Hardware Keystore . The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. From what i've read here,.
from www.hissenit.com
From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways.
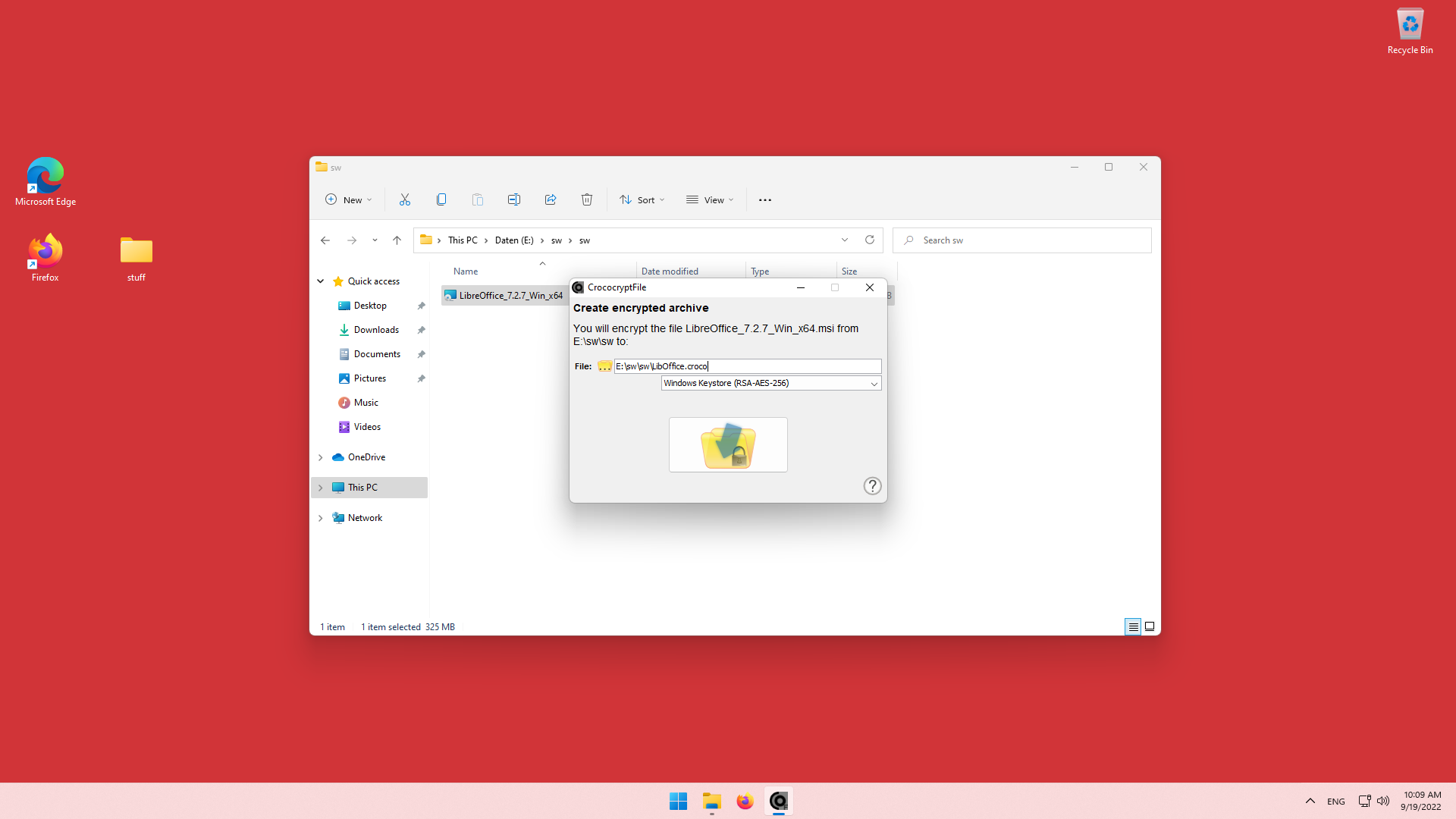
Windows 11 Certificatebased File Encryption (CrococryptFile with
Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. The android keystore system protects key material from unauthorized use in two ways.
From github.com
AndroidSecurityReference/hardware/keystore.md at master · doridori Hardware Keystore From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From www.keydemon.com
KeyGrabber Air USB WiFi hardware keylogger. Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From onlinedbalearning.blogspot.com
Oracle Transparent Data Encryption (TDE) Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From www.dreamstime.com
Hardware Store Vendor Holding Key and Locking Mechanism Stock Photo Hardware Keystore Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Hardware Keystore.
From cubist.dev
CubeSigner Snap Hardwarebacked key management for MetaMask developers Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. Hardware Keystore.
From www.youtube.com
Use Hardware Security Module (HSM) to Store Private Keys Securely in Hardware Keystore First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Hardware Keystore.
From de.dreamstime.com
Hardware keylogger stock abbildung. Illustration von skripterstellung Hardware Keystore From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From www.pizzolab.com
How to generate a Keystore. What is it? Easy Guide Pizzo Hardware Keystore Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. First, it reduces the risk of. Hardware Keystore.
From brandiscrafts.com
Android Hardware Backed Keystore Example? The 20 Top Answers Hardware Keystore First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Hardware Keystore.
From www.pocket-lint.com
Best hardware security keys for twofactor authentication Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From www.dtoaec.com
Architect's Master Guide to Door Hardware Key Components for The Door Hardware Keystore First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From androiddevblog.blogspot.com
Android Programming for Fun Secure your data in Android by Simple Hardware Keystore From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Hardware Keystore.
From security.googleblog.com
Google Online Security Blog New Keystore features keep your slice of Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From www.ibm.com
Define a keystore for hardware encryption using the iKeyman utility Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. First, it reduces the risk of. Hardware Keystore.
From multimarketinc.com
What are {hardware} safety keys and the way do they work? MultiMarketInc Hardware Keystore First, it reduces the risk of. From what i've read here,. The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From keystore-explorer.org
KeyStore Explorer Screenshots Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From www.hissenit.com
Windows 11 Certificatebased File Encryption (CrococryptFile with Hardware Keystore From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From speakerdeck.com
Introducing Oracle key Vault Speaker Deck Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From www.makeuseof.com
The 5 Best Hardware Security Keys for Online Protection Hardware Keystore From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From headjack.io
How to create an Android Keystore file for Headjack Headjack Hardware Keystore Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From www.researchgate.net
Abbildung 4.4 AndroidKeyStore Hardwarebacked Keystore Download Hardware Keystore First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From www.researchgate.net
Abbildung 4.4 AndroidKeyStore Hardwarebacked Keystore Download Hardware Keystore First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From www.theverge.com
The best hardware security keys for twofactor authentication The Verge Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From www.youtube.com
How to Use Hardware Security Keys Like YubiKey for 2FA YouTube Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From medium.com
Securing Secret Key In Android Using Keystore by Varun Dwarkani Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. First, it reduces the risk of. Hardware Keystore.
From docs.aws.amazon.com
External key stores AWS Key Management Service Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.
From aubinhardware.com
ace hardware Aubin Hardware Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. First, it reduces the risk of. Hardware Keystore.
From www.yumpu.com
HARDWARE KEYS To install Hardware Keystore Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Hardware Keystore.
From www.dreamstime.com
Hardware Key Color Square Buttons Stock Vector Illustration of secure Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. From what i've read here,. Hardware Keystore.
From proandroiddev.com
Android KeyStore what is the difference between “StrongBox” and Hardware Keystore The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. Hardware Keystore.
From www.acehardwaremission.com
Hardware Services Santa Rosa, CA Mission Ace Hardware & Lumber Hardware Keystore From what i've read here,. The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. Hardware Keystore.
From tilakpuli.medium.com
Unlocking Android Security Harnessing Android Hardware KeyStore and Hardware Keystore Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. First, it reduces the risk of. From what i've read here,. The android keystore system protects key material from unauthorized use in two ways. Hardware Keystore.
From proandroiddev.com
Android KeyStore what is the difference between “StrongBox” and Hardware Keystore First, it reduces the risk of. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Hardware Keystore.
From dokumen.tips
(PPT) Computer Hardware Key board Mouse Input Devices Monitor Hardware Keystore First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. From what i've read here,. Hardware Keystore.
From alternativeto.net
KeyStore Explorer Alternatives and Similar Software Hardware Keystore First, it reduces the risk of. The android keystore system protects key material from unauthorized use in two ways. From what i've read here,. Keystore requires keys to be bound to a root of trust, which is a bitstring provided to the keymaster secure hardware during startup,. Hardware Keystore.