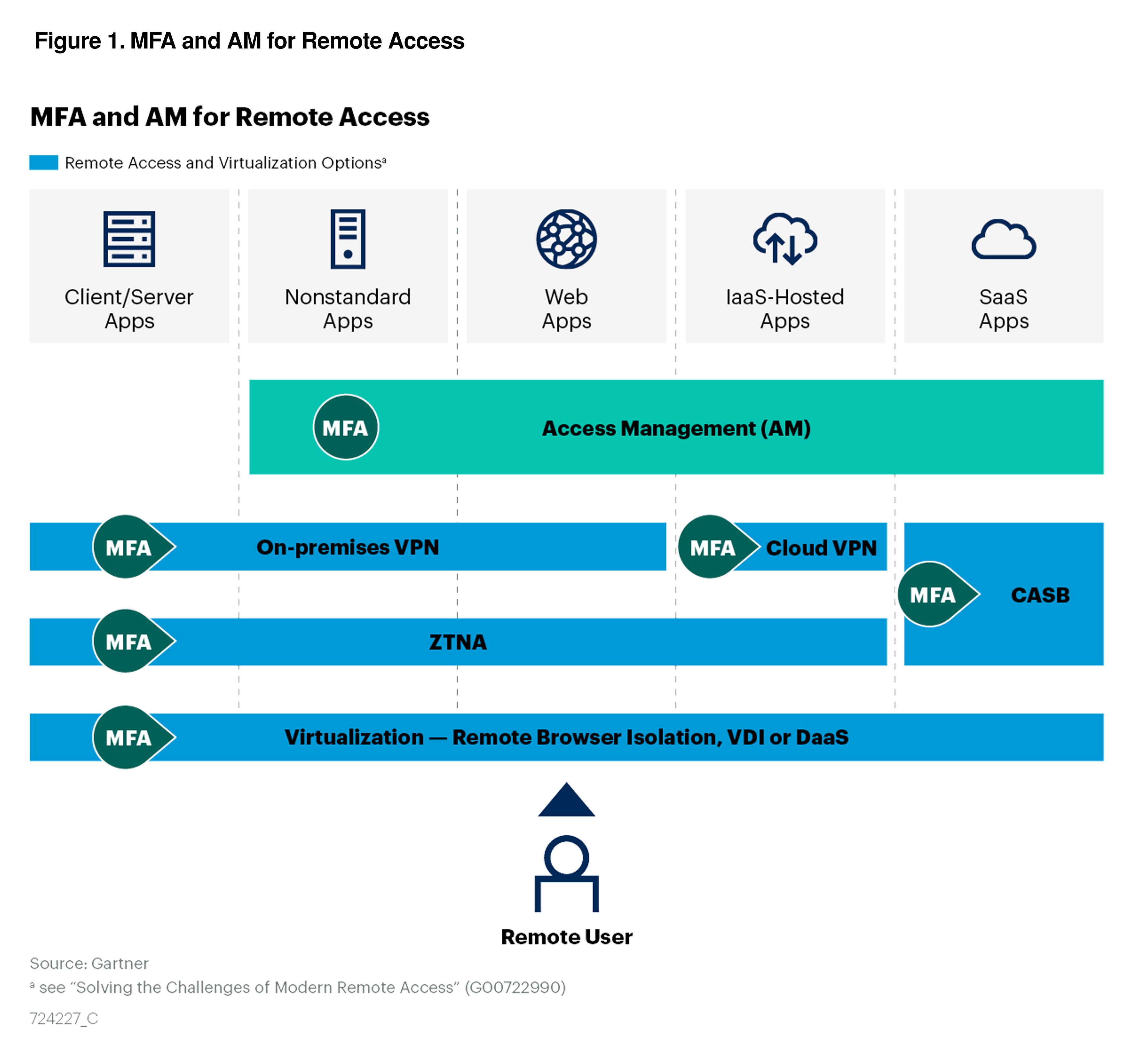
Security Controls For Remote Access Domain . Whether the network threats are intentional or not, they're still predictable. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies.
from www.okta.com
In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Whether the network threats are intentional or not, they're still predictable. The nature of telework and. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations.
Enhance Remote Access Security With Multifactor Authentication and
Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. The nature of telework and. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized.
From tiptopsecurity.com
All About VPNs « TipTopSecurity Security Controls For Remote Access Domain The nature of telework and. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. In this. Security Controls For Remote Access Domain.
From iebmedia.com
Five key considerations for secure remote access solutions Industrial Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. The nature of telework and. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies. Security Controls For Remote Access Domain.
From blog.isa.org
How to Implement Secure, Remote Access to an Industrial Automation System Security Controls For Remote Access Domain Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. The. Security Controls For Remote Access Domain.
From in.pinterest.com
5 steps to Secure Remote Access Remote, Access, Telework Security Controls For Remote Access Domain The nature of telework and. Whether the network threats are intentional or not, they're still predictable. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote. Security Controls For Remote Access Domain.
From duo.com
The Essential Guide to Securing Remote Access Duo Security Security Controls For Remote Access Domain Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide,. Security Controls For Remote Access Domain.
From www.okta.com
Enhance Remote Access Security With Multifactor Authentication and Security Controls For Remote Access Domain The nature of telework and. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data. Security Controls For Remote Access Domain.
From www.youtube.com
Secure Remote Access Network Control VPN System YouTube Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote. Security Controls For Remote Access Domain.
From www.cr-t.com
What is Secure Remote Access? IT Services in Utah CRT Security Controls For Remote Access Domain By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set. Security Controls For Remote Access Domain.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Controls For Remote Access Domain The nature of telework and. Whether the network threats are intentional or not, they're still predictable. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access. Security Controls For Remote Access Domain.
From www.researchgate.net
Remote access domain [8]. Download Scientific Diagram Security Controls For Remote Access Domain The nature of telework and. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Whether the network threats are intentional or not, they're still predictable. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. By. Security Controls For Remote Access Domain.
From www.oreilly.com
The Seven Domains of a Typical IT Infrastructure Fundamentals of Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. In this guide, we examine how businesses should. Security Controls For Remote Access Domain.
From iptechlabs.com
Model 770 Series Secure Remote Access Appliance Performance Server with Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The. Security Controls For Remote Access Domain.
From washingtonindependent.com
Secure Remote Access IoT Guardians Of Connectivity Security Controls For Remote Access Domain In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. Remote. Security Controls For Remote Access Domain.
From sectigostore.com
Top 5 Key Considerations for Secure Remote Access InfoSec Insights Security Controls For Remote Access Domain The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications,. Security Controls For Remote Access Domain.
From www.venn.com
What is Secure Remote Access Control? Venn Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. The nature of telework and. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies. Security Controls For Remote Access Domain.
From securedebug.com
Best Practices for Remote Access Security Controls Secure Debug Security Controls For Remote Access Domain In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. Whether the network threats are intentional or not, they're still predictable. Remote. Security Controls For Remote Access Domain.
From www.ssh.com
Guide to Secure Remote Access Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. The nature of telework and. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. By creating solid controls and policies surrounding remote access and utilizing best practices like. Security Controls For Remote Access Domain.
From purplesec.us
Types Of Security Controls Explained Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or. Security Controls For Remote Access Domain.
From aws.amazon.com
Securely extend and access onpremises Active Directory domain Security Controls For Remote Access Domain In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. By. Security Controls For Remote Access Domain.
From www.oreilly.com
Devices and Components Commonly Found in the Remote Access Domain Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide,. Security Controls For Remote Access Domain.
From www.ccontrols.com
AHR 2024 Secure Remote Access Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. The nature of telework and. Secure remote access refers to the methods and. Security Controls For Remote Access Domain.
From aws.amazon.com
Securely extend and access onpremises Active Directory domain Security Controls For Remote Access Domain Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. In. Security Controls For Remote Access Domain.
From bleuwire.com
How to Set up Secure Remote Network Access Bleuwire Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Whether the network threats are intentional. Security Controls For Remote Access Domain.
From www.conceptdraw.com
Network Security Security Controls For Remote Access Domain The nature of telework and. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data. Security Controls For Remote Access Domain.
From www.youtube.com
VPNs and Remote Access Protocols CompTIA Security+ Performance Based Security Controls For Remote Access Domain The nature of telework and. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Whether the network threats are intentional or not, they're still predictable. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. By. Security Controls For Remote Access Domain.
From apstorm.co.uk
Remote Access Solutions ApStorm Security Controls For Remote Access Domain In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. By creating solid controls and policies surrounding remote access and utilizing best. Security Controls For Remote Access Domain.
From www.boydsecurity.com
How to Secure Your Remote Access Security Camera System 𝗕𝗼𝘆𝗱 & 𝗔𝘀𝘀𝗼𝗰𝗶𝗮𝘁𝗲𝘀 Security Controls For Remote Access Domain Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Secure remote access refers to the methods and technologies that allow users to. Security Controls For Remote Access Domain.
From www.remote-accesss.com
What Is Remote Access Domain Security Controls For Remote Access Domain The nature of telework and. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies. Security Controls For Remote Access Domain.
From duo.com
The Essential Guide to Securing Remote Access Duo Security Security Controls For Remote Access Domain By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure. Security Controls For Remote Access Domain.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Security Controls For Remote Access Domain By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Whether the network threats are intentional or not, they're still predictable. Remote access security (sometimes called “secure remote. Security Controls For Remote Access Domain.
From www.greyson.com
Remote Access VPN Guide Greyson Technologies Florida Security Controls For Remote Access Domain Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure. Security Controls For Remote Access Domain.
From blog.techprognosis.com
Secure Remote Access Keeping Business Going with Remote Work Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Whether the network threats are intentional or not, they're still predictable. Secure remote access refers to the methods and technologies that allow users to. Security Controls For Remote Access Domain.
From mgiaccess.com
Access Control System 2023 A Guide from Basics to Advanced Techniques Security Controls For Remote Access Domain Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. In. Security Controls For Remote Access Domain.
From info.pivitglobal.com
Remote Access Clientless VPN What You Need To Know Security Controls For Remote Access Domain Secure remote access refers to the methods and technologies that allow users to access an organization's network, applications, or data securely from remote locations. The nature of telework and. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Whether the network threats are intentional or not, they're still predictable. Remote. Security Controls For Remote Access Domain.
From www.beyondtrust.com
How the Right Secure Remote Access Solution can Help You Reduce Costs Security Controls For Remote Access Domain By creating solid controls and policies surrounding remote access and utilizing best practices like auditing and logging, your. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies. Remote access security (sometimes called “secure remote access”) comprises technologies and processes that help ensure only authorized. Secure remote access refers to the. Security Controls For Remote Access Domain.