Port 9001 Tor-Orport Exploit . Bridgerelay 1 # replace todo1 with a tor port of your choice. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Here is my /etc/tor/torcc file: Here's a version probe for the tor protocol. Some trojans connect over tor to the cnc server. # this port must be externally reachable. I was performing a nmap scan on my own ip and found this closed but strange looking port: # avoid port 9001 because it's. Most of them just execute. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: If you didn't run tor yourself, it's probably a trojan.
from akvilekiskis.com
# this port must be externally reachable. # avoid port 9001 because it's. Here is my /etc/tor/torcc file: Most of them just execute. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Some trojans connect over tor to the cnc server. Bridgerelay 1 # replace todo1 with a tor port of your choice. Here's a version probe for the tor protocol. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. I was performing a nmap scan on my own ip and found this closed but strange looking port:
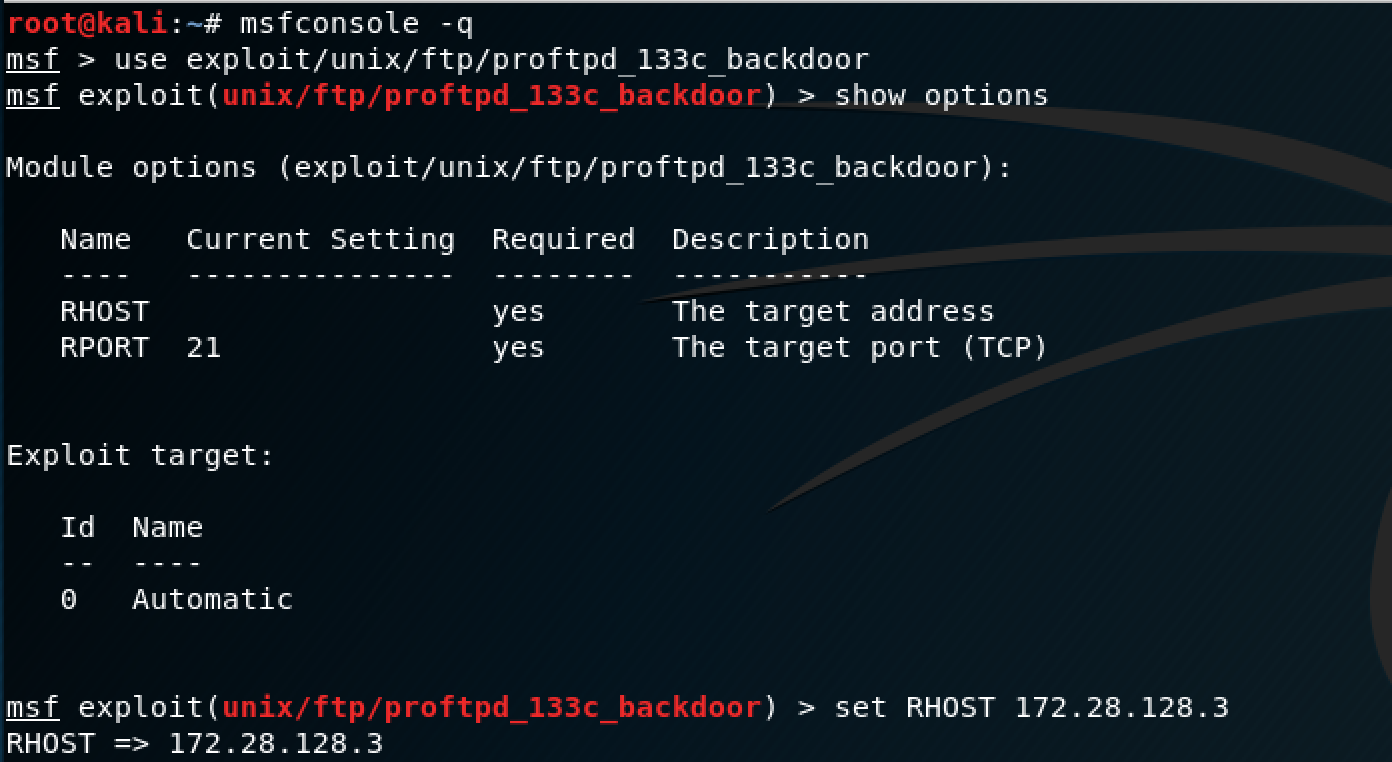
Basic Pentesting 1 Walkthrough
Port 9001 Tor-Orport Exploit I was performing a nmap scan on my own ip and found this closed but strange looking port: Bridgerelay 1 # replace todo1 with a tor port of your choice. # avoid port 9001 because it's. Here is my /etc/tor/torcc file: Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Most of them just execute. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. If you didn't run tor yourself, it's probably a trojan. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: Here's a version probe for the tor protocol. # this port must be externally reachable. Some trojans connect over tor to the cnc server. I was performing a nmap scan on my own ip and found this closed but strange looking port:
From www.youtube.com
How to Exploit SSH Port 22 Kali Linux Metasploitable2 V2 YouTube Port 9001 Tor-Orport Exploit Bridgerelay 1 # replace todo1 with a tor port of your choice. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. I was performing a nmap scan on my own ip and found this closed but strange looking port: If you didn't run tor yourself, it's probably a trojan. Most of. Port 9001 Tor-Orport Exploit.
From developer.aliyun.com
某内网域的writeup阿里云开发者社区 Port 9001 Tor-Orport Exploit Bridgerelay 1 # replace todo1 with a tor port of your choice. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: # avoid port 9001 because it's. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. I was performing a nmap scan on my. Port 9001 Tor-Orport Exploit.
From tor.stackexchange.com
configuration Access ORPort via tailscale Tor Stack Exchange Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. # avoid port 9001 because it's. Bridgerelay 1 # replace todo1 with a tor port of your choice. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Some trojans connect over tor to the cnc server. For. Port 9001 Tor-Orport Exploit.
From blog.csdn.net
centos7.x搭建Tor私人网桥_obfs4免费网桥地址CSDN博客 Port 9001 Tor-Orport Exploit I was performing a nmap scan on my own ip and found this closed but strange looking port: Here's a version probe for the tor protocol. # avoid port 9001 because it's. Most of them just execute. # this port must be externally reachable. Here is my /etc/tor/torcc file: For a few examples of possibilities, assuming tor is compromised by. Port 9001 Tor-Orport Exploit.
From www.d4-project.org
Analyzing TCP port scan D4 Project Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. # this port must be externally reachable. Some trojans connect over tor to the cnc server. Here's a version probe for the tor protocol. If you didn't run tor yourself, it's probably a trojan. Here is my /etc/tor/torcc file: # avoid port. Port 9001 Tor-Orport Exploit.
From blog.csdn.net
server failed to start. Port 9001 was already in use.端口号被占用CSDN博客 Port 9001 Tor-Orport Exploit Some trojans connect over tor to the cnc server. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. # this port must be externally reachable. Most of them just execute. # avoid port 9001 because it's. Bridgerelay 1 # replace todo1 with a tor port of your choice. Here's a version. Port 9001 Tor-Orport Exploit.
From www.youtube.com
What is tor PART 1 How to forward port over tor YouTube Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Most of them just execute. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here's a version probe for the tor protocol. For a few examples of possibilities, assuming tor is compromised by an exploit over the. Port 9001 Tor-Orport Exploit.
From defenserootin.blogspot.com
Defenseroot Consulting Which are the latest Exploit kits used by hackers Port 9001 Tor-Orport Exploit Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here is my /etc/tor/torcc file: Here's a version probe for the tor protocol. If you didn't run tor yourself, it's probably a trojan. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: I was performing. Port 9001 Tor-Orport Exploit.
From www.redeszone.net
Nuevos detalles sobre el exploit que atormenta a los usuarios de Tor Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Bridgerelay 1 # replace todo1 with a tor port of your choice. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. # this port must be externally reachable. Here's a version probe for the tor protocol. Here. Port 9001 Tor-Orport Exploit.
From beardycast.com
Завязываем узлы Tor — Бородокаст Port 9001 Tor-Orport Exploit If you didn't run tor yourself, it's probably a trojan. Here's a version probe for the tor protocol. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here is my /etc/tor/torcc file: I was performing a nmap scan on my own ip and found this closed but strange looking port: # this port must be. Port 9001 Tor-Orport Exploit.
From github.com
GitHub Launchvox/OscLiveLink OSC Live Link for Unreal and Hallway Port 9001 Tor-Orport Exploit Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here's a version probe for the tor protocol. # avoid port 9001 because it's. # this port must be externally reachable. Bridgerelay 1 # replace todo1 with a tor port of your choice. If you didn't run tor yourself, it's probably a trojan. I was performing. Port 9001 Tor-Orport Exploit.
From forum.torproject.org
Our server has not managed to confirm reachability for its ORPort(s Port 9001 Tor-Orport Exploit For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: # this port must be externally reachable. I was performing a nmap scan on my own ip and found this closed but strange looking port: Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or. Port 9001 Tor-Orport Exploit.
From www.radware.com
Reaper Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Bridgerelay 1 # replace todo1 with a tor port of your choice. # this port must be externally reachable. Most of them just execute. Here is my /etc/tor/torcc file: # avoid port 9001 because it's. I was performing a nmap scan on. Port 9001 Tor-Orport Exploit.
From slideplayer.com
Denial of Service (DoS) Attacks and Defenses ppt download Port 9001 Tor-Orport Exploit I was performing a nmap scan on my own ip and found this closed but strange looking port: Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here is my /etc/tor/torcc file: # this port must be externally reachable. For a few examples of possibilities, assuming tor is compromised by an exploit over the network,. Port 9001 Tor-Orport Exploit.
From www.fortinet.com
How Tor Browser Works and Where to Find Builtin Tor Bridges Port 9001 Tor-Orport Exploit Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Most of them just execute. I was performing a nmap scan on my own ip and found this closed but strange looking port: Some trojans connect over tor to the cnc server. For a few examples of possibilities, assuming tor is compromised by an exploit over. Port 9001 Tor-Orport Exploit.
From github.com
Feature Ability to change tor ports · Issue 14594 · brave/browser Port 9001 Tor-Orport Exploit Most of them just execute. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: If you didn't run tor yourself, it's probably a trojan. Here is my /etc/tor/torcc file: Some trojans connect over tor to the cnc server. Bridgerelay 1 # replace todo1 with a tor port of your. Port 9001 Tor-Orport Exploit.
From lala.im
Debian10搭建Tor中继节点,以及多个实例共存荒岛 Port 9001 Tor-Orport Exploit Some trojans connect over tor to the cnc server. Here's a version probe for the tor protocol. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Here is my /etc/tor/torcc file: Most of them just execute. For. Port 9001 Tor-Orport Exploit.
From answers.microsoft.com
Port 9001 is not available Microsoft Community Port 9001 Tor-Orport Exploit Here is my /etc/tor/torcc file: Most of them just execute. # avoid port 9001 because it's. Some trojans connect over tor to the cnc server. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: I was performing a nmap scan on my own ip and found this closed but. Port 9001 Tor-Orport Exploit.
From answers.microsoft.com
Port 9001 is not available Microsoft Community Port 9001 Tor-Orport Exploit Some trojans connect over tor to the cnc server. # this port must be externally reachable. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Bridgerelay 1 # replace todo1 with a tor port of your choice. Here's a version probe for the tor protocol. # avoid port 9001 because it's.. Port 9001 Tor-Orport Exploit.
From www.youtube.com
How to Exploit port 53 Domain ISC BIND 9.4.2 2022.23 YouTube Port 9001 Tor-Orport Exploit Most of them just execute. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here's a version probe for the tor protocol. Bridgerelay 1 # replace todo1 with a tor port of your choice. Here is my /etc/tor/torcc file: If you didn't run tor yourself, it's probably a trojan. For a few examples of possibilities,. Port 9001 Tor-Orport Exploit.
From www.fortinet.com
How Tor Browser Works and Where to Find Builtin Tor Bridges Port 9001 Tor-Orport Exploit Here's a version probe for the tor protocol. I was performing a nmap scan on my own ip and found this closed but strange looking port: # this port must be externally reachable. Most of them just execute. Some trojans connect over tor to the cnc server. Here is my /etc/tor/torcc file: Tor is tunneled inside of tls, so the. Port 9001 Tor-Orport Exploit.
From www.youtube.com
How to exploit Port 22 ssh how to exploit ssh ssh YouTube Port 9001 Tor-Orport Exploit If you didn't run tor yourself, it's probably a trojan. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Here is my /etc/tor/torcc file: I was performing a nmap scan on my own ip and found this closed but strange looking port: Some trojans connect over tor to the cnc server.. Port 9001 Tor-Orport Exploit.
From www.youtube.com
Port 9001 used by MicrosoftHTTPAPI/2.0 YouTube Port 9001 Tor-Orport Exploit Bridgerelay 1 # replace todo1 with a tor port of your choice. Most of them just execute. # avoid port 9001 because it's. Some trojans connect over tor to the cnc server. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Here is my /etc/tor/torcc file: For a few examples of. Port 9001 Tor-Orport Exploit.
From slidetodoc.com
Port Scanning Introduction Port scanning techniques that attackers Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. # avoid port 9001 because it's. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here's a version probe for the tor protocol. Bridgerelay 1 # replace todo1 with a tor port of your choice. Most of. Port 9001 Tor-Orport Exploit.
From mhgas.weebly.com
Tor bridge settings mhgas Port 9001 Tor-Orport Exploit # avoid port 9001 because it's. If you didn't run tor yourself, it's probably a trojan. Here's a version probe for the tor protocol. Most of them just execute. Some trojans connect over tor to the cnc server. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: Here is. Port 9001 Tor-Orport Exploit.
From www.cyberdefensemagazine.com
Feds request Judge to review the order to reveal TOR Exploit Code Port 9001 Tor-Orport Exploit If you didn't run tor yourself, it's probably a trojan. # this port must be externally reachable. # avoid port 9001 because it's. Bridgerelay 1 # replace todo1 with a tor port of your choice. Here is my /etc/tor/torcc file: Tor is tunneled inside of tls, so the probe relies on service detection's automatic. For a few examples of possibilities,. Port 9001 Tor-Orport Exploit.
From learn.microsoft.com
Azure Stack HCI twonode storage switchless, two switches deployment Port 9001 Tor-Orport Exploit Some trojans connect over tor to the cnc server. If you didn't run tor yourself, it's probably a trojan. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Here's a version probe for the tor protocol. Here is my /etc/tor/torcc file: # avoid port 9001 because it's. For a few examples. Port 9001 Tor-Orport Exploit.
From slideplayer.com
Targeted Breakin, DoS, & Malware attacks (I) ppt download Port 9001 Tor-Orport Exploit Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. # this port must be externally reachable. Bridgerelay 1 # replace todo1 with a tor port of your choice. Some trojans connect over tor to the cnc server. If you didn't run tor yourself, it's probably a trojan. Here's a version probe. Port 9001 Tor-Orport Exploit.
From stackoverflow.com
php How to debug a test and/or running code in a Docker container Port 9001 Tor-Orport Exploit # avoid port 9001 because it's. Here is my /etc/tor/torcc file: Most of them just execute. Bridgerelay 1 # replace todo1 with a tor port of your choice. Some trojans connect over tor to the cnc server. If you didn't run tor yourself, it's probably a trojan. # this port must be externally reachable. For a few examples of possibilities,. Port 9001 Tor-Orport Exploit.
From blog.jxtsai.info
如何搭建洋蔥網路的中繼 Tor Relay (1) personal blog buit by hugo, hosted on Port 9001 Tor-Orport Exploit Tor is tunneled inside of tls, so the probe relies on service detection's automatic. Here is my /etc/tor/torcc file: Here's a version probe for the tor protocol. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. I was performing a nmap scan on my own ip and found this closed but. Port 9001 Tor-Orport Exploit.
From www.youtube.com
How to Exploit SMTP Port 25 Kali Linux Metasploitable2 V4 YouTube Port 9001 Tor-Orport Exploit If you didn't run tor yourself, it's probably a trojan. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: Bridgerelay 1 # replace todo1 with a tor port of your choice. Most of them just execute. Tor is tunneled inside of tls, so the probe relies on service detection's. Port 9001 Tor-Orport Exploit.
From akvilekiskis.com
Basic Pentesting 1 Walkthrough Port 9001 Tor-Orport Exploit Bridgerelay 1 # replace todo1 with a tor port of your choice. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: Some trojans connect over tor to the cnc server. Here is my /etc/tor/torcc file: Tor is tunneled inside of tls, so the probe relies on service detection's automatic.. Port 9001 Tor-Orport Exploit.
From codeembedded.wordpress.com
TCP/UDP ports forwarding over SSH Baremetal, RTOS and Linux Port 9001 Tor-Orport Exploit Here is my /etc/tor/torcc file: # avoid port 9001 because it's. Most of them just execute. Some trojans connect over tor to the cnc server. Here's a version probe for the tor protocol. Tor is tunneled inside of tls, so the probe relies on service detection's automatic. I was performing a nmap scan on my own ip and found this. Port 9001 Tor-Orport Exploit.
From slideplayer.com
Tunneling into Tor client proxy and “hidden services” ppt download Port 9001 Tor-Orport Exploit Bridgerelay 1 # replace todo1 with a tor port of your choice. If you didn't run tor yourself, it's probably a trojan. Here's a version probe for the tor protocol. Examine activity between any ephemeral port and tor ip—this could be malicious data exfiltration or c2 traffic (except. Some trojans connect over tor to the cnc server. Here is my. Port 9001 Tor-Orport Exploit.
From www.researchgate.net
Connection ports of the Tor network Download Scientific Diagram Port 9001 Tor-Orport Exploit # this port must be externally reachable. # avoid port 9001 because it's. For a few examples of possibilities, assuming tor is compromised by an exploit over the network, the tor process can: Most of them just execute. Some trojans connect over tor to the cnc server. Examine activity between any ephemeral port and tor ip—this could be malicious data. Port 9001 Tor-Orport Exploit.