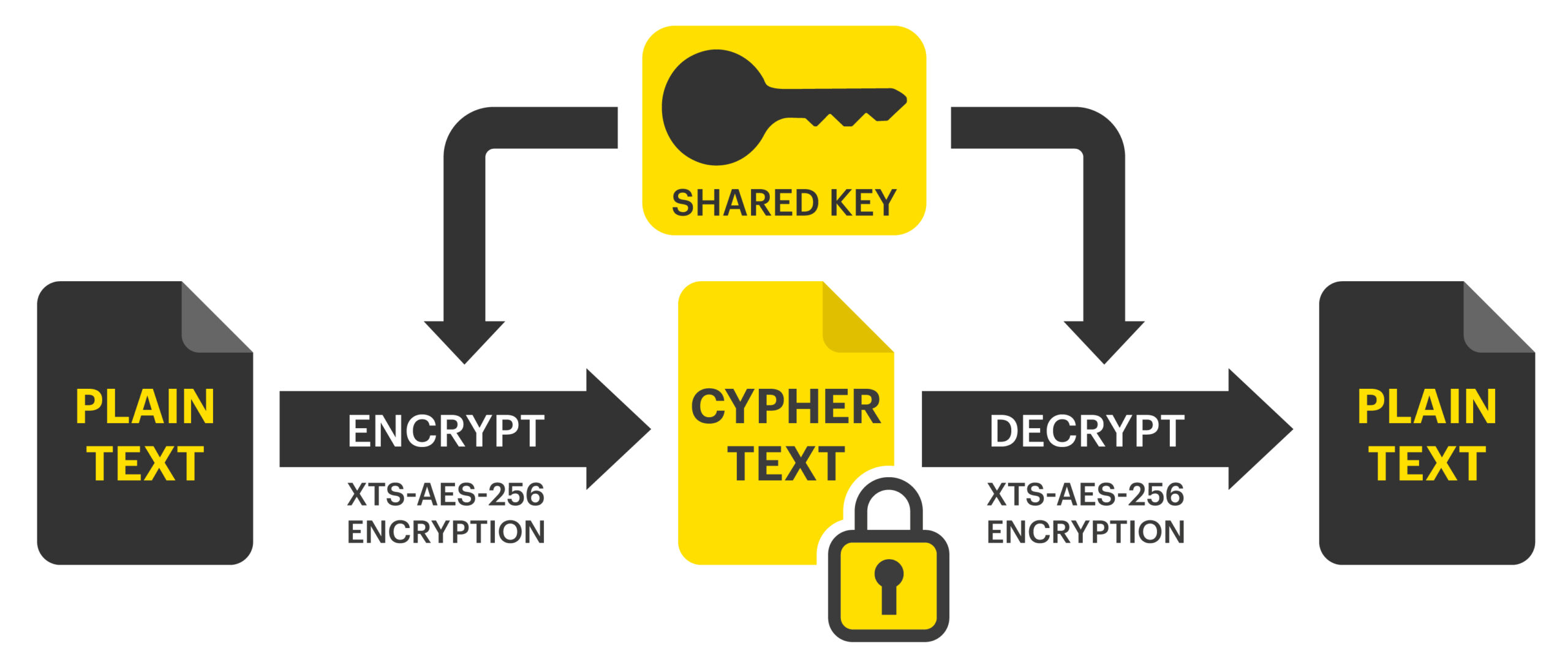
Encryption Data Key . Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. The public key can be shared openly, while the private key must remain secret. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. The following is the generatedatakey request. This kek is then used to encrypt what they call the. Data encrypted with the public key can only be. Microsoft generates a key encryption key using the user's password. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Deks also can be master keys.
from stormagic.com
Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encrypted with the public key can only be. The following is the generatedatakey request. This kek is then used to encrypt what they call the. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Deks also can be master keys. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. The public key can be shared openly, while the private key must remain secret. Microsoft generates a key encryption key using the user's password.
Encryption A Beginner's Guide Start Learning with StorMagic
Encryption Data Key Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Data encrypted with the public key can only be. This kek is then used to encrypt what they call the. The following is the generatedatakey request. Deks also can be master keys. Microsoft generates a key encryption key using the user's password. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. The public key can be shared openly, while the private key must remain secret.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta Encryption Data Key Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Deks also can be master keys. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. The public key can be shared openly, while the private key must remain secret. The following is the generatedatakey. Encryption Data Key.
From subscription.packtpub.com
Serverside encryption with KMSmanaged keys (SSEKMS) AWS Certified Security Specialty Exam Encryption Data Key Microsoft generates a key encryption key using the user's password. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. The following is the generatedatakey request. Data encrypted with the public key can only be. This kek is then used to encrypt what they call the. The public key can be shared. Encryption Data Key.
From ico.org.uk
Types of encryption ICO Encryption Data Key Microsoft generates a key encryption key using the user's password. Deks also can be master keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Data encrypted with the public key can only be. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your. Encryption Data Key.
From research.aimultiple.com
Encryption Key Management Benefits, Tools & Best Practices in 2024 Encryption Data Key Microsoft generates a key encryption key using the user's password. This kek is then used to encrypt what they call the. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encrypted with the public key can only be. Data encryption keys (deks) — these keys enable you to encrypt data at rest. Encryption Data Key.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Encryption Data Key Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Deks also can be master keys. This kek is then used to encrypt what they call the. The public key can be shared openly, while the private key must remain secret. Encryption restricts access to sensitive data to only the users that have. Encryption Data Key.
From www.assured.enterprises
data encryption key graphic big Assured Enterprises Serious Cybersecurity™ Encryption Data Key Microsoft generates a key encryption key using the user's password. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Data encrypted with the public key can only be. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption restricts access to sensitive. Encryption Data Key.
From medium.com
Securing Encryption Keys in the Cloud Part 1 (AWS KMS) by Thando Toto Medium Encryption Data Key Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encrypted with the public key can only be. The following is the generatedatakey request. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Data encryption is a method of preserving data confidentiality by transforming it. Encryption Data Key.
From brightlineit.com
Understanding Encryption Key Management for Businesses Brightline Technologies Encryption Data Key Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Microsoft generates a key encryption key using the user's password. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. The following is the generatedatakey request. Encryption keys represent a data variable used to control. Encryption Data Key.
From www.encryptionconsulting.com
What is the difference between Encryption and Tokenization? Which is better for data security Encryption Data Key Data encrypted with the public key can only be. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. The following is the generatedatakey request. The public key can be shared openly, while the private key. Encryption Data Key.
From www.springboard.com
Cryptography Basics Ins and Outs of Encryption Encryption Data Key Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. The public key can be shared openly, while the private key must remain secret. Data encrypted with the public key can only be. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Microsoft generates a key. Encryption Data Key.
From atos.net
Protecting your sensitive data with double key encryption Atos Encryption Data Key This kek is then used to encrypt what they call the. Data encrypted with the public key can only be. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. The following is the generatedatakey. Encryption Data Key.
From www.thesslstore.com
Cryptographic Keys 101 What They Are & How They Secure Data Hashed Out by The SSL Store™ Encryption Data Key Microsoft generates a key encryption key using the user's password. Data encrypted with the public key can only be. The following is the generatedatakey request. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. This kek is then used to encrypt what they call the. Deks also can be master. Encryption Data Key.
From www.alamy.com
Data encryption key lock Stock Photo Alamy Encryption Data Key Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. The public key can be shared openly, while the private key must remain secret. Data encrypted with the public key can only be. The following is the. Encryption Data Key.
From www.virtru.com
Why Hosting Your Own Encryption Keys is Better for Data Security Encryption Data Key The public key can be shared openly, while the private key must remain secret. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. The following is the generatedatakey request. This kek is then used to encrypt what they call the. Microsoft generates a key encryption key using the user's password. Encryption. Encryption Data Key.
From eduinput.com
Data Encryption in the Cloud Types, Examples, and Software Encryption Data Key Microsoft generates a key encryption key using the user's password. The following is the generatedatakey request. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption is a method of preserving data confidentiality by transforming. Encryption Data Key.
From wickr.com
5 Data Encryption Best Practices AWS Wickr Encryption Data Key Deks also can be master keys. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. This kek is then used to encrypt what they call the. The public key can be shared openly, while the private key must remain secret. Data encrypted with the public key can only be. Data encryption. Encryption Data Key.
From www.poweradmin.com
A Quick Guide to Encrypted Messaging Network Wrangler Tech Blog Encryption Data Key Microsoft generates a key encryption key using the user's password. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encrypted with the public key can only be. The following is the generatedatakey request. The. Encryption Data Key.
From www.freecodecamp.org
How to Manage Encryption at Scale with Envelope Encryption & Key Management Systems Encryption Data Key This kek is then used to encrypt what they call the. The public key can be shared openly, while the private key must remain secret. Deks also can be master keys. Data encrypted with the public key can only be. The following is the generatedatakey request. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext,. Encryption Data Key.
From securityboulevard.com
12 Enterprise Encryption Key Management Best Practices Security Boulevard Encryption Data Key Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. This kek is then used to encrypt what they call the. Microsoft generates a key encryption key using the user's password. Data encrypted with the public. Encryption Data Key.
From 7t.co
Data Security Strategy The Different Types of Encryption Encryption Data Key Deks also can be master keys. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Data. Encryption Data Key.
From securityintelligence.com
What You Need to Know About Data Encryption Right Now Encryption Data Key Deks also can be master keys. The following is the generatedatakey request. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. This kek is then used to encrypt what they call the. The public key can be shared openly, while the private key must remain secret. Encryption restricts access to. Encryption Data Key.
From jayendrapatil.com
AWS S3 Encryption Encryption Data Key The following is the generatedatakey request. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. The public key can be shared openly, while the private key must remain secret. Data encryption is a method of preserving. Encryption Data Key.
From www.dreamstime.com
Encryption key stock photo. Image of document, encryption 8467680 Encryption Data Key The public key can be shared openly, while the private key must remain secret. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Microsoft generates a key encryption key using the user's password. The. Encryption Data Key.
From eduinput.com
Data Encryption in the Cloud Types, Examples, and Software Encryption Data Key Data encrypted with the public key can only be. Deks also can be master keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. The following is the generatedatakey request. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. This kek is. Encryption Data Key.
From www.bitdefender.com
What is Data Encryption? Bitdefender Cyberpedia Encryption Data Key Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Deks also can be master keys. Data encryption is. Encryption Data Key.
From docs.snowflake.com
Understanding Encryption Key Management in Snowflake Snowflake Documentation Encryption Data Key Data encrypted with the public key can only be. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Microsoft generates a key encryption key using the user's password. The public key can be shared openly, while the private key must remain secret. This kek is then used to encrypt what they. Encryption Data Key.
From www.newsoftwares.net
Encrypting Data In Windows A Comprehensive Guide To Using BitLocker And EFS Blog Encryption Data Key This kek is then used to encrypt what they call the. The following is the generatedatakey request. The public key can be shared openly, while the private key must remain secret. Deks also can be master keys. Microsoft generates a key encryption key using the user's password. Encryption keys represent a data variable used to control how an algorithm processes. Encryption Data Key.
From www.cloudflare.com
What Is a Cryptographic Key? Keys and SSL Encryption Cloudflare Encryption Data Key Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. This kek is then used to encrypt what they call the. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Data encryption keys (deks) — these keys enable you to encrypt data. Encryption Data Key.
From www.proofpoint.com
What Is Encryption? Definition, Types & More Proofpoint US Encryption Data Key Deks also can be master keys. Microsoft generates a key encryption key using the user's password. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Data encryption is a method of preserving data confidentiality. Encryption Data Key.
From stormagic.com
Encryption A Beginner's Guide Start Learning with StorMagic Encryption Data Key Deks also can be master keys. The public key can be shared openly, while the private key must remain secret. Microsoft generates a key encryption key using the user's password. Data encrypted with the public key can only be. This kek is then used to encrypt what they call the. Data encryption is a method of preserving data confidentiality by. Encryption Data Key.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Encryption Data Key Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Data encrypted with the public key can only be. Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back. Data encryption keys (deks) — these keys enable you to encrypt data at rest. Encryption Data Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Encryption Data Key Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be decoded. Deks also can be master keys. Data encrypted with the public key can only be. This kek is then used to encrypt what they call the. Microsoft generates a key encryption key using the user's password. Encryption restricts access to sensitive. Encryption Data Key.
From www.imperva.com
Four levels of data encryption Encryption Data Key Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Data encrypted with the public key can only be. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Data encryption is a method of preserving data confidentiality by transforming it into ciphertext, which can only be. Encryption Data Key.
From aws.amazon.com
Encrypt global data clientside with AWS KMS multiRegion keys AWS Security Blog Encryption Data Key This kek is then used to encrypt what they call the. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. The following is the generatedatakey request. Encryption restricts access to sensitive data to only the users that have the appropriate decryption keys. Deks also can be master keys. Data encrypted with the. Encryption Data Key.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Encryption Data Key Data encrypted with the public key can only be. Deks also can be master keys. Data encryption keys (deks) — these keys enable you to encrypt data at rest on your server. Microsoft generates a key encryption key using the user's password. The following is the generatedatakey request. This kek is then used to encrypt what they call the. The. Encryption Data Key.