Apple Keychain Vulnerability . University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Apple patched the flaw that keysteal was exploiting at the end of. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. It sounds like you’re noticing your passwords stored in keychain being vulnerable.
from www.forensicfocus.com
The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. It sounds like you’re noticing your passwords stored in keychain being vulnerable.
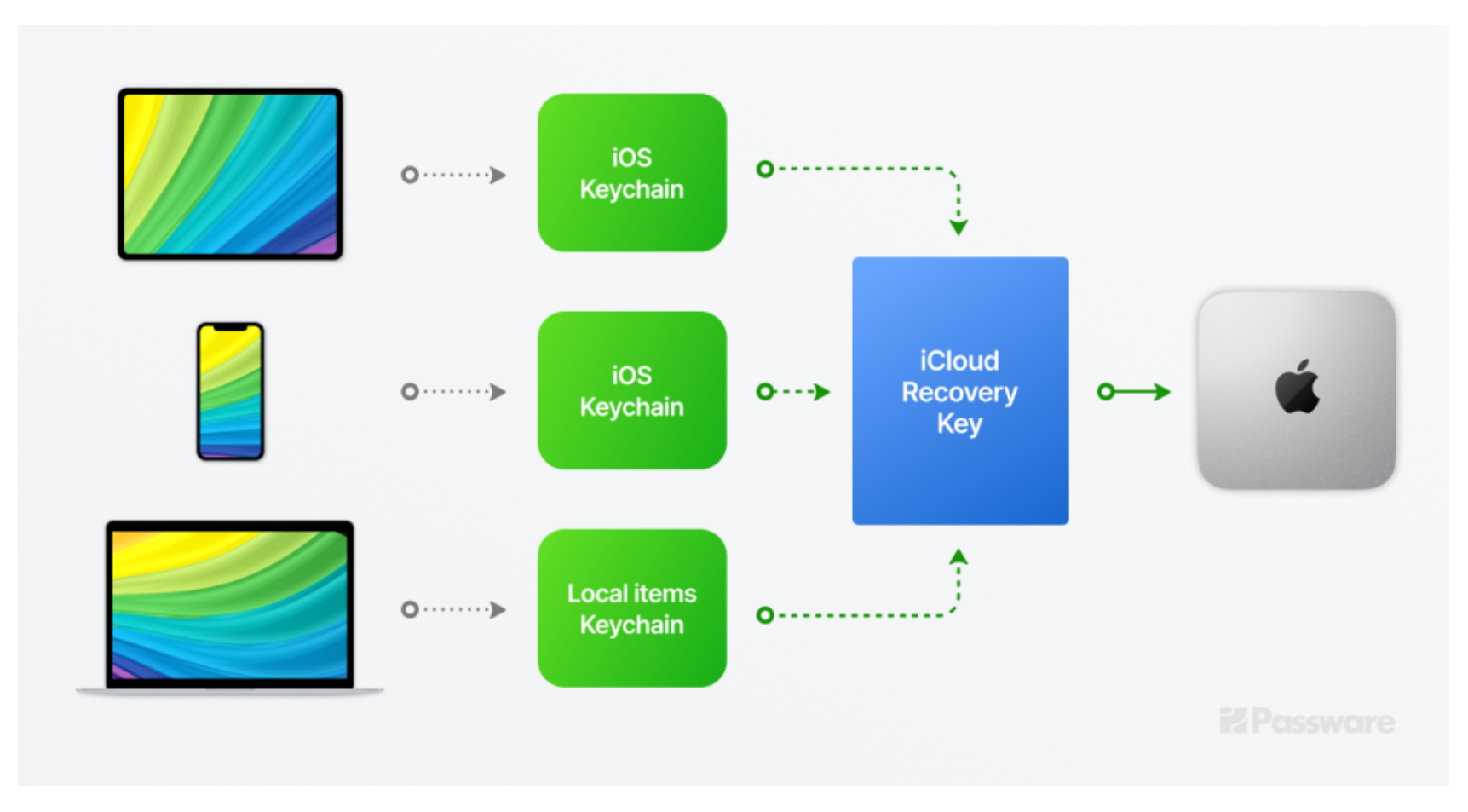
A Deep Dive into Apple Keychain Decryption Forensic Focus
Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. It sounds like you’re noticing your passwords stored in keychain being vulnerable. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption.
From www.imore.com
Apple mitigates macOS Keychain vulnerability iMore Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. It sounds like you’re. Apple Keychain Vulnerability.
From support.apple.com
Set up iCloud Keychain Apple Support Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. It sounds like you’re. Apple Keychain Vulnerability.
From www.forensicfocus.com
A Deep Dive into Apple Keychain Decryption Forensic Focus Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Apple patched the flaw that keysteal was exploiting at the end of. It sounds like you’re noticing your passwords stored in keychain being vulnerable. The triangledb implant used to target apple ios devices packs in at least four different modules. Apple Keychain Vulnerability.
From bettavr.weebly.com
Mac keychain access vulnerability bettavr Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Apple patched the flaw that keysteal was exploiting at the end of. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios. Apple Keychain Vulnerability.
From gomath.ch
Apple Corrige une Grave Vulnérabilité de Sécurité Apple Apple Keychain Vulnerability Icloud keychain is a great way to manage your. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw that keysteal was exploiting at the end of. University researchers have found an unpatchable security. Apple Keychain Vulnerability.
From www.aiseesoft.com
Verified Solutions to Fix the Issue of Keychain Not Working on iPhone Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an. Apple Keychain Vulnerability.
From www.cybercureme.com
Vulnerability in Apple iMessage Let Hackers Remotely Read Files in Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract. Apple Keychain Vulnerability.
From siliconangle.com
Researcher details macOS vulnerability but refuses to share information Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. It sounds like you’re. Apple Keychain Vulnerability.
From securityaffairs.co
iCloud Keychain vulnerability allowed hackers to Steal sensitive data Apple Keychain Vulnerability Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps,. Apple Keychain Vulnerability.
From mashable.com
How to set up Keychain Access in macOS to keep your passwords safe Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw. Apple Keychain Vulnerability.
From www.artofit.org
Apple devices threatened by keychain vulnerability Artofit Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Icloud keychain is a great way to manage your. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow. Apple Keychain Vulnerability.
From blog.passware.com
A Deep Dive into Apple Keychain Decryption Passware Blog Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. It sounds like you’re noticing your passwords stored. Apple Keychain Vulnerability.
From bettavr.weebly.com
Mac keychain access vulnerability bettavr Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. Dubbed keysteal, the. Apple Keychain Vulnerability.
From bettavr.weebly.com
Mac keychain access vulnerability bettavr Apple Keychain Vulnerability It sounds like you’re noticing your passwords stored in keychain being vulnerable. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Icloud keychain is a great way to manage your. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break. Apple Keychain Vulnerability.
From punchbetta.weebly.com
Mac keychain access vulnerability punchbetta Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. It sounds like. Apple Keychain Vulnerability.
From punchbetta.weebly.com
Mac keychain access vulnerability punchbetta Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Apple patched the flaw that keysteal was exploiting at the end of. Dubbed keysteal, the attack called attention to the fact that the macos. Apple Keychain Vulnerability.
From www.intego.com
Mac and iOS Keychain Tutorial How Apple’s iCloud Keychain Works The Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple ios. Apple Keychain Vulnerability.
From www.malwarebytes.com
Keychain vulnerability in macOS Malwarebytes Labs Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple. Apple Keychain Vulnerability.
From blog.passware.com
A Deep Dive into Apple Keychain Decryption Passware Blog Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Apple patched the flaw that keysteal was exploiting at the end of. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very. Apple Keychain Vulnerability.
From sensorstechforum.com
CVE202423204 Vulnerability in Apple's Shortcuts App Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. University researchers have found. Apple Keychain Vulnerability.
From www.iphoneincanada.ca
macOS High Sierra Vulnerability Allows ThirdParty Apps to Access Apple Keychain Vulnerability It sounds like you’re noticing your passwords stored in keychain being vulnerable. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used. Apple Keychain Vulnerability.
From www.intego.com
Mac and iOS Keychain Tutorial How Apple's iCloud Keychain Works The Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. It sounds like you’re noticing your passwords stored in keychain being vulnerable. University researchers have found an unpatchable security. Apple Keychain Vulnerability.
From blogs.manageengine.com
Are your Apple devices safe from the latest vulnerabilities Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw. Apple Keychain Vulnerability.
From www.youtube.com
brokenChain Mac OSX Keychain Vulnerability YouTube Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for. Apple Keychain Vulnerability.
From support.apple.com
Keychain Access User Guide for Mac Apple Support Apple Keychain Vulnerability Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. It sounds like you’re noticing your passwords stored in keychain being vulnerable. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone,. Apple Keychain Vulnerability.
From www.planet-it.net
Apple software Critical Kit Vulnerability CVE202337450 Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Dubbed keysteal, the. Apple Keychain Vulnerability.
From www.intego.com
Mac and iOS Keychain Tutorial How Apple's iCloud Keychain Works The Apple Keychain Vulnerability University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. Apple patched the flaw. Apple Keychain Vulnerability.
From www.macrumors.com
macOS High Sierra Vulnerability Allegedly Allows Malicious ThirdParty Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. It sounds like you’re noticing your passwords stored in keychain being vulnerable. University researchers have found an unpatchable security. Apple Keychain Vulnerability.
From meterpreter.org
Researcher discovered the macOS keychain vulnerability decided to Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw that keysteal was exploiting at the end of. Icloud keychain is a great way to manage your. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone,. Apple Keychain Vulnerability.
From 9to5mac.com
Major macOS (incl. High Sierra) Keychain password extraction Apple Keychain Vulnerability Icloud keychain is a great way to manage your. It sounds like you’re noticing your passwords stored in keychain being vulnerable. Apple patched the flaw that keysteal was exploiting at the end of. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Dubbed keysteal, the attack called attention to. Apple Keychain Vulnerability.
From www.lifehacker.com.au
Apple Updates macOS High Sierra To Counter Keychain Vulnerability Apple Keychain Vulnerability Apple patched the flaw that keysteal was exploiting at the end of. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. It sounds like you’re noticing your passwords stored in keychain being vulnerable. The triangledb implant used to target apple ios devices packs in at least four different modules. Apple Keychain Vulnerability.
From www.malwarebytes.com
Keychain vulnerability in macOS Malwarebytes Labs Apple Keychain Vulnerability It sounds like you’re noticing your passwords stored in keychain being vulnerable. Icloud keychain is a great way to manage your. Apple patched the flaw that keysteal was exploiting at the end of. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. The triangledb implant used to target apple. Apple Keychain Vulnerability.
From www.groovypost.com
Apple Keychain Overview What it is and Why You Should Use it Apple Keychain Vulnerability Icloud keychain is a great way to manage your. Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. Apple patched the flaw that keysteal was exploiting at the end of. The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone,. Apple Keychain Vulnerability.
From www.bralin.com
Keychain Makes Mac Users Vulnerable Protect Your Personal Information Apple Keychain Vulnerability Dubbed keysteal, the attack called attention to the fact that the macos keychain makes a very attractive target for hackers. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Apple patched the flaw that keysteal was exploiting at the end of. The triangledb implant used to target apple ios. Apple Keychain Vulnerability.
From www.artofit.org
Apple devices threatened by keychain vulnerability Artofit Apple Keychain Vulnerability The triangledb implant used to target apple ios devices packs in at least four different modules to record microphone, extract icloud keychain, steal data from sqlite databases used by various apps, and estimate the victim's location. University researchers have found an unpatchable security flaw in apple silicon macs, which would allow an attacker to break encryption. Dubbed keysteal, the attack. Apple Keychain Vulnerability.