How To Secure A Dmz . At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. Learn how to use dmz for secure. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added layer of security between your precious data and potential hackers.
from www.getdroidtips.com
A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added layer of security between your precious data and potential hackers. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network.
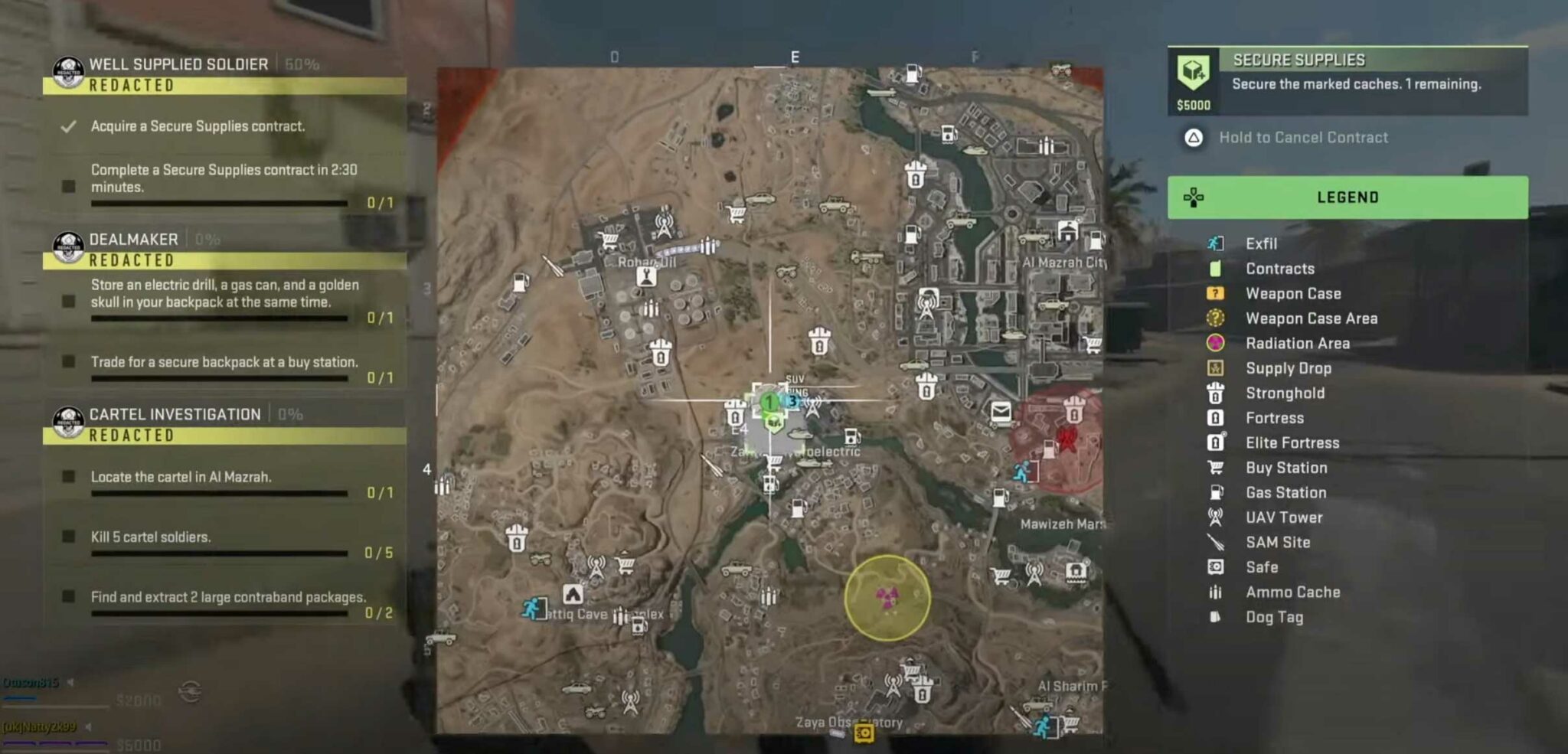
How to Acquire Secure Supplies Contract in DMZ Well Supplied Soldier Mission
How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. Learn how to use dmz for secure. A dmz can bring an added layer of security between your precious data and potential hackers. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections.
From www.acrosec.jp
Dedicated DMZ Security Architectures ACROSEC IT Security How To Secure A Dmz At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A dmz can bring an added layer of security between your precious data and potential hackers. Learn. How To Secure A Dmz.
From www.youtube.com
(NEW) DMZ HOW TO DUPE A SECURE BACKPACK GLITCH! (DUPE HEATED MADNESS ATTACHMENTS / KEYS) MW2 How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams begin the setup process for a dmz,. How To Secure A Dmz.
From modernizemodest1712.blogspot.com
37 dmz network diagram example Diagram For You How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. Learn how to use dmz for secure. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone (dmz) is cut off from the enterprise. How To Secure A Dmz.
From www.goanywhere.com
Download "DMZ Secure Gateways" Guide GoAnywhere How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from. How To Secure A Dmz.
From www.youtube.com
Module 5 Demilitarized Zone (DMZ) YouTube How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A dmz can bring an added layer of security between your precious data and potential hackers. A. How To Secure A Dmz.
From www.youtube.com
How To Complete Secure RADIOACTIVE MATERIAL Contract & Loot RADIOACTIVE CACHES! (MW2 DMZ Guide How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A dmz can bring an added layer of security between your precious data and potential hackers. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz.. How To Secure A Dmz.
From www.youtube.com
DMZ How To Complete Dealmaker, Trade For A Secure Backpack YouTube How To Secure A Dmz Learn how to use dmz for secure. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams. How To Secure A Dmz.
From soultec.ch
[HowTo] Secure your DMZ with a proxy souITec How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic. How To Secure A Dmz.
From www.youtube.com
How to get the "Secure Backpack" & "Skeleton Key" in DMZ YouTube How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate. How To Secure A Dmz.
From www.howtogame.net
CH 7 Secure Records Room Key Location DMZ How To Game How To Secure A Dmz At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from. How To Secure A Dmz.
From dotesports.com
DMZ Secure Backpack How it works and how to get one How To Secure A Dmz Learn how to use dmz for secure. A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. When your. How To Secure A Dmz.
From circuitdbplastered.z13.web.core.windows.net
Secure Network Diagram With Dmz How To Secure A Dmz Learn how to use dmz for secure. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the very least, using a dmz and utilizing simple tips to secure your routers can make it. How To Secure A Dmz.
From www.newsoftwares.net
How To Securely Transfer Data From The DMZ? Blog How To Secure A Dmz Learn how to use dmz for secure. A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing. How To Secure A Dmz.
From www.youtube.com
*NEW* DMZ HOW TO SECURE AND UPLOAD YOUR TROPHIES!! DMZ/WARZONE/MULTIPLAYER.. YouTube How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle. How To Secure A Dmz.
From www.getdroidtips.com
How to Acquire Secure Supplies Contract in DMZ Well Supplied Soldier Mission How To Secure A Dmz When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection. How To Secure A Dmz.
From cybr.com
Project DMZ and Network Hardening Tutorial with Packet Tracer Cybr How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone (dmz) is cut off. How To Secure A Dmz.
From routerctrl.com
What is DMZ and Should I Use It? (Everything You Need to Know About DMZ in Networking) RouterCtrl How To Secure A Dmz At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. Learn how to use dmz for secure. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. A demilitarized zone (dmz) is cut off. How To Secure A Dmz.
From campingbeech.com
How To Get Secure Backpack Dmz How To Secure A Dmz At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. Learn how to use dmz for secure. A dmz can bring an added layer of security between. How To Secure A Dmz.
From practonet.com
Let’s understand DMZ Demilitarized Zone Cyber Security, Networking, Technology Courses and Blog How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams. How To Secure A Dmz.
From edtechmagazine.com
How to Secure a Network DMZ EdTech Magazine How To Secure A Dmz At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. When your networking, it, or security teams begin the setup process for a dmz,. How To Secure A Dmz.
From docs.secureauth.com
Configure a DMZ SecureAuth Connection How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from. How To Secure A Dmz.
From www.shieldoo.io
What Is a DMZ Network and How Does It Work? How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle. How To Secure A Dmz.
From twinfinite.net
How to Get Secure & Scavenger Backpacks in DMZ Twinfinite How To Secure A Dmz When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. Learn how to use dmz. How To Secure A Dmz.
From www.youtube.com
FREE SECURE BACKPACK IN EVERY DMZ GAME! (EASY GOLD SKULL FOR SOLO PLAYERS!) MW2 YouTube How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. At the. How To Secure A Dmz.
From dotesports.com
DMZ Secure Backpack How it works and how to get one How To Secure A Dmz Learn how to use dmz for secure. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing. How To Secure A Dmz.
From www.youtube.com
Downtown Post Office and Secure Room Key DMZ Location Guide YouTube How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. Learn how to use dmz for secure. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. A dmz can bring an added layer of security between. How To Secure A Dmz.
From www.zenarmor.com
What is a DMZ (Demilitarized Zone) Network? How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle. How To Secure A Dmz.
From progameguides.com
Secure and Scavenger Backpacks in DMZ, explained Pro Game Guides How To Secure A Dmz A dmz can bring an added layer of security between your precious data and potential hackers. At the very least, using a dmz and utilizing simple tips to secure your routers can make it very hard for threat actors to penetrate your network. Learn how to use dmz for secure. A demilitarized zone (dmz) is cut off from the enterprise. How To Secure A Dmz.
From www.pcinvasion.com
How To Get and Use a Secure Backpack in DMZ How To Secure A Dmz Learn how to use dmz for secure. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added layer of security. How To Secure A Dmz.
From www.downtimebros.com
How to unlock Secure Buy Station in DMZ Koschei Complex How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. A dmz can bring an added layer of security between your precious data and potential hackers. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. At the very least, using a dmz and utilizing. How To Secure A Dmz.
From www.youtube.com
Call Of Duty DMZ in தமிழில் (For Beginner) How to do Secure Intel Mission Gameavan YouTube How To Secure A Dmz A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. Learn how to use dmz for secure. A dmz can bring an added layer of security between your precious data and potential hackers. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic. How To Secure A Dmz.
From www.okta.com
DMZ Network What Is a DMZ & How Does It Work? Okta UK How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. A dmz can bring an added layer of security between your precious data and potential hackers. Learn how to use dmz for secure. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. At the. How To Secure A Dmz.
From wiki.ipfire.org
Setting up a DMZ How To Secure A Dmz A demilitarized zone (dmz) is cut off from the enterprise to facilitate access to untrusted connections. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added layer of security between your precious data and potential hackers.. How To Secure A Dmz.
From www.zenarmor.com
What is a DMZ (Demilitarized Zone) Network? How To Secure A Dmz Learn how to use dmz for secure. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A dmz can bring an added. How To Secure A Dmz.
From www.esecurityplanet.com
What Is a DMZ Network? Ultimate Guide to DMZ in Networking How To Secure A Dmz When your networking, it, or security teams begin the setup process for a dmz, you’ll first handle basic tasks like choosing a host machine and naming the dmz. A demilitarized zone network, or dmz, is a subnet that creates an extra layer of protection from external attack. A demilitarized zone (dmz) is cut off from the enterprise to facilitate access. How To Secure A Dmz.