Security Access Review . user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access reviews aid in the detection and prevention of employee access rights misuse. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. User access reviews help organizations limit who has access to critical data. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. access review is an important process for verifying and validating access rights in an organization’s it environment. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access.
from www.cisco.com
a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. User access reviews help organizations limit who has access to critical data. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access reviews aid in the detection and prevention of employee access rights misuse. access review is an important process for verifying and validating access rights in an organization’s it environment.
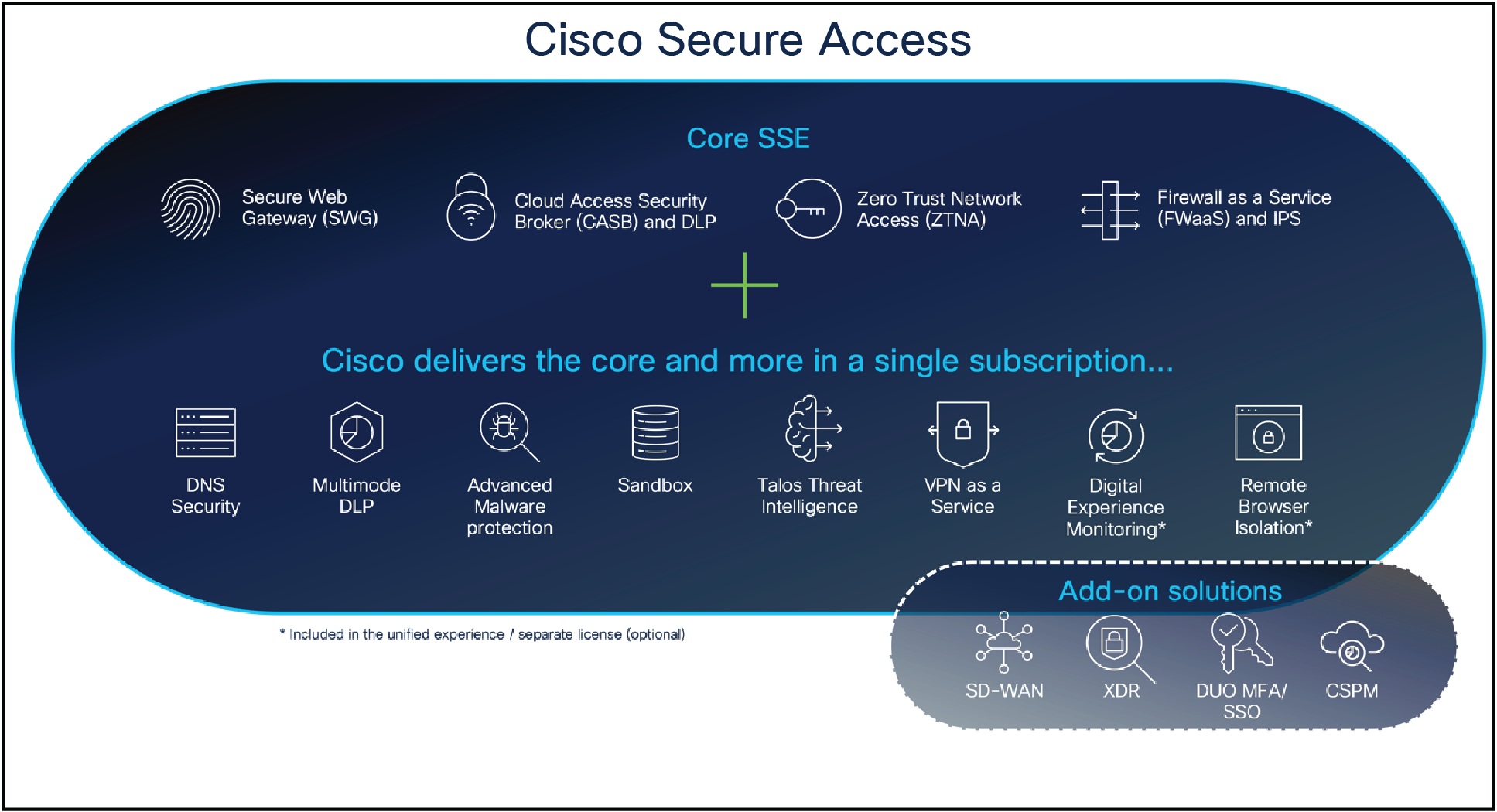
Cisco Secure Access AtaGlance Cisco
Security Access Review access review is an important process for verifying and validating access rights in an organization’s it environment. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. User access reviews help organizations limit who has access to critical data. user access reviews aid in the detection and prevention of employee access rights misuse. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data.
From www.alamy.com
Secure access and online data protection. Data privacy and cyber Security Access Review user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched. Security Access Review.
From www.conceptdraw.com
Network Security Diagrams Network Security Architecture Diagram Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. User access reviews help organizations limit who has access to critical data. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and. Security Access Review.
From cress-security.co.uk
A Deep Dive into Security Access Controls Cress Security Co Security Access Review access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. . Security Access Review.
From www.dreamstime.com
Secure Access To User Private Data with Encryption. Stock Image Image Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews aid in the detection and prevention of employee access rights misuse. User access reviews help organizations limit who has access to critical data. user access reviews. Security Access Review.
From www.nxp.com
Secure Access Rights FAQs NXP Semiconductors Security Access Review a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. User access reviews help organizations limit who has access to critical data. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user. Security Access Review.
From loverlockq.weebly.com
Sandisk secure access review loverlockq Security Access Review a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews aid in the detection. Security Access Review.
From www.idgconnect.com
Secure Access Service Edge (SASE) Which solution is best? IDG Connect Security Access Review user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. User access reviews help organizations limit who has access to critical data. user access reviews are essential to mitigate security threats like privilege. Security Access Review.
From kentonbrothers.com
CPTED Part 2 Natural Surveillance and Natural Access Control Kenton Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. access review is an important process for verifying and validating access rights in an organization’s it environment. user access review process entails periodically reviewing individual user access rights, whereas. Security Access Review.
From aflyertemplate.blogspot.com
User Access Review Template Flyer Template Security Access Review access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential to mitigate security threats like privilege creep,. Security Access Review.
From www.ismena.com
Access Security & Control Ismena website Security Access Review user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. User access reviews help organizations limit who has access to critical data. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. user access reviews are designed to identify and remediate unwanted access,. Security Access Review.
From www.secomea.com
Secure Remote Access for OT & ICS 3 Essential Security Features Security Access Review User access reviews help organizations limit who has access to critical data. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews aid in the detection and prevention of employee. Security Access Review.
From www.agilicus.com
Secure Remote Access through Clientless Zero Trust Architecture Agilicus Security Access Review User access reviews help organizations limit who has access to critical data. access review is an important process for verifying and validating access rights in an organization’s it environment. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are essential for. Security Access Review.
From www.nsa.gov
NSA and CoAuthors Best Practices to Secure Remote Access Security Access Review user access reviews aid in the detection and prevention of employee access rights misuse. User access reviews help organizations limit who has access to critical data. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews. Security Access Review.
From blog.leapp.cloud
How to master and secure access and permissions in an AWS Landing Zone Security Access Review user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access reviews aid in the detection and prevention of employee access rights misuse. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. User access reviews help organizations limit who has access to critical. Security Access Review.
From blogs.cisco.com
Cisco Secure Access is generally available to secure today’s hyper Security Access Review user access reviews aid in the detection and prevention of employee access rights misuse. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. access review is an important process for verifying and validating access rights in an organization’s it environment. User access reviews help. Security Access Review.
From www.documentcloud.org
LIMITED SECURITY ACCESS APPROVAL DocumentCloud Security Access Review user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews aid in the detection and prevention of employee access rights misuse. user access review process entails periodically reviewing individual. Security Access Review.
From www.standardfusion.com
Improving Security With User Access Reviews Security Access Review user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. User access reviews help organizations limit who has access to critical data. user access reviews are designed to. Security Access Review.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Access Review User access reviews help organizations limit who has access to critical data. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user. Security Access Review.
From www.getapp.com
Forcepoint CASB (Cloud Access Security Broker) Pricing, Features Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. a user access review, uar for short, refers to the. Security Access Review.
From redingtongroup.com
Security Redington Security Access Review a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. access review is an important process for verifying and validating access rights in an organization’s it environment. User access reviews help organizations limit who has access to critical data. user access reviews are designed to. Security Access Review.
From www.strongpoint.io
Building Effective Access Controls in NetSuite Strategies for Security Access Review user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access reviews aid in the detection and prevention of employee access rights misuse. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are essential. Security Access Review.
From www.dreamstime.com
Information Security,encryption and Secure Access Stock Illustration Security Access Review a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access. Security Access Review.
From mungfali.com
Security Role Matrix Security Access Review user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. user access reviews aid in the detection and prevention of employee access rights misuse. User access reviews help organizations limit who has access to critical data. user access reviews are essential to mitigate security threats like privilege creep,. Security Access Review.
From www.softwareadvice.com
Cisco Secure Access Software Reviews, Demo & Pricing 2024 Security Access Review access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews aid in the detection and prevention of employee access. Security Access Review.
From www.securitycameras-stlouis.com
Benefits of Access Control Security Access Review user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. a user access. Security Access Review.
From websiterepair-imc.com
Security Access Control Rx Security Access Review user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. User access reviews help organizations limit who has access to critical data. user access reviews aid in the detection and prevention of employee access rights misuse. user access reviews are essential to mitigate security threats like privilege creep,. Security Access Review.
From www.agilicus.com
Secure Remote Access through Clientless Zero Trust Architecture Agilicus Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. User access reviews help organizations limit who has access to critical data. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access. Security Access Review.
From www.youtube.com
User Access Reviews and Monitoring CompTIA Security+ SY0401 5.3 Security Access Review a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. access review is an important process for verifying and validating access rights in an organization’s it environment. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and. Security Access Review.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Security Access Review User access reviews help organizations limit who has access to critical data. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. access review is an important process for verifying and validating access rights in. Security Access Review.
From alta-ict.nl
Global Secure Access Microsoft's New Security Solution ALTAICT Security Access Review user access reviews aid in the detection and prevention of employee access rights misuse. user access review process entails periodically reviewing individual user access rights, whereas rbac, or role. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. access review is an important process for verifying. Security Access Review.
From www.alamy.com
Security Access Indicating Accessible Permission And Encryption Stock Security Access Review user access reviews aid in the detection and prevention of employee access rights misuse. user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and. Security Access Review.
From www.dreamstime.com
Security Access with Fingerprint Scan and Binary Code on Deep Blue Security Access Review user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. user access reviews aid in the detection and prevention of employee access rights misuse. a user access review, uar for. Security Access Review.
From www.cisco.com
Cisco Secure Access AtaGlance Cisco Security Access Review access review is an important process for verifying and validating access rights in an organization’s it environment. a user access review, uar for short, refers to the periodic review of the credentials and privileges of users who can access. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. . Security Access Review.
From www.splashtop.com
How to Simplify Secure Access for ThirdParties and Temp Users Security Access Review user access reviews are designed to identify and remediate unwanted access, such as permissions left active after an assignment has ended or a user switched to another department. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access reviews are essential for identifying and managing who has access. Security Access Review.
From www.rechenberg.com.au
EKA CyberKeys convenient & secure access control Rechenberg Security Access Review user access reviews aid in the detection and prevention of employee access rights misuse. user access reviews are essential to mitigate security threats like privilege creep, privilege misuse, and privilege abuse. user access reviews are essential for identifying and managing who has access to your organization’s critical systems and data. access review is an important process. Security Access Review.