Enforces An Access Control Policy Based On Packet Content . Enforces an access control policy based on packet content lock a setting in an access control policy to enforce the setting in all descendant policies. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. what is the role of an ips? the three design layers from lowest to highest are access, distribution, and core.
from docs.cloud.ruckuswireless.com
the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips? lock a setting in an access control policy to enforce the setting in all descendant policies. Enforces an access control policy based on packet content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security.
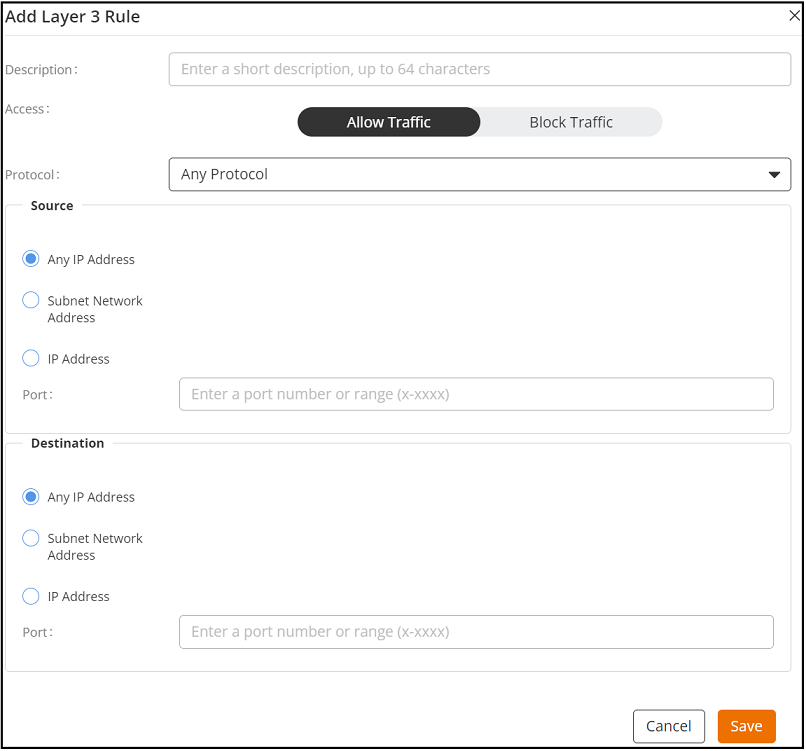
Creating an Access Control Policy
Enforces An Access Control Policy Based On Packet Content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. what is the role of an ips? access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. lock a setting in an access control policy to enforce the setting in all descendant policies. the three design layers from lowest to highest are access, distribution, and core. Enforces an access control policy based on packet content
From www.scribd.com
Configuring RoleBased Access Control To Enforce Mandatory and Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. Enforces an access control policy based on packet content the reference monitor enforces an access control policy over all subjects and objects, ensuring that. Enforces An Access Control Policy Based On Packet Content.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Enforces An Access Control Policy Based On Packet Content Enforces an access control policy based on packet content access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the fastpath rule action in the prefilter policy bypasses all. Enforces An Access Control Policy Based On Packet Content.
From www.vrogue.co
What Is Authorization And Access Control vrogue.co Enforces An Access Control Policy Based On Packet Content Enforces an access control policy based on packet content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the three design layers from lowest to highest are access,. Enforces An Access Control Policy Based On Packet Content.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Enforces An Access Control Policy Based On Packet Content access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. Enforces an access control policy based on packet content the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips? lock a setting in an access control policy. Enforces An Access Control Policy Based On Packet Content.
From axiomatics.com
What is Policy Based Access Control (PBAC)? Axiomatics Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. the three design layers from lowest to highest are access, distribution, and core. Enforces an access control policy based on packet content access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance.. Enforces An Access Control Policy Based On Packet Content.
From www.nccoe.nist.gov
Attribute Based Access Control Enforces An Access Control Policy Based On Packet Content the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips? lock a setting in an access control policy to enforce the setting in all descendant policies. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the reference. Enforces An Access Control Policy Based On Packet Content.
From dokumen.tips
(PPT) Configuring RoleBased Access Control to Enforce Mandatory and Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the three design layers from lowest to highest are access, distribution, and core. lock a setting in an access control policy to enforce the setting in all descendant policies. Enforces. Enforces An Access Control Policy Based On Packet Content.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. Enforces an access control policy based on packet content access control policies can be enforced by assigning devices to specific vlans based. Enforces An Access Control Policy Based On Packet Content.
From www.resmo.com
9 Access Control Best Practices Resmo Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. what is the role of an ips? access control policies can be enforced by assigning devices to specific vlans based. Enforces An Access Control Policy Based On Packet Content.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. lock a setting in an access control policy to enforce the setting in. Enforces An Access Control Policy Based On Packet Content.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the three design layers from lowest to highest are access, distribution, and core. lock a setting in an access control policy to enforce the setting in all descendant policies. the reference monitor enforces an access control policy over all. Enforces An Access Control Policy Based On Packet Content.
From www.controlcase.com
Access Control Policy and Procedures Template ControlCase Enforces An Access Control Policy Based On Packet Content the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips? the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. Enforces an access control policy based on packet content the reference monitor enforces an access control policy over all. Enforces An Access Control Policy Based On Packet Content.
From www.immuta.com
How to Enforce Access Control Policies with Your Metadata Immuta Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the three design layers from lowest to highest are access, distribution, and core. lock a setting in an access control policy to enforce the setting in all descendant policies. Enforces an access control policy based on packet content access control policies can be enforced by assigning devices to specific. Enforces An Access Control Policy Based On Packet Content.
From www.nextlabs.com
What is PolicyBased Access Control (PBAC)? NextLabs Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the three design layers from lowest to highest are access, distribution, and core. Enforces an access control policy based on packet content. Enforces An Access Control Policy Based On Packet Content.
From www.slideserve.com
PPT RoleBased Access Control PowerPoint Presentation, free download Enforces An Access Control Policy Based On Packet Content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. what is the role of an ips? lock a setting in an access control policy to enforce the setting in all descendant policies. the three design layers from lowest to highest are access, distribution, and core. Enforces. Enforces An Access Control Policy Based On Packet Content.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Enforces An Access Control Policy Based On Packet Content what is the role of an ips? access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. Enforces an access control policy based on packet content lock a setting in an access control policy to enforce the setting in all descendant policies. the reference monitor enforces an. Enforces An Access Control Policy Based On Packet Content.
From www.scribd.com
Access Control Policy Template PDF Enforces An Access Control Policy Based On Packet Content what is the role of an ips? lock a setting in an access control policy to enforce the setting in all descendant policies. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the reference monitor enforces an access control policy over all subjects and objects, ensuring. Enforces An Access Control Policy Based On Packet Content.
From www.scribd.com
Access_Control_Policy_EN PDF Enforces An Access Control Policy Based On Packet Content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. lock a setting in an access control policy to enforce the setting in all descendant policies. what is. Enforces An Access Control Policy Based On Packet Content.
From www.slideteam.net
Standard Access Control Policy Format PPT Template Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the three design layers from lowest to highest are access, distribution, and core. lock a setting in an access control. Enforces An Access Control Policy Based On Packet Content.
From treewebsolutions.com
What Is RoleBased Access Control (RBAC)? Tree Solutions Enforces An Access Control Policy Based On Packet Content the three design layers from lowest to highest are access, distribution, and core. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. lock a setting in an access control policy to enforce the setting in all descendant policies. access control policies can be enforced by assigning devices to. Enforces An Access Control Policy Based On Packet Content.
From docs.cloud.ruckuswireless.com
Creating an Access Control Policy Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. what is the role of an ips? the three design layers from lowest to highest are access, distribution, and core. . Enforces An Access Control Policy Based On Packet Content.
From dokumen.tips
(PDF) Configuring RoleBased Access Control to Enforce Mandatory Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the three design layers from lowest to highest are access, distribution, and core. Enforces an access control policy based on packet content the fastpath rule action in the prefilter policy. Enforces An Access Control Policy Based On Packet Content.
From www.researchgate.net
(PDF) Enforcing RoleBased Access Control Policies in Services with Enforces An Access Control Policy Based On Packet Content Enforces an access control policy based on packet content what is the role of an ips? access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the three design layers. Enforces An Access Control Policy Based On Packet Content.
From www.researchgate.net
Format of a Role Based Access Control Policy Download Scientific Diagram Enforces An Access Control Policy Based On Packet Content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. lock a setting in an access control policy to enforce the setting in all descendant policies. what is. Enforces An Access Control Policy Based On Packet Content.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the. Enforces An Access Control Policy Based On Packet Content.
From www.scribd.com
Access Control Policy Template PDF Access Control User Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the three design layers from lowest to highest are access, distribution, and core.. Enforces An Access Control Policy Based On Packet Content.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the fastpath rule action in the prefilter policy bypasses all further packet inspection and. Enforces An Access Control Policy Based On Packet Content.
From blog.plainid.com
Policy Based Access Control 5 Key Features Enforces An Access Control Policy Based On Packet Content Enforces an access control policy based on packet content lock a setting in an access control policy to enforce the setting in all descendant policies. the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips? the fastpath rule action in the prefilter policy bypasses all further. Enforces An Access Control Policy Based On Packet Content.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Enforces An Access Control Policy Based On Packet Content the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the three design layers from lowest to highest are access, distribution, and core. lock a setting in an access control policy to enforce the setting in all descendant policies. Enforces an access control policy based on packet content. Enforces An Access Control Policy Based On Packet Content.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID829739 Enforces An Access Control Policy Based On Packet Content what is the role of an ips? Enforces an access control policy based on packet content access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the fastpath. Enforces An Access Control Policy Based On Packet Content.
From www.verticalrelevance.com
Using AWS Lambda’s New Attribute Based Access Control (ABAC) to Enforce Enforces An Access Control Policy Based On Packet Content the three design layers from lowest to highest are access, distribution, and core. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. Enforces an access control policy based on packet. Enforces An Access Control Policy Based On Packet Content.
From www.effectivegovernance.com.au
Do you need a policy on policies? Effective Governance Enforces An Access Control Policy Based On Packet Content lock a setting in an access control policy to enforce the setting in all descendant policies. what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. access control policies can be enforced by assigning devices to specific vlans based on. Enforces An Access Control Policy Based On Packet Content.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Enforces An Access Control Policy Based On Packet Content the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance. the three design layers from lowest to highest are access, distribution, and core. what is the role of an ips?. Enforces An Access Control Policy Based On Packet Content.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the reference monitor enforces an access control policy over all subjects and objects, ensuring that access is restricted based. the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. Enforces an access control policy based on packet content the three design layers. Enforces An Access Control Policy Based On Packet Content.
From www.formsbirds.com
Access Control Policy Template 2 Free Templates in PDF, Word, Excel Enforces An Access Control Policy Based On Packet Content what is the role of an ips? the fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security. the three design layers from lowest to highest are access, distribution, and core. access control policies can be enforced by assigning devices to specific vlans based on their identity, type, or compliance.. Enforces An Access Control Policy Based On Packet Content.