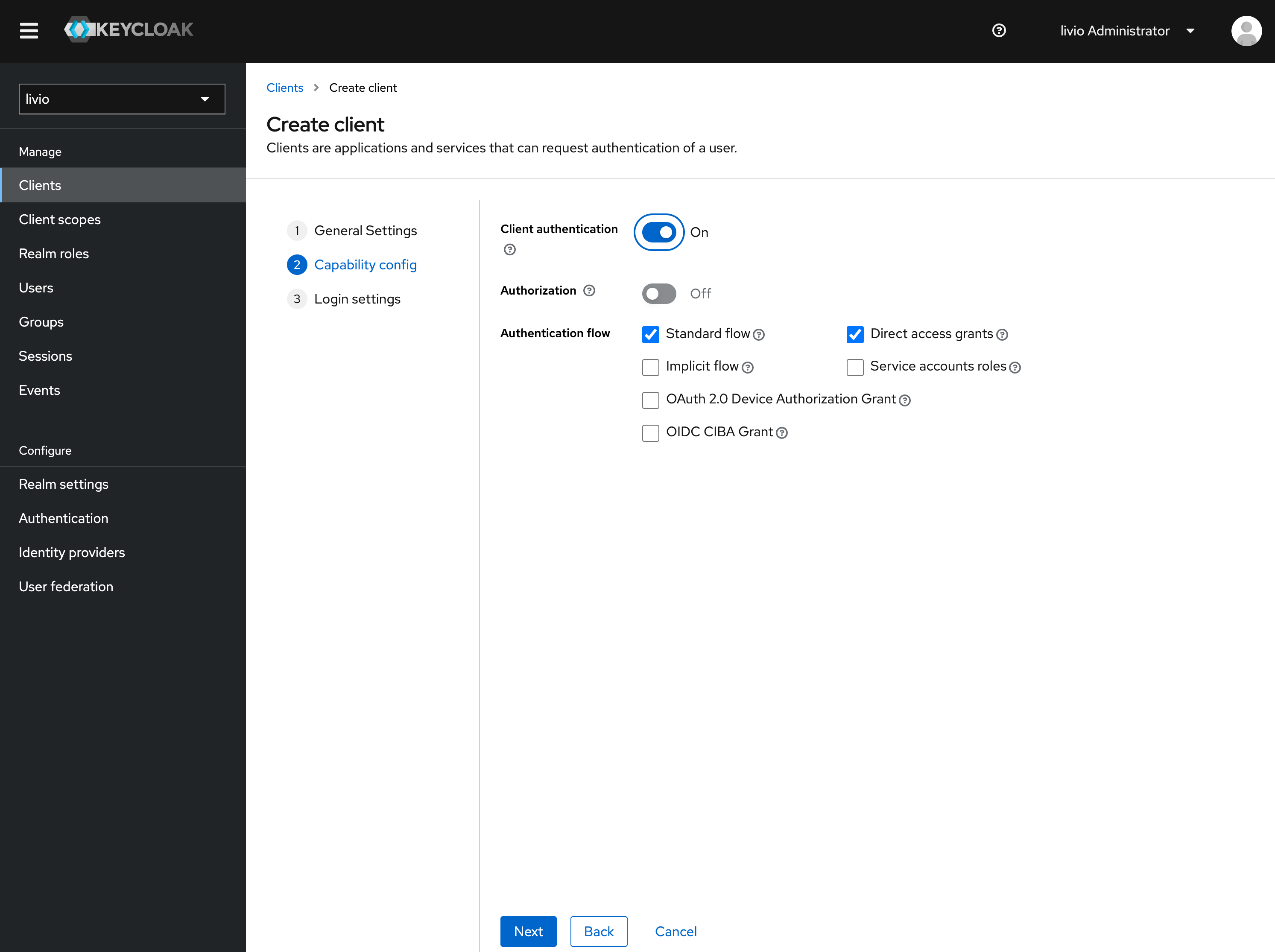
Keycloak Configure Identity Provider . The client applications redirects the user to red hat. Social login via facebook or google is an example of. To configure things on the keycloak side,. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. User is not authenticated and requests a protected resource in a client application. How can we do sso to your system?
from zitadel.com
Social login via facebook or google is an example of. The client applications redirects the user to red hat. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. Keycloak can be configured to delegate authentication to one or more idps. How can we do sso to your system? To configure things on the keycloak side,. User is not authenticated and requests a protected resource in a client application.
Configure Keycloak as an Identity Provider in ZITADEL ZITADEL Docs
Keycloak Configure Identity Provider After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. User is not authenticated and requests a protected resource in a client application. The client applications redirects the user to red hat. To configure things on the keycloak side,. How can we do sso to your system? Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure.
From nikiforovall.github.io
Use Keycloak as Identity Provider in Core 6 Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. How can we do sso to your system? Social login via facebook or google is an example of. The client applications redirects the user to red hat. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able. Keycloak Configure Identity Provider.
From zitadel.com
Configure Keycloak as an Identity Provider in ZITADEL ZITADEL Docs Keycloak Configure Identity Provider Social login via facebook or google is an example of. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on. Keycloak Configure Identity Provider.
From access.redhat.com
How to configure Microsoft Azure Active Directory as a SAML identity Keycloak Configure Identity Provider To configure things on the keycloak side,. How can we do sso to your system? Social login via facebook or google is an example of. The client applications redirects the user to red hat. Keycloak can be configured to delegate authentication to one or more idps. User is not authenticated and requests a protected resource in a client application. After. Keycloak Configure Identity Provider.
From docs.axual.io
Create and Configure a Keycloak Realms Axual Documentation Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. How can we do sso to your system? To configure things. Keycloak Configure Identity Provider.
From developer.beyondidentity.com
Integrate with KeyCloak Beyond Identity Developer Docs Keycloak Configure Identity Provider The client applications redirects the user to red hat. Social login via facebook or google is an example of. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on the keycloak side,. How can we do sso to your system? Keycloak can. Keycloak Configure Identity Provider.
From medium.com
Keycloak as an Identity Broker & an Identity Provider by Abhishek Keycloak Configure Identity Provider Social login via facebook or google is an example of. User is not authenticated and requests a protected resource in a client application. The client applications redirects the user to red hat. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. The client applications redirects the user to red hat. Social login via facebook or google is an example of. Keycloak can be configured to delegate authentication to one or more idps. How can we do sso to your system? To configure things on the keycloak side,. After. Keycloak Configure Identity Provider.
From medium.com
Keycloak for Identity and Access Management & High Availability Keycloak Configure Identity Provider The client applications redirects the user to red hat. How can we do sso to your system? Social login via facebook or google is an example of. To configure things on the keycloak side,. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. User is. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider Social login via facebook or google is an example of. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on the keycloak side,. How can we do sso to your system? The client applications redirects the user to red hat. Keycloak can. Keycloak Configure Identity Provider.
From docs.axual.io
Create and Configure a Keycloak Realms Axual Documentation Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on the keycloak side,. Social login via facebook or google is an example of. Keycloak can be configured to delegate. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider Keycloak can be configured to delegate authentication to one or more idps. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. To configure things on the keycloak side,. After reading this guide, you should be able to use the concepts and the steps herein explained to install,. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider The client applications redirects the user to red hat. Social login via facebook or google is an example of. User is not authenticated and requests a protected resource in a client application. How can we do sso to your system? Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able. Keycloak Configure Identity Provider.
From documentation.cloud-iam.com
Identity Provider Authentication with Keycloak (OIDC) CloudIAM Keycloak Configure Identity Provider Keycloak can be configured to delegate authentication to one or more idps. How can we do sso to your system? Social login via facebook or google is an example of. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. After reading this guide, you should be able. Keycloak Configure Identity Provider.
From keycloak.discourse.group
Keycloak ADFS IDP Configuring the server Keycloak Keycloak Configure Identity Provider Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on the keycloak side,. The client applications redirects the user to red hat. User is not authenticated and requests a protected. Keycloak Configure Identity Provider.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Configure Identity Provider Social login via facebook or google is an example of. User is not authenticated and requests a protected resource in a client application. The client applications redirects the user to red hat. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on. Keycloak Configure Identity Provider.
From docs.dominodatalab.com
keycloak identity providers Keycloak Configure Identity Provider Keycloak can be configured to delegate authentication to one or more idps. To configure things on the keycloak side,. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. Social login via facebook or google is an example of. How can we do sso to your system? After. Keycloak Configure Identity Provider.
From blog.beachgeek.co.uk
Integrating Keycloak as my Identity Provider for IAM Identity Centre Keycloak Configure Identity Provider After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of. To configure things on the keycloak side,. How can we do sso to your. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider How can we do sso to your system? The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. To configure things on the keycloak side,. Social login via facebook or google is an example of. After reading this guide, you should be able to use the concepts and. Keycloak Configure Identity Provider.
From zitadel.com
Configure Keycloak as an Identity Provider in ZITADEL ZITADEL Docs Keycloak Configure Identity Provider To configure things on the keycloak side,. The client applications redirects the user to red hat. Social login via facebook or google is an example of. How can we do sso to your system? Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use the concepts and the. Keycloak Configure Identity Provider.
From ahus1.github.io
SAML v2.0 Identity Providers Keycloak Docs Keycloak Configure Identity Provider To configure things on the keycloak side,. How can we do sso to your system? After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. Keycloak can be configured to delegate authentication to one or more idps. The client applications redirects the user to red hat.. Keycloak Configure Identity Provider.
From keycloak.discourse.group
Create a custom identity provider and configure it with keycloak Keycloak Configure Identity Provider Social login via facebook or google is an example of. The client applications redirects the user to red hat. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. How can we do sso to your system? To configure things on the keycloak side,. User is. Keycloak Configure Identity Provider.
From www.grebintegration.dk
Microsoft Azure Active Directory as KeyCloak Identity Provider greB Keycloak Configure Identity Provider Social login via facebook or google is an example of. How can we do sso to your system? To configure things on the keycloak side,. User is not authenticated and requests a protected resource in a client application. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use. Keycloak Configure Identity Provider.
From documentation.cloud-iam.com
Identity Provider Authentication with Keycloak (OIDC) CloudIAM Keycloak Configure Identity Provider To configure things on the keycloak side,. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. Social login via facebook or google is an example of. Keycloak can be configured to delegate authentication to one or more idps. How can we do sso to your system? After. Keycloak Configure Identity Provider.
From www.olvid.io
Olvid Keycloak Configuration Guide Configuration of an External IdP Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. Keycloak can be configured to delegate authentication to one or more idps. How can we do sso to your system? To configure things on the keycloak side,. Social login via facebook or google is an example of. The client applications redirects the user to red hat. After. Keycloak Configure Identity Provider.
From developer.beyondidentity.com
Integrate with KeyCloak Beyond Identity Developer Docs Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. The client applications redirects the user to red hat. To configure things on the keycloak side,. How can we do sso to your system? After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and. Keycloak Configure Identity Provider.
From www.youtube.com
How to add Keycloak as a SAML Identity Provider in AWS Cognito? YouTube Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is an example of. How can we do sso to your system? The client applications redirects the user to red hat. After reading this guide, you should be able. Keycloak Configure Identity Provider.
From admin.dominodatalab.com
keycloak launching workspace run Keycloak Configure Identity Provider After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. How can we do sso to your system? The client applications redirects the user to red hat. To configure things on the keycloak side,. User is not authenticated and requests a protected resource in a client. Keycloak Configure Identity Provider.
From sis-cc.gitlab.io
Thirdparty Identity Providers in Keycloak .Stat Suite documentation Keycloak Configure Identity Provider After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. Social login via facebook or google is an example of. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. How can we do. Keycloak Configure Identity Provider.
From wjw465150.gitbooks.io
General Configuration keycloakdocumentation Keycloak Configure Identity Provider How can we do sso to your system? After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. The client applications redirects the user to red hat. Keycloak can be configured to delegate authentication to one or more idps. Social login via facebook or google is. Keycloak Configure Identity Provider.
From github-wiki-see.page
Identity Provider Configuration Keycloak oidcwp/openidconnect Keycloak Configure Identity Provider How can we do sso to your system? User is not authenticated and requests a protected resource in a client application. To configure things on the keycloak side,. Keycloak can be configured to delegate authentication to one or more idps. The client applications redirects the user to red hat. After reading this guide, you should be able to use the. Keycloak Configure Identity Provider.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker Keycloak Configure Identity Provider Social login via facebook or google is an example of. The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. To configure things on the keycloak side,. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to. Keycloak Configure Identity Provider.
From medium.com
Keycloak as an Identity Broker & an Identity Provider by Abhishek Keycloak Configure Identity Provider User is not authenticated and requests a protected resource in a client application. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. To configure things on the keycloak side,. Keycloak can be configured to delegate authentication to one or more idps. How can we do. Keycloak Configure Identity Provider.
From ahus1.github.io
OpenID Connect v1.0 identity providers Keycloak Docs Keycloak Configure Identity Provider The client applications redirects the user to red hat. User is not authenticated and requests a protected resource in a client application. Keycloak can be configured to delegate authentication to one or more idps. To configure things on the keycloak side,. After reading this guide, you should be able to use the concepts and the steps herein explained to install,. Keycloak Configure Identity Provider.
From zitadel.com
Configure Keycloak as an Identity Provider in ZITADEL ZITADEL Docs Keycloak Configure Identity Provider Social login via facebook or google is an example of. The client applications redirects the user to red hat. To configure things on the keycloak side,. Keycloak can be configured to delegate authentication to one or more idps. After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable,. Keycloak Configure Identity Provider.
From demo.kube-plus.cloud
Setup IDP integration on keycloak Application Platform Docs Keycloak Configure Identity Provider How can we do sso to your system? After reading this guide, you should be able to use the concepts and the steps herein explained to install, uninstall, enable, disable, and configure. Social login via facebook or google is an example of. The client applications redirects the user to red hat. Keycloak can be configured to delegate authentication to one. Keycloak Configure Identity Provider.