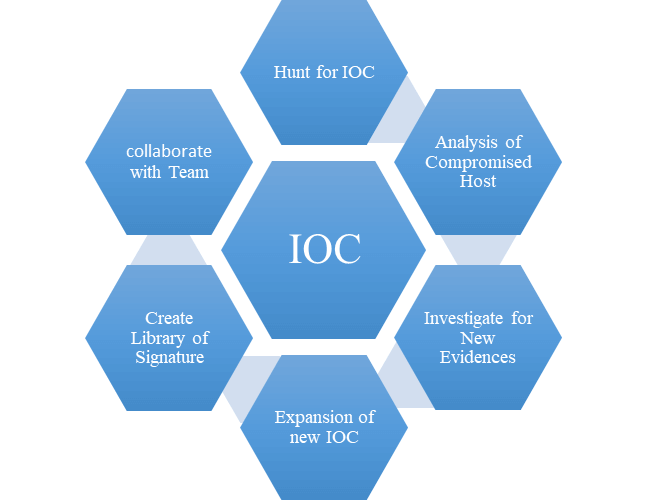
Indicator Of Compromise Database . Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. This guide explores the types of iocs, their. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. 251 rows threatfox ioc database. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. You are browsing the indicator of compromise (ioc) database of threatfox. If you would like to.
from hackforlab.com
An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. You are browsing the indicator of compromise (ioc) database of threatfox. If you would like to. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. 251 rows threatfox ioc database.
Indicator of Attack vs Indicator of Compromises
Indicator Of Compromise Database 251 rows threatfox ioc database. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. 251 rows threatfox ioc database. If you would like to. You are browsing the indicator of compromise (ioc) database of threatfox. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. This guide explores the types of iocs, their.
From any.run
IoC Indicators of Compromise ANY.RUN Blog Indicator Of Compromise Database An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (ioc). Indicator Of Compromise Database.
From publish.obsidian.md
indicators of compromise Cyber MiSC Obsidian Publish Indicator Of Compromise Database An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. 251 rows threatfox ioc database. If you would like to. You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Threatfox is a free platform. Indicator Of Compromise Database.
From hackforlab.com
Indicator of Attack vs Indicator of Compromises Indicator Of Compromise Database This guide explores the types of iocs, their. 251 rows threatfox ioc database. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. You are browsing the indicator of compromise (ioc) database of threatfox. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s. Indicator Of Compromise Database.
From medium.com
A Guide to Indicators of Compromise (IoC) Analysis by Paritosh Medium Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. This guide explores the types of iocs, their. 251 rows threatfox ioc database. If you would like to. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. You are. Indicator Of Compromise Database.
From www.trendmicro.com.my
Empowering the Analyst Indicators of Compromise Security News Indicator Of Compromise Database An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (ioc) help. Indicator Of Compromise Database.
From medium.com
Indicators of Compromise (IOCs). are pieces of evidence that suggest a Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) are artifacts that indicate a. Indicator Of Compromise Database.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Indicator Of Compromise Database Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (ioc) help organizations. Indicator Of Compromise Database.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.15] Elastic Indicator Of Compromise Database This guide explores the types of iocs, their. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. 251 rows threatfox ioc database. If you would like to. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise. Indicator Of Compromise Database.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicator Of Compromise Database You are browsing the indicator of compromise (ioc) database of threatfox. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (iocs) are artifacts. Indicator Of Compromise Database.
From www.lepide.com
What are Indicators of Compromise? Indicator Of Compromise Database Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. You are browsing the indicator of compromise (ioc) database of threatfox. If you would like to. This guide explores the types of iocs, their. Indicators of compromise. Indicator Of Compromise Database.
From www.youtube.com
What are the Indicators of compromise YouTube Indicator Of Compromise Database Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s. Indicator Of Compromise Database.
From www.lepide.com
What are Indicators of Compromise? Indicator Of Compromise Database You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. 251 rows threatfox ioc database. Threatfox is a free platform from. Indicator Of Compromise Database.
From www.onlinesolutionsgroup.de
Indicators of Compromise (IoCs) ⏩ Online Marketing Glossar der OSG Indicator Of Compromise Database Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have. Indicator Of Compromise Database.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. If you would like to. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an. Indicator Of Compromise Database.
From www.upguard.com
What are Indicators of Attack (IOAs)? How they Differ from IOCs UpGuard Indicator Of Compromise Database 251 rows threatfox ioc database. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (iocs). Indicator Of Compromise Database.
From www.mdpi.com
JCP Free FullText Sharing Machine Learning Models as Indicators of Indicator Of Compromise Database Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached.. Indicator Of Compromise Database.
From www.scribd.com
Top 15 Indicators of Compromise PDF Denial Of Service Attack Indicator Of Compromise Database Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (ioc) help organizations locate and confirm the presence of. Indicator Of Compromise Database.
From www.youtube.com
What is IOC and IOA Indicator of Attack and Indicator of Compromise Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. If you would like to. You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (iocs). Indicator Of Compromise Database.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Indicator Of Compromise Database An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. You are browsing the indicator of compromise (ioc) database of threatfox. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. Indicators of compromise (iocs) refer to data that. Indicator Of Compromise Database.
From cyberhoot.com
Indicators of Compromise (IoC) CyberHoot Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. You are browsing the indicator of compromise (ioc) database of threatfox. This guide explores the types of iocs, their. An indicator of compromise (ioc) is evidence that someone. Indicator Of Compromise Database.
From www.elastic.co
Indicators of compromise Elastic Security Solution [8.10] Elastic Indicator Of Compromise Database This guide explores the types of iocs, their. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. 251 rows threatfox ioc database. You are browsing the indicator of compromise (ioc) database of threatfox. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or. Indicator Of Compromise Database.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Indicator Of Compromise Database This guide explores the types of iocs, their. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. You are browsing the indicator of compromise (ioc) database of threatfox. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators. Indicator Of Compromise Database.
From aplikas.com
Indicator of Compromise Cara Cerdas Antisipasi Ancaman Cyber Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. This guide explores the types of iocs, their. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (ioc) help organizations locate and confirm the presence of. Indicator Of Compromise Database.
From flare.io
What are Indicators of Compromise in Threat Intelligence? Flare Indicator Of Compromise Database This guide explores the types of iocs, their. Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. If you would like to. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators of compromise (iocs) refer to data that indicates a system. Indicator Of Compromise Database.
From www.rstcloud.com
Public Database of 10M Indicators of Compromise RST Cloud Indicator Of Compromise Database You are browsing the indicator of compromise (ioc) database of threatfox. If you would like to. This guide explores the types of iocs, their. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been. Indicator Of Compromise Database.
From www.linkedin.com
Indicators of Compromise (IOCs) Explained Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. If you would like to. An indicator of compromise. Indicator Of Compromise Database.
From www.linkedin.com
The Importance and Difference Between Indicators of Attack and Indicator Of Compromise Database 251 rows threatfox ioc database. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s. Indicator Of Compromise Database.
From www.salvagedata.com
Cyber Security Awareness What Are Indicators of Compromise (IoC Indicator Of Compromise Database Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. You are browsing the indicator of compromise (ioc) database of threatfox. If you would like to. Indicators of compromise. Indicator Of Compromise Database.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Indicator Of Compromise Database This guide explores the types of iocs, their. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. 251 rows threatfox ioc database. You are browsing the indicator of compromise (ioc) database of threatfox. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or. Indicator Of Compromise Database.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Indicator Of Compromise Database An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. If you would like to. This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of. Indicator Of Compromise Database.
From cyberartspro.com
IoC (Indicator Of Compromise) Nedir? CyberArts Indicator Of Compromise Database Threatfox is a free platform from abuse.ch with the goal of sharing indicators of compromise (iocs) associated with malware with the. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. 251 rows threatfox ioc database. If you would like to. You are browsing the indicator of compromise (ioc) database of. Indicator Of Compromise Database.
From docs.fortinet.com
Indicator of Compromise log types and custom view 7.4.2 FortiAnalyzer Indicator Of Compromise Database An indicator of compromise (ioc) is evidence that someone may have breached an organization’s network. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. 251 rows threatfox ioc database. You are browsing the indicator of compromise (ioc) database of threatfox. This guide explores the types of iocs, their. An indicator of compromise (ioc) is a piece of digital. Indicator Of Compromise Database.
From www.redpacketsecurity.com
Indicators of compromise (IOCs) how we collect and use them Indicator Of Compromise Database Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. An indicator of compromise (ioc) is evidence that. Indicator Of Compromise Database.
From fineproxy.org
Indicator of Compromise (IOC) FineProxy Glossary Indicator Of Compromise Database You are browsing the indicator of compromise (ioc) database of threatfox. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. This guide explores the types of iocs, their. 251 rows threatfox ioc database. An indicator of compromise (ioc) is evidence that someone may have breached an organization’s. Indicator Of Compromise Database.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicator Of Compromise Database Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (ioc) help organizations locate and confirm the presence of malicious software on a device or network. 251 rows threatfox ioc database. This guide explores. Indicator Of Compromise Database.