Extended Acl Example . In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. This article describes the configuration and verification of extended acls (access lists) using an example. Learn extended access list management through a packet. This tutorial explains the commands and configurations required for extended access lists. You can identify parameters within the. Each ace specifies a source and destination for matching traffic. An extended acl is made up of one or more access control entries (aces). This tutorial explains how to create, apply, update and delete a named extended access list. In an extended access list, particular services. Learn the extended access list management through a packet tracer example.
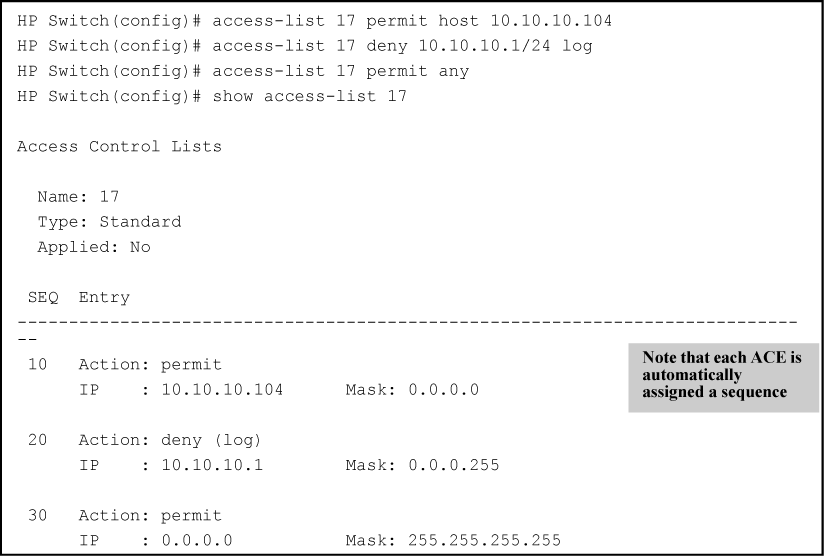
from techhub.hpe.com
This tutorial explains how to create, apply, update and delete a named extended access list. This tutorial explains the commands and configurations required for extended access lists. Learn extended access list management through a packet. Each ace specifies a source and destination for matching traffic. An extended acl is made up of one or more access control entries (aces). In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. In an extended access list, particular services. This article describes the configuration and verification of extended acls (access lists) using an example. You can identify parameters within the. Learn the extended access list management through a packet tracer example.
IPv4 Access Control Lists (ACLs)
Extended Acl Example You can identify parameters within the. You can identify parameters within the. This tutorial explains how to create, apply, update and delete a named extended access list. Each ace specifies a source and destination for matching traffic. An extended acl is made up of one or more access control entries (aces). In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. In an extended access list, particular services. This article describes the configuration and verification of extended acls (access lists) using an example. Learn the extended access list management through a packet tracer example. Learn extended access list management through a packet. This tutorial explains the commands and configurations required for extended access lists.
From www.slideshare.net
Extended ACL Extended Acl Example In an extended access list, particular services. Learn the extended access list management through a packet tracer example. This tutorial explains the commands and configurations required for extended access lists. This article describes the configuration and verification of extended acls (access lists) using an example. In the extended access list, packet filtering takes place on the basis of source ip. Extended Acl Example.
From www.youtube.com
4. ACL Sample Configuration YouTube Extended Acl Example Learn extended access list management through a packet. An extended acl is made up of one or more access control entries (aces). You can identify parameters within the. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. This tutorial explains the commands and configurations required for extended access. Extended Acl Example.
From geek-university.com
Extended ACLs CCNA Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. Learn extended access list management through a packet. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. You can identify parameters within the. In an extended access list, particular services. An extended acl. Extended Acl Example.
From www.slideserve.com
PPT IP QoS PowerPoint Presentation, free download ID3346698 Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. Each ace specifies a source and destination for matching traffic. This tutorial explains how to create, apply, update and delete a named extended access list. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port. Extended Acl Example.
From networkustad.com
How to Configure Extended ACLs Exclusive Explanation » NetworkUstad Extended Acl Example In an extended access list, particular services. Learn extended access list management through a packet. You can identify parameters within the. An extended acl is made up of one or more access control entries (aces). This article describes the configuration and verification of extended acls (access lists) using an example. This tutorial explains the commands and configurations required for extended. Extended Acl Example.
From www.youtube.com
Named ACL Configuration Demonstration Access Control Lists (ACLs Extended Acl Example An extended acl is made up of one or more access control entries (aces). You can identify parameters within the. Learn extended access list management through a packet. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. In an extended access list, particular services. This tutorial explains how. Extended Acl Example.
From ccna-200-301.online
Configure Extended IPv4 ACLs » CCNA 200301 Extended Acl Example Learn the extended access list management through a packet tracer example. Learn extended access list management through a packet. You can identify parameters within the. This article describes the configuration and verification of extended acls (access lists) using an example. In an extended access list, particular services. This tutorial explains how to create, apply, update and delete a named extended. Extended Acl Example.
From www.youtube.com
Types of ACLs !! Standard ACL !! Extended ACL !! Difference Between Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. You can identify parameters within the. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. This article describes the configuration and verification of extended acls (access lists) using an example. In an extended. Extended Acl Example.
From advancedmedicalcertification.com
Adult Cardiac Arrest Management Algorithm ACLS Online Handbook Extended Acl Example Each ace specifies a source and destination for matching traffic. You can identify parameters within the. An extended acl is made up of one or more access control entries (aces). In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. In an extended access list, particular services. This tutorial. Extended Acl Example.
From www.cisco.com
Access Control Lists and IP Fragments Cisco Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. This tutorial explains the commands and configurations required for extended access lists. You can identify parameters within the. This article describes the configuration and verification of extended acls (access lists) using an example. Learn the extended access list management through a packet tracer example. In. Extended Acl Example.
From www.ccnablog.com
ACLs (Access Control Lists) Part I CCNA Blog Extended Acl Example Learn extended access list management through a packet. In an extended access list, particular services. An extended acl is made up of one or more access control entries (aces). This tutorial explains the commands and configurations required for extended access lists. Each ace specifies a source and destination for matching traffic. Learn the extended access list management through a packet. Extended Acl Example.
From www.youtube.com
Configure Cisco Extended ACL/ Extended Numbered Access Control List ACL Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. Learn extended access list management through a packet. Each ace specifies a source and destination for matching traffic. This article describes the configuration and verification of extended acls (access lists) using an example. You can identify parameters within the. In an extended access list, particular. Extended Acl Example.
From charlesinstitute.com
BLS ACLS PALS Sample Certificates Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. Learn the extended access list management through a packet tracer example. Each ace specifies a source and destination for matching traffic. You can identify parameters within the. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip. Extended Acl Example.
From www.slideserve.com
PPT Access Control Lists (ACLs) PowerPoint Presentation, free Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. This tutorial explains the commands and configurations required for extended access lists. This article describes the configuration and verification of extended acls (access lists) using an example. Learn the extended access list management through a packet tracer example. An extended acl is made up of. Extended Acl Example.
From www.youtube.com
Configuring Extended IPv4 ACLs Numbered and Named YouTube Extended Acl Example Each ace specifies a source and destination for matching traffic. In an extended access list, particular services. Learn the extended access list management through a packet tracer example. This tutorial explains the commands and configurations required for extended access lists. This tutorial explains how to create, apply, update and delete a named extended access list. An extended acl is made. Extended Acl Example.
From www.slideserve.com
PPT ACL(Access Control Lists) PowerPoint Presentation, free download Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. This tutorial explains the commands and configurations required for extended access lists. This article describes the configuration and verification of extended acls (access lists) using an example. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip. Extended Acl Example.
From emedcert.com
ACLS Algorithms You Need To Know Extended Acl Example This tutorial explains the commands and configurations required for extended access lists. Each ace specifies a source and destination for matching traffic. You can identify parameters within the. An extended acl is made up of one or more access control entries (aces). In the extended access list, packet filtering takes place on the basis of source ip address, destination ip. Extended Acl Example.
From www.youtube.com
Configuring cisco extended acl / extended named access control list Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. Each ace specifies a source and destination for matching traffic. Learn extended access list management through a packet. In an extended access list, particular services. Learn the extended access list management through a packet tracer example. An extended acl is made up of one or. Extended Acl Example.
From www.practicalnetworking.net
Access Control Lists (ACLs) Practical Networking Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. Learn the extended access list management through a packet tracer example. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. An extended acl is made up of one or more access control entries. Extended Acl Example.
From www.slideserve.com
PPT CCENT Study Guide PowerPoint Presentation, free download ID1564817 Extended Acl Example Learn extended access list management through a packet. This tutorial explains the commands and configurations required for extended access lists. An extended acl is made up of one or more access control entries (aces). This article describes the configuration and verification of extended acls (access lists) using an example. This tutorial explains how to create, apply, update and delete a. Extended Acl Example.
From www.youtube.com
Extended Access List (ACL) for the Cisco CCNA Part 1 YouTube Extended Acl Example Learn extended access list management through a packet. This article describes the configuration and verification of extended acls (access lists) using an example. In an extended access list, particular services. An extended acl is made up of one or more access control entries (aces). In the extended access list, packet filtering takes place on the basis of source ip address,. Extended Acl Example.
From www.bytesofcloud.net
Those Pesky ACLs Bytes of Cloud Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. In an extended access list, particular services. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. Learn extended access list management through a packet. Learn the extended access list management through a packet. Extended Acl Example.
From www.youtube.com
Configuration of Standard ACLs Example 1 YouTube Extended Acl Example An extended acl is made up of one or more access control entries (aces). Learn extended access list management through a packet. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. This article describes the configuration and verification of extended acls (access lists) using an example. You can. Extended Acl Example.
From www.youtube.com
Extended Access List (ACL) for the Cisco CCNA Part 2 YouTube Extended Acl Example In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. An extended acl is made up of one or more access control entries (aces). This article describes the configuration and verification of extended acls (access lists) using an example. You can identify parameters within the. Learn extended access list. Extended Acl Example.
From www.slideserve.com
PPT ACL & QoS PowerPoint Presentation, free download ID5507397 Extended Acl Example In an extended access list, particular services. Each ace specifies a source and destination for matching traffic. Learn extended access list management through a packet. This tutorial explains how to create, apply, update and delete a named extended access list. Learn the extended access list management through a packet tracer example. In the extended access list, packet filtering takes place. Extended Acl Example.
From www.slideserve.com
PPT Managing IP Traffic with ACLs PowerPoint Presentation, free Extended Acl Example This tutorial explains the commands and configurations required for extended access lists. Learn the extended access list management through a packet tracer example. In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. You can identify parameters within the. Learn extended access list management through a packet. This tutorial. Extended Acl Example.
From www.slideserve.com
PPT Year 2 Chapter 6/Cisco 3 Module 6 ACLs PowerPoint Extended Acl Example In the extended access list, packet filtering takes place on the basis of source ip address, destination ip address, port numbers. You can identify parameters within the. An extended acl is made up of one or more access control entries (aces). Learn the extended access list management through a packet tracer example. This article describes the configuration and verification of. Extended Acl Example.
From www.slideserve.com
PPT Year 2 Chapter 6/Cisco 3 Module 6 ACLs PowerPoint Extended Acl Example This tutorial explains the commands and configurations required for extended access lists. This tutorial explains how to create, apply, update and delete a named extended access list. In an extended access list, particular services. Each ace specifies a source and destination for matching traffic. You can identify parameters within the. Learn extended access list management through a packet. In the. Extended Acl Example.
From www.slideserve.com
PPT Access Control List (ACL) PowerPoint Presentation, free download Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. In an extended access list, particular services. This tutorial explains the commands and configurations required for extended access lists. An extended acl is made up of one or more access control entries (aces). This tutorial explains how to create, apply, update and delete a named. Extended Acl Example.
From www.youtube.com
Extended ACLs Configuration L8 Access Control List Cisco Packet Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. In an extended access list, particular services. An extended acl is made up of one or more access control entries (aces). Learn the extended access list management through a packet tracer example. In the extended access list, packet filtering takes place on the basis of. Extended Acl Example.
From techhub.hpe.com
IPv4 Access Control Lists (ACLs) Extended Acl Example You can identify parameters within the. This tutorial explains the commands and configurations required for extended access lists. An extended acl is made up of one or more access control entries (aces). In an extended access list, particular services. Each ace specifies a source and destination for matching traffic. This article describes the configuration and verification of extended acls (access. Extended Acl Example.
From www.slideserve.com
PPT Extended Access Control Lists PowerPoint Presentation, free Extended Acl Example This tutorial explains how to create, apply, update and delete a named extended access list. Learn extended access list management through a packet. An extended acl is made up of one or more access control entries (aces). Learn the extended access list management through a packet tracer example. This tutorial explains the commands and configurations required for extended access lists.. Extended Acl Example.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Extended Acl Example Each ace specifies a source and destination for matching traffic. You can identify parameters within the. Learn extended access list management through a packet. This article describes the configuration and verification of extended acls (access lists) using an example. Learn the extended access list management through a packet tracer example. An extended acl is made up of one or more. Extended Acl Example.
From www.youtube.com
Extended ACL Example YouTube Extended Acl Example You can identify parameters within the. An extended acl is made up of one or more access control entries (aces). Learn the extended access list management through a packet tracer example. This tutorial explains how to create, apply, update and delete a named extended access list. This tutorial explains the commands and configurations required for extended access lists. This article. Extended Acl Example.
From ipcisco.com
Extended ACL Cisco Configuration on GNS3 4 Steps ⋆ IpCisco Extended Acl Example This article describes the configuration and verification of extended acls (access lists) using an example. This tutorial explains the commands and configurations required for extended access lists. In an extended access list, particular services. Learn extended access list management through a packet. This tutorial explains how to create, apply, update and delete a named extended access list. Learn the extended. Extended Acl Example.