What Is Security Key In Bluetooth . The security key device works offline to protect you online through. A security key/token is a physical usb drive that acts as a 2fa or mfa method. Link key, pairing, authentication & authorization. This page on bluetooth security covers basics of security concepts in bluetooth network. The temporary key is used during the bluetooth pairing process. Bluetooth pairing, encryption & authentication. The short term key is used as the key for encrypting a. When two bluetooth devices pair with each other, they first generate an initialization key. Using your phone as a bluetooth security key is a simple and effective way to make your google. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Transform your phone into a security key. Bluetooth uses symmetric key cryptography for authentication and encryption. In this article, we’ll zero in on how bluetooth le technology uses security keys.
from www.intego.com
Bluetooth uses symmetric key cryptography for authentication and encryption. Transform your phone into a security key. When two bluetooth devices pair with each other, they first generate an initialization key. The temporary key is used during the bluetooth pairing process. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Using your phone as a bluetooth security key is a simple and effective way to make your google. The short term key is used as the key for encrypting a. In this article, we’ll zero in on how bluetooth le technology uses security keys. A security key/token is a physical usb drive that acts as a 2fa or mfa method. Bluetooth pairing, encryption & authentication.
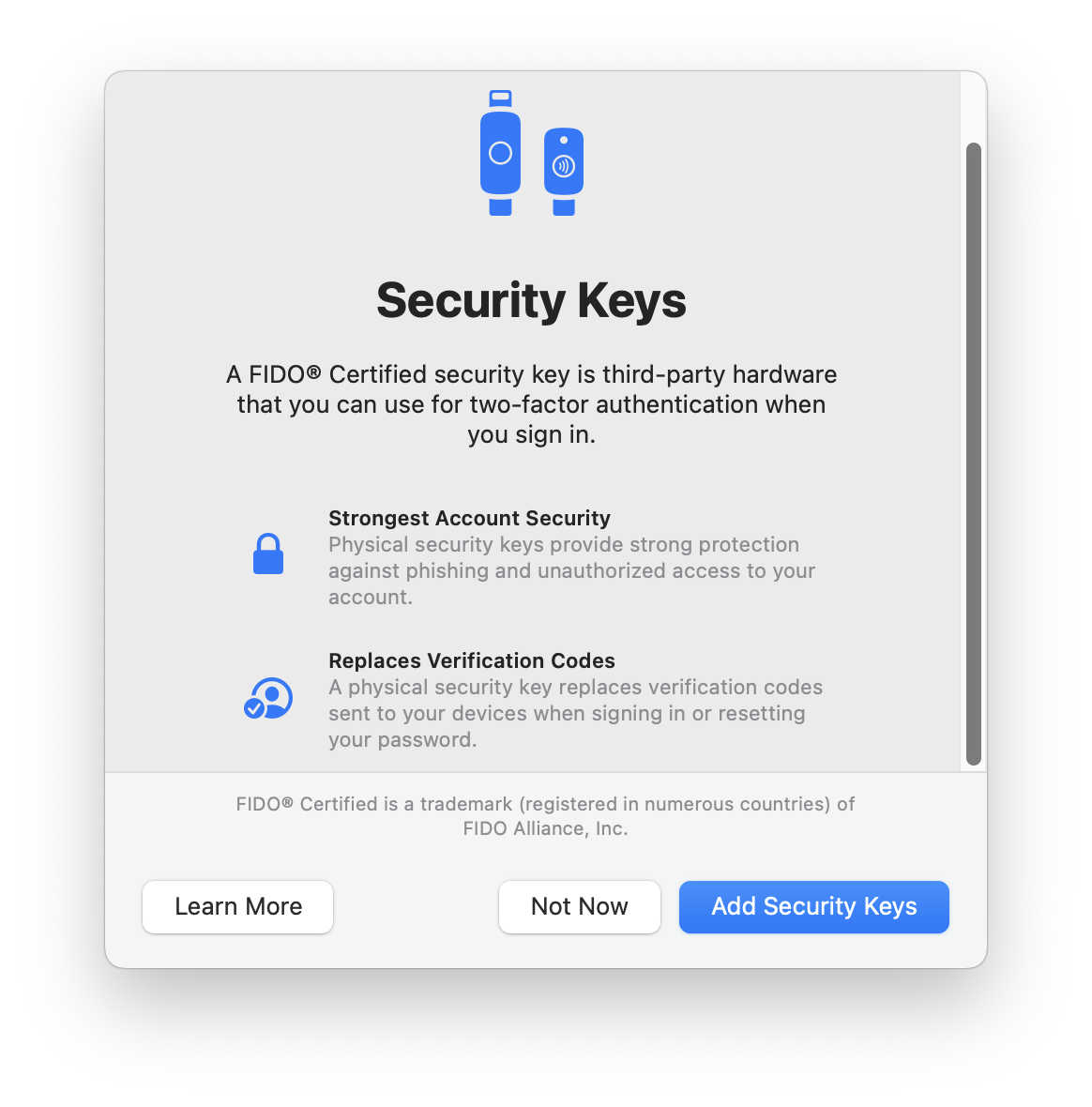
How to protect your Apple ID account with Security Keys on iPhone, iPad
What Is Security Key In Bluetooth Transform your phone into a security key. The security key device works offline to protect you online through. Bluetooth uses symmetric key cryptography for authentication and encryption. The short term key is used as the key for encrypting a. This page on bluetooth security covers basics of security concepts in bluetooth network. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. A security key/token is a physical usb drive that acts as a 2fa or mfa method. Transform your phone into a security key. The temporary key is used during the bluetooth pairing process. Link key, pairing, authentication & authorization. In this article, we’ll zero in on how bluetooth le technology uses security keys. Using your phone as a bluetooth security key is a simple and effective way to make your google. When two bluetooth devices pair with each other, they first generate an initialization key. Bluetooth pairing, encryption & authentication.
From www.allaboutsafes.co.uk
Master Lock Smart Bluetooth Key Safe 5441D, Key Storage Unit, Securikey UK What Is Security Key In Bluetooth This page on bluetooth security covers basics of security concepts in bluetooth network. The security key device works offline to protect you online through. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The short term key is used as the key for encrypting a. Bluetooth pairing, encryption & authentication. In this article, we’ll. What Is Security Key In Bluetooth.
From www.ubuy.mk
iMagic Bluetooth Key Lock Box Smart Wall Mounted Security Door What Is Security Key In Bluetooth Bluetooth pairing, encryption & authentication. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. A security key/token is a physical usb drive that acts as a 2fa or mfa method. The security key device works offline to protect you online through. Link key, pairing, authentication & authorization. When two bluetooth devices pair with each. What Is Security Key In Bluetooth.
From www.intego.com
How to use a Security Key to protect sensitive online accounts The What Is Security Key In Bluetooth With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Using your phone as a bluetooth security key is a simple and effective way to make your google. This page on bluetooth security covers basics of security concepts in bluetooth network. The security key device works offline to protect you online through. A security key/token. What Is Security Key In Bluetooth.
From www.desertcart.ph
Buy FEITIAN MultiPass K16 and USB ePass K9 Security Key FIDO 2in1 What Is Security Key In Bluetooth The temporary key is used during the bluetooth pairing process. Link key, pairing, authentication & authorization. In this article, we’ll zero in on how bluetooth le technology uses security keys. Bluetooth uses symmetric key cryptography for authentication and encryption. When two bluetooth devices pair with each other, they first generate an initialization key. The short term key is used as. What Is Security Key In Bluetooth.
From robots.net
What Is The Security Key For Wifi What Is Security Key In Bluetooth This page on bluetooth security covers basics of security concepts in bluetooth network. The temporary key is used during the bluetooth pairing process. The short term key is used as the key for encrypting a. A security key/token is a physical usb drive that acts as a 2fa or mfa method. Bluetooth uses symmetric key cryptography for authentication and encryption.. What Is Security Key In Bluetooth.
From www.internetsafetystatistics.com
What Is a Network Security Key? What Is Security Key In Bluetooth The short term key is used as the key for encrypting a. Link key, pairing, authentication & authorization. Transform your phone into a security key. Bluetooth pairing, encryption & authentication. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Bluetooth uses symmetric key cryptography for authentication and encryption. A security key/token is a physical. What Is Security Key In Bluetooth.
From posetke.ru
What is my wifi network security key » Posetke What Is Security Key In Bluetooth With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The temporary key is used during the bluetooth pairing process. The security key device works offline to protect you online through. The short term key is used as the key for encrypting a. Bluetooth uses symmetric key cryptography for authentication and encryption. When two bluetooth. What Is Security Key In Bluetooth.
From gizmodo.com
Google Wants You to Use Physical Security Keys So Bad It's Willing to What Is Security Key In Bluetooth Transform your phone into a security key. Bluetooth uses symmetric key cryptography for authentication and encryption. The temporary key is used during the bluetooth pairing process. In this article, we’ll zero in on how bluetooth le technology uses security keys. The security key device works offline to protect you online through. Using your phone as a bluetooth security key is. What Is Security Key In Bluetooth.
From ar.inspiredpencil.com
Security Key What Is Security Key In Bluetooth Using your phone as a bluetooth security key is a simple and effective way to make your google. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Link key, pairing, authentication & authorization. The security key device works offline to protect you online through. The temporary key is used during the bluetooth pairing process.. What Is Security Key In Bluetooth.
From ar.inspiredpencil.com
Security Key What Is Security Key In Bluetooth In this article, we’ll zero in on how bluetooth le technology uses security keys. When two bluetooth devices pair with each other, they first generate an initialization key. The security key device works offline to protect you online through. Transform your phone into a security key. The temporary key is used during the bluetooth pairing process. Link key, pairing, authentication. What Is Security Key In Bluetooth.
From shopee.sg
Philips Digital Lock Easy Key 515K Smart Lock Digital key Bluetooth What Is Security Key In Bluetooth A security key/token is a physical usb drive that acts as a 2fa or mfa method. Link key, pairing, authentication & authorization. Bluetooth pairing, encryption & authentication. The security key device works offline to protect you online through. Bluetooth uses symmetric key cryptography for authentication and encryption. Using your phone as a bluetooth security key is a simple and effective. What Is Security Key In Bluetooth.
From www.techradar.com
Best security key in 2022 TechRadar What Is Security Key In Bluetooth The short term key is used as the key for encrypting a. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. A security key/token is a physical usb drive that acts as a 2fa or mfa method. Link key, pairing, authentication & authorization. This page on bluetooth security covers basics of security concepts in. What Is Security Key In Bluetooth.
From updatetechworld.blogspot.com
Security Key!!! What Is Security Key? (Yubico YubiKey 5 NFC USBA What Is Security Key In Bluetooth With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. When two bluetooth devices pair with each other, they first generate an initialization key. The temporary key is used during the bluetooth pairing process. The security key device works offline to protect you online through. Bluetooth pairing, encryption & authentication. Bluetooth uses symmetric key cryptography. What Is Security Key In Bluetooth.
From paulstamatiou.com
Getting started with security keys — What Is Security Key In Bluetooth With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Bluetooth uses symmetric key cryptography for authentication and encryption. A security key/token is a physical usb drive that acts as a 2fa or mfa method. The short term key is used as the key for encrypting a. Bluetooth pairing, encryption & authentication. Link key, pairing,. What Is Security Key In Bluetooth.
From www.ftsafe.com
FIDO Security Keys FEITIAN What Is Security Key In Bluetooth When two bluetooth devices pair with each other, they first generate an initialization key. The temporary key is used during the bluetooth pairing process. Using your phone as a bluetooth security key is a simple and effective way to make your google. The short term key is used as the key for encrypting a. A security key/token is a physical. What Is Security Key In Bluetooth.
From techsphinx.com
Best Security Key for Multifactor Authentication (2023) TechSphinx What Is Security Key In Bluetooth Link key, pairing, authentication & authorization. The short term key is used as the key for encrypting a. Transform your phone into a security key. When two bluetooth devices pair with each other, they first generate an initialization key. The temporary key is used during the bluetooth pairing process. A security key/token is a physical usb drive that acts as. What Is Security Key In Bluetooth.
From www.vecteezy.com
3d sign in with a security key illustration 10872178 PNG What Is Security Key In Bluetooth This page on bluetooth security covers basics of security concepts in bluetooth network. Bluetooth uses symmetric key cryptography for authentication and encryption. In this article, we’ll zero in on how bluetooth le technology uses security keys. The temporary key is used during the bluetooth pairing process. The security key device works offline to protect you online through. Link key, pairing,. What Is Security Key In Bluetooth.
From www.indiamart.com
Bluetooth Key Finder, For Finding Key at Rs 135 in Bengaluru ID What Is Security Key In Bluetooth The security key device works offline to protect you online through. The temporary key is used during the bluetooth pairing process. The short term key is used as the key for encrypting a. This page on bluetooth security covers basics of security concepts in bluetooth network. When two bluetooth devices pair with each other, they first generate an initialization key.. What Is Security Key In Bluetooth.
From updatetechworld.blogspot.com
Security Key!!! What Is Security Key? (Yubico YubiKey 5 NFC USBA What Is Security Key In Bluetooth Using your phone as a bluetooth security key is a simple and effective way to make your google. This page on bluetooth security covers basics of security concepts in bluetooth network. The security key device works offline to protect you online through. Bluetooth uses symmetric key cryptography for authentication and encryption. With an emphasis on three types of keys—the long. What Is Security Key In Bluetooth.
From www.makeuseof.com
Should You Buy a USB, Bluetooth, or NFC Security Key? Here's the Best What Is Security Key In Bluetooth The security key device works offline to protect you online through. Transform your phone into a security key. A security key/token is a physical usb drive that acts as a 2fa or mfa method. This page on bluetooth security covers basics of security concepts in bluetooth network. Using your phone as a bluetooth security key is a simple and effective. What Is Security Key In Bluetooth.
From www.intego.com
How to protect your Apple ID account with Security Keys on iPhone, iPad What Is Security Key In Bluetooth The security key device works offline to protect you online through. Transform your phone into a security key. Using your phone as a bluetooth security key is a simple and effective way to make your google. Bluetooth pairing, encryption & authentication. When two bluetooth devices pair with each other, they first generate an initialization key. In this article, we’ll zero. What Is Security Key In Bluetooth.
From us.norton.com
Bluetooth security risks to know + how to avoid them Norton What Is Security Key In Bluetooth This page on bluetooth security covers basics of security concepts in bluetooth network. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Using your phone as a bluetooth security key is a simple and effective way to make your google. The security key device works offline to protect you online through. Bluetooth pairing, encryption. What Is Security Key In Bluetooth.
From www.researchgate.net
Bluetooth Secure Simple Pairing with numeric comparison [12 What Is Security Key In Bluetooth Bluetooth uses symmetric key cryptography for authentication and encryption. Bluetooth pairing, encryption & authentication. Transform your phone into a security key. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The security key device works offline to protect you online through. In this article, we’ll zero in on how bluetooth le technology uses security. What Is Security Key In Bluetooth.
From www.programmingcube.com
What is a Network Security Key Programming Cube What Is Security Key In Bluetooth The short term key is used as the key for encrypting a. In this article, we’ll zero in on how bluetooth le technology uses security keys. Transform your phone into a security key. A security key/token is a physical usb drive that acts as a 2fa or mfa method. With an emphasis on three types of keys—the long term key. What Is Security Key In Bluetooth.
From www.microsoft.com
Windows Hello and FIDO2 Security Keys enable secure and easy What Is Security Key In Bluetooth This page on bluetooth security covers basics of security concepts in bluetooth network. Transform your phone into a security key. The temporary key is used during the bluetooth pairing process. Link key, pairing, authentication & authorization. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The short term key is used as the key. What Is Security Key In Bluetooth.
From www.makeuseof.com
Should You Buy a USB, Bluetooth, or NFC Security Key? Here's the Best What Is Security Key In Bluetooth A security key/token is a physical usb drive that acts as a 2fa or mfa method. Transform your phone into a security key. In this article, we’ll zero in on how bluetooth le technology uses security keys. The security key device works offline to protect you online through. Bluetooth uses symmetric key cryptography for authentication and encryption. When two bluetooth. What Is Security Key In Bluetooth.
From www.pcworld.com
Google offers free 2FA Bluetooth Titan Security Key swaps after What Is Security Key In Bluetooth When two bluetooth devices pair with each other, they first generate an initialization key. The short term key is used as the key for encrypting a. Transform your phone into a security key. The security key device works offline to protect you online through. A security key/token is a physical usb drive that acts as a 2fa or mfa method.. What Is Security Key In Bluetooth.
From www.intego.com
How to protect your Apple ID account with Security Keys on iPhone, iPad What Is Security Key In Bluetooth Bluetooth pairing, encryption & authentication. Using your phone as a bluetooth security key is a simple and effective way to make your google. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The temporary key is used during the bluetooth pairing process. The security key device works offline to protect you online through. When. What Is Security Key In Bluetooth.
From www.youtube.com
iPhone Security Keys iOS 16.3 Changes/Features YouTube What Is Security Key In Bluetooth The temporary key is used during the bluetooth pairing process. The short term key is used as the key for encrypting a. Bluetooth uses symmetric key cryptography for authentication and encryption. Transform your phone into a security key. Using your phone as a bluetooth security key is a simple and effective way to make your google. Bluetooth pairing, encryption &. What Is Security Key In Bluetooth.
From www.walmart.com
Electric Keyless Smart Lock with Bluetooth Key Pad Keyless Entry Door What Is Security Key In Bluetooth With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. The temporary key is used during the bluetooth pairing process. This page on bluetooth security covers basics of security concepts in bluetooth network. Using your phone as a bluetooth security key is a simple and effective way to make your google. Bluetooth pairing, encryption &. What Is Security Key In Bluetooth.
From thesecuritykey.com
What Is a Security Key or a Token? What Is Security Key In Bluetooth A security key/token is a physical usb drive that acts as a 2fa or mfa method. The temporary key is used during the bluetooth pairing process. Bluetooth pairing, encryption & authentication. This page on bluetooth security covers basics of security concepts in bluetooth network. Link key, pairing, authentication & authorization. The short term key is used as the key for. What Is Security Key In Bluetooth.
From www.intego.com
How to protect your Apple ID account with Security Keys on iPhone, iPad What Is Security Key In Bluetooth Using your phone as a bluetooth security key is a simple and effective way to make your google. Bluetooth pairing, encryption & authentication. Link key, pairing, authentication & authorization. This page on bluetooth security covers basics of security concepts in bluetooth network. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. Transform your phone. What Is Security Key In Bluetooth.
From www.bunnings.com.au
Master Lock Portable Bluetooth Key Safe Bunnings Australia What Is Security Key In Bluetooth Using your phone as a bluetooth security key is a simple and effective way to make your google. When two bluetooth devices pair with each other, they first generate an initialization key. Transform your phone into a security key. A security key/token is a physical usb drive that acts as a 2fa or mfa method. The temporary key is used. What Is Security Key In Bluetooth.
From www.thewindowsclub.com
How to remove Security Key in Windows 11 What Is Security Key In Bluetooth Bluetooth uses symmetric key cryptography for authentication and encryption. Transform your phone into a security key. The security key device works offline to protect you online through. With an emphasis on three types of keys—the long term key (ltk), connection signature resolving. When two bluetooth devices pair with each other, they first generate an initialization key. The temporary key is. What Is Security Key In Bluetooth.
From www.youtube.com
Google Titan Security Key Set Review YouTube What Is Security Key In Bluetooth Using your phone as a bluetooth security key is a simple and effective way to make your google. The short term key is used as the key for encrypting a. This page on bluetooth security covers basics of security concepts in bluetooth network. In this article, we’ll zero in on how bluetooth le technology uses security keys. The temporary key. What Is Security Key In Bluetooth.