Network Device Configuration Standards . Network configuration manager helps you to stay compliant to hipaa standards by: Notifying and keeping a track of user activities on network devices. This document also discusses emerging network configurations that each address a specific security function (e.g.,. The network device must be configured in accordance with the security configuration settings based on dod security. The following guidance will serve to determine the services that should be enabled or disabled: Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices.
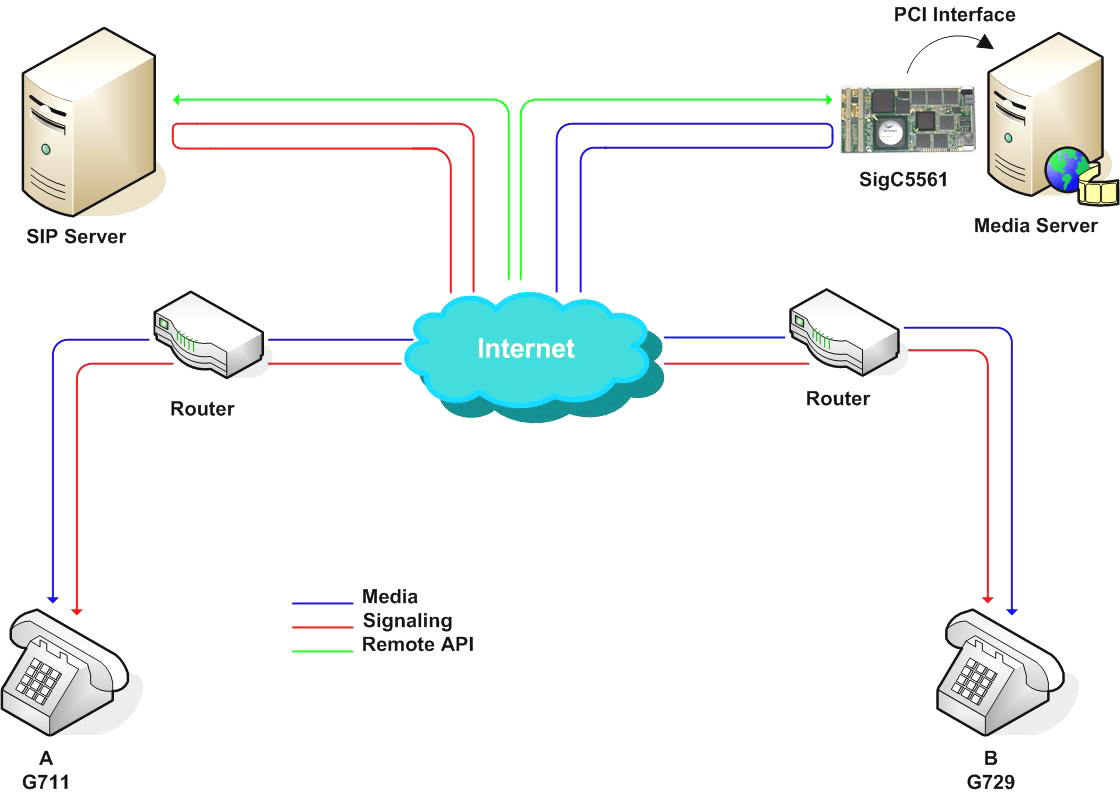
from www.signalogic.com
Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. Notifying and keeping a track of user activities on network devices. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Network configuration manager helps you to stay compliant to hipaa standards by: This document also discusses emerging network configurations that each address a specific security function (e.g.,. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. The following guidance will serve to determine the services that should be enabled or disabled: The network device must be configured in accordance with the security configuration settings based on dod security.
Network Configuration Examples
Network Device Configuration Standards Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Notifying and keeping a track of user activities on network devices. The network device must be configured in accordance with the security configuration settings based on dod security. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The following guidance will serve to determine the services that should be enabled or disabled: This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configuration manager helps you to stay compliant to hipaa standards by: Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices.
From www.packetfence.org
Network Devices Configuration Guide Network Device Configuration Standards Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configuration manager helps you to stay compliant to hipaa standards by: Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Configuration management—configuration aspects of network devices such as configuration file management, inventory. Network Device Configuration Standards.
From novus-computers.com
How to Basic Home Network Setup Network Device Configuration Standards Notifying and keeping a track of user activities on network devices. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The network device must be configured in accordance with the security configuration settings based on dod security. Network configuration manager helps you to stay compliant to hipaa standards by: Many of the standard. Network Device Configuration Standards.
From www.pinterest.com
Standard ACL Configuration Example Cisco Networking Technology, Ccna Network Device Configuration Standards The network device must be configured in accordance with the security configuration settings based on dod security. The following guidance will serve to determine the services that should be enabled or disabled: This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configuration manager helps you to stay compliant to hipaa standards by: Notifying. Network Device Configuration Standards.
From smartnetworkgeek.com
8 Effective Home Network Setup Diagram For Your House In 2023 Smart Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The network device must be configured in accordance with the security configuration settings based on dod security. The following guidance will serve to determine the services that should be enabled or disabled: Network configuration manager helps you to stay compliant to hipaa standards by:. Network Device Configuration Standards.
From www.techjockey.com
What are Computer Network Devices Types, Functions and Usage Network Device Configuration Standards Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. This document also discusses emerging network configurations that. Network Device Configuration Standards.
From softwareportal.com
The 5 Best Network Configuration Management Software & Tools of 2021 Network Device Configuration Standards The network device must be configured in accordance with the security configuration settings based on dod security. The following guidance will serve to determine the services that should be enabled or disabled: Network configuration manager helps you to stay compliant to hipaa standards by: Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure. Network Device Configuration Standards.
From www.scribd.com
Basic Network Device Configuration PDF Ip Address Shell Network Device Configuration Standards The network device must be configured in accordance with the security configuration settings based on dod security. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configuration manager helps you to stay compliant to hipaa standards by: Notifying and keeping a track of user activities on network devices. Many of the standard frameworks. Network Device Configuration Standards.
From www.atatus.com
Network Configuration Management Definition, Benefits, More Network Device Configuration Standards The network device must be configured in accordance with the security configuration settings based on dod security. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Notifying and keeping a track of user activities on network devices. Network configuration manager helps you to stay compliant to hipaa standards by: Configuration management—configuration aspects of network. Network Device Configuration Standards.
From www.researchgate.net
Current Configuration of Network Devices Download Table Network Device Configuration Standards Notifying and keeping a track of user activities on network devices. The network device must be configured in accordance with the security configuration settings based on dod security. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. This document also discusses emerging network configurations that each address a specific security function (e.g.,.. Network Device Configuration Standards.
From desklib.com
Network Device Configuration Study Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Notifying and keeping a track of user activities on network devices. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software. Network Device Configuration Standards.
From ar.inspiredpencil.com
Network Wiring Standards Network Device Configuration Standards The network device must be configured in accordance with the security configuration settings based on dod security. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configuration manager helps you to stay compliant to. Network Device Configuration Standards.
From techhub.hpe.com
Network configuration (available for scheme 2) Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configuration manager helps you to stay compliant to hipaa standards by: Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management.. Network Device Configuration Standards.
From www.youtube.com
2 standard network devices YouTube Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Notifying and keeping a track of user activities on network devices. Network configuration manager helps you to stay compliant to hipaa standards by: The network device must be configured in accordance with the security configuration settings based on dod security. Network configurations (e.g., zero trust. Network Device Configuration Standards.
From www.signalogic.com
Network Configuration Examples Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Network configuration manager helps you to stay compliant to hipaa. Network Device Configuration Standards.
From docs.oracle.com
2.1. Using a Shared Network Configuration Network Device Configuration Standards Network configuration manager helps you to stay compliant to hipaa standards by: This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. The network device must be configured in accordance with the security configuration settings based. Network Device Configuration Standards.
From www.conceptdraw.com
Computer Network Diagrams Local area network (LAN). Computer and Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Network configuration manager helps you to stay compliant to hipaa. Network Device Configuration Standards.
From www.networksecuritytoolkit.org
Chapter 13. Networking Network Device Configuration Standards Notifying and keeping a track of user activities on network devices. The network device must be configured in accordance with the security configuration settings based on dod security. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Configuration management—configuration aspects of network devices such as configuration file management, inventory management,. Network Device Configuration Standards.
From subscription.packtpub.com
Basic networks and their components Network Scanning Cookbook Network Device Configuration Standards This document also discusses emerging network configurations that each address a specific security function (e.g.,. The following guidance will serve to determine the services that should be enabled or disabled: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area. Network Device Configuration Standards.
From www.conceptdraw.com
Rack Diagrams How To use Switches in Network Diagram Computer Network Device Configuration Standards Notifying and keeping a track of user activities on network devices. The network device must be configured in accordance with the security configuration settings based on dod security. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software. Network Device Configuration Standards.
From logicalread.com
6 Tools for Network Configuration Management + Guide SolarWinds Network Device Configuration Standards Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The following guidance will serve to determine the services that should be enabled or disabled: This document also discusses emerging network configurations that each address a specific. Network Device Configuration Standards.
From innovationcenter.zones.com
Innovation Center Network Configuration Management Use Case Network Device Configuration Standards Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. The network device must be configured in accordance with the security configuration settings based on dod security. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Many of the standard frameworks use an umbrella approach. Network Device Configuration Standards.
From www.fiber-optic-cable-sale.com
Dynamic Host Configuration Protocol Archives Fiber Cabling Solution Network Device Configuration Standards This document also discusses emerging network configurations that each address a specific security function (e.g.,. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. Notifying and keeping a track of user activities on network devices. Network configuration manager helps you to stay compliant to hipaa standards by: Many of the standard frameworks use. Network Device Configuration Standards.
From gotowebsecurity.com
Comptia Network+ Tutorial Module 03, Part 02 Wireless Configurations Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Notifying and keeping a track of user activities on network devices. The network device must be configured in accordance with the security configuration settings based on dod security.. Network Device Configuration Standards.
From www.configex.com
ConfigEx Network Configuration Management Network Device Configuration Standards Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configuration manager helps you to stay compliant to hipaa standards by: This document also discusses emerging network configurations that each address a specific security function (e.g.,. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management.. Network Device Configuration Standards.
From nleiva.medium.com
Automating Network Device Configuration Parsing with Ansible Tips and Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. The network device must be configured in accordance with the security configuration settings based on dod security. Network configurations (e.g., zero trust network access [ztna]), and the evolving. Network Device Configuration Standards.
From www.itrelease.com
Types of network devices IT Release Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The network device must be configured in accordance with the security configuration settings based on dod security. Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configuration manager helps you to stay compliant to hipaa. Network Device Configuration Standards.
From www.dnsstuff.com
10 Top Network Configuration Management Tools DNSstuff Network Device Configuration Standards The following guidance will serve to determine the services that should be enabled or disabled: Network configuration manager helps you to stay compliant to hipaa standards by: The network device must be configured in accordance with the security configuration settings based on dod security. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure. Network Device Configuration Standards.
From www.signalogic.com
Network Configuration Examples Network Device Configuration Standards Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Notifying and keeping a track of user activities on network devices. Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. Network configuration manager helps you to stay compliant to hipaa standards by: The following. Network Device Configuration Standards.
From www.researchgate.net
Network configuration for a home network with three different traffic Network Device Configuration Standards Network configuration manager helps you to stay compliant to hipaa standards by: The network device must be configured in accordance with the security configuration settings based on dod security. This document also discusses emerging network configurations that each address a specific security function (e.g.,. The following guidance will serve to determine the services that should be enabled or disabled: Configuration. Network Device Configuration Standards.
From network-byte.com
Cable Color Coding NetworkByte Network Device Configuration Standards Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Notifying and keeping a track of user activities on network devices. The following guidance will serve to determine the services that should be enabled. Network Device Configuration Standards.
From www.youtube.com
Network Configuration LAN WAN configuration network address Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The following guidance will serve to determine the services that should be enabled or disabled: Notifying and keeping a track of user activities on network devices. This document also discusses emerging network configurations that each address a specific security function (e.g.,. Network configurations (e.g.,. Network Device Configuration Standards.
From manualzz.com
Network Devices Configuration Guide Manualzz Network Device Configuration Standards Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Network configuration manager helps you to stay compliant to hipaa standards by: Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. This document also discusses emerging network configurations that each address a specific security. Network Device Configuration Standards.
From www.conceptdraw.com
Draw Network Diagram based on Templates and Examples Network Network Device Configuration Standards Configuration management—configuration aspects of network devices such as configuration file management, inventory management, and software management. The network device must be configured in accordance with the security configuration settings based on dod security. Network configuration manager helps you to stay compliant to hipaa standards by: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat. Network Device Configuration Standards.
From louwrentius.com
Example of a home networking setup with VLANs Network Device Configuration Standards Network configuration manager helps you to stay compliant to hipaa standards by: Many of the standard frameworks use an umbrella approach for recommending configuration baselines and treat all devices. Network configurations (e.g., zero trust network access [ztna]), and the evolving wide area network (wan) infrastructure to provide a. Notifying and keeping a track of user activities on network devices. The. Network Device Configuration Standards.
From tentouchapps.com
Network Diagram Ten Touch Network Device Configuration Standards This document also discusses emerging network configurations that each address a specific security function (e.g.,. The network device must be configured in accordance with the security configuration settings based on dod security. Network configuration manager helps you to stay compliant to hipaa standards by: Notifying and keeping a track of user activities on network devices. Network configurations (e.g., zero trust. Network Device Configuration Standards.