Kubernetes Privileged Pod Example . A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. The privileged policy is defined by an absence of restrictions. Security context settings include, but are not. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. What are the risks associated with overly permissive pod creation in kubernetes? Runasuser to specify the uid with which each container will run. If you define a pod where the privileged security policy applies, the. This can be achieved by setting the hostnetwork property in. The answer varies based on which of the host’s namespaces and security. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. A security context defines privilege and access control settings for a pod or container. Here are some of the settings which can be configured as part of kubernetes securitycontext field:
from medium.com
In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. Security context settings include, but are not. If you define a pod where the privileged security policy applies, the. A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. Runasuser to specify the uid with which each container will run. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. Here are some of the settings which can be configured as part of kubernetes securitycontext field: This can be achieved by setting the hostnetwork property in. What are the risks associated with overly permissive pod creation in kubernetes?
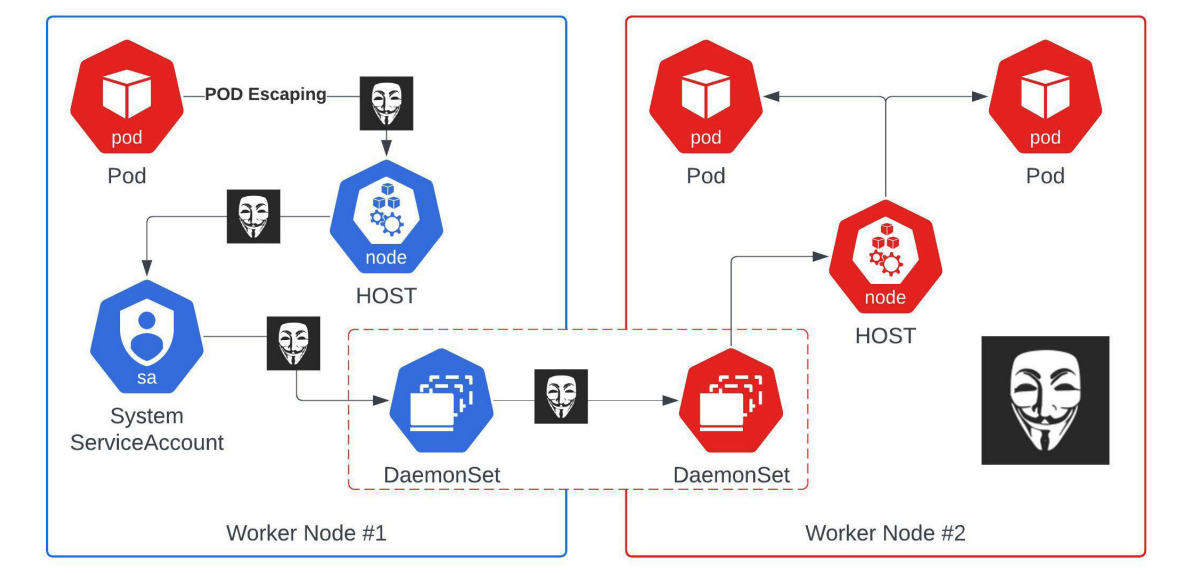
POD escaping privilege escalation by David Mosyan Medium
Kubernetes Privileged Pod Example For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. Runasuser to specify the uid with which each container will run. The privileged policy is defined by an absence of restrictions. The answer varies based on which of the host’s namespaces and security. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. If you define a pod where the privileged security policy applies, the. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. Security context settings include, but are not. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. Here are some of the settings which can be configured as part of kubernetes securitycontext field: This can be achieved by setting the hostnetwork property in. A security context defines privilege and access control settings for a pod or container. What are the risks associated with overly permissive pod creation in kubernetes?
From ronaknathani.com
How a Pod Gets an IP Address Ronak Nathani Kubernetes Privileged Pod Example Security context settings include, but are not. A security context defines privilege and access control settings for a pod or container. What are the risks associated with overly permissive pod creation in kubernetes? In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and. Kubernetes Privileged Pod Example.
From www.bestdevops.com
What is Pod in Explain 15 points with image as an example Kubernetes Privileged Pod Example If you define a pod where the privileged security policy applies, the. What are the risks associated with overly permissive pod creation in kubernetes? We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. The answer varies based on which of the host’s namespaces and security. A security. Kubernetes Privileged Pod Example.
From k21academy.com
for Beginners A Complete Beginners Guide (Updated) Kubernetes Privileged Pod Example This can be achieved by setting the hostnetwork property in. Security context settings include, but are not. Here are some of the settings which can be configured as part of kubernetes securitycontext field: A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. The privileged policy is. Kubernetes Privileged Pod Example.
From medium.com
Understanding networking pods Google Cloud Platform Kubernetes Privileged Pod Example The privileged policy is defined by an absence of restrictions. What are the risks associated with overly permissive pod creation in kubernetes? For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. The answer varies based on which of the host’s namespaces and security. If you define a pod where the. Kubernetes Privileged Pod Example.
From medium.com
POD escaping privilege escalation by David Mosyan Medium Kubernetes Privileged Pod Example For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. Here are some of the settings which can be configured as part of kubernetes securitycontext field: We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context. Kubernetes Privileged Pod Example.
From www.densify.com
The Guide to Affinity by Example Kubernetes Privileged Pod Example If you define a pod where the privileged security policy applies, the. Here are some of the settings which can be configured as part of kubernetes securitycontext field: Security context settings include, but are not. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context. Kubernetes Privileged Pod Example.
From devopscube.com
What Is Pod? Explained With Practical Examples Kubernetes Privileged Pod Example Security context settings include, but are not. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. What are the risks associated with overly permissive pod creation in kubernetes? A security context defines privilege and access control settings for a pod or container. A security context is used to define different. Kubernetes Privileged Pod Example.
From www.golinuxcloud.com
Privileged Pod Practical Examples GoLinuxCloud Kubernetes Privileged Pod Example The answer varies based on which of the host’s namespaces and security. The privileged policy is defined by an absence of restrictions. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. What are the risks associated with overly permissive pod creation in kubernetes? In kubernetes, using dac implies that you,. Kubernetes Privileged Pod Example.
From matthewpalmer.net
Deployment Tutorial with YAML Book Kubernetes Privileged Pod Example The answer varies based on which of the host’s namespaces and security. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. Runasuser to specify the uid with which each container will run. For example, a pod may need to use the node’s network adapters instead of its. Kubernetes Privileged Pod Example.
From blog.kubesimplify.com
Understanding the Architecture of A Beginner's Guide Kubernetes Privileged Pod Example A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. Security context settings include, but are not. If you define a pod where the privileged security policy applies, the. Here are some of the settings which can be configured as part of kubernetes securitycontext field: We explore. Kubernetes Privileged Pod Example.
From www.opsmx.com
What is Images, Containers and Pods Explained Kubernetes Privileged Pod Example We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. The privileged policy is defined by an absence of restrictions. What are the risks associated with overly permissive pod creation in kubernetes? Here are some of the settings which can be configured as part of kubernetes securitycontext field:. Kubernetes Privileged Pod Example.
From cast.ai
Load Balancer Expert Guide With Examples CAST AI Kubernetes Privileged Pod Example What are the risks associated with overly permissive pod creation in kubernetes? A security context defines privilege and access control settings for a pod or container. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context is used to define different privilege and access level. Kubernetes Privileged Pod Example.
From howtoconfigure.blogspot.com
Example of ConfigMap, Secret and Volume in pod on Kubernetes Privileged Pod Example This can be achieved by setting the hostnetwork property in. A security context defines privilege and access control settings for a pod or container. What are the risks associated with overly permissive pod creation in kubernetes? In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in. Kubernetes Privileged Pod Example.
From www.akeyless.io
Better Protect Your Secrets and Privileged Access Akeyless Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. The answer varies based on which of the host’s namespaces and security. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context is used to define different privilege and access level control settings for. Kubernetes Privileged Pod Example.
From medium.com
Understanding networking pods Google Cloud Platform Kubernetes Privileged Pod Example In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. The privileged policy is defined by an absence of restrictions. Here are some of the settings which can be configured as part of kubernetes securitycontext field: The answer varies based on which. Kubernetes Privileged Pod Example.
From www.starwindsoftware.com
How Storage Works in a Container Cluster Kubernetes Privileged Pod Example The privileged policy is defined by an absence of restrictions. Here are some of the settings which can be configured as part of kubernetes securitycontext field: Runasuser to specify the uid with which each container will run. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A. Kubernetes Privileged Pod Example.
From ostechnix.com
Create And Manage Pods In Linux OSTechNix Kubernetes Privileged Pod Example The answer varies based on which of the host’s namespaces and security. If you define a pod where the privileged security policy applies, the. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context is used to define different privilege and access level control settings. Kubernetes Privileged Pod Example.
From devops4solutions.com
Pods explained with examples DevOps4Solutions Kubernetes Privileged Pod Example If you define a pod where the privileged security policy applies, the. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. Security context settings include, but are not. A security context is used to define different privilege and access level control settings for any pod or container. Kubernetes Privileged Pod Example.
From www.densify.com
The Guide to Affinity by Example Kubernetes Privileged Pod Example The privileged policy is defined by an absence of restrictions. Runasuser to specify the uid with which each container will run. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. What are the risks associated with overly permissive pod creation in kubernetes? Security context settings include, but are not. The. Kubernetes Privileged Pod Example.
From release.com
Pods Advanced Concepts Explained — Release Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. What are the risks associated with overly permissive pod creation in kubernetes? If you define a pod where the privileged security. Kubernetes Privileged Pod Example.
From twitter.com
K3sDaily on Twitter "This repo covers objects' and Kubernetes Privileged Pod Example A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. A security context defines privilege and access control settings for a pod or container. The privileged policy is defined by an absence of restrictions. The answer varies based on which of the host’s namespaces and security. Runasuser. Kubernetes Privileged Pod Example.
From blog.devops.dev
Security Context — Capabilities explained. by Sagar Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. The answer varies based on which of the host’s namespaces and security. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. What are the risks associated with overly permissive pod creation in kubernetes? This can be achieved by setting. Kubernetes Privileged Pod Example.
From www.densify.com
The Guide to Affinity by Example Kubernetes Privileged Pod Example The privileged policy is defined by an absence of restrictions. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context defines privilege and access control settings. Kubernetes Privileged Pod Example.
From belowthemalt.com
Cluster & Process Flow of a POD creation Blogs, Ideas Kubernetes Privileged Pod Example The answer varies based on which of the host’s namespaces and security. A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. Here are some. Kubernetes Privileged Pod Example.
From www.devopsschool.com
Tutorials List of Components of Kubernetes Privileged Pod Example Security context settings include, but are not. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. Runasuser to specify the uid with which each container will run. A security context is used to define different privilege and access level control settings. Kubernetes Privileged Pod Example.
From k21academy.com
Deployment A demo of K8s Deployment Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. A security context defines privilege and access control settings for a pod or container. The answer varies based on which of the host’s namespaces and security. Security context settings include, but are not. A security context is used to define different privilege and access level control settings for any. Kubernetes Privileged Pod Example.
From coderise.io
How establishes communication between Pods CodeRise Kubernetes Privileged Pod Example If you define a pod where the privileged security policy applies, the. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. Security context settings include, but are not. What are the risks associated with overly permissive pod creation in kubernetes? A security context defines privilege and access control settings for. Kubernetes Privileged Pod Example.
From www.wallarm.com
What is a pod? ⚙️ Lifecycle Explanation Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security by adjusting operating system security settings. A security context defines privilege and access control settings for a pod or container. Here are some of the settings which can be configured as part of. Kubernetes Privileged Pod Example.
From dzone.com
Cluster Setup on Ubuntu, Explained DZone Kubernetes Privileged Pod Example A security context defines privilege and access control settings for a pod or container. A security context is used to define different privilege and access level control settings for any pod or container running inside the pod. Security context settings include, but are not. We explore a security mechanism in kubernetes known as securitycontext, which enhances container and pod security. Kubernetes Privileged Pod Example.
From www.armosec.io
4 Attack Chains and How to Break Them Kubernetes Privileged Pod Example For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. Security context settings include, but are not. The privileged policy is defined by. Kubernetes Privileged Pod Example.
From www.devopsschool.com
Tutorials What is Preemption in with example Kubernetes Privileged Pod Example What are the risks associated with overly permissive pod creation in kubernetes? Security context settings include, but are not. This can be achieved by setting the hostnetwork property in. In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. The answer varies. Kubernetes Privileged Pod Example.
From blog.kubecost.com
node affinity examples & instructions Kubecost Blog Kubernetes Privileged Pod Example If you define a pod where the privileged security policy applies, the. What are the risks associated with overly permissive pod creation in kubernetes? A security context defines privilege and access control settings for a pod or container. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. A security context. Kubernetes Privileged Pod Example.
From codeblog.dotsandbrackets.com
Dissecting example Dots and Brackets Code Blog Kubernetes Privileged Pod Example In kubernetes, using dac implies that you, as a user or administrator, can set access and permission constraints on files and processes running in your pods and containers. The privileged policy is defined by an absence of restrictions. Security context settings include, but are not. Here are some of the settings which can be configured as part of kubernetes securitycontext. Kubernetes Privileged Pod Example.
From www.advantagecomputers.com
Privileged pod escalations in and GKE Advantage Computers NJ Kubernetes Privileged Pod Example Runasuser to specify the uid with which each container will run. Here are some of the settings which can be configured as part of kubernetes securitycontext field: The privileged policy is defined by an absence of restrictions. Security context settings include, but are not. If you define a pod where the privileged security policy applies, the. This can be achieved. Kubernetes Privileged Pod Example.
From itnext.io
An illustrated guide to Networking [Part 2] Kubernetes Privileged Pod Example Security context settings include, but are not. Runasuser to specify the uid with which each container will run. The privileged policy is defined by an absence of restrictions. For example, a pod may need to use the node’s network adapters instead of its own virtual network adapters. A security context defines privilege and access control settings for a pod or. Kubernetes Privileged Pod Example.