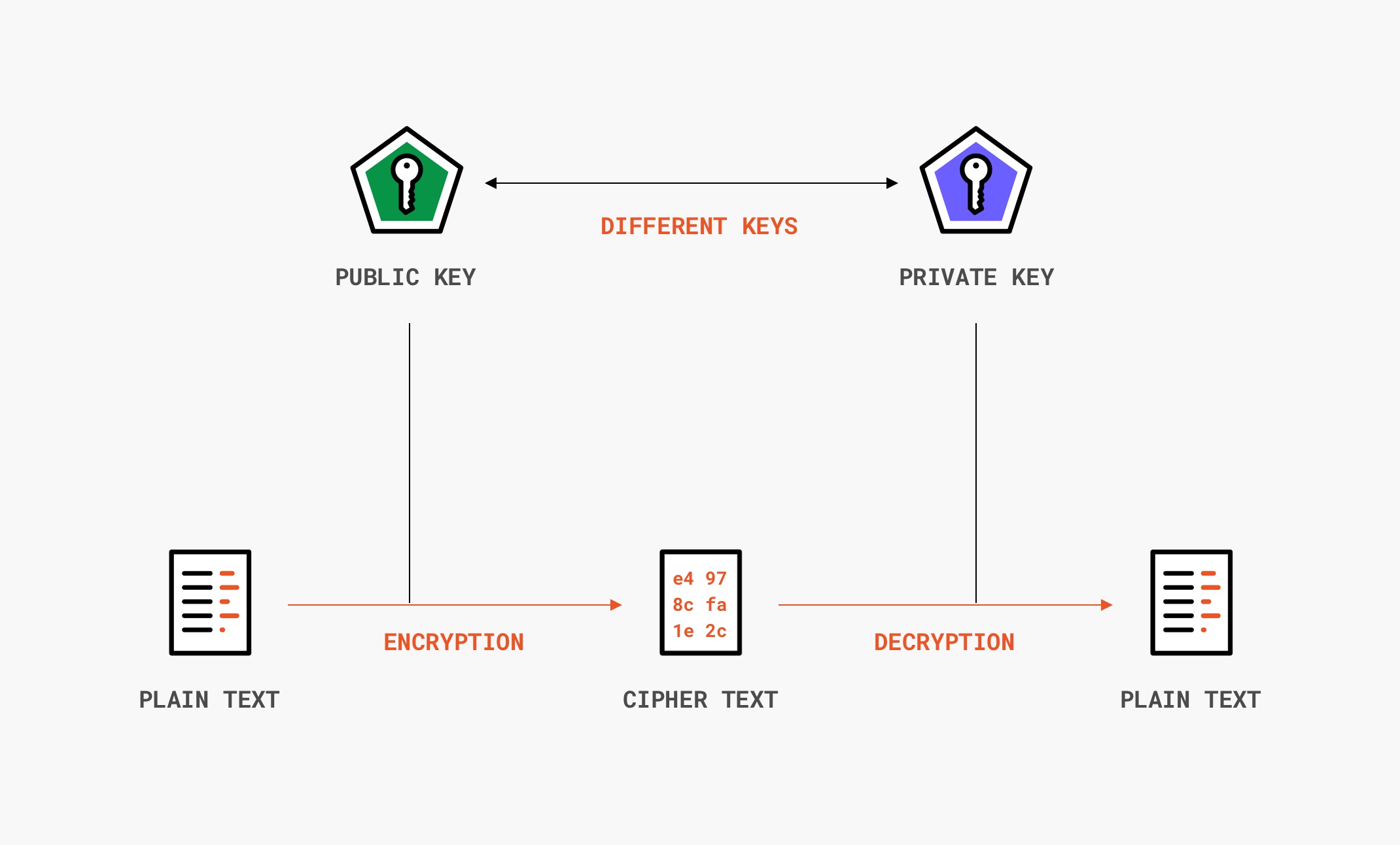
Hardware Key Authentication . Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their.
from auth0.com
Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. Learn how yubikeys work with any. After you’ve enrolled your security key with a.
The Working Principles of 2FA (2Factor Authentication) Hardware
Hardware Key Authentication After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any.
From www.malwarebytes.com
How to enable Facebook's hardware key authentication for iOS and Android Hardware Key Authentication Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From www.protectimus.com
PayPal TwoFactor Authentication with Hardware Security Key Hardware Key Authentication Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From medium.com
The Benefits of Hardware Security Keys for Passwordless Authentication Hardware Key Authentication Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From www.researchgate.net
Hardware authentication module for generating cryptographic key from Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From locker.io
What are hardware security keys, and should you use them? Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From www.youtube.com
2FA Types and Options OTP vs App Authenticator vs Hardware Key Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Hardware Key Authentication.
From www.youtube.com
2 PKI and 802 1X Certificate Based Authentication YouTube Hardware Key Authentication Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Hardware Key Authentication.
From www.nytimes.com
The 2 Best Security Keys for MultiFactor Authentication in 2023 Hardware Key Authentication After you’ve enrolled your security key with a. Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From www.techradar.com
Best security key in 2022 TechRadar Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From developer.signicat.com
Hardwareprotected keys Signicat Documentation Hardware Key Authentication Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From gatekeeperhelp.zendesk.com
What is hardwarebased authentication? GateKeeper Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From www.linkedin.com
How to Use Hardware Keys in Encryption and Authentication Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From plurilock.com
Compared Token Authentication Plurilock Security Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Hardware Key Authentication.
From www.pocket-lint.com
Best hardware security keys for twofactor authentication Hardware Key Authentication Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From www.pocket-lint.com
What are hardware security keys and how do they work? Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From meugen.com.br
Yubico YubiKey 5C Two Factor Authentication USB Security Key Hardware Key Authentication After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From auth0.com
The Working Principles of 2FA (2Factor Authentication) Hardware Hardware Key Authentication After you’ve enrolled your security key with a. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From deepai.org
Usability Assessment of the OnlyKey Hardware TwoFactor Authentication Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Hardware Key Authentication.
From www.mdpi.com
Symmetry Free FullText A Secure Authentication and Key Agreement Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Hardware Key Authentication.
From www.malwarebytes.com
How to set up twofactor authentication on Twitter using a hardware key Hardware Key Authentication Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Hardware Key Authentication.
From www.scmagazine.com
Tech giants encouraging adoption of hardwarebased auth keys SC Media Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Hardware Key Authentication.
From www.slideshare.net
Hardware Authentication Hardware Key Authentication Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Hardware Key Authentication.
From geekflare.com
9 Best Hardware Security Keys for TwoFactor Authentication [2024] Hardware Key Authentication After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From docs.servicenow.com
Register a hardware security key Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From anvil.works
Using hardware tokens for twofactor authentication how does it work? Hardware Key Authentication After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From geekflare.com
9 Best Hardware Security Keys for TwoFactor Authentication [2024] Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. Learn how yubikeys work with any. After you’ve enrolled your security key with a. Hardware Key Authentication.
From zabir.ru
Authenticate Hardware Key Authentication After you’ve enrolled your security key with a. Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From www.scienceabc.com
Factors Of Authentication What is 2FA? What is MFA? Hardware Key Authentication Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From laptrinhx.com
Authentication with Hardware Security Keys and Authn in SAP Commerce Hardware Key Authentication Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. Compare 9 best security keys for 2fa from amazon and their. Hardware Key Authentication.
From www.ssh.com
What is an SSH Key? An Overview of SSH Keys Hardware Key Authentication Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. After you’ve enrolled your security key with a. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Hardware Key Authentication.
From auth0.com
The Working Principles of 2FA (2Factor Authentication) Hardware Hardware Key Authentication Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Learn how yubikeys work with any. Hardware Key Authentication.
From geekflare.com
9 Best Hardware Security Keys for TwoFactor Authentication [2024 Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. Learn how yubikeys work with any. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From sectona.com
What Is Active Directory Authentication And How Does It Work? Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Learn how yubikeys work with any. After you’ve enrolled your security key with a. Hardware Key Authentication.
From medium.com
Authereum Now Supports Hardware Security Keys for TwoFactor Hardware Key Authentication Compare 9 best security keys for 2fa from amazon and their. After you’ve enrolled your security key with a. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Hardware Key Authentication.
From www.tomsguide.com
How to Make Your Own TwoFactor Authentication Key Tom's Guide Hardware Key Authentication Learn how yubikeys work with any. Learn what 2fa is, why it is essential, and how hardware security keys work as an extra layer of verification. Compare 9 best security keys for 2fa from amazon and their. Yubico offers hardware security keys that protect users from phishing attacks and account takeovers. After you’ve enrolled your security key with a. Hardware Key Authentication.