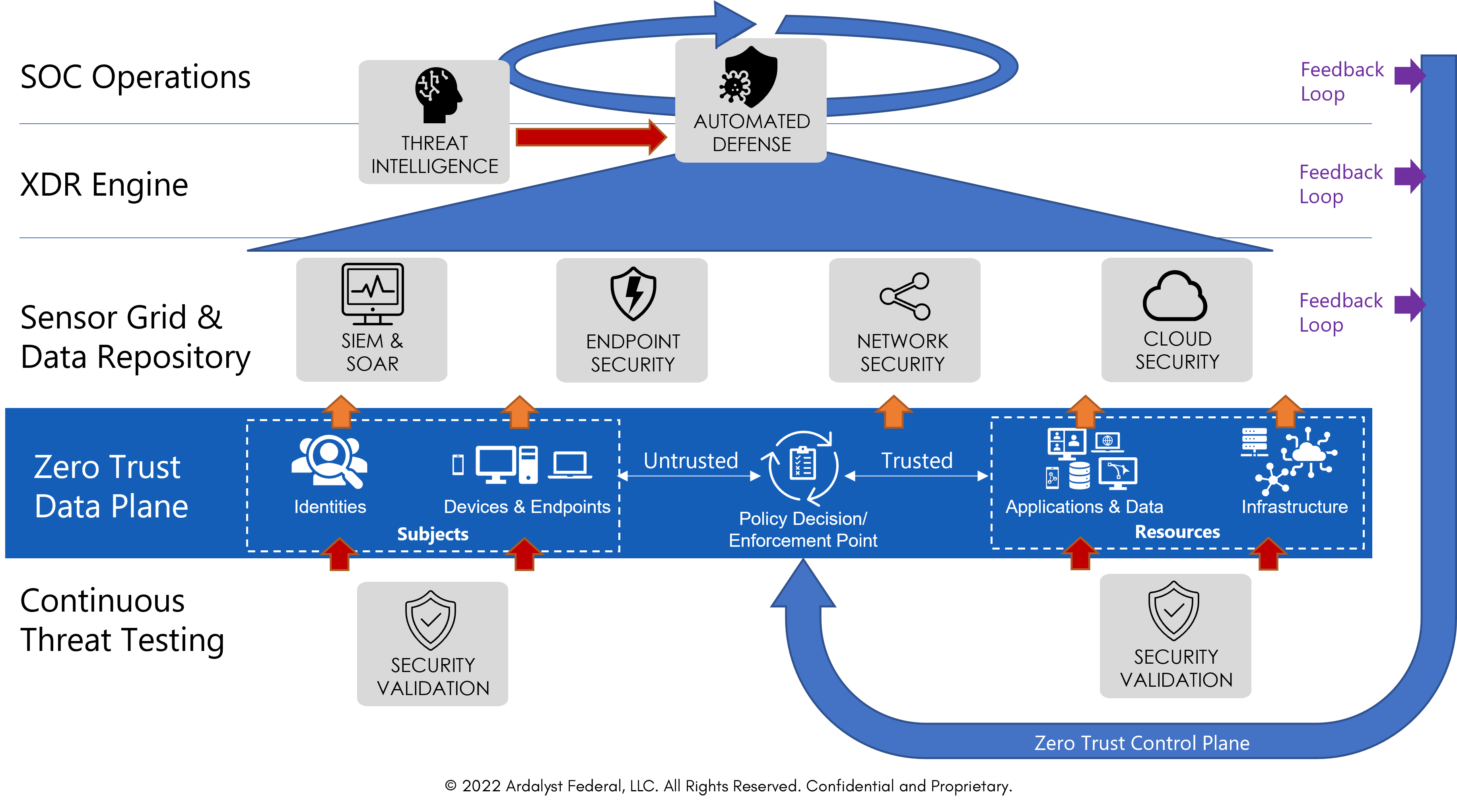
Endpoint Security Architecture . With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your.
from ardalyst.com
The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing.
AllThreat™ (Zero Trust) Architecture Ardalyst
Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. With threats continually increasing in sophistication and frequency, it is. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your.
From electronicsguide4u.com
The Ultimate Guide To Endpoint Security Solutions And Tools Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are. Endpoint Security Architecture.
From cdn.acalvio.com
The Role of Deception Technology in the Endpoint Security Reference Endpoint Security Architecture Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. This paper outlines the challenges. Endpoint Security Architecture.
From www.youtube.com
Microsoft Defender for Endpoint architecture YouTube Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. With threats continually. Endpoint Security Architecture.
From www.youtube.com
Thinking Cloud Endpoint Protection? Lets Look at 3 Solutions YouTube Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations.. Endpoint Security Architecture.
From mavink.com
Endpoint Security Architecture Endpoint Security Architecture Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. With threats continually increasing in. Endpoint Security Architecture.
From blog.trendmicro.ch
ICS endpoints, highlighted, as shown in a Purdue model architecture Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. This paper outlines the challenges and opportunities for security. Endpoint Security Architecture.
From docs.microsoft.com
Review Microsoft Defender for Endpoint architecture requirements and Endpoint Security Architecture Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. The microsoft cybersecurity. Endpoint Security Architecture.
From ardalyst.com
AllThreat™ (Zero Trust) Architecture Ardalyst Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity. Endpoint Security Architecture.
From subscription.packtpub.com
vShield Endpoint architecture VMware vCloud Security Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for. Endpoint Security Architecture.
From blazenetworks.co.uk
Endpoint Security Blaze Networks Endpoint Security Architecture Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. With threats continually increasing in sophistication and. Endpoint Security Architecture.
From blog.ahasayen.com
P1 Microsoft Defender for Endpoint Architecture Ammar Hasayen Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes. Endpoint Security Architecture.
From mavink.com
Microsoft Defender For Endpoint Architecture Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are. Endpoint Security Architecture.
From www.bitdefender.com
Bitdefender Managed Endpoint Detection and Response Service (MEDR) Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. An endpoint security. Endpoint Security Architecture.
From support.kaspersky.com
About Kaspersky Endpoint Security for Business Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of. Endpoint Security Architecture.
From mungfali.com
Defender For Endpoint Architecture Diagram Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. With threats continually increasing in sophistication and frequency, it is. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations.. Endpoint Security Architecture.
From www.itsasap.com
What is Microsoft Defender for Office 365? (A Beginner’s Guide) Endpoint Security Architecture Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security. Endpoint Security Architecture.
From uniserveit.com
The Goal Of Endpoint Security Uniserve IT Solutions Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. With threats continually increasing in sophistication and frequency, it is. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security architects as they race to keep up with this. Endpoint Security Architecture.
From www.cynet.com
Microsoft Defender for Endpoint Architecture, Plans, Pros & Cons Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. Endpoint security, a network's critical first line of cybersecurity defense, protects. Endpoint Security Architecture.
From sourceforge.net
Trellix DLP Endpoint Reviews and Pricing 2024 Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. With threats continually increasing in sophistication and frequency, it is. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of. Endpoint Security Architecture.
From docs.blackberry.com
Cylance Endpoint Security architecture Endpoint Security Architecture Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. With threats continually increasing in sophistication and frequency, it is. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity defense, protects end users. Endpoint Security Architecture.
From www.datalinknetworks.net
The Ultimate Guide to Endpoint Security Top Endpoint Security Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. With threats continually increasing in sophistication and frequency, it is. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops,. Endpoint Security Architecture.
From www.kareemccie.com
Introduction to Symantec Endpoint Architecture Network & Security Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess. Endpoint Security Architecture.
From aws.amazon.com
Choosing Your VPC Endpoint Strategy for Amazon S3 AWS Architecture Blog Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's. Endpoint Security Architecture.
From sc1.checkpoint.com
Endpoint Security Introduction Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. With threats continually increasing in sophistication and frequency,. Endpoint Security Architecture.
From designarchitects.art
Mcafee Endpoint Security Architecture The Architect Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's. Endpoint Security Architecture.
From www.vrogue.co
Microsoft Defender For Endpoint Architecture vrogue.co Endpoint Security Architecture An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. The microsoft cybersecurity reference architectures (mcra) are the component. Endpoint Security Architecture.
From www.cachatto.in
A Complete Guide To EndPoint Security And Its Importance In Enterprise Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. An endpoint security. Endpoint Security Architecture.
From www.vrogue.co
Managing Microsoft Defender For Endpoint With The New vrogue.co Endpoint Security Architecture Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. An endpoint security solution includes. Endpoint Security Architecture.
From www.spiceworks.com
What Is Endpoint Encryption? Definition, Architecture, and Best Endpoint Security Architecture Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. With threats continually increasing in sophistication and frequency, it is. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural. Endpoint Security Architecture.
From blog.omnetworks.com.np
5 StandOut Features of Endpoint Security You Should Know Endpoint Security Architecture Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. With threats continually increasing in. Endpoint Security Architecture.
From www.datalinknetworks.net
The Ultimate Guide to Microsoft Defender for Endpoint Protection (2023) Endpoint Security Architecture Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. With threats continually increasing in sophistication and frequency, it is. This paper outlines the challenges and opportunities for security architects as they race to. Endpoint Security Architecture.
From edfuturetech.com
Endpoint Detection and Response (EDR) Protecting Your Endpoints Endpoint Security Architecture The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. With threats continually increasing in sophistication and frequency, it is.. Endpoint Security Architecture.
From docs.trendmicro.com
Endpoint Encryption Components Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. The microsoft cybersecurity reference architectures (mcra) are the component of microsoft's security adoption framework (saf) that describe microsoft’s. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. With threats continually increasing. Endpoint Security Architecture.
From support.kaspersky.com
Applications and architecture of Kaspersky Security Center Cloud Console Endpoint Security Architecture This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. An endpoint security solution includes continuous monitoring, rapid time to detection, and architectural integrations. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. Endpoint security, a network's critical first line. Endpoint Security Architecture.
From www.techgape.com
5 Traits of a Great Endpoint Security System Endpoint Security Architecture With threats continually increasing in sophistication and frequency, it is. Defender for endpoint includes microsoft secure score for devices to help you dynamically assess the security state of your. This paper outlines the challenges and opportunities for security architects as they race to keep up with this rapidly changing. Endpoint security, a network's critical first line of cybersecurity defense, protects. Endpoint Security Architecture.