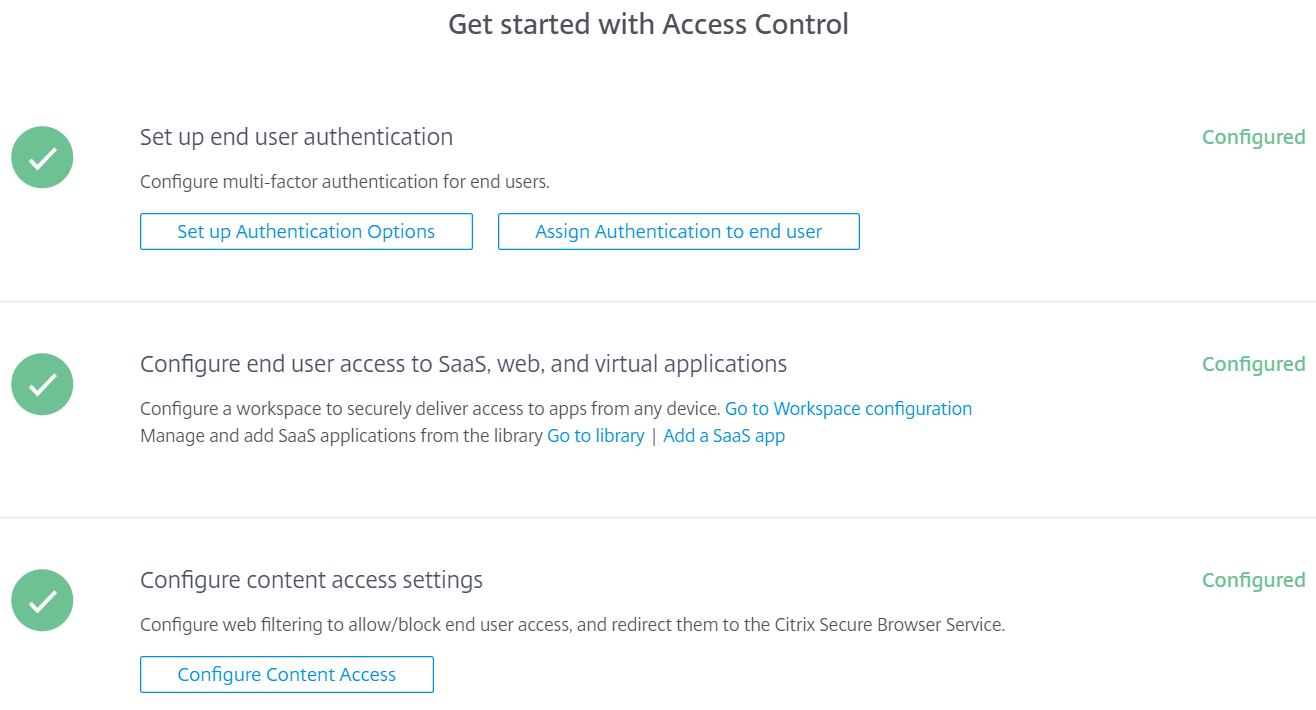
Access Control Citrix Policy . Citrix offers two methods of delivering citrix policy settings: Then you configure a higher priority citrix. I want to block this when a user is coming in. This policy controls user access to files, folders, and registries. You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control user access to apps. The app access control feature lets you control access to applications using rules. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. With this feature, you can streamline the management of.
from docs.citrix.com
A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. Then you configure a higher priority citrix. Citrix offers two methods of delivering citrix policy settings: Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. This policy controls user access to files, folders, and registries. You typically configure the unfiltered citrix policy to block all client device mappings. With this feature, you can streamline the management of. The app access control feature lets you control access to applications using rules.
Reference Architecture Secure Private Access Citrix Tech Zone
Access Control Citrix Policy A typical use case is to apply rules to control user access to apps. You typically configure the unfiltered citrix policy to block all client device mappings. Then you configure a higher priority citrix. The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. With this feature, you can streamline the management of. I want to block this when a user is coming in. This policy controls user access to files, folders, and registries. Citrix offers two methods of delivering citrix policy settings: Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from.
From community.citrix.com
Issue with Citrix WEM Service on File System Operations Access Access Control Citrix Policy Then you configure a higher priority citrix. Citrix offers two methods of delivering citrix policy settings: I want to block this when a user is coming in. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. You typically configure the unfiltered citrix policy to block all client device mappings. With this feature, you. Access Control Citrix Policy.
From community.citrix.com
On premises Delivery Controller required? Access Control Citrix Access Control Citrix Policy Citrix offers two methods of delivering citrix policy settings: You typically configure the unfiltered citrix policy to block all client device mappings. Then you configure a higher priority citrix. With this feature, you can streamline the management of. A typical use case is to apply rules to control user access to apps. I want to block this when a user. Access Control Citrix Policy.
From docs.citrix.com
リファレンスアーキテクチャリモートPCアクセス Citrix Tech Zone Access Control Citrix Policy The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. This policy controls user access to files, folders, and registries. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. With this feature, you can streamline the. Access Control Citrix Policy.
From clouddnagroup.com
What is Citrix Secure Access? • cloudDNA Access Control Citrix Policy The app access control feature lets you control access to applications using rules. I want to block this when a user is coming in. Then you configure a higher priority citrix. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. This policy controls user access to files, folders, and registries. A typical use. Access Control Citrix Policy.
From docs.citrix.com
End user settings Citrix Enterprise Browser Access Control Citrix Policy A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. You typically configure the unfiltered citrix policy to block all client device mappings. Then you configure a higher priority citrix. Citrix offers two methods of delivering citrix policy settings: This policy controls user access to. Access Control Citrix Policy.
From docs.citrix.com
Policy templates Citrix Virtual Apps and Desktops 7 2407 Access Control Citrix Policy Citrix offers two methods of delivering citrix policy settings: You typically configure the unfiltered citrix policy to block all client device mappings. With this feature, you can streamline the management of. A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. Then you configure a. Access Control Citrix Policy.
From docs.citrix.com
SmartAccess for HDX apps Citrix Endpoint Management Access Control Citrix Policy Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. I want to block this when a user is coming in. This policy controls user access to files, folders, and registries. You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy I want to block this when a user is coming in. A typical use case is to apply rules to control user access to apps. This policy controls user access to files, folders, and registries. With this feature, you can streamline the management of. You typically configure the unfiltered citrix policy to block all client device mappings. Citrix offers two. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy This policy controls user access to files, folders, and registries. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control user access to apps. With this feature, you can streamline the. Access Control Citrix Policy.
From docs.citrix.com
Contextual App Protection for Workspace Citrix Workspace app Access Control Citrix Policy You typically configure the unfiltered citrix policy to block all client device mappings. I want to block this when a user is coming in. Then you configure a higher priority citrix. The app access control feature lets you control access to applications using rules. This policy controls user access to files, folders, and registries. With this feature, you can streamline. Access Control Citrix Policy.
From docs.citrix.com
Tech Brief Citrix Workspace Citrix Tech Zone Access Control Citrix Policy You typically configure the unfiltered citrix policy to block all client device mappings. This policy controls user access to files, folders, and registries. Citrix offers two methods of delivering citrix policy settings: Then you configure a higher priority citrix. The app access control feature lets you control access to applications using rules. With this feature, you can streamline the management. Access Control Citrix Policy.
From clouddnagroup.com
What is Citrix Secure Private Access? • cloudDNA Access Control Citrix Policy I want to block this when a user is coming in. The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. Then you configure a higher priority citrix. This policy controls user access to files, folders, and registries. Access control keeps confidential information. Access Control Citrix Policy.
From www.citrix.com
Citrix Masterclass Citrix Secure Private Access and Autoscale On Access Control Citrix Policy The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. I want to block this when a user is coming in. Then you configure a higher priority. Access Control Citrix Policy.
From www.quadrasystems.net
Quadra Citrix Secure Private Access An Essential Tool for Protecting Access Control Citrix Policy A typical use case is to apply rules to control user access to apps. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. With this feature, you can streamline the management of. You typically configure the unfiltered citrix policy to block all client device mappings. Then you configure a higher priority citrix. Citrix. Access Control Citrix Policy.
From www.sourcesecurity.com
Citrix modernises security to hybrid work Security News Access Control Citrix Policy With this feature, you can streamline the management of. The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. This policy controls user access to files, folders, and registries. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual. Access Control Citrix Policy.
From learn.microsoft.com
Session controls in Conditional Access policy Microsoft Entra ID Access Control Citrix Policy You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control user access to apps. This policy controls user access to files, folders, and registries. With this feature, you can streamline the management of. I want to block this when a user is coming in. The app access. Access Control Citrix Policy.
From www.slideserve.com
PPT Citrix Access Gateway 5.0 Selling & Positioning PowerPoint Access Control Citrix Policy A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. With this feature, you can streamline the management of. This policy controls user access to files, folders, and registries. Citrix offers two methods of delivering citrix policy settings: Then you configure a higher priority citrix.. Access Control Citrix Policy.
From www.slideserve.com
PPT What is Citrix ‘Smart Access’? PowerPoint Presentation, free Access Control Citrix Policy With this feature, you can streamline the management of. Citrix offers two methods of delivering citrix policy settings: This policy controls user access to files, folders, and registries. A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. The app access control feature lets you. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy You typically configure the unfiltered citrix policy to block all client device mappings. The app access control feature lets you control access to applications using rules. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. With this feature, you can streamline the management of. This policy controls user access to files, folders, and. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy Then you configure a higher priority citrix. The app access control feature lets you control access to applications using rules. You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control user access to apps. This policy controls user access to files, folders, and registries. I want to. Access Control Citrix Policy.
From centrogeriatricohera.com.br
5 types of access control Access Control Citrix Policy Then you configure a higher priority citrix. The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. With this feature, you can streamline the management of. This policy controls user access to. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy This policy controls user access to files, folders, and registries. The app access control feature lets you control access to applications using rules. A typical use case is to apply rules to control user access to apps. With this feature, you can streamline the management of. I want to block this when a user is coming in. Citrix offers two. Access Control Citrix Policy.
From www.pdfprof.com
citrix cloud security compliance Access Control Citrix Policy Then you configure a higher priority citrix. You typically configure the unfiltered citrix policy to block all client device mappings. Citrix offers two methods of delivering citrix policy settings: The app access control feature lets you control access to applications using rules. I want to block this when a user is coming in. Access control keeps confidential information such as. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy With this feature, you can streamline the management of. Then you configure a higher priority citrix. A typical use case is to apply rules to control user access to apps. The app access control feature lets you control access to applications using rules. This policy controls user access to files, folders, and registries. Access control keeps confidential information such as. Access Control Citrix Policy.
From www.ervik.as
Citrix Secure Private Access Ervik.as Access Control Citrix Policy Citrix offers two methods of delivering citrix policy settings: I want to block this when a user is coming in. This policy controls user access to files, folders, and registries. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. You typically configure the unfiltered citrix policy to block all client device mappings. With. Access Control Citrix Policy.
From www.techtarget.com
Compare Citrix ADC and VMware Unified Access Gateway VMware vs Access Control Citrix Policy This policy controls user access to files, folders, and registries. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. The app access control feature lets you control access to applications using rules. With this feature, you can streamline the management of. A typical use case is to apply rules to control user access. Access Control Citrix Policy.
From docs.citrix.com
Configure Citrix Secure Private Access Citrix Secure Private Access Access Control Citrix Policy You typically configure the unfiltered citrix policy to block all client device mappings. The app access control feature lets you control access to applications using rules. I want to block this when a user is coming in. This policy controls user access to files, folders, and registries. With this feature, you can streamline the management of. Citrix offers two methods. Access Control Citrix Policy.
From community.citrix.com
Citrix Cloud admin login error when use Entra ID identity Access Access Control Citrix Policy The app access control feature lets you control access to applications using rules. With this feature, you can streamline the management of. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. This policy controls user access to files, folders, and registries. Then you configure a higher priority citrix. You typically configure the unfiltered. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy A typical use case is to apply rules to control user access to apps. I want to block this when a user is coming in. With this feature, you can streamline the management of. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. The app access control feature lets you control access to. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. The app access control feature lets you control access to applications using rules. You typically configure the unfiltered citrix policy to block all client device mappings. With this feature, you can streamline the management of. Then you configure a higher priority citrix. Citrix offers. Access Control Citrix Policy.
From www.slideserve.com
PPT Citrix Access Gateway 5.0 Selling & Positioning PowerPoint Access Control Citrix Policy Citrix offers two methods of delivering citrix policy settings: You typically configure the unfiltered citrix policy to block all client device mappings. A typical use case is to apply rules to control user access to apps. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. I want to block this when a user. Access Control Citrix Policy.
From docs.citrix.com
Reference Architecture Secure Private Access Citrix Tech Zone Access Control Citrix Policy With this feature, you can streamline the management of. This policy controls user access to files, folders, and registries. Then you configure a higher priority citrix. A typical use case is to apply rules to control user access to apps. The app access control feature lets you control access to applications using rules. Citrix offers two methods of delivering citrix. Access Control Citrix Policy.
From www.slideserve.com
PPT Citrix Access Gateway Advanced Edition Technical Overview Access Control Citrix Policy With this feature, you can streamline the management of. The app access control feature lets you control access to applications using rules. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. Then you configure a higher priority citrix. Citrix offers two methods of delivering citrix policy settings: You typically configure the unfiltered citrix. Access Control Citrix Policy.
From docs.citrix.com
Manage administrator access to Citrix Cloud Citrix Cloud Access Control Citrix Policy Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. The app access control feature lets you control access to applications using rules. Then you configure a higher priority citrix. This policy controls user access to files, folders, and registries. A typical use case is to apply rules to control user access to apps.. Access Control Citrix Policy.
From dennisspan.com
Making limited use of Citrix SmartAccess without Universal licenses Access Control Citrix Policy With this feature, you can streamline the management of. This policy controls user access to files, folders, and registries. Then you configure a higher priority citrix. Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from. I want to block this when a user is coming in. The app access control feature lets you. Access Control Citrix Policy.