Jinja2 Filter Bypass . The filter is the first stage. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? However, to bypass the filters, we are essentially only using two strategies: Leveraging the jina2 attr() filter and hex. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The first filter looks config and. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,.
from progala.net
In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. However, to bypass the filters, we are essentially only using two strategies: Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The filter is the first stage. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Leveraging the jina2 attr() filter and hex. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.?
Jinja2 Tutorial Part 4 Template filters
Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The first filter looks config and. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. Leveraging the jina2 attr() filter and hex. The filter is the first stage. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? However, to bypass the filters, we are essentially only using two strategies: In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?.
From abstractkitchen.com
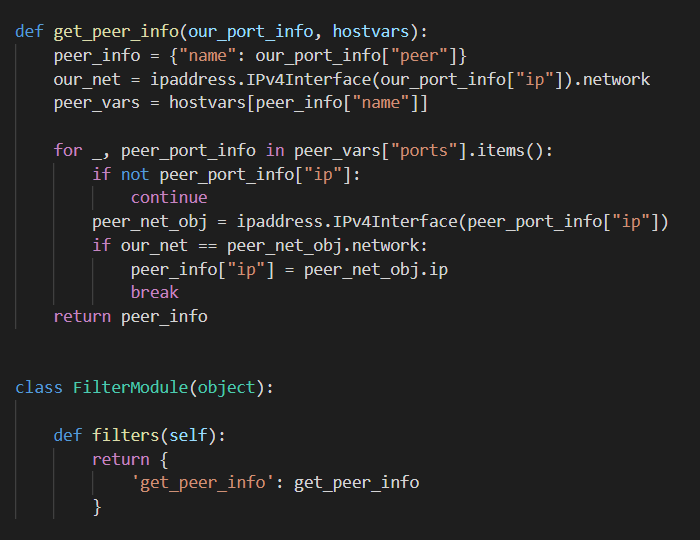
How to Create Jinja2 Filters in Flask. Jinja2 Filter Bypass Leveraging the jina2 attr() filter and hex. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. To check the class in ssti jinja2 we can use payload { {. Jinja2 Filter Bypass.
From fyonmhvtw.blob.core.windows.net
Jinja2 Filter Escape Characters at Jill Burns blog Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: The first filter looks config and. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Leveraging the jina2 attr() filter and. Jinja2 Filter Bypass.
From www.packetcoders.io
How to Use Jinja Custom Filters within Nornir Jinja2 Filter Bypass Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). However, to bypass the filters, we are essentially only using two strategies: Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The filter is the first stage. Is it. Jinja2 Filter Bypass.
From github.com
Ansible filter_plugins (Jinja2 filters) cannot import python modules Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. However, to bypass the filters, we are essentially only using two strategies: Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? The first filter looks config and. Leveraging the. Jinja2 Filter Bypass.
From www.packetswitch.co.uk
How to Create Custom Jinja2 Filters? Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? The filter is the first stage. Leveraging the jina2 attr() filter and hex. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods. Jinja2 Filter Bypass.
From www.youtube.com
PYTHON How to import custom jinja2 filters from another file (and Jinja2 Filter Bypass In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. However, to bypass the filters, we are essentially only using two strategies: Generally, if there is a blacklist you can use. Jinja2 Filter Bypass.
From blog.amsoil.com
A Closer Look at Bypass Filtration Jinja2 Filter Bypass The filter is the first stage. However, to bypass the filters, we are essentially only using two strategies: To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Generally, if there. Jinja2 Filter Bypass.
From www.youtube.com
Build Your Own Filter Bypass! DIY Bypass For Water Filter Systems Jinja2 Filter Bypass Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The first filter looks config and. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. To check the class in ssti jinja2 we can use payload { { ().__class__}}. Jinja2 Filter Bypass.
From exorfzlic.blob.core.windows.net
Jinja2 Filter Attr at Evelyn Contreras blog Jinja2 Filter Bypass To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Leveraging the jina2 attr() filter and hex. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The first filter looks config and. In jinja2/flask it is possible to initialize variables. Jinja2 Filter Bypass.
From 9to5answer.com
[Solved] How to import custom jinja2 filters from another 9to5Answer Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? The filter is the first stage. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). In jinja2/flask it is possible to. Jinja2 Filter Bypass.
From www.slideshare.net
Jinja2 filters Jinja2 Filter Bypass In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. However, to bypass the filters, we are essentially only using two strategies: The first filter looks config and. The filter is the first stage. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param. Jinja2 Filter Bypass.
From codingnetworker.com
Custom filters for a Jinja2 based Config Generator Coding Networker Blog Jinja2 Filter Bypass Leveraging the jina2 attr() filter and hex. The filter is the first stage. However, to bypass the filters, we are essentially only using two strategies: Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new. Jinja2 Filter Bypass.
From www.youtube.com
Network Automation Master Jinja2 Configuration GenerationApply loops Jinja2 Filter Bypass The first filter looks config and. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? The filter is the first stage. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. However, to bypass the filters, we are essentially only using two strategies:. Jinja2 Filter Bypass.
From medium.com
Jinja2 SSTI filter bypasses. as you (should) know — blacklists are Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: Leveraging the jina2 attr() filter and hex. The first filter looks config and. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The filter is the first stage. To check the class in ssti jinja2 we can use payload. Jinja2 Filter Bypass.
From www.packetswitch.co.uk
How to Use Jinja2 Filters in Ansible Jinja2 Filter Bypass Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Can anyone suggest. Jinja2 Filter Bypass.
From progala.net
Jinja2 Tutorial Part 4 Template filters Jinja2 Filter Bypass Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Leveraging the jina2 attr() filter and hex. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about. Jinja2 Filter Bypass.
From www.packetcoders.io
How to Use Jinja Custom Filters within Nornir Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. The filter is the first stage. The first filter looks config and. Leveraging the jina2 attr() filter and hex. However,. Jinja2 Filter Bypass.
From www.xmsec.cc
从SSTI到沙箱逃逸jinja2 Jinja2 Filter Bypass Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The first filter looks config and. The filter is the first stage. However, to bypass the filters, we are essentially only using two strategies:. Jinja2 Filter Bypass.
From github.com
GitHub Jinja2 filter to compress vlan Jinja2 Filter Bypass The first filter looks config and. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding. Jinja2 Filter Bypass.
From fyonmhvtw.blob.core.windows.net
Jinja2 Filter Escape Characters at Jill Burns blog Jinja2 Filter Bypass Leveraging the jina2 attr() filter and hex. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Generally, if there is a blacklist you can. Jinja2 Filter Bypass.
From github.com
[BGP Group][Direct Session] No jinja2 filter to remove mask from Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Leveraging the jina2 attr() filter and hex. However, to bypass the. Jinja2 Filter Bypass.
From www.dhgate.com
Stainless Steel Kitchen Sink Strainer Stopper With Waste Plug Jinja2 Jinja2 Filter Bypass The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. However, to bypass the filters, we are essentially only using two strategies: Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The filter is. Jinja2 Filter Bypass.
From www.linuxtechi.com
How to Use Jinja2 Template in Ansible Playbook Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: The filter is the first stage. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Leveraging the jina2. Jinja2 Filter Bypass.
From github.com
Jinja2 Custom Filters not supported in the format_execution_result Jinja2 Filter Bypass Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. The filter is the first stage. Is it getting filtered in the web app, a. Jinja2 Filter Bypass.
From github.com
regex_replace jinja2 filter · Issue 11478 · frappe/frappe · GitHub Jinja2 Filter Bypass Leveraging the jina2 attr() filter and hex. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The filter is the first stage. To check the class in ssti jinja2. Jinja2 Filter Bypass.
From www.youtube.com
Unix & Linux Ansible jinja2 filter reject (2 Solutions!!) YouTube Jinja2 Filter Bypass Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). Leveraging the jina2 attr() filter and hex. The first filter looks config and. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? In jinja2/flask it is possible to initialize variables for templates, and. Jinja2 Filter Bypass.
From github.com
Custom jinja filters JINJA2_FILTERS · netbox Jinja2 Filter Bypass Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding etc hasn’t worked). The first filter looks config and. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. The filter is the first stage. However, to bypass the filters, we are essentially only. Jinja2 Filter Bypass.
From itsourcecode.com
Attributeerror module 'jinja2' has no attribute 'contextfilter' Jinja2 Filter Bypass In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Leveraging the jina2 attr() filter and hex. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. To check the class in ssti jinja2 we can use payload { {. Jinja2 Filter Bypass.
From github.com
Jinja2 3.1 Breaks filter · Issue 77413 · ansible/ansible · GitHub Jinja2 Filter Bypass To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. The first filter looks config and. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Can anyone suggest ways i could bypass the restrictions on (and url encoding, hex encoding. Jinja2 Filter Bypass.
From github.com
GitHub mjuenema/ansiblefilterciscohash Ansible Jinja2 filters for Jinja2 Filter Bypass In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. The first filter looks config and. Leveraging the jina2 attr() filter and hex. However, to bypass the filters, we are essentially. Jinja2 Filter Bypass.
From stackoverflow.com
jinja2 Is there a way to connect filter box under 2 tabs in superset Jinja2 Filter Bypass However, to bypass the filters, we are essentially only using two strategies: In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? To check the class in ssti jinja2 we can use payload {. Jinja2 Filter Bypass.
From github.com
GitHub metworkframework/jinja2_shell_extension a jinja2 extension Jinja2 Filter Bypass The filter is the first stage. Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. In jinja2/flask it is possible to initialize variables for templates, and deliver payload parts through different methods (i.e.,. Is it getting filtered in the web app, a modification to the backend server. Jinja2 Filter Bypass.
From www.packetswitch.co.uk
Generating Cisco Interface Configurations with Jinja2 Template Jinja2 Filter Bypass To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if blacklisted?. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? Leveraging the jina2 attr() filter and hex. Generally, if there is a blacklist you can use request.args.param to retrieve the value. Jinja2 Filter Bypass.
From medium.com
Jinja2 SSTI filter bypasses. as you (should) know — blacklists are Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. The filter is the first stage. Leveraging the jina2 attr() filter and hex. However, to bypass the filters, we are essentially only using two strategies: To check the class in ssti jinja2 we can use payload { {. Jinja2 Filter Bypass.
From github.com
Jinja2 filter operator precedence is confusing · Issue 379 · pallets Jinja2 Filter Bypass Generally, if there is a blacklist you can use request.args.param to retrieve the value of a new param passed with the querystring. Is it getting filtered in the web app, a modification to the backend server running jinja2, python, etc.? To check the class in ssti jinja2 we can use payload { { ().__class__}} but how about using underscore if. Jinja2 Filter Bypass.