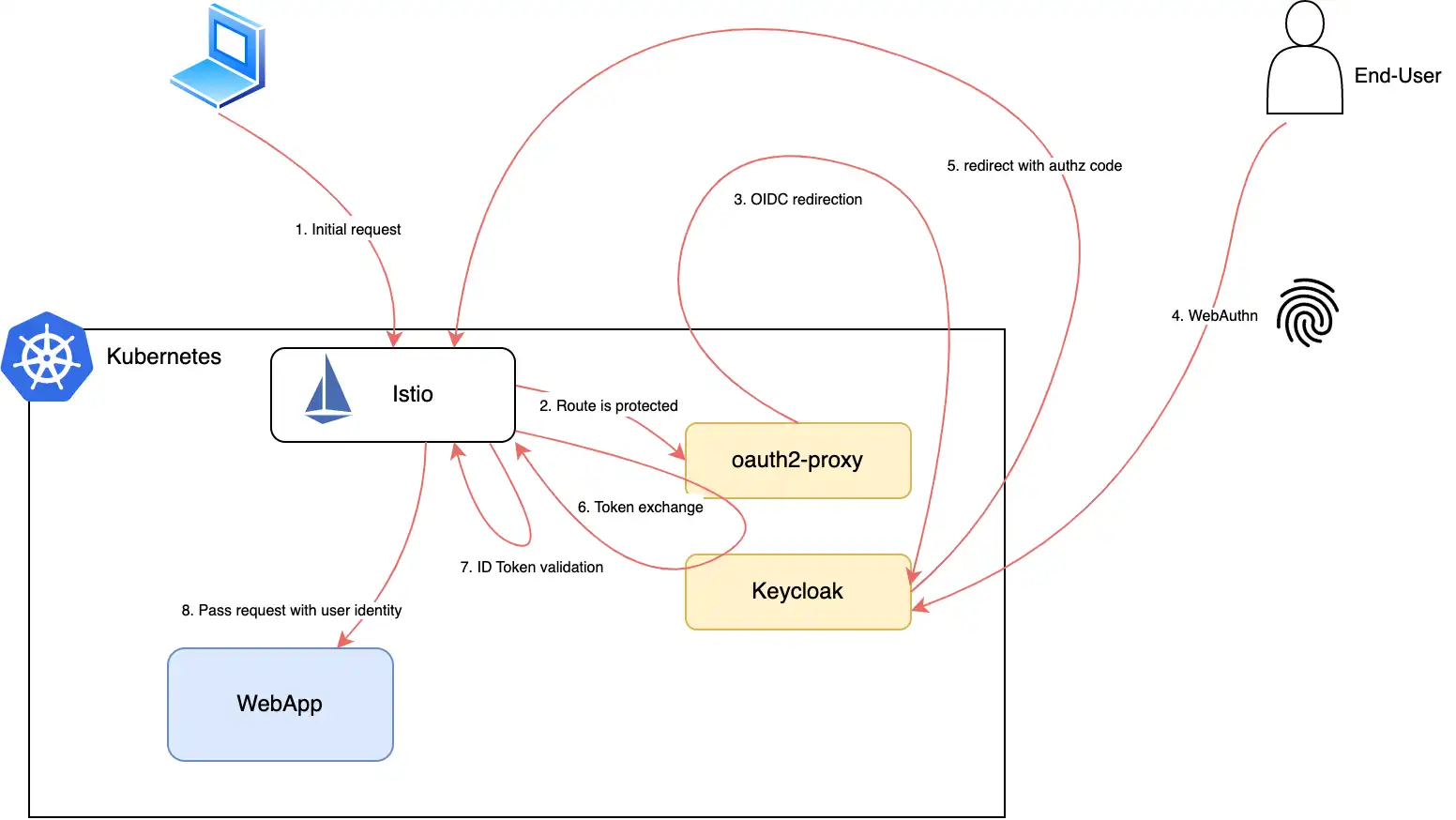
Keycloak Istio Authentication . The goal is to simplify. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. Keycloak is a prominent open source identity and access management (iam) solution. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. It is capable of authenticating a user. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. A web app pod (cars web): Clients are entities that can request keycloak to authenticate a user. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. In this blog post, we will look at the first part of my ideal setup,. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. Configuring istio with oidc authentication. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token.
from baptistout.net
Clients are entities that can request keycloak to authenticate a user. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Keycloak is a prominent open source identity and access management (iam) solution. A web app pod (cars web): It is capable of authenticating a user. The goal is to simplify. Configuring istio with oidc authentication. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. In this blog post, we will look at the first part of my ideal setup,. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single.
Passwordless authentication with Authn, Keycloak and Istio
Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. It is capable of authenticating a user. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. A web app pod (cars web): This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Keycloak is a prominent open source identity and access management (iam) solution. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. The goal is to simplify. Configuring istio with oidc authentication. In this blog post, we will look at the first part of my ideal setup,. Clients are entities that can request keycloak to authenticate a user.
From platform.ex-offenders.co.uk
Authentication and Authorization with Istio and Keycloak Cloud Keycloak Istio Authentication Clients are entities that can request keycloak to authenticate a user. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. It is capable of authenticating a user. A web app pod (cars web): Keycloak is a prominent open source identity and access management (iam) solution. Among other. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication Configuring istio with oidc authentication. In this blog post, we will look at the first part of my ideal setup,. A web app pod (cars web): It is capable of authenticating a user. Clients are entities that can request keycloak to authenticate a user. Keycloak is a prominent open source identity and access management (iam) solution. Learn how to enable. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication Clients are entities that can request keycloak to authenticate a user. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Configuring istio with oidc authentication. The goal is to simplify. Most often, clients are applications and services that want to use keycloak to secure themselves and provide. Keycloak Istio Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. A web app pod (cars web): This pod contains the web app that will perform the authentification through the keycloak login in. Keycloak Istio Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Istio Authentication Keycloak is a prominent open source identity and access management (iam) solution. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. Configuring istio with oidc authentication. In this blog post, we will look at the first part of my ideal setup,. Clients are entities that can request keycloak to authenticate. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication It is capable of authenticating a user. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. Configuring istio with oidc authentication. The goal is to simplify. A web app pod (cars web):. Keycloak Istio Authentication.
From labs.consol.de
Simple example how to use Istio and Keycloak ConSol Labs Keycloak Istio Authentication Keycloak is a prominent open source identity and access management (iam) solution. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. My idea is to. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication Clients are entities that can request keycloak to authenticate a user. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Keycloak is a prominent open source identity and access management (iam) solution. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and. Keycloak Istio Authentication.
From medium.com
EndUserAuthentication with Istio & Keycloak by Engin Güngör Dec Keycloak Istio Authentication The goal is to simplify. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. It is capable of authenticating a user. Among other things, i wanted to show how to. Keycloak Istio Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Istio Authentication Clients are entities that can request keycloak to authenticate a user. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. Configuring istio with oidc authentication. It is capable of authenticating a user. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. Most often,. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. In this blog post, we will look at the first part of my ideal setup,. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Keycloak is a prominent open source identity and access management (iam). Keycloak Istio Authentication.
From www.dangtrinh.com
Enduser authentication with Istio and KeyCloak on the AWS EKS environment Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. It is capable of authenticating a user. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single.. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. Clients are entities that can request keycloak to authenticate a user. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. It is capable of authenticating a user. A web app pod (cars web): The goal. Keycloak Istio Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Istio Authentication A web app pod (cars web): Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. It is capable of authenticating a user. Learn how to enable request level authentication for. Keycloak Istio Authentication.
From okansungur.medium.com
k8sistiossokeycloak(iam). Authentication is the process of… by Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. The goal is to simplify. Clients are entities that can request keycloak to authenticate a user. In this blog post, we will look at the first part of my ideal setup,. Most often, clients are applications and services that want to use. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. A web app pod (cars web): Clients are entities that can request keycloak to authenticate a user. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt. Keycloak Istio Authentication.
From www.agile-solutions.ch
Keycloak agilesolution Keycloak Istio Authentication In this blog post, we will look at the first part of my ideal setup,. Clients are entities that can request keycloak to authenticate a user. The goal is to simplify. Configuring istio with oidc authentication. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. My idea is to implement keycloak authentication. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication A web app pod (cars web): Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Keycloak is a prominent open source identity and access management (iam) solution. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. It is capable of authenticating a user.. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication A web app pod (cars web): My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain. Keycloak Istio Authentication.
From labs.consol.de
Simple example how to use Istio and Keycloak ConSol Labs Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. A web app pod (cars web): Among other things,. Keycloak Istio Authentication.
From www.dangtrinh.com
Enduser authentication with Istio and KeyCloak on the AWS EKS environment Keycloak Istio Authentication In this blog post, we will look at the first part of my ideal setup,. The goal is to simplify. A web app pod (cars web): Configuring istio with oidc authentication. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. Learn how to enable request level authentication for your applications using. Keycloak Istio Authentication.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Istio Authentication The goal is to simplify. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. In this blog post, we will look at the first part of my ideal setup,. Clients are entities that can request keycloak to authenticate a user. My idea is to implement keycloak authentication. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication It is capable of authenticating a user. Clients are entities that can request keycloak to authenticate a user. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Among other things,. Keycloak Istio Authentication.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Istio Authentication My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific,. Keycloak Istio Authentication.
From www.youtube.com
Securing Requests with Keycloak and Istio through RequestLevel Keycloak Istio Authentication It is capable of authenticating a user. The goal is to simplify. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. Configuring istio with oidc authentication. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. A web app pod. Keycloak Istio Authentication.
From aytartana.wordpress.com
Adding Authentication with nocode, Istio and Keycloak Jonathan Vila Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. Clients are entities that can request keycloak to authenticate a user. Learn how to enable request. Keycloak Istio Authentication.
From medium.com
API Authentication Configure Istio IngressGateway, OAuth2Proxy and Keycloak Istio Authentication Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. It is capable of authenticating a user. My idea is to implement keycloak authentication where oauth2 used as an external auth provider in the istio. A web app pod (cars web): Configuring istio with oidc authentication. Most often,. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. A web. Keycloak Istio Authentication.
From www.infracloud.io
Securing Requests with Keycloak and Istio through RequestLevel Keycloak Istio Authentication Configuring istio with oidc authentication. It is capable of authenticating a user. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. In this blog post, we will look at the first part of my ideal setup,. The goal is to simplify. Most often, clients are applications and. Keycloak Istio Authentication.
From keycloak.blogspot.com
Keycloak Keycloak and Istio Keycloak Istio Authentication Configuring istio with oidc authentication. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. Clients are entities that can request keycloak to authenticate a user. Keycloak is a prominent open source identity and access management (iam) solution. My idea is to implement keycloak authentication where oauth2 used. Keycloak Istio Authentication.
From www.infracloud.io
Guide to Istio’s Authentication and Authorization Policies Keycloak Istio Authentication The goal is to simplify. It is capable of authenticating a user. Clients are entities that can request keycloak to authenticate a user. A web app pod (cars web): In this guide, we will explore how to leverage istio to implement authentication and authorization using keycloak. This pod contains the web app that will perform the authentification through the keycloak. Keycloak Istio Authentication.
From www.infracloud.io
Request Level Authentication and Authorization with Istio and Keycloak Keycloak Istio Authentication In this blog post, we will look at the first part of my ideal setup,. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. Clients are entities that can request keycloak to authenticate a user. The goal is to simplify. Configuring istio with oidc authentication. A web. Keycloak Istio Authentication.
From labs.consol.de
Simple example how to use Istio and Keycloak ConSol Labs Keycloak Istio Authentication Clients are entities that can request keycloak to authenticate a user. Most often, clients are applications and services that want to use keycloak to secure themselves and provide a single. Learn how to enable request level authentication for your applications using istio’s request authentication/authorization and keycloak. Keycloak is a prominent open source identity and access management (iam) solution. This pod. Keycloak Istio Authentication.
From medium.com
EndUserAuthentication with Istio & Keycloak by Engin Güngör Dec Keycloak Istio Authentication A web app pod (cars web): Configuring istio with oidc authentication. Among other things, i wanted to show how to do the authentication with jwt token in general and, more specific, with keycloak. This pod contains the web app that will perform the authentification through the keycloak login in order to obtain a jwt token. It is capable of authenticating. Keycloak Istio Authentication.