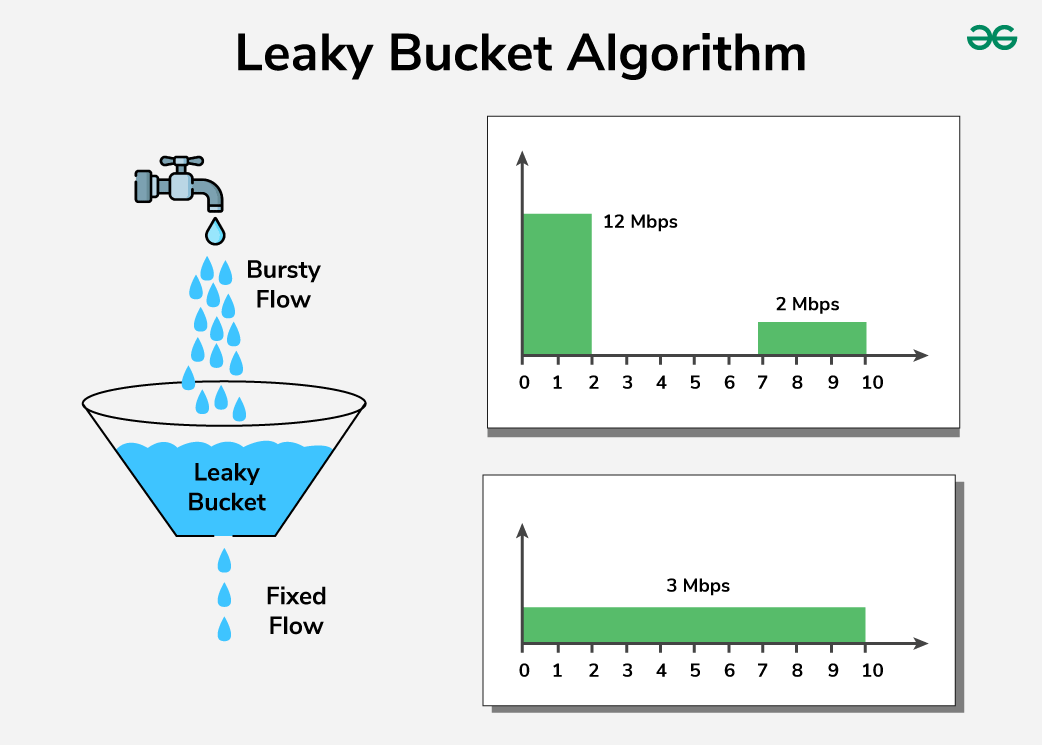
Leaky Bucket Algorithm With Example . the leaky bucket algorithm is essentially a congestion control mechanism. However, it has a downside as well. Step 1 − let us. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic.
from www.geeksforgeeks.org
leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. leaky bucket is a more robust algorithm compared to a token bucket. However, it has a downside as well. the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. It controls the shape of the traffic entering the.
Rate Limiting Algorithms System Design
Leaky Bucket Algorithm With Example leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. However, it has a downside as well. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us. the leaky bucket algorithm provides an elegant solution to. Leaky Bucket Algorithm With Example.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm With Example leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. However, it has a downside as well. It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is essentially. Leaky Bucket Algorithm With Example.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky Bucket Algorithm With Example the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. leaky bucket is a more robust algorithm compared to a token bucket. leaky bucket algorithm mainly controls. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm With Example leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. However, it has a downside as well. the leaky bucket algorithm is essentially a congestion control mechanism. leaky bucket is a more robust algorithm compared to a token bucket. It controls the shape of the traffic entering the. . Leaky Bucket Algorithm With Example.
From www.youtube.com
12. Leaky Bucket Algorithm Program VTU 5th Sem Computer Network Lab Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. leaky bucket is a more robust algorithm compared to a token. Leaky Bucket Algorithm With Example.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. However, it has a downside as well. Step 1 − let us. leaky bucket is a more robust algorithm compared to a token bucket. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm provides an. Leaky Bucket Algorithm With Example.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is essentially a congestion control mechanism. It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. leaky bucket is a more robust. Leaky Bucket Algorithm With Example.
From github.com
GitHub ShreyaRao09/LeakyBucketAlgorithmImplementation A Computer Leaky Bucket Algorithm With Example leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It controls the shape of the traffic entering the. However, it has a downside as well. the. Leaky Bucket Algorithm With Example.
From www.youtube.com
CN LabLeaky Bucket Algorithm YouTube Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm is essentially a congestion control mechanism. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. leaky bucket algorithm mainly controls the total amount and the rate. Leaky Bucket Algorithm With Example.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. However, it has a downside as well. Step 1 −. Leaky Bucket Algorithm With Example.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm With Example the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It controls the shape of the traffic entering the. Step 1 − let us. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is essentially a congestion control mechanism. leaky. Leaky Bucket Algorithm With Example.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm With Example leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm is a simple. Leaky Bucket Algorithm With Example.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm With Example the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is essentially a congestion control mechanism. It controls the shape of the traffic entering the. Step 1 − let us. However, it has a downside as well. leaky bucket is a. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Outline PowerPoint Presentation, free download ID6256891 Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm provides an elegant solution to. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Bandwidth Management PowerPoint Presentation, free download ID Leaky Bucket Algorithm With Example leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate. Leaky Bucket Algorithm With Example.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm With Example Step 1 − let us. leaky bucket is a more robust algorithm compared to a token bucket. However, it has a downside as well. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is essentially a congestion control mechanism. . Leaky Bucket Algorithm With Example.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm With Example leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. However, it has a downside as well. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It controls the shape of the traffic entering the. the leaky bucket algorithm is a simple yet effective. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is essentially a congestion control mechanism. However, it has a downside as well. the leaky bucket. Leaky Bucket Algorithm With Example.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. leaky bucket is a more robust algorithm compared to a token bucket. However, it has a downside as well. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Lecture 10 PowerPoint Presentation, free download ID4737649 Leaky Bucket Algorithm With Example the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. However, it has a downside as well. It controls the shape of the traffic entering the. leaky bucket is a more robust algorithm compared to a token bucket. leaky bucket algorithm mainly controls the total amount and the rate of. Leaky Bucket Algorithm With Example.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It controls the shape of the traffic entering the. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. However, it has a downside as well. . Leaky Bucket Algorithm With Example.
From lowleveldesign.io
Design a Distributed Scalable API Rate Limiter Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. the leaky bucket algorithm is essentially a congestion control mechanism. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to. Leaky Bucket Algorithm With Example.
From www.geeksforgeeks.org
Leaky Bucket Algorithm Computer Networks Leaky Bucket Algorithm With Example leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us. the leaky bucket algorithm is essentially a congestion control mechanism. However, it has a downside as well. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It controls the shape of the. Leaky Bucket Algorithm With Example.
From www.youtube.com
Program 11 C/C++ Program for Congestion control using Leaky Bucket Leaky Bucket Algorithm With Example However, it has a downside as well. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is essentially a congestion control mechanism. leaky bucket algorithm mainly controls the total amount and the. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Quality of Service Support PowerPoint Presentation, free download Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. However, it has a downside as well. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm. Leaky Bucket Algorithm With Example.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Communication Networks PowerPoint Presentation, free download Leaky Bucket Algorithm With Example the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. the leaky bucket algorithm is essentially a congestion control mechanism. Step 1 − let us. However, it has a downside as well. leaky bucket is a more robust algorithm compared to a token bucket. It controls the shape of the. Leaky Bucket Algorithm With Example.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the leaky bucket algorithm is essentially a congestion control mechanism. . Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Algorithm With Example the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It controls the shape of the traffic entering the. However, it has a downside as well. leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. the. Leaky Bucket Algorithm With Example.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm With Example It controls the shape of the traffic entering the. leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. However, it has a downside as well. leaky bucket algorithm mainly controls the total. Leaky Bucket Algorithm With Example.
From slideplayer.com
Chapter 18 Frame Relay. ppt download Leaky Bucket Algorithm With Example the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. However, it has a downside as well. It controls the shape of the traffic. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5320728 Leaky Bucket Algorithm With Example the leaky bucket algorithm is essentially a congestion control mechanism. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. However, it has a downside as well. It controls the shape of the traffic entering the. leaky bucket is a more robust algorithm compared to a token bucket. Step 1 − let us.. Leaky Bucket Algorithm With Example.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm With Example the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us. the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. However, it has a downside as well. It controls the shape of the traffic entering the. . Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. However, it has a downside as well. leaky bucket is a more robust algorithm compared to a token bucket. the leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It controls the shape of the traffic. Leaky Bucket Algorithm With Example.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Algorithm With Example the leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. the leaky bucket algorithm is essentially a congestion control mechanism. Step 1 − let us. the leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. leaky bucket algorithm mainly controls. Leaky Bucket Algorithm With Example.