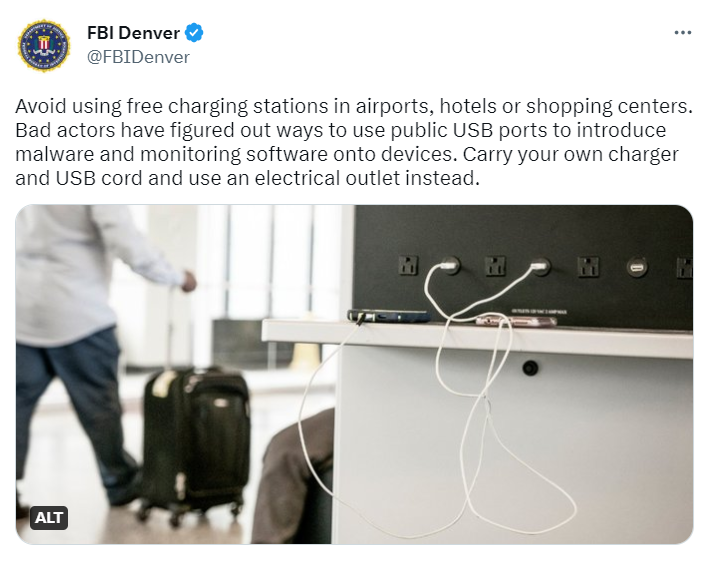
How Does Juice Jacking Work . Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. The same port or cable is used for both data and electricity. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Here's a common example of juice jacking: Cybersecurity experts warn that bad actors can. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Next, bestuzhev explained how juice jacking works. That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. “imagine using a phone for charging. Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers.
from blogs.blackberry.com
Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. “imagine using a phone for charging. Next, bestuzhev explained how juice jacking works. Here's a common example of juice jacking: You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Cybersecurity experts warn that bad actors can. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. The same port or cable is used for both data and electricity. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes.
Juice Jacking What It Is, How It Works, and How to Avoid It
How Does Juice Jacking Work Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Cybersecurity experts warn that bad actors can. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. “imagine using a phone for charging. Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. Here's a common example of juice jacking: Next, bestuzhev explained how juice jacking works. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. The same port or cable is used for both data and electricity. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from.
From primetechie.com
Juice jacking How to juice jacking works and protect? Prime Techie How Does Juice Jacking Work A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. The same port or cable is used for both data and electricity. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking is a term used. How Does Juice Jacking Work.
From www.youtube.com
What is juice jacking and how can you keep your device safe from being How Does Juice Jacking Work That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Here's a common example of juice jacking: Rather than simply providing power for charging, such ports also establish. How Does Juice Jacking Work.
From primetechie.com
Juice jacking How to juice jacking works and protect? Prime Techie How Does Juice Jacking Work Next, bestuzhev explained how juice jacking works. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. The same port or cable is used for both. How Does Juice Jacking Work.
From fbijohn.com
Juice Jacking What It Is, How It Works, And How To Protect Yourself How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. Cybersecurity experts warn that bad actors can. Here's. How Does Juice Jacking Work.
From www.hideipvpn.com
What are juice jacking attacks ? How to prevent them? [2023] How Does Juice Jacking Work The same port or cable is used for both data and electricity. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Cybersecurity experts warn that. How Does Juice Jacking Work.
From civils360.com
Juice Jacking Explained Civils360 IAS How Does Juice Jacking Work Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. Cybersecurity experts warn that bad actors can. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. The. How Does Juice Jacking Work.
From www.youtube.com
Juice Jacking Explained 2021 How to Avoid it YouTube How Does Juice Jacking Work Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. “imagine using a phone for charging. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking is a type of attack that. How Does Juice Jacking Work.
From www.slideserve.com
PPT Juice Jacking PowerPoint Presentation, free download ID12058375 How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Cybersecurity experts warn that bad actors can. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Nothing appears out of the ordinary, but when you're charging your. How Does Juice Jacking Work.
From blogs.blackberry.com
Juice Jacking What It Is, How It Works, and How to Avoid It How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. The same port or cable is used for both data and electricity. Cybersecurity experts. How Does Juice Jacking Work.
From www.yittbox.com
How to protect yourself from juice jacking? How Does Juice Jacking Work The same port or cable is used for both data and electricity. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. “imagine using a phone for charging. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Cybersecurity experts. How Does Juice Jacking Work.
From www.wallarm.com
What is Juice Jacking Attack? Definition, Meaning & Prevention How Does Juice Jacking Work Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them. How Does Juice Jacking Work.
From news.trendmicro.com
What Is Juice Jacking? Trend Micro News How Does Juice Jacking Work A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. “imagine using a phone for charging. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Juice jacking occurs when a malicious actor has infected a usb port (or the. How Does Juice Jacking Work.
From fbijohn.com
Juice Jacking What It Is, How It Works, And How To Protect Yourself How Does Juice Jacking Work “imagine using a phone for charging. Cybersecurity experts warn that bad actors can. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. Here's a common. How Does Juice Jacking Work.
From www.youtube.com
Juice Jacking क्या होता है? पब्लिक USB चार्जिंग का इस्तमाल कैसे पड़ How Does Juice Jacking Work That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. Next, bestuzhev explained how juice jacking works. Cybersecurity experts warn that bad actors can. Here's a common example of juice jacking: Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and. How Does Juice Jacking Work.
From www.putertutor.co.uk
“Juice Jacking” know the facts The PuterTutor Computer Repair Services How Does Juice Jacking Work Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. The same port or cable is used for both data and electricity. Next, bestuzhev explained how juice jacking works. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb. How Does Juice Jacking Work.
From www.comparitech.com
Juice jacking What it is, how it works, and how to avoid it How Does Juice Jacking Work Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. The same port or cable is used for both data and electricity. Next, bestuzhev explained how juice jacking works. That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other. How Does Juice Jacking Work.
From cybervie.com
Juice Jacking A Concise Overview CYBERVIE How Does Juice Jacking Work Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware. How Does Juice Jacking Work.
From eventura.com
Is public USB charging safe? Juice Jacking explained How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. The same port or cable is used for both data and electricity. Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Juice jacking. How Does Juice Jacking Work.
From www.youtube.com
Juice jacking explained What is Juice Jacking YouTube How Does Juice Jacking Work Cybersecurity experts warn that bad actors can. That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. The same port or cable is used for both data and electricity. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Juice. How Does Juice Jacking Work.
From articles.brick.tech
Juice Jacking What It Is and How It Works How Does Juice Jacking Work That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. Cybersecurity experts warn that bad actors can. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Rather than simply providing power for charging, such ports also establish a data. How Does Juice Jacking Work.
From www.youtube.com
JuiceJack Defender Turbo How it Works YouTube How Does Juice Jacking Work Next, bestuzhev explained how juice jacking works. “imagine using a phone for charging. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. The. How Does Juice Jacking Work.
From blogs.blackberry.com
Juice Jacking What It Is, How It Works, and How to Avoid It How Does Juice Jacking Work Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. Cybersecurity experts warn that bad actors can. The same port or cable is used for both data and electricity. Next, bestuzhev explained how juice jacking works. A scammer secretly installs hardware. How Does Juice Jacking Work.
From cyberastral.com
How to Protect Yourself from Juice Jacking How Does Juice Jacking Work Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other. How Does Juice Jacking Work.
From securitygladiators.com
What Is Juice Jacking? How Does Juice Jacking Work Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Here's a common example of juice jacking: Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. You use the same cable for synchronizing data on. How Does Juice Jacking Work.
From unboxdiaries.com
Beware of "Juice Jacking" when you use Public Charging Stations! How Does Juice Jacking Work Next, bestuzhev explained how juice jacking works. You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. That typically occurs. How Does Juice Jacking Work.
From inturity.com
Avoid Juice Jacking Inturity How Does Juice Jacking Work Nothing appears out of the ordinary, but when you're charging your mobile phone, the hidden hardware steals your personal and financial info, like bank statements or credit card numbers. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. “imagine using a phone for charging. Juice jacking is a term used. How Does Juice Jacking Work.
From www.def-logix.com
DefLogix What is juice jacking? And how to detect it. How Does Juice Jacking Work That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places. Cybersecurity experts warn that bad actors can. “imagine using a phone for charging. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Here's a common example of juice jacking: Rather than. How Does Juice Jacking Work.
From www.samurai.security.ntt
What is Juice Jacking and How Does it Hurt Your Business? Samurai XDR How Does Juice Jacking Work Cybersecurity experts warn that bad actors can. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Here's a common example of juice jacking: The same. How Does Juice Jacking Work.
From www.youtube.com
What is Juice Jacking? YouTube How Does Juice Jacking Work Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Here's a common example of juice jacking: The same port or cable is used for both data and electricity. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device. How Does Juice Jacking Work.
From www.thesecuritybuddy.com
What is juice jacking in cyber security? The Security Buddy How Does Juice Jacking Work “imagine using a phone for charging. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking is a type of attack that exploits portable devices such as smartphones when you plug them into a compromised usb port. Cybersecurity experts warn that bad actors can. A. How Does Juice Jacking Work.
From www.snsin.com
Cyber Threats in using Public Charging Stations Juice Jacking How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. The same port or cable is used for both data and electricity. That typically occurs on. How Does Juice Jacking Work.
From www.youtube.com
What is juice jacking and how can it be avoided? YouTube How Does Juice Jacking Work Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb ports to steal data from. Here's a common example of juice jacking: A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Cybersecurity experts warn that bad actors can. Juice jacking is a. How Does Juice Jacking Work.
From www.linkedin.com
Juice Jacking What is it? How Does Juice Jacking Work You use the same cable for synchronizing data on your phone with a computer, such as photos, videos, and other information. Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations. How Does Juice Jacking Work.
From www.youtube.com
Juice Jacking How Hackers can steal your Info when you charge devices How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. Juice jacking occurs when a malicious actor has infected a usb port (or the cable attached to the port) with malware. Next, bestuzhev explained how juice jacking works. Juice jacking is a type of attack that exploits. How Does Juice Jacking Work.
From www.asurion.com
Juice jacking what it is, how it works and how to prevent it Asurion How Does Juice Jacking Work Rather than simply providing power for charging, such ports also establish a data connection with a computer or storage device behind the scenes. A scammer secretly installs hardware into a public usb port, which can be found in airports, hotels, or gyms. Juice jacking is a term used for a cybercriminal attack when attackers use public charging stations or usb. How Does Juice Jacking Work.