Hardware Information Flow Analysis . understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. information flow tracking (ift) is a fundamental computer security technique used to understand how. in this work, we propose a property specific approach for information flow security. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),.
from learn.g2.com
understanding how information flows throughout a computing system is crucial to determine if that system operates. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. We create information flow models tailored to. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how.
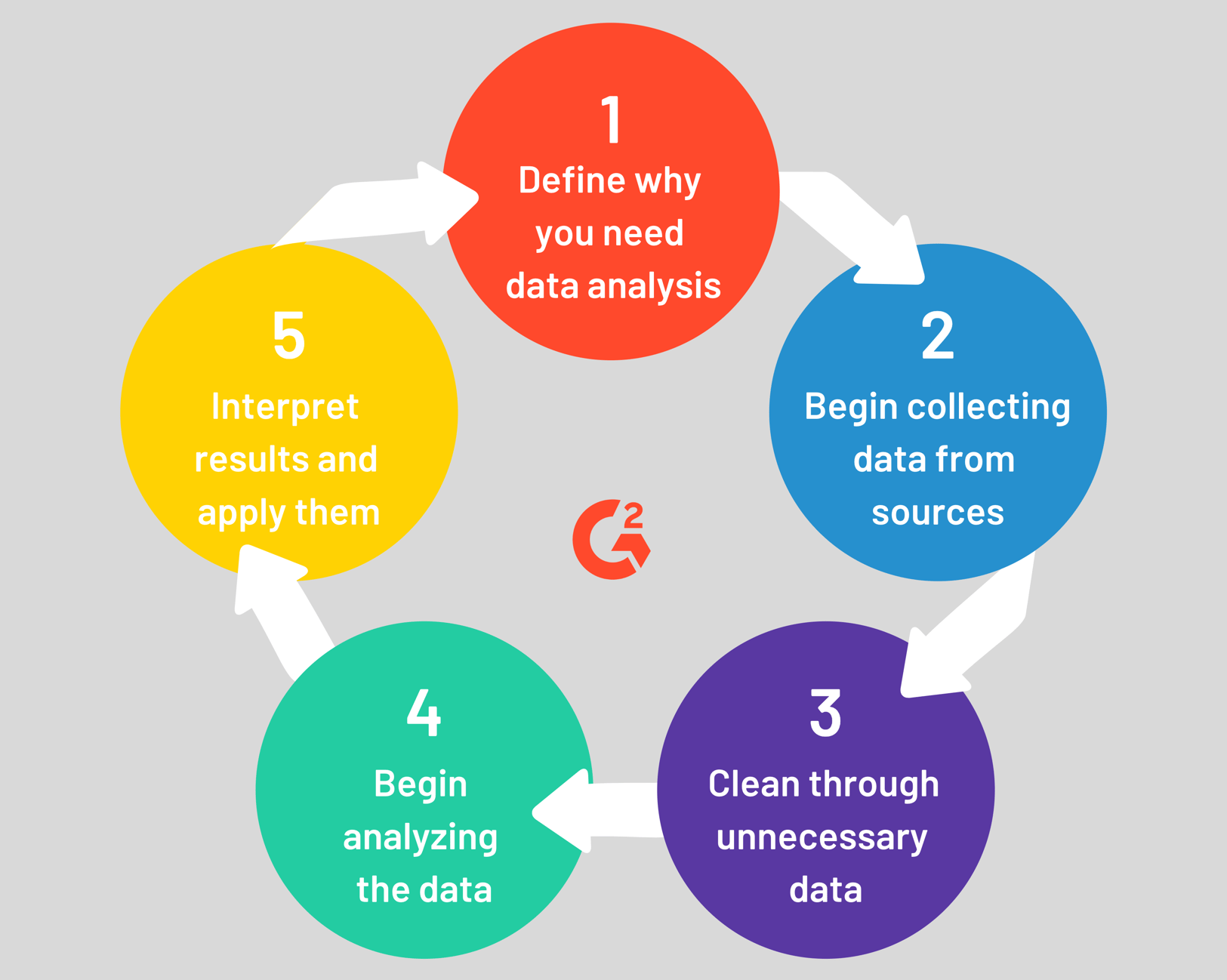
5 Steps of the Data Analysis Process
Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. information flow tracking (ift) is a fundamental computer security technique used to understand how. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. We create information flow models tailored to. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. understanding how information flows throughout a computing system is crucial to determine if that system operates.
From learn.g2.com
5 Steps of the Data Analysis Process Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. We create information flow models tailored to. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system.. Hardware Information Flow Analysis.
From www.knowledgezonee.com
Basic Knowledge Of Hardware And Networking knowledge Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. the methodology we present here can inform an automated analysis of a hardware design by identifying. Hardware Information Flow Analysis.
From www.researchgate.net
(PDF) Automated Information Flow Analysis for Integrated Computingin Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. We create information flow models tailored to. in this work, we propose a property specific approach for information flow security. understanding how information flows throughout a computing system is crucial to determine if that system operates. . Hardware Information Flow Analysis.
From www.researchgate.net
Flow chart for hardware implementation. Download Scientific Diagram Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how. in this work, we propose a property specific approach for information flow security. We create information flow models tailored to. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this. Hardware Information Flow Analysis.
From www.researchgate.net
Hardware Flow Diagram Download Scientific Diagram Hardware Information Flow Analysis We create information flow models tailored to. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this work, we propose a property specific approach for information flow security. the methodology we present here can inform an automated analysis of a hardware design by identifying flow.. Hardware Information Flow Analysis.
From www.lucidchart.com
Data Flow Diagram (DFD) Software Lucidchart Hardware Information Flow Analysis We create information flow models tailored to. information flow tracking (ift) is a fundamental computer security technique used to understand how. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates.. Hardware Information Flow Analysis.
From www.vrogue.co
School Library System Dataflow Diagram Dfd Freeprojec vrogue.co Hardware Information Flow Analysis the methodology we present here can inform an automated analysis of a hardware design by identifying flow. We create information flow models tailored to. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this work, we propose a property specific approach for information flow security.. Hardware Information Flow Analysis.
From www.researchgate.net
Structure of an information flow analysis Download Scientific Diagram Hardware Information Flow Analysis in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. We create information flow models tailored to. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing. Hardware Information Flow Analysis.
From www.lucidchart.com
Data Flow Diagram Symbols, Types, and Tips Lucidchart Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. We create information flow models tailored to. understanding how information flows throughout a computing system is crucial to determine. Hardware Information Flow Analysis.
From arannaroob.blogspot.com
20+ data flow network diagram ArannAroob Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this work, we propose a property specific approach for information flow security. information flow tracking (ift). Hardware Information Flow Analysis.
From thejitcompany.com
VSM, MIFA And Philips’ Goods Flow Analysis THE JIT COMPANY Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section, we. Hardware Information Flow Analysis.
From www.researchgate.net
Flow chart of the hardwaresoftware complex Download Scientific Diagram Hardware Information Flow Analysis the methodology we present here can inform an automated analysis of a hardware design by identifying flow. information flow tracking (ift) is a fundamental computer security technique used to understand how. We create information flow models tailored to. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. . Hardware Information Flow Analysis.
From www.perplexity.ai
Data Flow Diagrams Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. understanding how information flows throughout a computing system is crucial to determine if that system operates. the methodology. Hardware Information Flow Analysis.
From www.smartdraw.com
Data Flow Diagram Everything You Need to Know About DFD Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section,. Hardware Information Flow Analysis.
From diagramlibdrindar43l.z13.web.core.windows.net
Data Flow Diagram Generator Ai Hardware Information Flow Analysis We create information flow models tailored to. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. information flow tracking (ift) is a fundamental computer security technique used to understand how. understanding how information flows throughout a computing system is crucial to determine if that system operates. in. Hardware Information Flow Analysis.
From dzone.com
The Search for a Better BIG Data Analytics Pipeline DZone Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. We create information flow models tailored to. information flow. Hardware Information Flow Analysis.
From www.slideserve.com
PPT Data flow analysis PowerPoint Presentation, free download ID902610 Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security. Hardware Information Flow Analysis.
From www.youtube.com
Lecture "Information Flow Analysis (Part 1, Introduction)" of "Program Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this. Hardware Information Flow Analysis.
From old.sermitsiaq.ag
Data Flow Diagram Template Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. information flow tracking (ift) is a fundamental computer security technique used to understand how. understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to.. Hardware Information Flow Analysis.
From cs.stackexchange.com
lambda calculus What makes data flow analysis higher level than Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how. in this work, we propose a. Hardware Information Flow Analysis.
From blog.adafruit.com
The Manufacturing Process a Timeline and Analysis for Hardware Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how. in this work,. Hardware Information Flow Analysis.
From www.slideshare.net
Chapter 1 computer hardware and flow of information Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this section, we. Hardware Information Flow Analysis.
From www.researchgate.net
Data flow in hardware implementation Download Scientific Diagram Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. understanding how information flows throughout a. Hardware Information Flow Analysis.
From www.smartdraw.com
How to Make a Data Flow Diagram or DFD Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how. We create information flow models tailored to. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system.. Hardware Information Flow Analysis.
From www.youtube.com
Data Flow Analysis YouTube Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. We create information flow models tailored to. the methodology. Hardware Information Flow Analysis.
From robhosking.com
14+ Data Flow Diagram For Online Ordering System Robhosking Diagram Hardware Information Flow Analysis in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. in this work, we propose a property specific approach for information flow security. understanding how information flows throughout. Hardware Information Flow Analysis.
From mungfali.com
Data Management Process Flow Diagram Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how. understanding how information flows throughout a computing system is crucial to determine if that system operates. in this work, we propose a property specific approach for information flow security. the methodology we present here can inform an automated analysis of a hardware. Hardware Information Flow Analysis.
From www.researchgate.net
Typical simplified design flow of a hardware/software embedded system Hardware Information Flow Analysis in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. information flow tracking (ift) is a fundamental computer security technique used to understand how. understanding how information flows. Hardware Information Flow Analysis.
From www.conceptdraw.com
Data Flow Diagram, workflow diagram, process flow diagram Hardware Information Flow Analysis We create information flow models tailored to. in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing. Hardware Information Flow Analysis.
From www.semanticscholar.org
Figure 6.1 from Informationflow analysis for covertchannel Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. understanding how information flows throughout a computing system is crucial to determine if that system operates. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. in this section, we provide a brief. Hardware Information Flow Analysis.
From www.allassignmenthelp.co.uk
Information Flow Analysis and Types of Information Flow Hardware Information Flow Analysis understanding how information flows throughout a computing system is crucial to determine if that system operates. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how. in this work, we propose a property specific approach for. Hardware Information Flow Analysis.
From www.dosupply.com
PLC Troubleshooting Flowchart (and Explanation) Do Supply Tech Support Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. understanding how information flows throughout a computing system is crucial to determine if that system operates. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. information flow tracking (ift) is a fundamental. Hardware Information Flow Analysis.
From www.youtube.com
ACSAC'17 Kakute A Precise, Unified Information Flow Analysis System Hardware Information Flow Analysis information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. understanding how information flows throughout a computing system is crucial to determine if that system operates. We create information flow models tailored to. in this work, we propose a property specific approach for information flow security. . Hardware Information Flow Analysis.
From www.researchgate.net
(PDF) Quantitative Information Flow for Hardware Advancing the Attack Hardware Information Flow Analysis in this work, we propose a property specific approach for information flow security. understanding how information flows throughout a computing system is crucial to determine if that system operates. the methodology we present here can inform an automated analysis of a hardware design by identifying flow. understanding how information flows throughout a computing system is crucial. Hardware Information Flow Analysis.
From mail.ida-inc.com
FTA Hardware and Software Services by Independent Design Analyses, Inc Hardware Information Flow Analysis in this section, we provide a brief background on existing techniques about hardware information flow tracking (section 2.1),. in this work, we propose a property specific approach for information flow security. information flow tracking (ift) is a fundamental computer security technique used to understand how information moves through a computing system. the methodology we present here. Hardware Information Flow Analysis.