Splunk Count By Time Bucket . Count occurrences of each field my_field in the query output: as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Use stats count by field_name. this example counts the values in the action field and organized the results into 30 minute time spans. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. See the bin command for syntax information and examples. The bucket command is an alias for the bin command. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Search criteria | extract fields if necessary | stats or timechart. Specify a bin size and return the count of raw events for. Return the average for a field for a specific time span;
from library.humio.com
this example counts the values in the action field and organized the results into 30 minute time spans. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Search criteria | extract fields if necessary | stats or timechart. Count occurrences of each field my_field in the query output: See the bin command for syntax information and examples. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Return the average for a field for a specific time span; The bucket command is an alias for the bin command. Use stats count by field_name. Specify a bin size and return the count of raw events for.
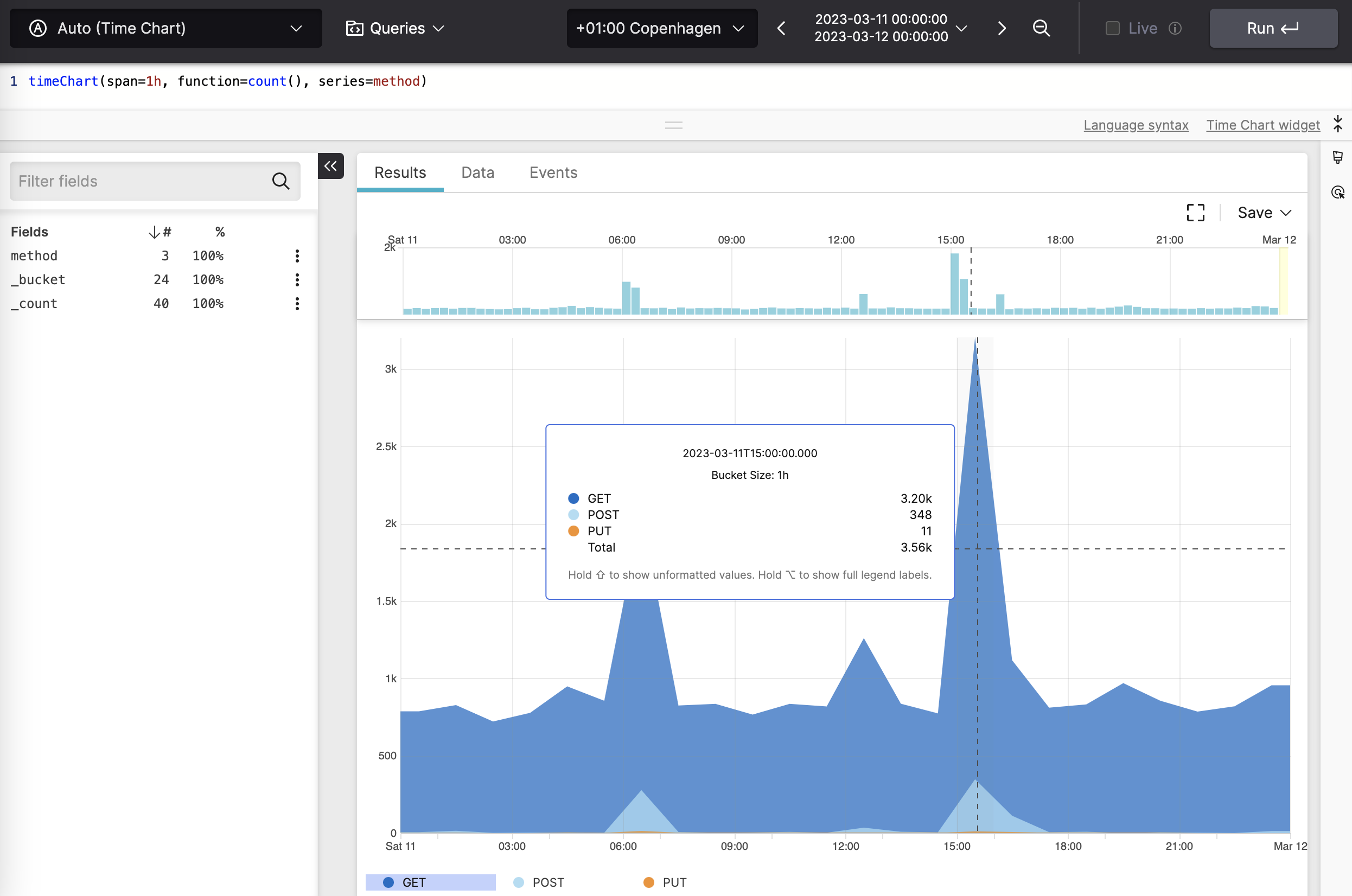
timeChart() Data Analysis 1.89.01.100.0 LogScale Documentation
Splunk Count By Time Bucket if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. See the bin command for syntax information and examples. Search criteria | extract fields if necessary | stats or timechart. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. this example counts the values in the action field and organized the results into 30 minute time spans. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Count occurrences of each field my_field in the query output: Specify a bin size and return the count of raw events for. Use stats count by field_name. The bucket command is an alias for the bin command. Return the average for a field for a specific time span;
From community.splunk.com
Solved How to show Splunk field based on count of another... Splunk Splunk Count By Time Bucket See the bin command for syntax information and examples. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. The bucket command is an alias for the bin command. Specify a bin size and return the count of raw events for. Return the average for a field for a specific time. Splunk Count By Time Bucket.
From www.youtube.com
07. Splunk Tutorial How to create Reports and Charts in Splunk YouTube Splunk Count By Time Bucket if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. this example counts the values in the action field and organized the results into 30 minute time spans. Count occurrences of each field my_field in the query output: as time is a. Splunk Count By Time Bucket.
From community.splunk.com
How to create timechart depends on count of two fi... Splunk Community Splunk Count By Time Bucket use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Search criteria | extract fields if necessary | stats or timechart. this example counts. Splunk Count By Time Bucket.
From community.splunk.com
Solved Diagrams of how indexing works in the Splunk platf... Splunk Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. The bucket command is an alias for the bin command. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. this example counts the values in the. Splunk Count By Time Bucket.
From www.webanalisten.nl
Splunk de toekomst van dataanalyse en webanalytics, deel 2 Splunk Count By Time Bucket Specify a bin size and return the count of raw events for. The bucket command is an alias for the bin command. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Count occurrences of each field my_field in the query output: See the. Splunk Count By Time Bucket.
From www.sergiofreire.com
Exporting test runs to Splunk Sergio Freire Splunk Count By Time Bucket use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. The bucket command is an alias for the bin command. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Use stats count by field_name.. Splunk Count By Time Bucket.
From www.vrogue.co
What Is Splunk A Beginners Guide To Understanding Splunk Edureka Vrogue Splunk Count By Time Bucket Use stats count by field_name. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Count occurrences of each field my_field in the query output:. Splunk Count By Time Bucket.
From bertjbrowno.blob.core.windows.net
Splunk Bucket Count By Day at bertjbrowno blog Splunk Count By Time Bucket See the bin command for syntax information and examples. Count occurrences of each field my_field in the query output: Return the average for a field for a specific time span; if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. use span instead. Splunk Count By Time Bucket.
From securitysynapse.blogspot.com
SecuritySynapse Splunk Dashboard Tricks Update Time Range for All Splunk Count By Time Bucket The bucket command is an alias for the bin command. Use stats count by field_name. as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. See the bin command for syntax information and examples. use span instead of bins option with bucket command, like this.| bucket. Splunk Count By Time Bucket.
From abbywright.z13.web.core.windows.net
Splunk Chart Over Time Splunk Count By Time Bucket Use stats count by field_name. Specify a bin size and return the count of raw events for. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Count occurrences of each field my_field in the query output: this example counts the values in. Splunk Count By Time Bucket.
From www.acte.in
Splunk Timechart Free Guide Tutorial & REALTIME Examples Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Search criteria | extract fields if necessary | stats or timechart. Count occurrences of each field my_field in the query output: this example counts the values in the action field and organized the results into 30. Splunk Count By Time Bucket.
From cloudian.com
Splunk Storage Calculator Estimate Your Storage Costs Cloudian Splunk Count By Time Bucket The bucket command is an alias for the bin command. See the bin command for syntax information and examples. Return the average for a field for a specific time span; this example counts the values in the action field and organized the results into 30 minute time spans. use span instead of bins option with bucket command, like. Splunk Count By Time Bucket.
From community.splunk.com
How to get the chart of count and percentage by i... Splunk Community Splunk Count By Time Bucket Count occurrences of each field my_field in the query output: The bucket command is an alias for the bin command. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Use stats count by field_name. this example counts the values in the action field and organized the results into 30. Splunk Count By Time Bucket.
From community.splunk.com
Extract count of each value of a field and create Splunk Community Splunk Count By Time Bucket See the bin command for syntax information and examples. Return the average for a field for a specific time span; Use stats count by field_name. this example counts the values in the action field and organized the results into 30 minute time spans. Count occurrences of each field my_field in the query output: use span instead of bins. Splunk Count By Time Bucket.
From dxowlbqpc.blob.core.windows.net
Splunk Bucket Response Time at Sylvia French blog Splunk Count By Time Bucket See the bin command for syntax information and examples. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Count occurrences of each field my_field in the query output: Use stats count by field_name. Specify a bin size and return the count of raw events for. as time is a. Splunk Count By Time Bucket.
From exorgwrzj.blob.core.windows.net
Splunk Search Archive Buckets at Karen Carter blog Splunk Count By Time Bucket Return the average for a field for a specific time span; Specify a bin size and return the count of raw events for. Count occurrences of each field my_field in the query output: if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Search. Splunk Count By Time Bucket.
From community.splunk.com
Solved How to show Splunk field based on count of another... Splunk Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. See the bin command for syntax information and examples. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Count occurrences. Splunk Count By Time Bucket.
From library.humio.com
timeChart() Data Analysis 1.89.01.100.0 LogScale Documentation Splunk Count By Time Bucket this example counts the values in the action field and organized the results into 30 minute time spans. as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Specify a bin size and return the count of raw events for. if i use bin _time. Splunk Count By Time Bucket.
From community.splunk.com
Solved How to show Splunk field based on count of another... Splunk Splunk Count By Time Bucket See the bin command for syntax information and examples. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Specify a bin size and return the count of raw events for. Use stats count by field_name. The bucket command is an alias for the bin command. Count occurrences of each field. Splunk Count By Time Bucket.
From queirozf.com
Splunk Examples Timecharts Splunk Count By Time Bucket Specify a bin size and return the count of raw events for. Use stats count by field_name. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Return the average for a field for a specific time span; if i use bin _time as time span=15m | stats count by. Splunk Count By Time Bucket.
From www.splunk.com
Search commands > stats, chart, and timechart Splunk Splunk Count By Time Bucket use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Return the average for a field for a specific time span; Search criteria | extract fields if necessary | stats or timechart. if i use bin _time as time span=15m | stats count by time on 17:20 for the past. Splunk Count By Time Bucket.
From www.youtube.com
Splunk Timechart SPL Tutorial YouTube Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Specify a bin size and return the count of raw events for. Search criteria | extract fields if necessary | stats or timechart. Return the average for a field for a specific time span; The bucket command. Splunk Count By Time Bucket.
From examples.javacodegeeks.com
Splunk Basic Charts Example Java Code Geeks Splunk Count By Time Bucket if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. use span instead of bins option with bucket command, like. Splunk Count By Time Bucket.
From community.splunk.com
Timechart with TIME, IPADDRESS and count Splunk Community Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. this example counts the values in the action field and organized the results into 30 minute time spans. The bucket command is an alias for the bin command. Count occurrences of each field my_field in the. Splunk Count By Time Bucket.
From docs.splunk.com
Use the Metrics dashboard Splunk Documentation Splunk Count By Time Bucket Specify a bin size and return the count of raw events for. Count occurrences of each field my_field in the query output: if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Return the average for a field for a specific time span; See. Splunk Count By Time Bucket.
From community.splunk.com
Chart count with timespan Splunk Community Splunk Count By Time Bucket Specify a bin size and return the count of raw events for. if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. See the bin command for syntax information and examples. The bucket command is an alias for the bin command. as time. Splunk Count By Time Bucket.
From www.primesoft.net
Retrospective Dashboard Queries in Splunk PrimeSoft Solutions Inc. Splunk Count By Time Bucket as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. Specify a bin size and return the count of raw events for. The bucket command is an alias for the bin command. this example counts the values in the action field and organized the results into. Splunk Count By Time Bucket.
From exofhdaxz.blob.core.windows.net
Splunk Total Number Of Buckets at Norma Andrews blog Splunk Count By Time Bucket this example counts the values in the action field and organized the results into 30 minute time spans. use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. as time is a field just like everything else, you can bucket first, and then use _time in your stats command. Splunk Count By Time Bucket.
From community.splunk.com
How to create timechart for a stat count result fo... Splunk Community Splunk Count By Time Bucket Count occurrences of each field my_field in the query output: The bucket command is an alias for the bin command. as time is a field just like everything else, you can bucket first, and then use _time in your stats command like. this example counts the values in the action field and organized the results into 30 minute. Splunk Count By Time Bucket.
From exofhdaxz.blob.core.windows.net
Splunk Total Number Of Buckets at Norma Andrews blog Splunk Count By Time Bucket if i use bin _time as time span=15m | stats count by time on 17:20 for the past 1 hour, the result would be like. Return the average for a field for a specific time span; The bucket command is an alias for the bin command. as time is a field just like everything else, you can bucket. Splunk Count By Time Bucket.
From geek-university.com
stats command Splunk Splunk Count By Time Bucket See the bin command for syntax information and examples. Specify a bin size and return the count of raw events for. Search criteria | extract fields if necessary | stats or timechart. Use stats count by field_name. this example counts the values in the action field and organized the results into 30 minute time spans. as time is. Splunk Count By Time Bucket.
From docs.splunk.com
chart Splunk Documentation Splunk Count By Time Bucket Search criteria | extract fields if necessary | stats or timechart. See the bin command for syntax information and examples. The bucket command is an alias for the bin command. Return the average for a field for a specific time span; if i use bin _time as time span=15m | stats count by time on 17:20 for the past. Splunk Count By Time Bucket.
From dxowlbqpc.blob.core.windows.net
Splunk Bucket Response Time at Sylvia French blog Splunk Count By Time Bucket use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Return the average for a field for a specific time span; The bucket command is an alias for the bin command. Search criteria | extract fields if necessary | stats or timechart. this example counts the values in the action. Splunk Count By Time Bucket.
From examples.javacodegeeks.com
Splunk Stats Command Example Java Code Geeks Splunk Count By Time Bucket use span instead of bins option with bucket command, like this.| bucket span=100 time_taken | stats count as. Specify a bin size and return the count of raw events for. Count occurrences of each field my_field in the query output: The bucket command is an alias for the bin command. as time is a field just like everything. Splunk Count By Time Bucket.
From threatvector.cylance.com
Introducing Splunk® RealTime Threat Monitoring and Analysis Made Easy Splunk Count By Time Bucket Return the average for a field for a specific time span; Specify a bin size and return the count of raw events for. The bucket command is an alias for the bin command. Search criteria | extract fields if necessary | stats or timechart. this example counts the values in the action field and organized the results into 30. Splunk Count By Time Bucket.