Receivers Public Key . If the decrypted data matches original message, it. Rsa algorithm is an asymmetric cryptography algorithm. Asymmetric means that it works on two different keys i.e. The receiver will verify by decrypting the encrypted data with your public key. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Receiver sends public key while keeping the matching private key secret. Is public key encryption better? The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Session key is encrypted using receivers pubic key.
from www.infosec.gov.hk
The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Session key is encrypted using receivers pubic key. Receiver sends public key while keeping the matching private key secret. Asymmetric means that it works on two different keys i.e. The receiver will verify by decrypting the encrypted data with your public key. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Is public key encryption better? At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Rsa algorithm is an asymmetric cryptography algorithm.
InfoSec Public Key Infrastructure
Receivers Public Key Rsa algorithm is an asymmetric cryptography algorithm. The receiver will verify by decrypting the encrypted data with your public key. If the decrypted data matches original message, it. Session key is encrypted using receivers pubic key. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Asymmetric means that it works on two different keys i.e. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Receiver sends public key while keeping the matching private key secret. Rsa algorithm is an asymmetric cryptography algorithm. Is public key encryption better?
From www.codingninjas.com
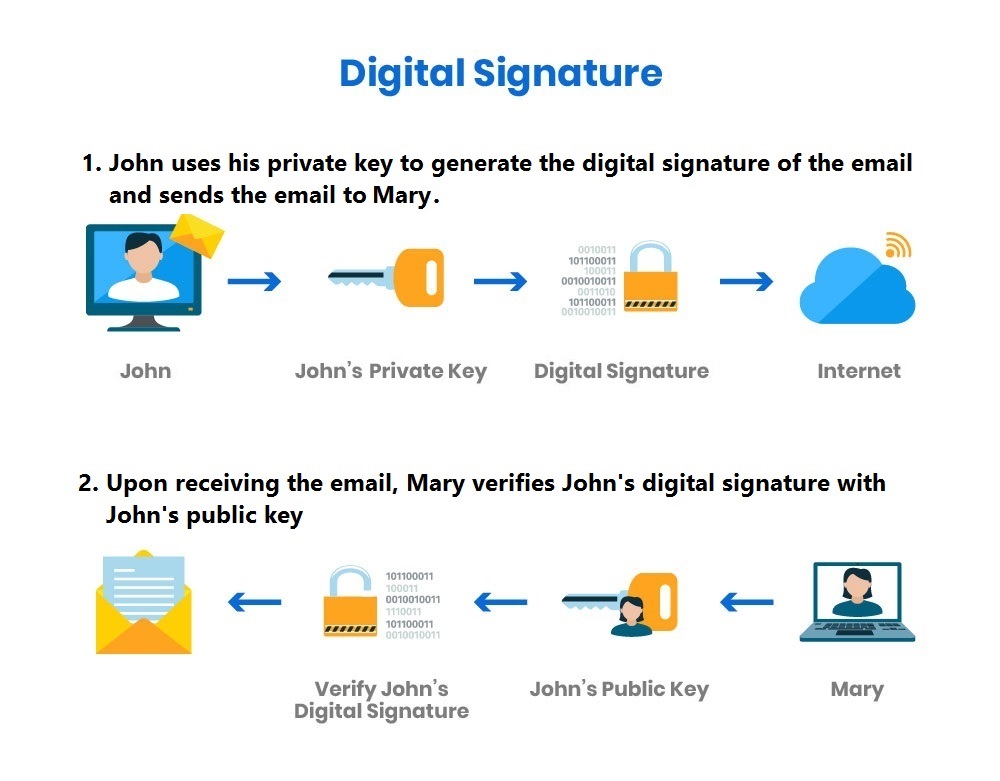
Cryptography Digital Signature Coding Ninjas Receivers Public Key The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Receiver sends public key while keeping the matching private key secret. Public key cryptography is a. Receivers Public Key.
From www.clickssl.net
What is Public Key Encryption and How Does It Works? Receivers Public Key Rsa algorithm is an asymmetric cryptography algorithm. Is public key encryption better? Receiver sends public key while keeping the matching private key secret. The receiver will verify by decrypting the encrypted data with your public key. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt. Receivers Public Key.
From www.securew2.com
What is a PKI (Public Key Infrastructure)? 2023 Update Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Is public key encryption better? Session key is encrypted using receivers pubic key. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s. Receivers Public Key.
From www.slideserve.com
PPT Network Security Protocols PowerPoint Presentation, free download Receivers Public Key Rsa algorithm is an asymmetric cryptography algorithm. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Is public key encryption better? The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. The receiver will verify by. Receivers Public Key.
From slideplayer.com
刘振 上海交通大学 计算机科学与工程系 电信群楼 ppt download Receivers Public Key Asymmetric means that it works on two different keys i.e. Receiver sends public key while keeping the matching private key secret. Rsa algorithm is an asymmetric cryptography algorithm. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. At a high level, pke between a sender and receiver is a. Receivers Public Key.
From present5.com
Public Key Infrastructure A Quick Look Inside PKI Receivers Public Key The receiver will verify by decrypting the encrypted data with your public key. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Rsa algorithm is an asymmetric cryptography algorithm. Is public key encryption better? The receiver sends the public key on the same channel as the one it intends. Receivers Public Key.
From www.flowbank.com
What is a Crypto Key? Public & Private Keys Receivers Public Key Rsa algorithm is an asymmetric cryptography algorithm. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Asymmetric means that it works on two different keys i.e. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to. Receivers Public Key.
From www.chegg.com
Solved 1. If a symmetric key is encrypted with a receiver's Receivers Public Key Asymmetric means that it works on two different keys i.e. Is public key encryption better? Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. The receiver sends the public key on the same channel as the one it intends to receive. Receivers Public Key.
From sectigo.com
Public Key vs Private Key Public Key Cryptography Explained Sectigo Receivers Public Key The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. At a high level, pke between a sender and receiver is a protocol for encrypting messages under. Receivers Public Key.
From www.slideserve.com
PPT Public Key Cryptography PowerPoint Presentation, free download Receivers Public Key The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Rsa algorithm is an asymmetric cryptography algorithm. Is public key encryption better? The receiver will verify by decrypting the. Receivers Public Key.
From slideplayer.com
Network Security. ppt download Receivers Public Key Session key is encrypted using receivers pubic key. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. The. Receivers Public Key.
From www.slideserve.com
PPT Security Continued PowerPoint Presentation, free download ID Receivers Public Key The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. If the decrypted data matches original message, it. Is public key encryption. Receivers Public Key.
From www.newsoftwares.net
Exploring The Intricacies Of PKI Encryption Which Key Encrypts The Data? Receivers Public Key The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. At a high level, pke between a sender and receiver is a protocol for encrypting messages under. Receivers Public Key.
From discover.hubpages.com
Unblocking the Blockchain PublicKey Cryptography HubPages Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Is public key encryption better? At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver will verify by decrypting. Receivers Public Key.
From www.franziskuskiefer.de
TL;DR Hybrid Public Key Encryption Receivers Public Key Receiver sends public key while keeping the matching private key secret. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or. Receivers Public Key.
From www.slideserve.com
PPT Electronic Commerce Technology PowerPoint Presentation, free Receivers Public Key Receiver sends public key while keeping the matching private key secret. Is public key encryption better? The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. At. Receivers Public Key.
From katuhito.net
Electronic Signature and Electronic Authentication/Electronic Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. If the decrypted data matches original message, it. Is public key encryption better? At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s. Receivers Public Key.
From slidetodoc.com
Public Key Infrastructure Digital Certificates n Public key Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Rsa algorithm is an asymmetric cryptography algorithm. Session key is encrypted using receivers pubic key. Is public key encryption better? Asymmetric means that it works on two different keys i.e. At a. Receivers Public Key.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta AU & NZ Receivers Public Key At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Receiver sends public key while keeping the matching private key secret. Is public key encryption better? If the decrypted data matches original message, it. The receiver’s public key is used to encrypt a message that can be decrypted only. Receivers Public Key.
From www.infosec.gov.hk
InfoSec Public Key Infrastructure Receivers Public Key Asymmetric means that it works on two different keys i.e. Session key is encrypted using receivers pubic key. If the decrypted data matches original message, it. The receiver will verify by decrypting the encrypted data with your public key. The receiver sends the public key on the same channel as the one it intends to receive the message, but the. Receivers Public Key.
From www.slideserve.com
PPT Grid Security PowerPoint Presentation, free download ID4218054 Receivers Public Key The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. The receiver will verify by decrypting the encrypted data with your public key. Rsa algorithm is an. Receivers Public Key.
From slideplayer.com
Security. ppt download Receivers Public Key Receiver sends public key while keeping the matching private key secret. The receiver will verify by decrypting the encrypted data with your public key. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Is public key encryption better? Session key is encrypted using receivers pubic key.. Receivers Public Key.
From deepaksood619.github.io
Publickey cryptography Deep Notes Receivers Public Key If the decrypted data matches original message, it. Rsa algorithm is an asymmetric cryptography algorithm. Asymmetric means that it works on two different keys i.e. Session key is encrypted using receivers pubic key. Is public key encryption better? The receiver will verify by decrypting the encrypted data with your public key. Receiver sends public key while keeping the matching private. Receivers Public Key.
From slideplayer.com
PGP CSC 492 Presentation May 2, 2007 Brandon Skari Ruby Matejcik. ppt Receivers Public Key Receiver sends public key while keeping the matching private key secret. If the decrypted data matches original message, it. Session key is encrypted using receivers pubic key. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Is public key encryption better?. Receivers Public Key.
From www.bartleby.com
Answered How will the Receiver verify a Digital… bartleby Receivers Public Key The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Session key is encrypted using receivers pubic key. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver’s public key is used to encrypt. Receivers Public Key.
From slideplayer.com
Cryptography and Network Security Chapter 9 ppt download Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. Receiver sends public key while keeping the matching private key secret. The receiver sends the public key on the same channel as the one it intends to receive the message, but the. Receivers Public Key.
From slideplayer.com
Unit 3 Section 6.4 Security ppt download Receivers Public Key If the decrypted data matches original message, it. The receiver sends the public key on the same channel as the one it intends to receive the message, but the key's authenticity. Rsa algorithm is an asymmetric cryptography algorithm. The receiver will verify by decrypting the encrypted data with your public key. The receiver’s public key is used to encrypt a. Receivers Public Key.
From cheapsslweb.com
Public Key and Private Key Pairs How do they work? Receivers Public Key Receiver sends public key while keeping the matching private key secret. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver will verify by decrypting the encrypted data with your public key. Public key cryptography is a method of secure communication that uses a pair of keys,. Receivers Public Key.
From www.slideserve.com
PPT Data Integrity PowerPoint Presentation, free download ID6013739 Receivers Public Key If the decrypted data matches original message, it. Receiver sends public key while keeping the matching private key secret. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver sends the public key on the same channel as the one it intends to receive the message, but. Receivers Public Key.
From slideplayer.com
CS162 Operating Systems and Systems Programming Lecture 24 Security Receivers Public Key Receiver sends public key while keeping the matching private key secret. The receiver’s public key is used to encrypt a message that can be decrypted only by the receiver's private key. Rsa algorithm is an asymmetric cryptography algorithm. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use. Receivers Public Key.
From slideplayer.com
Cryptography An Introduction Continued… ppt download Receivers Public Key At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver will verify by decrypting the encrypted data with your public key. Is public key encryption better? Session key is encrypted using receivers pubic key. Receiver sends public key while keeping the matching private key secret. Rsa algorithm. Receivers Public Key.
From www.sectigo.com
Public Key Cryptography Private vs Public Sectigo® Official Receivers Public Key Asymmetric means that it works on two different keys i.e. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Rsa algorithm is an asymmetric cryptography algorithm. Session key is encrypted using receivers pubic key. The receiver sends the public key on the same channel as the one it. Receivers Public Key.
From www.thesecuritybuddy.com
Symmetric Key Encryption vs Public Key Encryption The Security Buddy Receivers Public Key Asymmetric means that it works on two different keys i.e. Receiver sends public key while keeping the matching private key secret. Session key is encrypted using receivers pubic key. The receiver will verify by decrypting the encrypted data with your public key. If the decrypted data matches original message, it. The receiver’s public key is used to encrypt a message. Receivers Public Key.
From www.slideserve.com
PPT Receiver Anonymity via Public Keys PowerPoint Receivers Public Key Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures,. At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. Is public key encryption better? Asymmetric means that it works on. Receivers Public Key.
From blog.cloudflare.com
HPKE Standardizing publickey encryption (finally!) Receivers Public Key At a high level, pke between a sender and receiver is a protocol for encrypting messages under the receiver’s public key. The receiver will verify by decrypting the encrypted data with your public key. If the decrypted data matches original message, it. The receiver sends the public key on the same channel as the one it intends to receive the. Receivers Public Key.