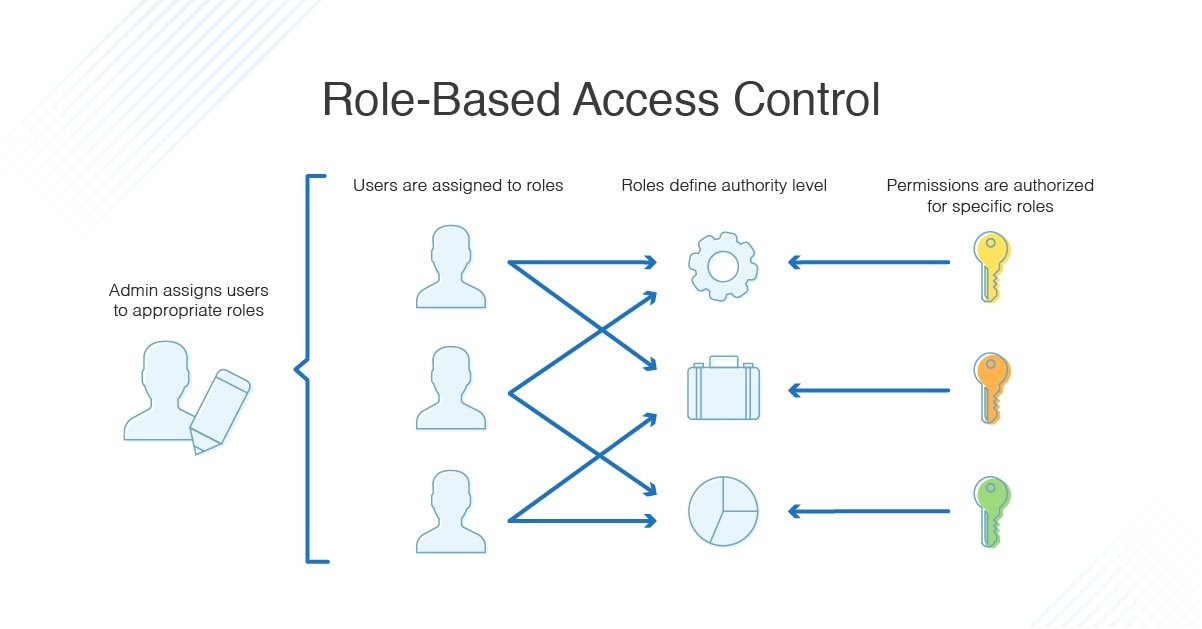
Security Policy Based Access Control . Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies.
from www.dnsstuff.com
Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies.
RBAC vs. ABAC Access Control What’s the Difference? DNSstuff
Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac.
From www.idenhaus.com
What is Policy Based Access Control (PBAC)? Security Policy Based Access Control Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.resmo.com
9 Access Control Best Practices Resmo Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.dnsstuff.com
RBAC vs. ABAC Access Control What’s the Difference? DNSstuff Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.educba.com
Security Policies List of 6 Most Useful Security Policies Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From www.nedapsecurity.com
How to establish an effective physical access control policy Nedap Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From learn.microsoft.com
Overview of Microsoft Entra rolebased access control (RBAC Security Policy Based Access Control Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.dnsstuff.com
RBAC vs. ABAC Access Control What’s the Difference? DNSstuff Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Security Policy Based Access Control.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.securityinfowatch.com
AlertEnterprise PolicyBased Access Control software Security Info Watch Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.nextlabs.com
What is PolicyBased Access Control (PBAC)? NextLabs Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.strongdm.com
What is PolicyBased Access Control (PBAC)? Definition StrongDM Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Security Policy Based Access Control.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] Security Policy Based Access Control Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From learn.microsoft.com
What is Azure rolebased access control (Azure RBAC)? Microsoft Learn Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From cyberhoot.com
Access Control Mechanism CyberHoot Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From www.slideserve.com
PPT Computer Security Principles and Practice PowerPoint Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Security Policy Based Access Control.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.upguard.com
What is RoleBased Access Control (RBAC)? Examples, Benefits, and More Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From www.slideserve.com
PPT Security Policies and Access Control PowerPoint Presentation Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID1691314 Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.slideserve.com
PPT Access Control and Operating System Security PowerPoint Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From blog.plainid.com
Policy Based Access Control 5 Key Features Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From www.researchgate.net
Format of a Role Based Access Control Policy Download Scientific Diagram Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From cie-group.com
How to design an Access Control system Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From axiomatics.com
Intro to Attribute Based Access Control (ABAC) Axiomatics Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.axiomatics.com
Guide to AttributeBased Access Control (ABAC) Axiomatics Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download Security Policy Based Access Control Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From axiomatics.com
What is Policy Based Access Control (PBAC)? Axiomatics Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Security Policy Based Access Control.
From www.researchgate.net
The current policybased access control process Download Scientific Security Policy Based Access Control Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.
From securityboulevard.com
The Power of PolicyBased Access Governance Security Boulevard Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From amplication.com
The Right Type of Access Control RBAC, PBAC or PBAC Amplication Security Policy Based Access Control Key components and elements of pbac. Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Security Policy Based Access Control.
From www.researchgate.net
An architecture for policybased access control. Download Scientific Security Policy Based Access Control Rules determine user access based on the individual’s role or attributes/characteristics. Access to network resources is documented and controlled via written policies. Key components and elements of pbac. Security Policy Based Access Control.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu Security Policy Based Access Control Key components and elements of pbac. Access to network resources is documented and controlled via written policies. Rules determine user access based on the individual’s role or attributes/characteristics. Security Policy Based Access Control.