Routersploit Cmd Commands . Enter the following commands to install, routersploit. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Routersploit has a number of exploits for different router models and they have the ability to. For installation from the official repository kali linux (version may be outdated): After exploiting a router, you can start an interactive shell session: Instead, we will install from source from github. It consists of various modules that aid penetration testing operations:.
from www.simplilearn.com.cach3.com
Enter the following commands to install, routersploit. For installation from the official repository kali linux (version may be outdated): To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Instead, we will install from source from github. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. Routersploit has a number of exploits for different router models and they have the ability to. After exploiting a router, you can start an interactive shell session: It consists of various modules that aid penetration testing operations:. The routersploit package in the kali linux repostory is outdated and broken.
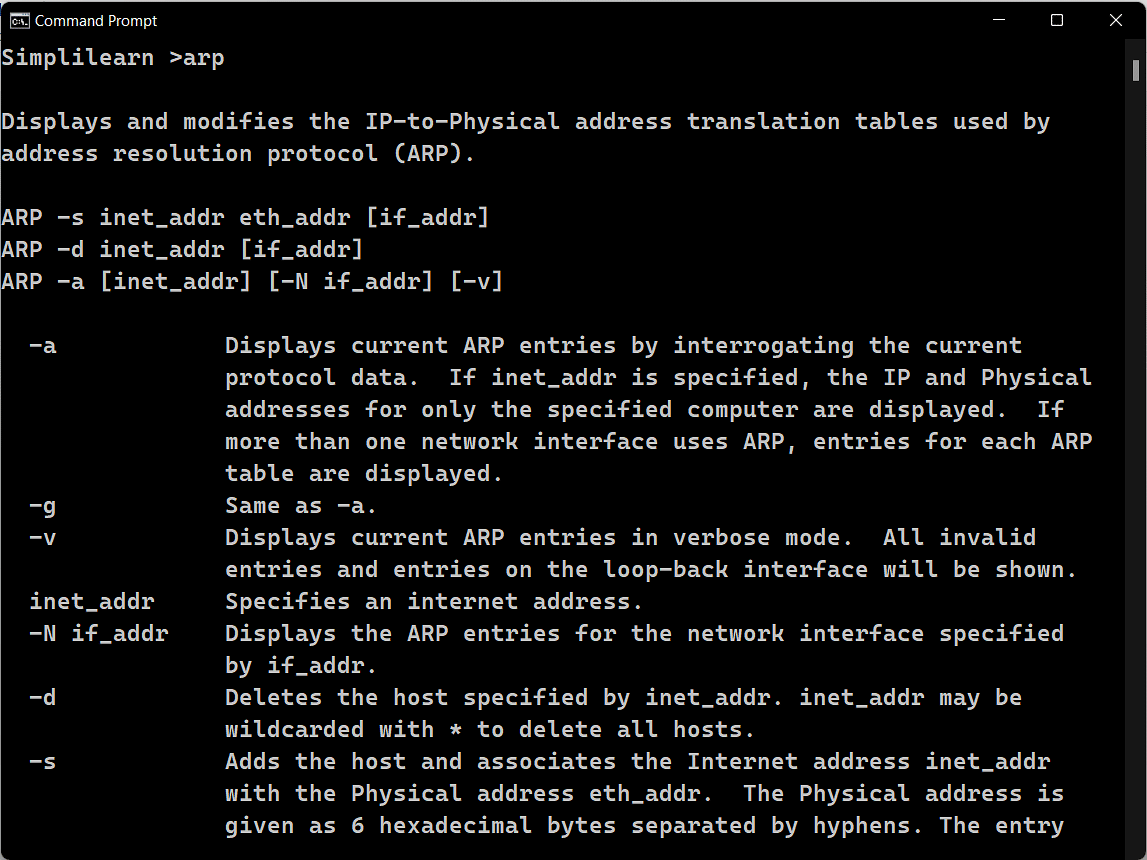
Understanding the Networking Commands A Walkthrough to Top 8 Commands
Routersploit Cmd Commands It consists of various modules that aid penetration testing operations:. Instead, we will install from source from github. Routersploit has a number of exploits for different router models and they have the ability to. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. After exploiting a router, you can start an interactive shell session: It consists of various modules that aid penetration testing operations:. Enter the following commands to install, routersploit. For installation from the official repository kali linux (version may be outdated): Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. The routersploit package in the kali linux repostory is outdated and broken. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below:
From www.auslogics.com
Windows Command Prompt Most Useful Commands — Auslogics Blog Routersploit Cmd Commands Instead, we will install from source from github. The routersploit package in the kali linux repostory is outdated and broken. Routersploit has a number of exploits for different router models and they have the ability to. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. It consists of various modules that. Routersploit Cmd Commands.
From fossbytes.com
A to Z List Of Windows CMD Commands Command Line Reference Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: For installation from the official repository kali linux (version may be outdated): Routersploit has a number of exploits for different router models and they have the ability to. After exploiting a router, you can start an interactive shell session: It. Routersploit Cmd Commands.
From github.com
GitHub SidraELEzz/Install_Termux Install all basic Termux commands Routersploit Cmd Commands Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. For installation from the official repository kali linux (version may be outdated): The routersploit package in the kali linux repostory is outdated and broken. Enter the following commands to install, routersploit. Instead, we will install from source from github. To install routersploit on kali linux, open. Routersploit Cmd Commands.
From beginnerbasicssp.blogspot.com
10 COMMAND PROMPT(CMD) COMMANDS Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. Instead, we will install from source from github. It consists of various modules that aid penetration testing operations:. For installation from the official repository kali linux (version may. Routersploit Cmd Commands.
From www.freecodecamp.org
Command Line Commands CLI Tutorial Routersploit Cmd Commands Instead, we will install from source from github. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. It consists of various modules that aid penetration testing operations:. After exploiting a router, you can start an interactive shell session: How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select. Routersploit Cmd Commands.
From www.lifewire.com
Command Prompt Commands A Complete List (CMD Commands) Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Routersploit has a number of exploits for different router models and they have the ability to. It consists of various modules that aid penetration testing operations:.. Routersploit Cmd Commands.
From itgito.blogspot.com
Perintah dalam cmd SEPUTAR IT Routersploit Cmd Commands Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. After exploiting a router, you can start an interactive shell session: Routersploit has a number of exploits for different router models and they have the ability to. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. For. Routersploit Cmd Commands.
From github.com
GitHub threat9/routersploit Exploitation Framework for Embedded Devices Routersploit Cmd Commands Instead, we will install from source from github. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: After exploiting a router, you can start an interactive shell session: Routersploit has a number of exploits for different router models and they have the ability to. The routersploit package in the. Routersploit Cmd Commands.
From hitechgazette.com
Checkout These New CMD Commands To Use Hi Tech Gazette Routersploit Cmd Commands For installation from the official repository kali linux (version may be outdated): Routersploit has a number of exploits for different router models and they have the ability to. The routersploit package in the kali linux repostory is outdated and broken. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Instead, we will install from source. Routersploit Cmd Commands.
From developingdaily.com
Basic CMD Commands Which Windows User Must Know Developing Daily Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. For installation from the official repository kali linux (version may be outdated): Instead, we will install from source from github. Routersploit provides an interactive shell for advanced users. Routersploit Cmd Commands.
From www.simplilearn.com.cach3.com
Understanding the Networking Commands A Walkthrough to Top 8 Commands Routersploit Cmd Commands For installation from the official repository kali linux (version may be outdated): It consists of various modules that aid penetration testing operations:. The routersploit package in the kali linux repostory is outdated and broken. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. After exploiting a router, you can start an. Routersploit Cmd Commands.
From www.prodefence.org
routersploit v3.2.0 released Router Exploitation Framework Routersploit Cmd Commands Instead, we will install from source from github. The routersploit package in the kali linux repostory is outdated and broken. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Enter the following commands to install, routersploit. To install routersploit on kali linux, open a terminal and type the following commands in the same order as. Routersploit Cmd Commands.
From www.luvburger.com
kis könyv dinasztia Hozzászoktat dos diskpart commands másodlagos Routersploit Cmd Commands How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. The routersploit package in the kali linux repostory is outdated and broken. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. For installation from the official repository kali linux (version may be outdated): After exploiting a router,. Routersploit Cmd Commands.
From www.wikihow.com
How to Find All Commands of CMD in Your Computer 8 Steps Routersploit Cmd Commands After exploiting a router, you can start an interactive shell session: How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. It consists of various modules that aid penetration testing operations:. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Routersploit has a number of exploits for. Routersploit Cmd Commands.
From www.artofit.org
8 cmd commands to manage wireless networks on windows Artofit Routersploit Cmd Commands Instead, we will install from source from github. After exploiting a router, you can start an interactive shell session: How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. Routersploit has a number of exploits for different router models and they have the ability to. It consists of various modules that aid. Routersploit Cmd Commands.
From www.simplilearn.com.cach3.com
Understanding the Networking Commands A Walkthrough to Top 8 Commands Routersploit Cmd Commands It consists of various modules that aid penetration testing operations:. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. Instead, we will install from source from github. For installation from the official repository kali linux (version may. Routersploit Cmd Commands.
From www.codingninjas.com
Basic Commands for Networking Coding Ninjas Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: After exploiting a router, you can start an interactive shell session: Enter the following commands to install, routersploit. For installation from the official repository kali linux (version may be outdated): How to use routersploit exploit routersploit commands after you find. Routersploit Cmd Commands.
From www.vrogue.co
Complete List Of Command Prompt Commands Hromtronics vrogue.co Routersploit Cmd Commands Routersploit has a number of exploits for different router models and they have the ability to. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. After exploiting a router, you can start an interactive shell session: Instead, we will install from source from github. It consists of various modules that aid. Routersploit Cmd Commands.
From www.wikihow.com
How to Find All Commands of CMD in Your Computer 8 Steps Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. Enter the following commands to install, routersploit. It consists of various modules that aid penetration testing operations:. How to use routersploit exploit routersploit commands after you find the. Routersploit Cmd Commands.
From www.91mobiles.com
CMD commands Top list of basic and network command prompt (CMD Routersploit Cmd Commands Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Enter the following commands to install, routersploit. For installation from the official repository kali linux (version may be outdated): After exploiting a router, you can start an interactive shell session: The routersploit package in the kali linux repostory is outdated and broken. Instead, we will install. Routersploit Cmd Commands.
From www.scribd.com
CMD Commands PDF Routersploit Cmd Commands Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Instead, we will install from source from github. After exploiting a router, you can start an interactive shell session: For installation from the official repository kali. Routersploit Cmd Commands.
From www.91mobiles.com
Top list of CMD commands for Windows users (2024) Routersploit Cmd Commands For installation from the official repository kali linux (version may be outdated): How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. It consists of various modules that aid penetration testing operations:. Routersploit has a number of exploits for different router models and they have the ability to. After exploiting a router,. Routersploit Cmd Commands.
From www.vrogue.co
5 Most Useful Windows Cmd Commands Hindi Youtube www.vrogue.co Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit has a number of exploits for different router models and they have the ability to. After exploiting a router, you can start an interactive shell session: Instead, we will install from source from github. Enter the following commands to. Routersploit Cmd Commands.
From www.simplilearn.com.cach3.com
Understanding the Networking Commands A Walkthrough to Top 8 Commands Routersploit Cmd Commands After exploiting a router, you can start an interactive shell session: Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. Enter the following commands to install, routersploit. Instead, we will install from source from github. Routersploit has. Routersploit Cmd Commands.
From www.auslogics.com
Windows Command Prompt Most Useful Commands — Auslogics Blog Tips to Routersploit Cmd Commands Instead, we will install from source from github. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit has a number of exploits for different router models and they have the. Routersploit Cmd Commands.
From www.91mobiles.com
Top list of CMD commands for Windows users (2024) Routersploit Cmd Commands For installation from the official repository kali linux (version may be outdated): Routersploit has a number of exploits for different router models and they have the ability to. It consists of various modules that aid penetration testing operations:. Instead, we will install from source from github. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices.. Routersploit Cmd Commands.
From www.moyens.net
8 commandes CMD pour gérer les réseaux sans fil sous Windows Moyens I/O Routersploit Cmd Commands Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. Instead, we will install from source from github. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. For installation from the official repository. Routersploit Cmd Commands.
From evbn.org
Command Prompt (CMD) 10 networkrelated commands you should know EU Routersploit Cmd Commands It consists of various modules that aid penetration testing operations:. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. After exploiting a router,. Routersploit Cmd Commands.
From www.artofit.org
8 cmd commands to manage wireless networks on windows Artofit Routersploit Cmd Commands Instead, we will install from source from github. After exploiting a router, you can start an interactive shell session: It consists of various modules that aid penetration testing operations:. Enter the following commands to install, routersploit. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. For installation from the official repository kali linux (version may. Routersploit Cmd Commands.
From www.wikigain.com
Most Useful CMD Commands Aka Terminal Commands wikigain Routersploit Cmd Commands The routersploit package in the kali linux repostory is outdated and broken. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. It consists of various modules that aid penetration testing operations:. Routersploit has a number. Routersploit Cmd Commands.
From kali.tools
RouterSploit Инструменты Kali Linux Routersploit Cmd Commands Instead, we will install from source from github. Enter the following commands to install, routersploit. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: Routersploit provides an interactive shell for advanced. Routersploit Cmd Commands.
From www.mysmartprice.com
cmd Commands 100+ Best Best Command Prompt Commands List You Should Routersploit Cmd Commands After exploiting a router, you can start an interactive shell session: Enter the following commands to install, routersploit. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. The routersploit package in the kali linux repostory is outdated and broken. Routersploit has a number of exploits for different router models and they have the ability to.. Routersploit Cmd Commands.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit Cmd Commands The routersploit package in the kali linux repostory is outdated and broken. It consists of various modules that aid penetration testing operations:. For installation from the official repository kali linux (version may be outdated): Instead, we will install from source from github. How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the.. Routersploit Cmd Commands.
From howtogethelpwithwin11.github.io
How To Get Wifi Password Using Cmd Windows 11 Lates Windows 10 Update Routersploit Cmd Commands To install routersploit on kali linux, open a terminal and type the following commands in the same order as below: The routersploit package in the kali linux repostory is outdated and broken. Routersploit provides an interactive shell for advanced users to execute commands on compromised devices. For installation from the official repository kali linux (version may be outdated): Instead, we. Routersploit Cmd Commands.
From www.freecodecamp.org
Command Line Commands CLI Tutorial Routersploit Cmd Commands How to use routersploit exploit routersploit commands after you find the vulnerability that affects the router, select the. The routersploit package in the kali linux repostory is outdated and broken. After exploiting a router, you can start an interactive shell session: Routersploit has a number of exploits for different router models and they have the ability to. Routersploit provides an. Routersploit Cmd Commands.