Cookie Replay Attack Prevention Asp.net . The example is a simple asp.net web service that will be invoked through a. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Once again, the owasp cheat sheets suggest a. We use oauth2 authentication with okta for our classic asp.net mvc website. After the user logs out of the application, he can. I have followed the advice below to protect. Let’s look at a method for reducing the viability of these attacks in asp.net projects.
from blog.chain.link
Let’s look at a method for reducing the viability of these attacks in asp.net projects. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. The example is a simple asp.net web service that will be invoked through a. We use oauth2 authentication with okta for our classic asp.net mvc website. Once again, the owasp cheat sheets suggest a. I have followed the advice below to protect. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I am being asked about cookie replay attacks with my asp.net website's forms authentication. After the user logs out of the application, he can.
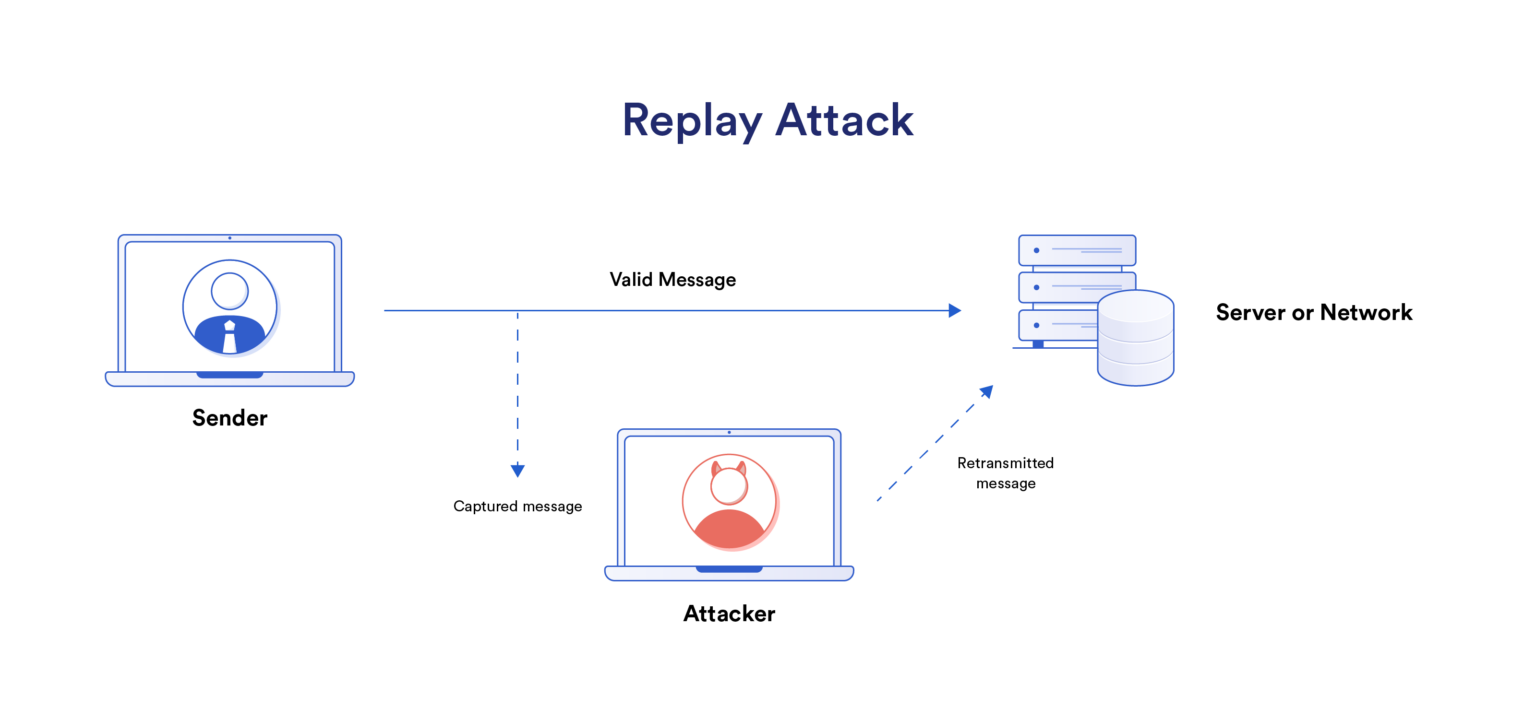
What Is a Replay Attack? Chainlink
Cookie Replay Attack Prevention Asp.net The example is a simple asp.net web service that will be invoked through a. The example is a simple asp.net web service that will be invoked through a. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Once again, the owasp cheat sheets suggest a. Let’s look at a method for reducing the viability of these attacks in asp.net projects. I have followed the advice below to protect. After the user logs out of the application, he can. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. We use oauth2 authentication with okta for our classic asp.net mvc website. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not.
From wakeupandcode.com
Cookies and Consent in ASP Core Wake Up And Code! Cookie Replay Attack Prevention Asp.net We use oauth2 authentication with okta for our classic asp.net mvc website. The example is a simple asp.net web service that will be invoked through a. Once again, the owasp cheat sheets suggest a. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. I have followed the advice below to. Cookie Replay Attack Prevention Asp.net.
From www.youtube.com
C Emulate authentication cookie YouTube Cookie Replay Attack Prevention Asp.net We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. We use oauth2 authentication with okta. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Authentication and Session Management PowerPoint Presentation Cookie Replay Attack Prevention Asp.net Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. After the user logs out of the application, he can. The example is a simple asp.net web service that will be invoked through a. I have followed the advice below to protect. Let’s look at a method. Cookie Replay Attack Prevention Asp.net.
From www.youtube.com
42 Course What is Cookies in explain How to set and Cookie Replay Attack Prevention Asp.net I have followed the advice below to protect. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Once again, the owasp cheat sheets suggest a. Let’s look at a method for reducing. Cookie Replay Attack Prevention Asp.net.
From 9to5answer.com
[Solved] How can I check for a response cookie in 9to5Answer Cookie Replay Attack Prevention Asp.net We use oauth2 authentication with okta for our classic asp.net mvc website. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Once again, the owasp cheat sheets suggest a. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to.. Cookie Replay Attack Prevention Asp.net.
From 9to5answer.com
[Solved] Using the cookie in Core but 9to5Answer Cookie Replay Attack Prevention Asp.net I have followed the advice below to protect. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. Let’s look at a method for reducing the viability of these attacks. Cookie Replay Attack Prevention Asp.net.
From referbruv.com
How to Cookie Authentication in Core MVC Cookie Replay Attack Prevention Asp.net We use oauth2 authentication with okta for our classic asp.net mvc website. Let’s look at a method for reducing the viability of these attacks in asp.net projects. I am being asked about cookie replay attacks with my asp.net website's forms authentication. The example is a simple asp.net web service that will be invoked through a. Microsoft asp.net 4.5 and earlier. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Cookie Replay Attacks PowerPoint Presentation, free download ID Cookie Replay Attack Prevention Asp.net We use oauth2 authentication with okta for our classic asp.net mvc website. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. After the user logs out of the application, he can. The example is a simple asp.net web service that will be invoked through a. Let’s look at a method. Cookie Replay Attack Prevention Asp.net.
From www.researchgate.net
(PDF) Cookie Authentication in Core API Cookie Replay Attack Prevention Asp.net I am being asked about cookie replay attacks with my asp.net website's forms authentication. Let’s look at a method for reducing the viability of these attacks in asp.net projects. The example is a simple asp.net web service that will be invoked through a. Once again, the owasp cheat sheets suggest a. We’ll explore the steps necessary to properly invalidate sessions. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Replay Attacks PowerPoint Presentation, free download ID3568479 Cookie Replay Attack Prevention Asp.net Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. After the user logs out of the application, he can. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Let’s look at a method for reducing the viability of. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Cookie Replay Attacks PowerPoint Presentation, free download ID Cookie Replay Attack Prevention Asp.net Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I have followed the advice below to protect. After the user logs out of the application, he can. The example is a simple asp.net web service that will be invoked through a. Microsoft asp.net 4.5 and earlier. Cookie Replay Attack Prevention Asp.net.
From www.cyberghostvpn.com
How to Stop Replay Attacks Forever Cookie Replay Attack Prevention Asp.net Once again, the owasp cheat sheets suggest a. Let’s look at a method for reducing the viability of these attacks in asp.net projects. After the user logs out of the application, he can. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. Microsoft asp.net 4.5 and. Cookie Replay Attack Prevention Asp.net.
From www.freecodespot.com
How to Implement CookieBased User Authentication in Core Cookie Replay Attack Prevention Asp.net I am being asked about cookie replay attacks with my asp.net website's forms authentication. After the user logs out of the application, he can. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication. Cookie Replay Attack Prevention Asp.net.
From www.vrogue.co
How To Implement Cookie Authentication In Asp Net Core Vrogue Cookie Replay Attack Prevention Asp.net Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. After the user logs out of the application, he can. Let’s look at a method for reducing the viability of these attacks in asp.net projects. Once again, the owasp cheat sheets suggest a. I am being asked about cookie replay attacks. Cookie Replay Attack Prevention Asp.net.
From www.youtube.com
Handling Cookie in Core MVC YouTube Cookie Replay Attack Prevention Asp.net Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. The example is a simple asp.net web service that will be invoked through a. Once again, the owasp cheat sheets suggest a. I have followed the advice below to protect. After the user logs out of the application, he can. Understanding. Cookie Replay Attack Prevention Asp.net.
From www.vrogue.co
Cookie Authentication In Asp Net Core vrogue.co Cookie Replay Attack Prevention Asp.net I am being asked about cookie replay attacks with my asp.net website's forms authentication. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I have followed the advice below to protect. Once again, the owasp cheat sheets suggest a. Microsoft asp.net 4.5 and earlier versions contain. Cookie Replay Attack Prevention Asp.net.
From securecloud.blog
Cookie replay client for testing Azure AD Identity Protection Cookie Replay Attack Prevention Asp.net We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. We use oauth2 authentication with okta for our classic asp.net mvc website. Let’s look at a method for reducing the viability of these attacks in asp.net projects. Understanding how session management works · learning how hackers can steal session id data · determining. Cookie Replay Attack Prevention Asp.net.
From hxeazqgwf.blob.core.windows.net
Forms Authentication Replay Attack at Christopher Brummitt blog Cookie Replay Attack Prevention Asp.net Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. We use oauth2 authentication with okta for our classic asp.net mvc website. Once again, the owasp cheat sheets suggest a. I have followed the advice below to protect. We’ll explore the steps necessary to properly invalidate sessions. Cookie Replay Attack Prevention Asp.net.
From laptrinhx.com
Cookie authentication with social providers in Core LaptrinhX Cookie Replay Attack Prevention Asp.net After the user logs out of the application, he can. The example is a simple asp.net web service that will be invoked through a. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Let’s look at a method for reducing the viability of these attacks in asp.net projects. We use oauth2 authentication with okta for. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Cookie Replay Attacks PowerPoint Presentation, free download ID Cookie Replay Attack Prevention Asp.net The example is a simple asp.net web service that will be invoked through a. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. Once again, the owasp cheat sheets suggest a. Let’s look. Cookie Replay Attack Prevention Asp.net.
From www.slideserve.com
PPT Cookie Replay Attacks PowerPoint Presentation, free download ID Cookie Replay Attack Prevention Asp.net We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. We use oauth2 authentication with okta for our classic asp.net mvc website. After the user logs out of the application, he can. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. Understanding how. Cookie Replay Attack Prevention Asp.net.
From www.certik.com
CertiK What is a Blockchain Replay Attack? Cookie Replay Attack Prevention Asp.net Let’s look at a method for reducing the viability of these attacks in asp.net projects. The example is a simple asp.net web service that will be invoked through a. I am being asked about cookie replay attacks with my asp.net website's forms authentication. After the user logs out of the application, he can. Once again, the owasp cheat sheets suggest. Cookie Replay Attack Prevention Asp.net.
From www.thesecuritybuddy.com
What are replay attacks? The Security Buddy Cookie Replay Attack Prevention Asp.net After the user logs out of the application, he can. I have followed the advice below to protect. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to.. Cookie Replay Attack Prevention Asp.net.
From blog.chain.link
What Is a Replay Attack? Chainlink Cookie Replay Attack Prevention Asp.net I am being asked about cookie replay attacks with my asp.net website's forms authentication. The example is a simple asp.net web service that will be invoked through a. Once again, the owasp cheat sheets suggest a. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. We use oauth2 authentication with. Cookie Replay Attack Prevention Asp.net.
From procodeguide.com
Implement Cookie Authentication in Core Detailed Guide Pro Cookie Replay Attack Prevention Asp.net The example is a simple asp.net web service that will be invoked through a. After the user logs out of the application, he can. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. We use oauth2 authentication with okta for our classic asp.net mvc website. Microsoft. Cookie Replay Attack Prevention Asp.net.
From cucyber.net
Replay Attacks Cookie Replay Attack Prevention Asp.net Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. I am being asked about cookie replay attacks with my asp.net website's forms authentication. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. The example is a. Cookie Replay Attack Prevention Asp.net.
From www.onelogin.com
Defending Against Session Cookie Replay Attacks OneLogin Cookie Replay Attack Prevention Asp.net I am being asked about cookie replay attacks with my asp.net website's forms authentication. Once again, the owasp cheat sheets suggest a. Let’s look at a method for reducing the viability of these attacks in asp.net projects. After the user logs out of the application, he can. We use oauth2 authentication with okta for our classic asp.net mvc website. The. Cookie Replay Attack Prevention Asp.net.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Cookie Replay Attack Prevention Asp.net We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. The example is a simple asp.net web service that will be invoked through a. We use oauth2 authentication with okta for our classic asp.net mvc website. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions. Cookie Replay Attack Prevention Asp.net.
From forestvpn.com
Replay Attack Prevention Secure Your Data ForestVPN Cookie Replay Attack Prevention Asp.net Let’s look at a method for reducing the viability of these attacks in asp.net projects. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I have followed the advice below to protect. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids. Cookie Replay Attack Prevention Asp.net.
From www.youtube.com
Cookie Howto use Session Cookie (temporary data) in Core MVC Cookie Replay Attack Prevention Asp.net Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. I have followed the advice below to protect. After the user logs out of the application, he can. We use oauth2 authentication with okta for our classic asp.net mvc website. Let’s look at a method for reducing. Cookie Replay Attack Prevention Asp.net.
From www.mdpi.com
Sustainability Free FullText ReplayAttack Detection and Cookie Replay Attack Prevention Asp.net We use oauth2 authentication with okta for our classic asp.net mvc website. I am being asked about cookie replay attacks with my asp.net website's forms authentication. After the user logs out of the application, he can. Understanding how session management works · learning how hackers can steal session id data · determining an attack has occurred and how to. The. Cookie Replay Attack Prevention Asp.net.
From www.totem.tech
What the heck are replayresistant authentication mechanisms? CMMC Cookie Replay Attack Prevention Asp.net Let’s look at a method for reducing the viability of these attacks in asp.net projects. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. After the user logs out of the application, he can. I have followed the advice below to protect. We use oauth2 authentication with okta for our. Cookie Replay Attack Prevention Asp.net.
From www.baeldung.com
What Are Replay Attacks? Baeldung on Computer Science Cookie Replay Attack Prevention Asp.net Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. I have followed the advice below to protect. Once again, the owasp cheat sheets suggest a. After the user logs out of the application,. Cookie Replay Attack Prevention Asp.net.
From www.scribd.com
COOKIE REPLAY ATTACK PREVENTION PDF Http Cookie Computer Mediated Cookie Replay Attack Prevention Asp.net After the user logs out of the application, he can. Once again, the owasp cheat sheets suggest a. Microsoft asp.net 4.5 and earlier versions contain a weakness in the forms authentication functionality whereby user sessions are not. I am being asked about cookie replay attacks with my asp.net website's forms authentication. We’ll explore the steps necessary to properly invalidate sessions. Cookie Replay Attack Prevention Asp.net.
From stackoverflow.com
how to get claims from shared cookie Stack Overflow Cookie Replay Attack Prevention Asp.net The example is a simple asp.net web service that will be invoked through a. I am being asked about cookie replay attacks with my asp.net website's forms authentication. We’ll explore the steps necessary to properly invalidate sessions upon logout, regenerate session ids upon login, and. Once again, the owasp cheat sheets suggest a. Microsoft asp.net 4.5 and earlier versions contain. Cookie Replay Attack Prevention Asp.net.