When managing encryption keys,. How Are Encryption Keys Stored.
From learn.g2.com
What Does Encryption Mean and Why Is It Important? How Are Encryption Keys Stored Symmetric keys = a single. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. When managing encryption keys, choosing the right storage solution is essential to maintaining their. How Are Encryption Keys Stored.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco How Are Encryption Keys Stored Symmetric keys = a single. There are four basic types of encryption keys: When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Understand what memory devices the keys are stored on. Cryptographic keys. How Are Encryption Keys Stored.
From www.themarketinginfo.com
What are Encryption Keys? Definition, Kinds, and More 2021 How Are Encryption Keys Stored Symmetric, asymmetric, public and private. Understand what memory devices the keys are stored on. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Symmetric keys = a single. Effective key management is crucial. How Are Encryption Keys Stored.
From medium.com
What are encryption keys and how do they work? 🔐 CodeClan Medium How Are Encryption Keys Stored Data encrypted by an application that’s running in the customer’s datacenter or by a service application. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Symmetric, asymmetric, public and private. There are four basic types of encryption keys: To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage,. How Are Encryption Keys Stored.
From www.freecodecamp.org
How to Manage Encryption at Scale with Envelope Encryption & Key How Are Encryption Keys Stored When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Keys must be protected on both volatile and persistent memory, ideally processed. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Symmetric keys = a single. Understand what memory devices the keys are stored on. To. How Are Encryption Keys Stored.
From blog.quickapi.cloud
加密初学者指南。 Beginners Guide to Cryptography. Quick博客 How Are Encryption Keys Stored Keys must be protected on both volatile and persistent memory, ideally processed. Symmetric keys = a single. Cryptographic keys are lumped into two general categories: There are four basic types of encryption keys: When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Understand what memory devices the keys are stored on. Effective. How Are Encryption Keys Stored.
From www.assured.enterprises
data encryption key graphic big Assured Enterprises Serious How Are Encryption Keys Stored Cryptographic keys are lumped into two general categories: Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Understand what memory devices the keys are stored on. Effective key management is crucial for successful data encryption and the protection of sensitive. When managing encryption keys, choosing the right storage solution is essential to maintaining. How Are Encryption Keys Stored.
From www.poweradmin.com
A Quick Guide to Encrypted Messaging Network Wrangler Tech Blog How Are Encryption Keys Stored Keys must be protected on both volatile and persistent memory, ideally processed. Effective key management is crucial for successful data encryption and the protection of sensitive. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Cryptographic keys are lumped into two general categories: Understand what memory devices the keys are. How Are Encryption Keys Stored.
From www.slideserve.com
PPT DATA ENCRYPTION STANDARD (DES) PowerPoint Presentation, free How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Symmetric keys = a single. Effective key management is crucial for successful data encryption and the protection of sensitive. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. There are four basic types of encryption keys: Data encrypted by an application that’s running. How Are Encryption Keys Stored.
From www.computertechreviews.com
What are Encryption Keys? Definition, Classifications, And More CTR How Are Encryption Keys Stored When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Effective key management is crucial for successful data encryption and the protection of sensitive. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Symmetric keys = a single. Understand what memory devices the keys are stored. How Are Encryption Keys Stored.
From study.com
Types of Encryption Keys Lesson How Are Encryption Keys Stored Data encrypted by an application that’s running in the customer’s datacenter or by a service application. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Keys must be protected on both volatile and persistent memory, ideally processed. Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. There. How Are Encryption Keys Stored.
From www.sandfield.co.nz
Cryptography 101 Sandfield How Are Encryption Keys Stored Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Symmetric keys = a single. To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Effective key management is crucial for successful data encryption and the protection of sensitive. Symmetric, asymmetric, public and private. Understand. How Are Encryption Keys Stored.
From medium.com
What is Cryptography?. Cryptography is used to secure and… by How Are Encryption Keys Stored There are four basic types of encryption keys: To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Keys must be protected on both volatile and persistent memory, ideally processed. Data encrypted by an. How Are Encryption Keys Stored.
From www.internetsafetystatistics.com
Exploring Encryption Key Examples How Are Encryption Keys Stored There are four basic types of encryption keys: Keys must be protected on both volatile and persistent memory, ideally processed. Symmetric keys = a single. Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. To manage encryption keys effectively,. How Are Encryption Keys Stored.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights How Are Encryption Keys Stored To manage encryption keys effectively, one must address their full lifecycle (generation, use, storage, update, archive, and destruction) as. Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. Symmetric keys = a single. Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive.. How Are Encryption Keys Stored.
From medium.com
What is Encryption & How Does It Work? Search Encrypt Medium How Are Encryption Keys Stored Keys must be protected on both volatile and persistent memory, ideally processed. Symmetric, asymmetric, public and private. Understand what memory devices the keys are stored on. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. There are four basic types of encryption keys: Cryptographic keys are lumped into two general categories: Effective key. How Are Encryption Keys Stored.
From duongnx03.github.io
Encription and Public Keys Duong NX How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Symmetric, asymmetric, public and private. Symmetric keys = a single. Effective key management is crucial for successful data encryption and the protection of sensitive. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. Keys must be protected on both volatile and persistent memory, ideally. How Are Encryption Keys Stored.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity How Are Encryption Keys Stored Symmetric keys = a single. Keys must be protected on both volatile and persistent memory, ideally processed. There are four basic types of encryption keys: Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. To manage encryption keys effectively, one must address their full lifecycle (generation, use,. How Are Encryption Keys Stored.
From stormagic.com
Encryption A Beginner's Guide Start Learning with StorMagic How Are Encryption Keys Stored Understand what memory devices the keys are stored on. Data encrypted by an application that’s running in the customer’s datacenter or by a service application. There are four basic types of encryption keys: When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Keys must be protected on both volatile and persistent memory,. How Are Encryption Keys Stored.
From help.mypurecloud.com
Recording encryption key overview Genesys Cloud Resource Center How Are Encryption Keys Stored Effective key management is crucial for successful data encryption and the protection of sensitive. Understand what memory devices the keys are stored on. When managing encryption keys, choosing the right storage solution is essential to maintaining their security and accessibility. Cryptographic keys are lumped into two general categories: To manage encryption keys effectively, one must address their full lifecycle (generation,. How Are Encryption Keys Stored.
From brightlineit.com
Understanding Encryption Key Management for Businesses Brightline How Are Encryption Keys Stored Symmetric, asymmetric, public and private. There are four basic types of encryption keys: Symmetric keys = a single. Cryptographic keys are lumped into two general categories: Effective key management is crucial for successful data encryption and the protection of sensitive. Understand what memory devices the keys are stored on. Data encrypted by an application that’s running in the customer’s datacenter. How Are Encryption Keys Stored.