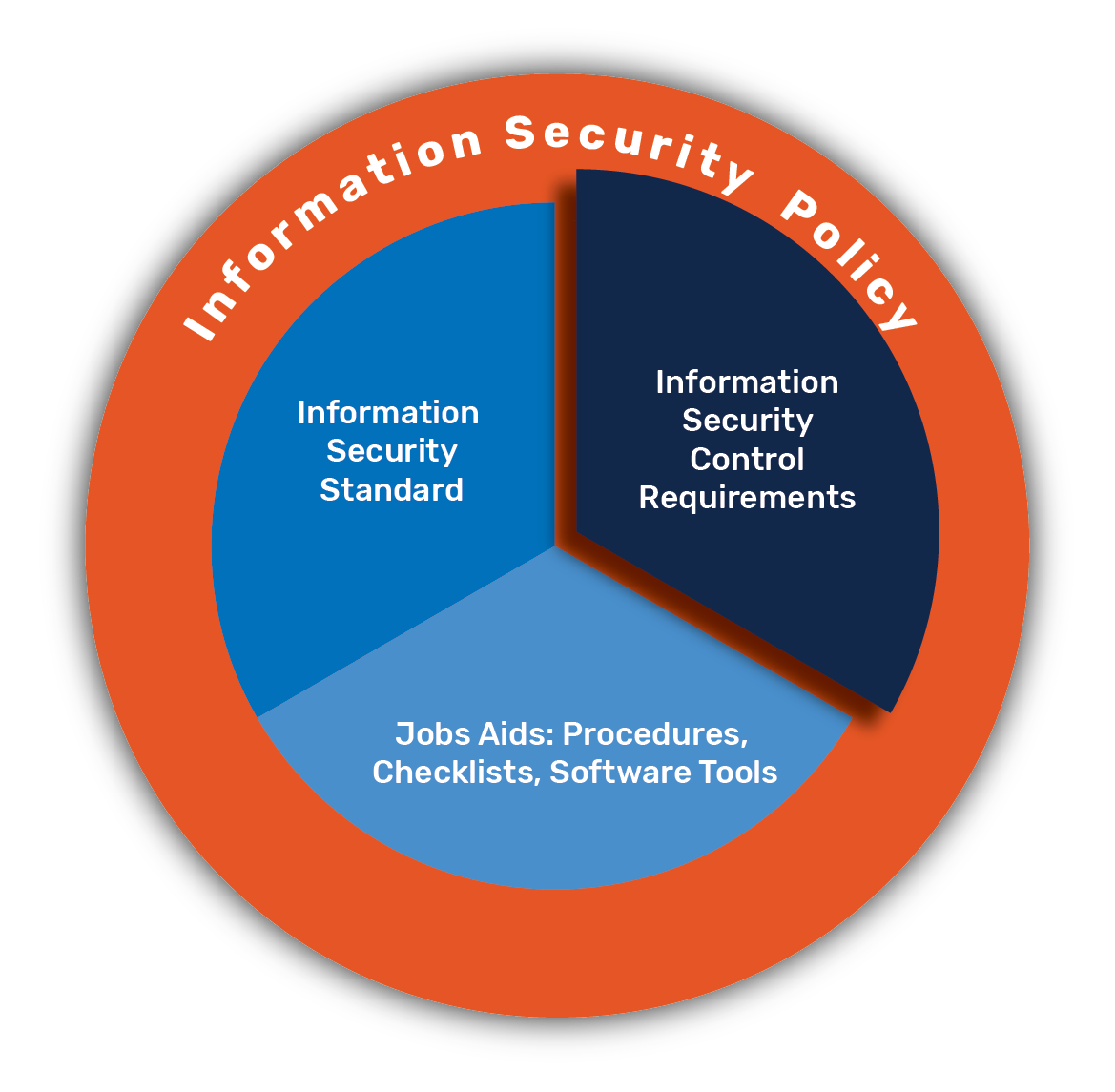
Security Policy On Access Control . Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Organizations planning to implement an access control system should consider three abstractions: Access controls protect network resources against unauthorized access. Learn how to create an effective access control policy that meets your security needs. Annex a.9 is all about access control procedures. The aim of annex a.9 is to safeguard access to information and ensure.
from www.gotyoursixcyber.com
The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Organizations planning to implement an access control system should consider three abstractions: Annex a.9 is all about access control procedures. Access controls protect network resources against unauthorized access. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Learn how to create an effective access control policy that meets your security needs. The aim of annex a.9 is to safeguard access to information and ensure.
Access Control Got Your Six Cybersecurity
Security Policy On Access Control The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Annex a.9 is all about access control procedures. Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Organizations planning to implement an access control system should consider three abstractions: The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The aim of annex a.9 is to safeguard access to information and ensure. Access controls protect network resources against unauthorized access.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard Security Policy On Access Control Annex a.9 is all about access control procedures. Learn how to create an effective access control policy that meets your security needs. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac) will grant or deny user access based on. Security Policy On Access Control.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Security Policy On Access Control Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac). Security Policy On Access Control.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Security Policy On Access Control Learn how to create an effective access control policy that meets your security needs. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac) will grant or deny user access based on. Security Policy On Access Control.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Security Policy On Access Control Annex a.9 is all about access control procedures. Learn how to create an effective access control policy that meets your security needs. Access controls protect network resources against unauthorized access. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac). Security Policy On Access Control.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Security Policy On Access Control Learn how to create an effective access control policy that meets your security needs. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Annex a.9 is all about. Security Policy On Access Control.
From thecyphere.com
Access Control Security Types Of Access Control Security Policy On Access Control Annex a.9 is all about access control procedures. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and. Security Policy On Access Control.
From www.slideserve.com
PPT Computer Security Principles and Practice PowerPoint Security Policy On Access Control Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and. Security Policy On Access Control.
From www.slideserve.com
PPT Access Control Policies PowerPoint Presentation, free download Security Policy On Access Control Learn how to create an effective access control policy that meets your security needs. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment.. Security Policy On Access Control.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu Security Policy On Access Control Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. The aim of annex a.9 is to safeguard access to information and ensure. Learn how to create an effective access control policy that meets your security needs. Organizations planning to implement an access control system should. Security Policy On Access Control.
From old.sermitsiaq.ag
Access Control Policy Template Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Access controls protect network resources against unauthorized access. Annex a.9. Security Policy On Access Control.
From www.slideteam.net
Systems Access Control Security Policy Security Policy On Access Control The aim of annex a.9 is to safeguard access to information and ensure. Organizations planning to implement an access control system should consider three abstractions: Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The iso 27001 access control policy ensures the correct access to the correct information. Security Policy On Access Control.
From cyberhoot.com
Access Control Mechanism CyberHoot Security Policy On Access Control The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Access controls protect network resources against unauthorized access. Annex a.9 is all about access control procedures. Learn how to create an effective access control policy that meets your security needs. Organizations planning to implement an access control system should consider. Security Policy On Access Control.
From www.scribd.com
Remote Access Policy Word Template PDF Wi Fi Wireless Access Point Security Policy On Access Control Learn how to create an effective access control policy that meets your security needs. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. The aim of annex a.9 is to safeguard access to information and ensure. Access control is a type of security measure that limits the visibility, access,. Security Policy On Access Control.
From www.researchgate.net
Access Control and Other Security Services Download Scientific Diagram Security Policy On Access Control The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. The aim of annex a.9 is to safeguard access to information and ensure. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Learn how to create an effective. Security Policy On Access Control.
From www.researchgate.net
Format of a Role Based Access Control Policy Download Scientific Diagram Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Access controls protect network resources against unauthorized access. Learn how to. Security Policy On Access Control.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Security Policy On Access Control Access controls protect network resources against unauthorized access. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Organizations planning to implement an access control. Security Policy On Access Control.
From www.dexform.com
Security policy template in Word and Pdf formats Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes. Security Policy On Access Control.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Learn how to create an effective access control policy that meets your security needs. The iso 27001 access control policy ensures the correct access. Security Policy On Access Control.
From www.techtarget.com
What is network access control (NAC) and how does it work? Security Policy On Access Control Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Learn how to create an effective access control policy that meets your security needs.. Security Policy On Access Control.
From www.formsbirds.com
Standard Access Control Policy Template Free Download Security Policy On Access Control The aim of annex a.9 is to safeguard access to information and ensure. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access controls. Security Policy On Access Control.
From old.sermitsiaq.ag
Remote Access Security Policy Template Security Policy On Access Control Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Annex a.9 is all about access control procedures. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Organizations planning to implement an access control system should consider three. Security Policy On Access Control.
From www.educba.com
Security Policies List of 6 Most Useful Security Policies Security Policy On Access Control Annex a.9 is all about access control procedures. Organizations planning to implement an access control system should consider three abstractions: Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac). Security Policy On Access Control.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Security Policy On Access Control Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Annex a.9 is all about access control procedures. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Access control is a type of security measure. Security Policy On Access Control.
From www.slideserve.com
PPT Security Policies and Access Control PowerPoint Presentation Security Policy On Access Control Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. The iso 27001 access control policy ensures the correct access to. Security Policy On Access Control.
From www.csoonline.com
What is access control? A key component of data security CSO Online Security Policy On Access Control The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Access control is a type of security measure that limits the visibility, access, and use. Security Policy On Access Control.
From templates.hilarious.edu.np
Access Control Policy Template Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Learn how to create an effective access control policy that meets your security needs. Access controls protect network resources against unauthorized access. Access control. Security Policy On Access Control.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: The aim of annex a.9 is to safeguard access to information and ensure. Access controls protect network resources against unauthorized access. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Annex a.9 is all about access control. Security Policy On Access Control.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Access controls protect network resources against unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct. Security Policy On Access Control.
From sprinto.com
What is an Information Security Policy and Why is it Important? Security Policy On Access Control The aim of annex a.9 is to safeguard access to information and ensure. Access controls protect network resources against unauthorized access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Learn how to create an effective access control policy that meets your security needs. Annex a.9 is all. Security Policy On Access Control.
From www.resmo.com
9 Access Control Best Practices Resmo Security Policy On Access Control Annex a.9 is all about access control procedures. The aim of annex a.9 is to safeguard access to information and ensure. Organizations planning to implement an access control system should consider three abstractions: Learn how to create an effective access control policy that meets your security needs. The iso 27001 access control policy ensures the correct access to the correct. Security Policy On Access Control.
From www.techtarget.com
Secure data in the cloud with encryption and access controls TechTarget Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Access controls protect network resources against unauthorized access. The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. The aim of annex a.9 is to safeguard access to information and ensure. Annex a.9 is all about access control. Security Policy On Access Control.
From firewalltimes.com
Access Control Policy What to Include Security Policy On Access Control Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. The aim of annex a.9 is to safeguard access to information and ensure. Access controls protect network resources against unauthorized access. The iso 27001 access control policy ensures the correct access to the correct information and. Security Policy On Access Control.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Access controls protect network resources against unauthorized access. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. The aim of annex a.9 is to safeguard access to information and ensure. Annex a.9 is. Security Policy On Access Control.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Security Policy On Access Control The iso 27001 access control policy ensures the correct access to the correct information and resources by the correct people. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Learn how to create an effective access control policy that meets your security needs. Annex a.9 is all about. Security Policy On Access Control.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity Security Policy On Access Control Organizations planning to implement an access control system should consider three abstractions: Learn how to create an effective access control policy that meets your security needs. Attribute based access control (abac) will grant or deny user access based on arbitrary attributes of the user and arbitrary attributes of the object,. Annex a.9 is all about access control procedures. The iso. Security Policy On Access Control.